Subnet Cheat Sheet – 24 Subnet Mask, 30, 26, 27, 29, and other IP Address CIDR Network References

As a developer or network engineer, you may need to occasionally look up subnet mask values and figure out what they mean.
To make your life easier, the freeCodeCamp community has made this simple cheat sheet. Just scroll or use Ctrl/Cmd + f to find the value you're looking for.
Here are the charts, followed by some explanations of what they mean.
| CIDR | Subnet mask | Wildcard mask | # of IP addresses | # of usable IP addresses |
| /32 | 255.255.255.255 | 0.0.0.0 | 1 | 1 |
| /31 | 255.255.255.254 | 0.0.0.1 | 2 | 2* |
| /30 | 255.255.255.252 | 0.0.0.3 | 4 | 2 |
| /29 | 255.255.255.248 | 0.0.0.7 | 8 | 6 |
| /28 | 255.255.255.240 | 0.0.0.15 | 16 | 14 |
| /27 | 255.255.255.224 | 0.0.0.31 | 32 | 30 |
| /26 | 255.255.255.192 | 0.0.0.63 | 64 | 62 |
| /25 | 255.255.255.128 | 0.0.0.127 | 128 | 126 |
| /24 | 255.255.255.0 | 0.0.0.255 | 256 | 254 |
| /23 | 255.255.254.0 | 0.0.1.255 | 512 | 510 |
| /22 | 255.255.252.0 | 0.0.3.255 | 1,024 | 1,022 |
| /21 | 255.255.248.0 | 0.0.7.255 | 2,048 | 2,046 |
| /20 | 255.255.240.0 | 0.0.15.255 | 4,096 | 4,094 |
| /19 | 255.255.224.0 | 0.0.31.255 | 8,192 | 8,190 |
| /18 | 255.255.192.0 | 0.0.63.255 | 16,384 | 16,382 |
| /17 | 255.255.128.0 | 0.0.127.255 | 32,768 | 32,766 |
| /16 | 255.255.0.0 | 0.0.255.255 | 65,536 | 65,534 |
| /15 | 255.254.0.0 | 0.1.255.255 | 131,072 | 131,070 |
| /14 | 255.252.0.0 | 0.3.255.255 | 262,144 | 262,142 |
| /13 | 255.248.0.0 | 0.7.255.255 | 524,288 | 524,286 |
| /12 | 255.240.0.0 | 0.15.255.255 | 1,048,576 | 1,048,574 |
| /11 | 255.224.0.0 | 0.31.255.255 | 2,097,152 | 2,097,150 |
| /10 | 255.192.0.0 | 0.63.255.255 | 4,194,304 | 4,194,302 |
| /9 | 255.128.0.0 | 0.127.255.255 | 8,388,608 | 8,388,606 |
| /8 | 255.0.0.0 | 0.255.255.255 | 16,777,216 | 16,777,214 |
| /7 | 254.0.0.0 | 1.255.255.255 | 33,554,432 | 33,554,430 |
| /6 | 252.0.0.0 | 3.255.255.255 | 67,108,864 | 67,108,862 |
| /5 | 248.0.0.0 | 7.255.255.255 | 134,217,728 | 134,217,726 |
| /4 | 240.0.0.0 | 15.255.255.255 | 268,435,456 | 268,435,454 |
| /3 | 224.0.0.0 | 31.255.255.255 | 536,870,912 | 536,870,910 |
| /2 | 192.0.0.0 | 63.255.255.255 | 1,073,741,824 | 1,073,741,822 |
| /1 | 128.0.0.0 | 127.255.255.255 | 2,147,483,648 | 2,147,483,646 |
| /0 | 0.0.0.0 | 255.255.255.255 | 4,294,967,296 | 4,294,967,294 |
- /31 is a special case detailed in RFC 3021 where networks with this type of subnet mask can assign two IP addresses as a point-to-point link.
And here's a table of the decimal to binary conversions for subnet mask and wildcard octets:
| Subnet Mask | Wildcard | ||
| 0 | 00000000 | 255 | 11111111 |
| 128 | 10000000 | 127 | 01111111 |
| 192 | 11000000 | 63 | 00111111 |
| 224 | 11100000 | 31 | 00011111 |
| 240 | 11110000 | 15 | 00001111 |
| 248 | 11111000 | 7 | 00000111 |
| 252 | 11111100 | 3 | 00000011 |
| 254 | 11111110 | 1 | 00000001 |
| 255 | 11111111 | 0 | 00000000 |
Note that the wildcard is just the inverse of the subnet mask.
If you are new to network engineering, you can get a better idea of how computer networks work here .
Finally, this cheat sheet and the rest of the article is focused on IPv4 addresses, not the newer IPv6 protocol. If you'd like to learn more about IPv6, check out the article on computer networks above.

How Do IP Address Blocks Work?
IPv4 addresses like 192.168.0.1 are really just decimal representations of four binary blocks.
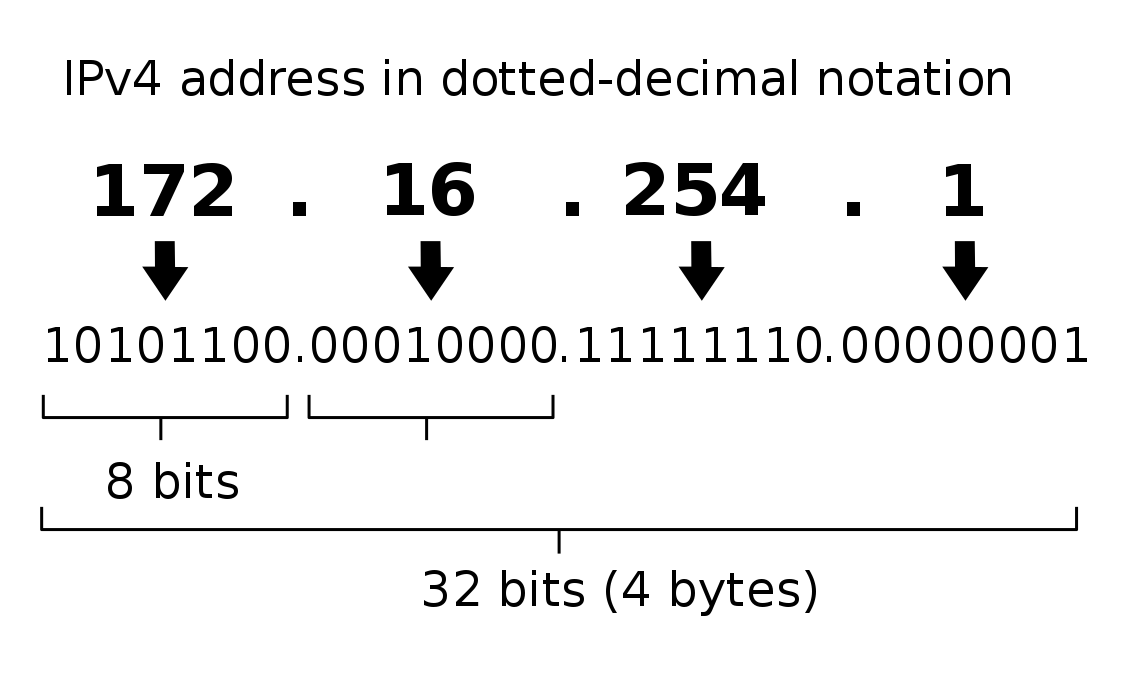
Each block is 8 bits, and represents numbers from 0-255. Because the blocks are groups of 8 bits, each block is known as an octet . And since there are four blocks of 8 bits, every IPv4 address is 32 bits.
For example, here's what the IP address 172.16.254.1 looks like in binary:
To convert an IP address between its decimal and binary forms, you can use this chart:
| 128 | 64 | 32 | 16 | 8 | 4 | 2 | 1 |
| x | x | x | x | x | x | x | x |
The chart above represents one 8 bit octive.
Now lets say you want to convert the IP address 168.210.225.206 . All you need to do is break the address into four blocks ( 168 , 210 , 225 , and 206 ), and convert each into binary using the chart above.
Remember that in binary, 1 is the equivalent to "on" and 0 is "off". So to convert the first block, 168 , into binary, just start from the beginning of the chart and place a 1 or 0 in that cell until you get a sum of 168 .
For example:
| 128 | 64 | 32 | 16 | 8 | 4 | 2 | 1 |
| 1 | 0 | 1 | 0 | 1 | 0 | 0 | 0 |
128 + 32 + 8 = 168, which in binary is 10101000 .
If you do this for the rest of the blocks, you'd get 10101000.11010010.11100001.11001110 .
What is Subnetting?
If you look at the table above, it can seem like the number of IP addresses is practically unlimited. After all, there are almost 4.2 billion possible IPv4 addresses available.
But if you think about how much the internet has grown, and how many more devices are connected these days, it might not surprise you to hear that there's already a shortage of IPv4 addresses .
Because the shortage was recognized years ago, developers came up with a way to split up an IP address into smaller networks called subnets.
This process, called subnetting, uses the host section of the IP address to break it down into those smaller networks or subnets.
Generally, an IP address is made up of network bits and host bits:
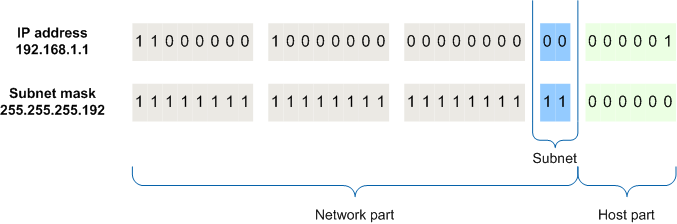
So generally, subnetting does two things: it gives us a way to break up networks into subnets, and allows devices to determine whether another device/IP address is on the same local network or not.
A good way to think about subnetting is to picture your wireless network at home.
Without subnetting, every internet connected device would need its own unique IP address.
But since you have a wireless router, you just need one IP address for your router. This public or external IP address is usually handled automatically, and is assigned by your internet service provider (ISP).
Then every device connected to that router has its own private or internal IP address:
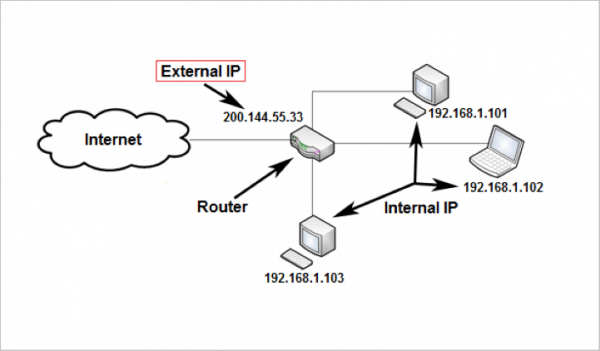
Now if your device with the internal IP address 192.168.1.101 wants to communicate with another device, it'll use the IP address of the other device and the subnet mask.
The combination of the IP addresses and subnet mask allows the device at 192.168.1.101 to figure out if the other device is on the same network (like the device at 192.168.1.103 ), or on a completely different network somewhere else online.
Interestingly, the external IP address assigned to your router by your ISP is probably part of a subnet, which might include many other IP addresses for nearby homes or businesses. And just like internal IP addresses, it also needs a subnet mask to work.
How Subnet Masks Work
Subnet masks function as a sort of filter for an IP address. With a subnet mask, devices can look at an IP address, and figure out which parts are the network bits and which are the host bits.
Then using those things, it can figure out the best way for those devices to communicate.
If you've poked around the network settings on your router or computer, you've likely seen this number: 255.255.255.0 .
If so, you've seen a very common subnet mask for simple home networks.
Like IPv4 addresses, subnet masks are 32 bits. And just like converting an IP address into binary, you can do the same thing with a subnet mask.
For example, here's our chart from earlier:
Now let's convert the first octet, 255:
| 128 | 64 | 32 | 16 | 8 | 4 | 2 | 1 |
| 1 | 1 | 1 | 1 | 1 | 1 | 1 | 1 |
Pretty simple, right? So any octet that's 255 is just 11111111 in binary. This means that 255.255.255.0 is really 11111111.11111111.11111111.00000000 in binary.
Now let's look at a subnet mask and IP address together and calculate which parts of the IP address are the network bits and host bits.
Here are the two in both decimal and binary:
| Type | Decimal | Binary |
| IP address | 192.168.0.101 | 11000000.10101000.00000000.01100101 |
| Subnet mask | 255.255.255.0 | 11111111.11111111.11111111.00000000 |
With the two laid out like this, it's easy to separate 192.168.0.101 into network bits and host bits.
Whenever a bit in a binary subnet mask is 1, then the same bit in a binary IP address is part of the network, not the host.
Since the octet 255 is 11111111 in binary, that whole octet in the IP address is part of the network. So the first three octets, 192.168.0 , is the network portion of the IP address, and 101 is the host portion.
In other words, if the device at 192.168.0.101 wants to communicate with another device, using the subnet mask it knows that anything with the IP address 192.168.0.xxx is on the same local network.
Another way to express this is with a network ID, which is just the network portion of the IP address. So the network ID of the address 192.168.0.101 with a subnet mask of 255.255.255.0 is 192.168.0.0 .
And it's the same for the other devices on the local network ( 192.168.0.102 , 192.168.0.103 , and so on).
What Does CIDR Mean and What is CIDR Notation?
CIDR stands for Classless Inter-Domain Routing, and is used in IPv4, and more recently, IPv6 routing.
CIDR was introduced in 1993 as a way to slow the usage of IPv4 addresses, which were quickly being exhausted under the older Classful IP addressing system that the internet was first built on.
CIDR encompasses a couple of major concepts.
The first is Variable Length Submasking (VLSM), which basically allowed network engineers to create subnets within subnets. And those subnets could be different sizes, so there would be fewer unused IP addresses.
The second major concept CIDR introduced is CIDR notation.
CIDR notation is really just shorthand for the subnet mask, and represents the number of bits available to the IP address. For instance, the /24 in 192.168.0.101/24 is equivalent to the IP address 192.168.0.101 and the subnet mask 255.255.255.0 .
How to Calculate CIDR Noation
To figure out the CIDR notation for a given subnet mask, all you need to do is convert the subnet mask into binary, then count the number of ones or "on" digits. For example:
| Type | Decimal | Binary |
| Subnet mask | 255.255.255.0 | 11111111.11111111.11111111.00000000 |
Because there's three octets of ones, there are 24 "on" bits meaning that the CIDR notation is /24 .
You can write it either way, but I'm sure you'll agree that /24 is a whole lot easier to write than 255.255.255.0 .
This is usually done with an IP address, so let's take a look at the same subnet mask with an IP address:
The first three octets of the subnet mask are all "on" bits, so that means that the same three octets in the IP address are all network bits.
Let's take a look at the last forth octet in a bit more detail:
| Type | Decimal | Binary |
| IP address | 101 | 01100101 |
| Subnet mask | 0 | 00000000 |
In this case, because all the bits for this octet in the subnet mask are "off", we can be certain that all of the corresponding bits for this octet in the IP address are part of the host.
When you write CIDR notation it's usually done with the network ID. So the CIDR notation of the IP address 192.168.0.101 with a subnet mask of 255.255.255.0 is 192.168.0.0/24 .
To see more examples of how to calculate the CIDR notation and network ID for a given IP address and subnet mask, check out this video:
Classful IP Addressing
Now that we've gone over some basic examples of subnetting and CIDR, let's zoom out and look at what's known as Classful IP addressing.
Back before subnetting was developed, all IP addresses fell into a particular class:
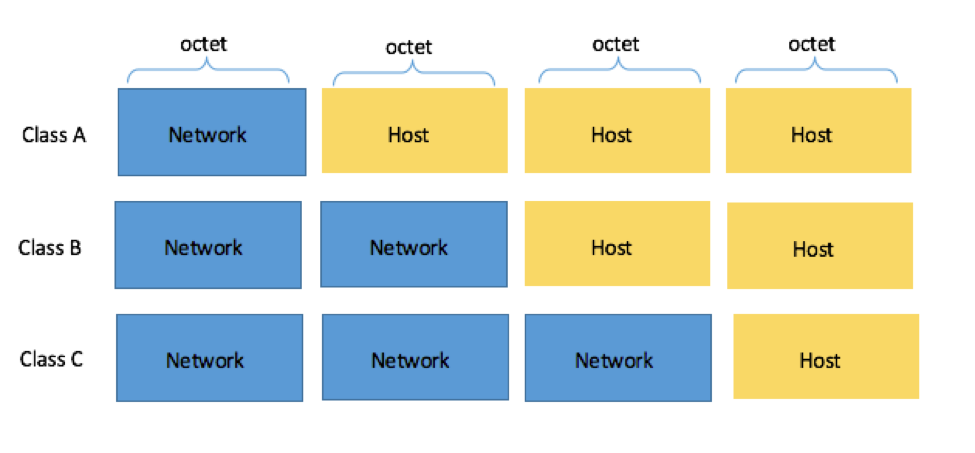
Note that there are class D and E IP addresses, but we'll go into these in more detail a bit later.
Classful IP addresses gave network engineers a way to provide different organizations with a range of valid IP addresses.
There were a lot of issues with this approach that eventually lead to subnetting. But before we get into those, let's take a closer look at the different classes.
Class A IP Addresses
For Class A IP addresses, the first octet (8 bits / 1 byte) represent the network ID, and the remaining three octets (24 bits / 3 bytes) are the host ID.
Class A IP addresses range from 1.0.0.0 to 127.255.255.255 , with a default mask of 255.0.0.0 (or /8 in CIDR).
This means that Class A addressing can have a total of 128 (2 7 ) networks and 16,777,214 (2 24 -2) usable addresses per network.
Also, note that the range 127.0.0.0 to 127.255.255.255 within the Class A range is reserved for host loopback address (see RFC5735 ).
Class B IP Addresses
For Class B IP addresses, the first two octets (16 bits / 2 bytes) represent the network ID and the remaining two octets (16 bits / 2 bytes) are the host ID.
Class B IP addresses range from 128.0.0.0 to 191.255.255.255 , with a default subnet mask of 255.255.0.0 (or /16 in CIDR).
Class B addressing can have 16,384 (2 14 ) network addresses and 65,534 (2 16 ) usable addresses per network.
Class C IP Addresses
For Class C IP addresses, the first three octets (24 bits / 3 bytes) represent the network ID and the last octet (8 bits / 1 bytes) is the host ID.
Class C IP Addresses range from 192.0.0.0 to 223.255.255.255 , with a default subnet mask of 255.255.255.0 (or /24 in CIDR).
Class C translates to 2,097,152 (2 21 ) networks and 254 (2 8 -2) usable addresses per network.
Class D and Class E IP Addresses
The last two classes are Class D and Class E.
Class D IP addresses are reserved for multicasts. They occupy the range from 224.0.0.0 through 239.255.255.255 .
Class E IP addresses are experimental, and are anything over 240.0.0.0 .
The Issue with Classful IP Addresses
The main issue with classful IP addresses is that it wasn't efficient, and could lead to a lot of wasted IP addresses.
For example, imagine that you're part of a large organization back then. Your company has 1,000 employees, meaning that it would fall into class B.
But if you look above, you'll see that a class B network can support up to 65,534 usable addresses. That's way more than your organization would likely need, even if each employee had multiple devices with a unique address.
And there was no way your organization could fall back to class C – there just wouldn't be enough usable IP addresses.
So while classful IP addresses were used around the time IPv4 addresses became widespread, it quickly became clear that a better system would be necessary to ensure we wouldn't use up all of the ~4.2 billion usable addresses.
Classful IP addresses haven't been used since they were replaced by CIDR in 1993, and are mostly studied to understand early internet architecture, and why subnetting is important.
I hope this cheat sheet has been a helpful reference for you
If you found this helpful, please share it with your friends so more people can benefit from it.
Also, feel free to reach out on Twitter and let me know what you think.
Read more posts .
If you read this far, thank the author to show them you care. Say Thanks
Learn to code for free. freeCodeCamp's open source curriculum has helped more than 40,000 people get jobs as developers. Get started
Stack Exchange Network
Stack Exchange network consists of 183 Q&A communities including Stack Overflow , the largest, most trusted online community for developers to learn, share their knowledge, and build their careers.
Q&A for work
Connect and share knowledge within a single location that is structured and easy to search.
How are IP addresses assigned?
How are IP addresses assigned? What if someone from USA and someone from Australia connected to the internet at the same time - how would they not have the same IP address?
- 1 Why is this computer software/hardware related? because, if you mess up with your IP address, you cannot reach Superuser in the first place -- even, to attempt the other questions you might have to post/answer there ;-) – nik Commented Jun 12, 2010 at 10:58
3 Answers 3
Because public IP addresses are not picked at random, they are allocated by your Internet Service Provider ; who in-turn gets a block assigned to them from the next level, and so on to IANA/ICANN . Think of this as, only ICANN give IP addresses YOU cannot :-) In your home or college network usually you would use private IP addresses, and might have statically assigned IPs or let your home router do a private IP allocation. These are not visible (or routed) on the Internet. You will find many people use the IP address 192.168.1.1 at their homes, for example, and yet there is apparently no conflict. This is because their home router 'translates' (very crude use of that word here) to the ISP allocated address -- which is what others on the Internet will see.
You might think of this private IP address as a local reference (like, take that left on the next block to reach the cake shop?) for your home router to find your machine in the home network.
If you tried to use a 'public' IP address at random, the ISP will not accept it and you will see no network connectivity.
Update: If you want to dig deeper on why an ISP might want to check what source IP you are using, read through the interaction in comments here... Or, head straight to Wikipedia Smurf Attack .
In the late 1990s, many IP networks would participate in Smurf attacks (that is, they would respond to pings to broadcast addresses). Today, thanks largely to the ease with which administrators can make a network immune to this abuse, very few networks remain vulnerable to Smurf attacks.
The fix is two-fold: Configure individual hosts and routers not to respond to ping requests or broadcasts. Configure routers not to forward packets directed to broadcast addresses. Until 1999, standards required routers to forward such packets by default, but in that year, the standard was changed to require the default to be not to forward. 3
Another proposed solution, to fix this as well as other problems, is network ingress filtering which rejects the attacking packets on the basis of the forged source address .
Thanks to Andy for making me recall this. You might also be interested in in this ServerFault question by Jeff: Are IP addresses “trivial to forge” ?
- If you try to use a public IP address at random, regardless of anything else, any return packets will end up on the wrong network at the wrong host, so you won't be able to have two-way comms. – Andy Commented Jun 12, 2010 at 11:11
- @Andy, actually the transmitted packets are likely to get dropped themselves. The point is, you cannot convince the ISP network devices to use your choice of IP address. They will not accept it. – nik Commented Jun 12, 2010 at 11:47
- @nik Totally! I focus on the return path because for me, whether or not your outgoing packet is dropped is a detail (maybe it will, maybe it won't); the fundamental reason you can't use an arbitrary IP address is that you break the routing system, which shows up on the return journey. – Andy Commented Jun 12, 2010 at 12:07
- @Andy, Umm, the packet with this 'spoofed' source IP will be dropped -- So, analysis of return path is really just theoretical musing. Look at the ifconfig (or ipconfig on Windows) output of your Internet connected machine. You will see two more things associated with your IP address: a subnet mask and a default gateway ip address. Think about what you will setup as the default gateway if you were to change your IP address say from ' a.x.y.z ' to ' b.x.y.z '. Changing it won't work. Now, think further on what that gateway machine will do to your changed-source-IP packet... – nik Commented Jun 12, 2010 at 12:45
- @Nik Don't see the problem. Sure if you spoof as a.b.c.d/24 and access a.b.c.d+1/24 you'll have problems. But as long as the dest appears to be in a different subnet, the default gateway'll be used, and once we're at routers, only the dest addr is used no? (I don't get your problem with the gateway machine.) We can modify our subnet mask to make (nearly) all addresses appear to be on a different subnet. Or just configure our host to send all packets to the default gateway. That's why I feel it's details - it's absolutely impossible for the return packets to find you. Have I missed something? – Andy Commented Jun 12, 2010 at 14:19
The assignment of addresses is managed in a hierarchal fashion. At the top of the chain is
Internet Assigned Numbers Authority
They are responsible for the global pool from which they allocate blocks to the
Regional Internet Registries
who are responsible for specific regions of the world. They in turn, allocate from their blocks, to the
Local Internet Registries
or if you prefer Internet Service providers.
Because of the way the address blocks are allocated every global Internet address is unique.
IP addresses are assigned by ICANN, so that won't happen. But there's also a more fundamental reason. IP addresses are used for routing. When a packet comes into a router, it compares the IP address against entries in its routing table, and sends the packet on through the appropriate outgoing line. So IP addresses aren't just arbitrary numbers that are assigned - they are meaningful addresses.
You must log in to answer this question.
Not the answer you're looking for browse other questions tagged internet ..
- The Overflow Blog
- The hidden cost of speed
- The creator of Jenkins discusses CI/CD and balancing business with open source
- Featured on Meta
- Announcing a change to the data-dump process
- Bringing clarity to status tag usage on meta sites
Hot Network Questions
- Basel FRTB Vega Sensitivity for Market Risk Capital Standardised Approach
- What's the purpose of scanning the area before opening the portal?
- Starting with 2014 "+" signs and 2015 "−" signs, you delete signs until one remains. What’s left?
- How cheap would rocket fuel have to be to make Mars colonization feasible (according to Musk)?
- I'm a little embarrassed by the research of one of my recommenders
- What are the most common types of FOD (Foreign Object Debris)?
- Understanding the parabolic state of a quantum particle in the infinite square well
- Does a party have to wait 1d4 hours to start a Short Rest if no healing is available and an ally is only stabilized?
- Is there a way to read lawyers arguments in various trials?
- What was the typical amount of disk storage for a mainframe installation in the 1980s?
- How to raise and lower indices as a physicist would handle it?
- Could they free up a docking port on ISS by undocking the emergency vehicle and letting it float next to the station for a little while
- How to fold or expand the wingtips on Boeing 777?
- How to connect 20 plus external hard drives to a computer?
- An assertion of Mahler
- Generating function for A261041
- Do US universities invite faculty applicants from outside the US for an interview?
- Beatles reference in parody story from the 1980s
- Why isn't a confidence level of anything >50% "good enough"?
- Setting the desired kernel in GRUB menu
- How high does the ocean tide rise every 90 minutes due to the gravitational pull of the space station?
- Is reading sheet music difficult?
- Is this host and 'parasite' interaction feasible?
- What qualifies as a Cantor diagonal argument?
Stack Exchange Network
Stack Exchange network consists of 183 Q&A communities including Stack Overflow , the largest, most trusted online community for developers to learn, share their knowledge, and build their careers.
Q&A for work
Connect and share knowledge within a single location that is structured and easy to search.
How are IP addresses actually assigned?
I'm having a hard time understanding how a governing body assigns IP addresses, companies use BGP to advertise those IPs, and how the internet works. Then, where the hell does DNS come in?
Can anyone suggest a good read of how this stuff actually works? I suppose I have several questions. The first is, does ARIN (or any other governing body) actually matter? If they weren't around, would there be chaos? When they assign a block, they don't LITERALLY assign it? You have to use BGP to advertise, correct? I have always been used to a closed hosting environment (dedicated/shared) where you have routed IPs.
Then, how does DNS come in to play? With my registrar I am able to register a DNS server (eNom) - what does that actually mean? I've installed Bind and made all of that work, and I run my own DNS servers, but who are they registering that DNS server with? I just don't get it.
I feel like this is something I should know and I don't, and I'm getting really frustrated. It's like.. simple.. how does the internet work? From assigning IPs, to companies routing them, and DNS.
I guess I have an example - I have this IP space let's say 158.124.0.0/16 (example). The company has 158.124.0.0/17 internet facing. (First of all, why do companies get blocks of IPs assigned and then not use them? Why don't they use use reserved internal space 10.x and 192.x?). So, that's where I'm at. What would I do to actually get these IPs on the Internet and available? Let's say I have a data center in Chicago and one in New York. I'm not able to upload a picture, but I can link one here: http://begolli.com/wp-content/gallery/tech/internetworkings.png
I'm just trying to understand how from when the IP block is assigned, to a company using BGP (attaining a public AS #?), and then how DNS comes in to play?
What would something look like from my picture? I've tried to put together a scenario, not sure if I did a good job.
- domain-name-system
- 6 As a professional system administrator, or someone working in a related field, we are expected to know these things. For any bits that may be a little unclear vast numbers of books and Internet articles have already been published. This is also not the kind of question, or set of questions, that can be properly addressed by a Q&A site like SF. – John Gardeniers Commented May 31, 2011 at 22:48
- 2 I don't really have a problem with this question - I look at it the same way as the "Subnetting 101" question & answer: It's something every sysadmin should know, but some may have slipped through without the requisite knowledge. We can't cover it as exhaustively as subnetting, but I think having it as a quick-and-dirty primer is a Good Thing. – voretaq7 Commented Jun 1, 2011 at 15:50
- 1 @John - I think there are many different levels. Like I stated, I grew up learning in a static environment as far as networks went. I never really dealt with ISPs, border routers, and configuring blocks of IPs. I have had the pleasure of having many dedicated servers, configuring linux distributions, securing them, running web applications, and being able to manage those boxes. There are different sides to the spectrum, and I don't think we are expected to know these things. We are expected to know specialized tasks. Some people know networking engineering real well.. others do not. – Vegim Commented Jun 2, 2011 at 16:08
4 Answers 4
Leased ip blocks.
IPs are assigned in blocks by IANA to the Regional Internet Registries (RIR). See this ( list and map ) of the RIRs. The RIRs then lease out smaller blocks IPs to individual companies (usually ISPs). There are requirements (including fees and proof of use) for getting a distribution and failing to maintain these means a loss of lease.
Once a company has leased one or more blocks from the RIR, they need some way of telling the rest of the world where to find a particular IP (or set thereof: subnets). This is where BGP comes into play. BGP uses a large network concept called an Autonomous System (AS). The AS knows how to route within itself. When routing to another network it only knows about AS Gateways and where the "next hop" toward those external addresses. AS numbers are managed by IANA as well.
Within an AS, even one as large as an ISP, they might use several routing protocols (RIP, OSPF, BGP, EIGRP, and ISIS come to mind) to route traffic internally. It's also possible to use Static Routing Tables, but entirely impractical in most applications. Internal routing protocols are a huge topic, so I'll simplify by saying there are other questions on Server Fault that can do those topics more justice than I can here.
Humans don't remember numbers well, so we invented host names. Skipping the history, we use the Domain Naming System (DNS) to keep track of what hostname points to what IP address. There is a central registry for these, also managed by IANA, and they determine what Top Level Domains (TLD) (eg ".com" or ".net") go in the Root Zone, which is served by the Root Servers. IANA delegates administration of the "root zone", this administrator only accepts updates from qualified Registrars.
You can use a Registrar to "purchase" a domain name, which is a subdomain of a TLD. This registration essentially creates that subdomain and assigns you control over it's Name Server (NS) and Glue (A) records. You point these to a DNS server that hosts your domain . When a client wants to resolve your IP from a domain name, the client contacts their DNS server which does a recursive lookup, starting with the root server, finding your DNS server and eventually getting the relevant information.
Everyone Agrees
As for the "governing bodies": everyone just agrees to use them. There are no (or very few) laws requiring anyone to cooperate at all. The Internet works because people choose to cooperate . The governing bodies provide a means of easy cooperation. All the various RFCs, "Standards", and such - nobody is being forced to use them. But we understand that society is built on cooperation, and it's in our own self interests to do so.
The efficiency bred by cooperation is the same reason BGP is popular, everyone basically agrees to use it. In the days of ArpaNet they started with hand configured route tables; then gradually progressed to a more comprehensive system as the Internet grew in complexity, but everyone just "agreed" to use whatever new standard. Similarly name resolution stated with host files that networks would distribute, and eventually grew into the DNS system we know today. ("Agreed" in quotes because many times a minority set a requirement for a new standard and nobody else had a better alternative, so it was accepted).
This level of cooperation requires trusting IANA, a lot. As you've seen they manage most of the various systems' cores. IANA is currently a US Government sponsored Non-Profit corporation (similar to the US Post Office), it is not part of the government, though only barely removed. In past years there was concern that the US Goernment might exercise some control over IANA as a "weapon" against other world governments or civilians (particularly through laws like SOPA and PIPA, which were not passed, but may be the basis for future laws).
Currently IANA has taken it upon themselves to raise funding (despite being a non-profit company) through the creation of new TLDs. The "xxx" TLD was viewed by some as an extortionist-style fundraising campaign, as a large percentage of registrants were "defending" their name. IANA has also taken applications for privately owned TLDs (at $180,000 each; they have suspended the application process after being inundated with applications, nearly half being from Amazon alone. Many of these applications resulted in new gTLDs .
- No problem! Good answer - this will be good to have to point to for people needing the overview. – Shane Madden Commented Jun 1, 2011 at 1:05
- Do you think you could elaborate on the delegations for reverse DNS? This is a great answer that touches on the related subjects already, so adding that info would close the loop on the whole thing. – Andrew B Commented Feb 28, 2015 at 20:59
All advertisements to the public internet, the DFZ (Default-Free Zone), is done via BGP (Border Gateway Protocol), how ISP's do internal routing varies a lot. Most would use BGP internally as well both between their own routers (BGP is often used in conjunction with an IGP such as OSPF) and also with clients, if you don't have your own AS number you can use a private AS to peer with your ISP and when they announce your address space to the DFZ they simply remove the private AS from the as-path. For smaller non-redundant links you can use static routing as well on the PE. The actual "assignment" is just in the database of your registrar, the whois database, RIPE/ARIN etc run their own databases for this purpose.
Try running the command whois 158.124.0.0/16 on a Linux box.
Same goes with DNS, the reverse DNS server is specified in whois records.
This is a very old question, but I had many of the same questions in figuring out how the Internet works . Like the other answers, the networking books give an overview of BGP and DNS but still left me confused. For example, a.root-servers.net through m.root-servers.net are given as the root servers, but how does a DNS service know where to find those servers if they can't use DNS themselves.
The basics of IP, subnetting, DNS, etc. are assumed to be known by this answer. I am addressing "gaps" I, and probably the questioner, have on how the Internet works. By no means am I an expert, but this is my understanding of the gaps.
IP Addresses
The first thing to note is that when the Internet started out as ARPANET, everybody knew everybody and routing tables for IP addresses were handcoded. I assume the assignment process for IP's was done over the phone. As the Internet became too big, BGP was used by multiple networks (AS's) to advertise they had public IP's or could get to a public IP through their AS to another AS. The trust was there that an AS wouldn't advertise an IP they didn't have.
Today, there's not as much trust. Instead, ISP's can download and authenticate the IP allocations to each AS from IANA and the regional authorities. These downloads are now authenticated through public key cryptography. So when IANA "assigns an IP address," they are changing their record (or really the regional authority changes their record). All other AS's can download and authenticate their records.
These records are important because ISP's can't take the word of other ISP's that they have the IP addresses. The ISP's can compare the BGP advertisement with the authenticated IP records. If any BGP advertisement shows the last AS as an AS other than what's in IANA's and RIR's authenticated record, the BGP advertisement does not change their own routing.
More commonly, a rogue ISP or AS can advertise they have a route through their AS they don't have. AS1 has an IP registered and AS5 currently uses AS5 -> AS4 -> AS3 -> AS1 -> IP. AS2 advertises to AS5 a route of AS5 -> AS2 -> AS1 -> IP. Except AS2 doesn't actually have a connection with AS1. It can just lose the packets, maybe to frustrate AS1's hosting customers. Or AS2 could be a small company network with a multihomed arrangement with AS5 and AS1. Their router is misconfigured and advertises a path through a small company network. Nearly all ISP's throw away such advertisements of their BGP customers and only pass on terminating BGP advertisements.
More likely, you have the case of Pakistan trying to shut off Youtube in Pakistan through such IP hijacking, and shutting off Youtube outside of Pakistan too since AS's outside of Pakistan assumed their BGP advertisements were correct.
In the end, there isn't a perfect defense against such IP hijacking. In most countries like the US, such abuse of BGP can be punished as breach of contract and other ISP's will shut off peering connections with that AS if they have to. An ISP could also disregard the whole IANA and RIR apparatus and redirect the IP addresses to their own servers. That won't work for any https sites though, assuming the ISP doesn't have the private keys for any CA's. There is very little to gain from it economically. It only happens with authoritarian governments, such as Egypt recently shutting off all BGP advertisements to their ISP's from outside the country.
DNS Servers
DNS is somewhat simpler once the IP tables are correct. The root servers are all hardcorded IP addresses in the DNS server code. a.root-servers.net is 198.41.0.4 and the IP address is anycast within one AS. In the case of a.root-servers.net, the AS is Verisign and there are five different sites. In the US, the two sites are New York and LA. Anycasting is like if you had an address of 123 Main Street and you said "It doesn't matter what town you are in, go to 123 Main Street and you'll find one of my businesses." Both 123 Main Street in NY and LA will give the same answer for all top-level domains. The AS, in this case Verisign, figures out internally which server has the fewest hops through OSPF, internal BGP, and other routing protocols. So a router in Denver may go to LA while a router in Chicago goes to New York. The same routing process can be used for Anycast hosts because the hosts don't offer to route traffic.
One of the root servers gives which IP address for the com top-level domain. Then that domain gives the domain for yoursite.com. The registrars really have a contract with whoever runs the top-level domain. So if the top-level domain currently doesn't have a record for yoursite.com, it has access to add a record with their who-is server. Then, with the access the registrar gave you to yoursite.com's DNS records, you change the records in their DNS server to go to your IP address.
Because DNS all depends on multiple IP addresses going to the right place, you have the same issue as before with AS's authenticating the IP registry and then the BGP assignments. That is the key piece for an http website. Https has the added protection of certificates. So, an ISP can't reroute requests for their own root servers and top-level domain servers to give their own IP for, say, citibank.com. If they did, the IP address given to the user will be a different IP address, but their server won't have Citibank's private key.
and no, I'm not kidding(I got started with this book 15 years ago, but it's still very relevant): http://www.amazon.com/Internet-Dummies-John-R-Levine/dp/0764506749
Then, come back here with the BGP questions =)
- 2 It looks like the first part of your answer go chopped off somehow. – John Gardeniers Commented Jun 1, 2011 at 1:34
You must log in to answer this question.
Not the answer you're looking for browse other questions tagged networking domain-name-system ip tcpip bgp ..
- The Overflow Blog
- The hidden cost of speed
- The creator of Jenkins discusses CI/CD and balancing business with open source
- Featured on Meta
- Announcing a change to the data-dump process
- Bringing clarity to status tag usage on meta sites
Hot Network Questions
- How to go from Asia to America by ferry
- Can reinforcement learning rewards be a combination of current and new state?
- How does a miner create multiple outputs in a coinbase transaction?
- Is this host and 'parasite' interaction feasible?
- Where is this railroad track as seen in Rocky II during the training montage?
- Information theoretical interpretation of Free Energy
- Is there a way to prove ownership of church land?
- Textile Innovations of Pachyderms: Clothing Type
- What is this phenomenon?
- Why isn't a confidence level of anything >50% "good enough"?
- What was the typical amount of disk storage for a mainframe installation in the 1980s?
- Integrity concerns
- Does a party have to wait 1d4 hours to start a Short Rest if no healing is available and an ally is only stabilized?
- The question about the existence of an infinite non-trivial controversy
- How to raise and lower indices as a physicist would handle it?
- Simulate Minecraft Redstone | Where to start?
- 70s-90s Anime Mecha Movie/Series
- Cardinality of connected LOTS
- What was the first "Star Trek" style teleporter in SF?
- How do I prove the amount of a flight delay in UK court?
- Are fuel efficiency charts available for mainstream engines?
- How is causality in Laplace transform related to Fourier transform?
- Help identifying a board-to-wire power connector
- Best approach to make lasagna fill pan
Your IP Address is: 185.194.105.172
Tip: try using "quotes around your search phrase"
- Executive Board
- Financial Information
- Press Centre
Understanding IP Addressing and CIDR Charts
Every device connected to the Internet needs to have an identifier. Internet Protocol (IP) addresses are the numerical addresses used to identify a particular piece of hardware connected to the Internet.
The two most common versions of IP in use today are Internet Protocol version 4 (IPv4) and Internet Protocol version 6 (IPv6). Both IPv4 and IPv6 addresses come from finite pools of numbers.
For IPv4, this pool is 32-bits (2 32 ) in size and contains 4,294,967,296 IPv4 addresses. The IPv6 address space is 128-bits (2 128 ) in size, containing 340,282,366,920,938,463,463,374,607,431,768,211,456 IPv6 addresses.
A bit is a digit in the binary numeral system, the basic unit for storing information.
Not every IP address in the IPv4 or IPv6 pool can be assigned to the machines and devices used to access the Internet. Some IP addresses have been reserved for other uses, such as for use in private networks. This means that the total number of IP addresses available for allocation is less than the total number in the pool.
Network prefixes
IP addresses can be taken from the IPv4 or the IPv6 pool and are divided into two parts, a network section and a host section. The network section identifies the particular network and the host section identifies the particular node (for example, a certain computer) on the Local Area Network (LAN).
IP addresses are assigned to networks in different sized ‘blocks'. The size of the ‘block' assigned is written after an oblique (/), which shows the number of IP addresses contained in that block. For example, if an Internet Service Provider (ISP) is assigned a “/16”, they receive around 64,000 IPv4 addresses. A “/26” network provides 64 IPv4 addresses. The lower the number after the oblique, the more addresses contained in that “block”.
The size of the prefix, in bits, is written after the oblique. This is called “slash notation”. There is a total of 32 bits in IPv4 address space. For example, if a network has the address “192.0.2.0/24”, the number “24” refers to how many bits are contained in the network. From this, the number of bits left for address space can be calculated. As all IPv4 networks have 32 bits, and each “section” of the address denoted by the decimal points contains eight bits, “192.0.2.0/24” leaves eight bits to contain host addresses. This is enough space for 256 host addresses. These host addresses are the IP addresses that are necessary to connect your machine to the Internet.
A network numbered “10.0.0.0/8” (which is one of those reserved for private use) is a network with eight bits of network prefix, denoted by “/8” after the oblique. The “8” denotes that there are 24 bits left over in the network to contain IPv4 host addresses: 16,777,216 addresses to be exact.
Classless Inter-Domain Routing (CIDR) Chart
The Classless Inter-Domain Routing (CIDR) is commonly known as the CIDR chart and is used by those running networks and managing IP addresses. It enables them to see the number of IP addresses contained within each “slash notation” and the size of each “slash notation” in bits.
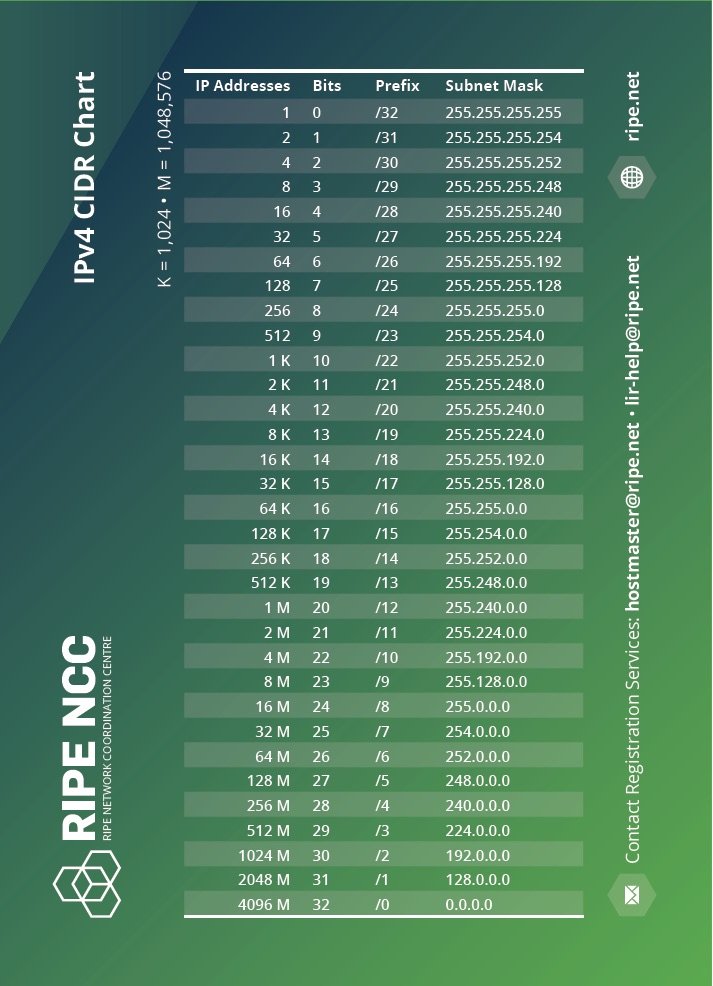
Download: IPv4 CIDR Chart (PDF)
IPv6 is similar to IPv4, but it is structured so that all LANs have 64 bits of network prefix as opposed to the variable length of network prefix (RFC2526, Reserved IPv6 Subnet Anycast Addresses (Proposed Standard)) that IPv4 networks have. All IPv6 networks have space for 18,446,744,073,709,551,616 IPv6 addresses.
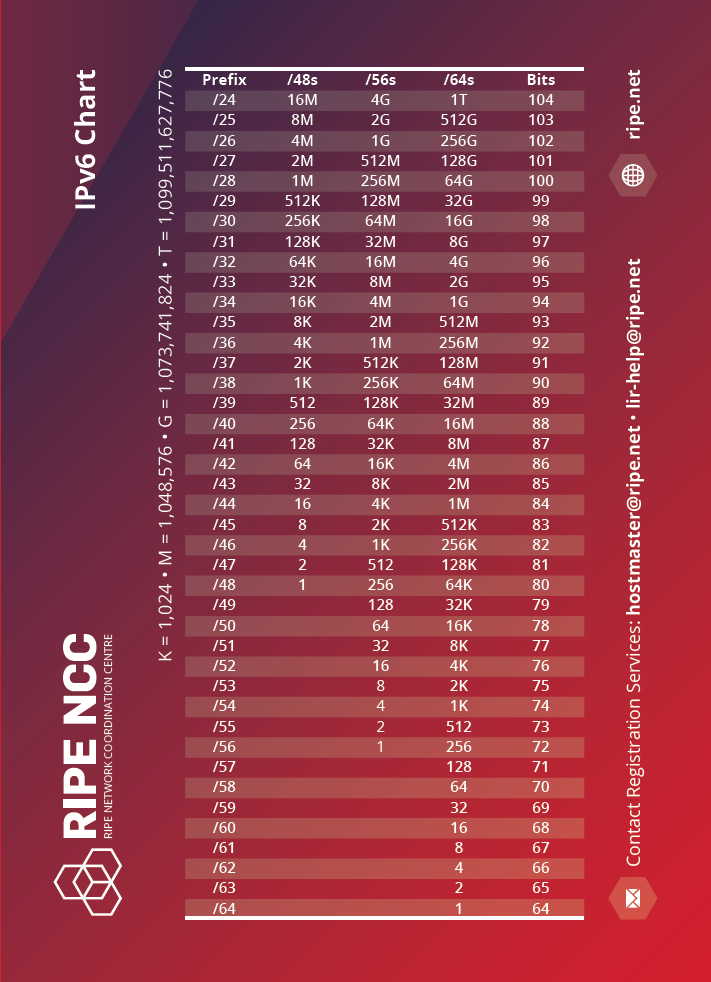
Download: IPv6 Chart (PDF)
Currently, most ISPs assign /48 network prefixes to subscribers' sites (the End Users' networks). Because all IPv6 networks have /64 prefixes, a /48 network prefix allows 65,536 LANs in an End User's site.
The current minimum IPv6 allocation made by the RIPE NCC is a /32 network prefix. If the LIR only made /48 assignments from this /32 network prefix, they would be able to make 65,536 /48 assignments. If they decided to only assign /56 network prefixes they would have 24 bits available to them, and so could make 16,777,216 /56 assignments.
For example, if a /24 IPv6 allocation is made to an LIR, it would be able to make 16,777,216 /48 assignments or 4,294,967,296 /56 assignments.
To give some perspective, it is worth noting that there are 4,294,967,296 IPv4 addresses in total, significantly less than the number of IPv6 addresses.
IPv6 Relative Network Sizes
A Short Guide to IP Addressing
How are ip addresses managed and distributed.
IP addresses are managed by the Internet Assigned Numbers Authority (IANA), which has overall responsibility for the Internet Protocol (IP) address pool, and by the Regional Internet Registries (RIRs) to which IANA distributes large blocks of addresses.
The RIRs manage, distribute, and publicly register IP addresses and related Internet number resources, such as Autonomous System Numbers (ASN) and reverse Domain Name System (DNS ) delegations within their respective regions. They do this according to policies which are developed within their respective regional communities, through open and bottom-up processes.
There are currently five RIRs:
- AfriNIC – African region
- APNIC – Asia Pacific region
- ARIN – North America and several Caribbean and North Atlantic islands
- LACNIC – Latin America and the Caribbean
- RIPE NCC – Europe, the Middle East, and parts of Central Asia
The five RIRs together also form the Number Resource Organization (NRO), which carries out joint activities of the RIRs, including joint technical projects, liaison activities, and policy co-ordination. For more background on IP address management visit:
- IANA’s Overview of IP Address Services
- Development of the Regional Internet Registry System , an article published in Cisco’s Internet Protocol Journal
How are IPv6 addresses allocated?
Both IPv4 and IPv6 addresses are allocated to those who show that they need addresses for their networks.
Shouldn’t addresses be allocated on a geographical basis to ensure that distribution is equitable?
For technical reasons the allocation of IP addresses has to follow the topology of the network and not geography or national borders.
Therefore, the addresses are allocated for use in specific networks, as they are required. RIRs allocate IP addresses using community-developed policies that are designed to ensure that distribution is fair and equitable.
In the early days of the Internet, the method for distributing IP addresses was less formal, resulting in some organisations receiving disproportionately large address ranges.
The RIRs were formed to provide a better way of distributing addresses. They have been successful at developing fair and equitable distribution policies. They have also helped to provide stability of the address pool and routing tables throughout a long period of rapid growth.
What happens when IPv4 addresses run out?
The Internet, in its current form, already has. According to the Number Resource Organization, the world officially ran out of IPv4 addresses in February 2011 .
The only option now is to divide the allocated properties into smaller portions or to start trading what’s already been assigned – both moves could complicate and compromise your privacy.
Did you find this resource helpful? By donating any amount, you help fund more research and content like this.
Related resources, ipv6 security for ipv4 engineers.
This document provides an overview of IPv6 security that is specifically aimed at IPv4 engineers and operators. Rather than...
IPv6 Security Frequently Asked Questions (FAQ)
Executive Summary The Internet Society recognises that global deployment of the IPv6 protocol is paramount to accommodate the present...
State of IPv6 Deployment 2018
IPv6 deployment continues to increase around the world. In the six years since World IPv6 Launch levels...
- Standards & Protocols
- Data Center
- Unified Communications

Enterprise Networking Planet content and product recommendations are editorially independent. We may make money when you click on links to our partners. Learn More .
Table of Contents
What is an IP address?
An Internet Protocol (IP) address is like a phone number for your computer. Just like you need to dial a phone number to reach someone, your computer (or computing device, such as a smartphone or tablet) needs an IP address to reach other devices on the network.
The history of IPv4 dates back to the early 1980s when the internet was a private network solely used by the military. Despite its initial intended purpose, it quickly grew in popularity, leading to an eventual shortage of IPv4 addresses due to all the different networks and devices now accessing the internet.
The total pool of 4.3 billion IPv4 addresses initially seemed like ample amounts; however, this figure quickly proved incapable of meeting demands. The depletion of available IPv4 began as early as the 1990s. Clever technical networking tricks have managed to delay this exhaustion and allow us access to IPv4 transactions even today.
IPv6 is the most recent variation of the Internet Protocol, granting more computer systems and devices access to the internet than ever before. IPv6 is designed to enable routing only within a local area network (LAN) or subnetwork.
How IP addressing works
There are two types of IP addresses, IPv4 and IPv6, and they work a little differently from each other—specifically, IPv4 is a 32-bit address while IPv6 is 128 bits.
IPv4 addressing
IPv4 uses 32 bits, and its address format is usually a unique string of numbers and letters that looks something like this: 123.123.123.123. Each IP address comprises four sets of numbers separated by periods, each ranging from 0 to 255.
IPv4 addresses are composed of two parts: the network ID and the host ID. The network ID identifies the network a device is connected to, while the host ID identifies a specific device on that network.
The network ID is typically expressed in dotted decimal notation, which is a series of three numbers separated by dots. Each number can range from 0 to 255, forming an 8-bit binary number. The host ID is also expressed in dotted decimal notation, but it can be any combination of numbers up to 32 bits long.
For example, take the IP address 192.168.1.20.
The first part, 192.168.1, represents the network ID, while the last part, 20, represents the device ID.
Usually, a device ID 1 is allocated to the router while subsequent numbers 2 and onwards are used to identify other devices on the network.
Together, these two parts make up an IPv4 address and allow devices to communicate with each other over the internet. By knowing both the network ID and host ID, devices can send and receive data from one another without knowing each other’s exact location or IP address.
IPv6 addressing
Like IPv4, an IPv6 address is made up of two distinct parts: a network component and a participant/node component. However, IPv6 uses 128 bits for its address instead of the 32 bits allowed by IPv4. This provides users with a much greater range of addresses than IPv4, enabling every device to have a unique address.
Represented in hexadecimal format, each IPv6 address includes eight groups separated by colons. For example, 2620:0aba2:0d01:2042:0100:8c4d:d370:72b4.
6 types of IP addresses
Within the two types of IPv4 and IPv6 addresses, there are also several other classifications to be aware of: internal versus external IPv4, static versus dynamic IP addresses, and special address formats for particular purposes.
Internal IPv4 addresses (local/private)
Internal IPv4 addresses are used for private networks, such as LANs. They’re not visible on the public internet; only devices connected to the same subnetwork can see each other’s internal IP address. These IP addresses generally start with 192.168.x.x, 10.0.x.x, or 172.16-31.x.x and cannot be accessed from directly outside the network. In other words, they are not globally routable.
External IPv4 addresses (public)
External IPv4 addresses are used to connect to the public internet and make websites available on the World Wide Web. They’re assigned by internet service providers (ISPs) and are usually dynamic, meaning they can change over time. They do not start with 192.168 or 10.0, as these numbers signify private IP addresses. Being public IP addresses means they’re globally routable.
Static IP addresses
A static IP address remains constant over time, allowing for a more reliable connection on the network. This type of address is beneficial when computers need to access the same resource regularly, such as remote desktop access and file sharing between devices. Static IPs remain unchanged until manually changed by an administrator.
Dynamic IP addresses
A dynamic IP address changes each time you connect to a new network. This type of address is beneficial for reducing the amount of IP address space needed from the ISP, as well as providing a more secure connection. Dynamic IP addresses are assigned to each computer or device on the network when they join it. External IP addresses are almost always dynamic.
Special IP addresses
Special IP addresses are used to identify particular services, such as servers, web hosting, and other uses. These special-use IP addresses include the IANA IPv4 Special-Purpose Address Registry, loopback addresses, wildcard addresses, multicast addresses, limited broadcasts, and directed broadcasts.
IANA IPv4 Special-Purpose Address Registry
IANA IPv4 Special-Purpose Address Registry is a registry managed by the Internet Engineering Task Force (IETF) for protocol assignments in the address block of 192.0.0.0/24. It consists of all the current IETF assignments from this particular address block and provides a convenient centralized database for tracking protocol assignment usage. It’s an important resource for those needing special-purpose IP addresses, as it provides easy access to the latest updates and provides information about IETF-assigned protocol assignments.
Loopback address
A loopback address is a special IP address that serves as a virtual interface, allowing your computer to connect to itself. It’s usually used for testing or diagnostics purposes, such as checking network configurations and running programs that require two or more network connections simultaneously. On IPv4, this address ranges from 127.0.0.1 to 127.255.255.255.
Wildcard address
A wildcard address is a special IP address that matches any host or domain name, allowing for a broad range of access from the same source IP address. It’s commonly used for websites and applications needing multiple services from the same IP address. Wildcard addresses are usually in the form of an asterisk (*) followed by a number or string that matches any IP address.
Multicast address
A multicast address is a special type of IP address used for sending data to multiple computers on a network simultaneously. It’s a helpful tool for sending large files, such as multimedia streams and video, as it reduces bandwidth usage by sending the same data stream to multiple computers at once. Multicast addresses range between 224.0.0.1 and 239.255.255.255 on IPv4 networks.
Limited broadcast
A limited broadcast is a special type of IP address used to send data to a specific subnet. It’s used to find the gateway address on a network or to send messages out to all hosts within a certain range. Limited broadcasts are usually in the form of an IP address with all 255s in the last octet.

Directed broadcast
A directed broadcast is a special type of IP address used to send data to all computers on an external network. It’s usually used for network administration, such as notifying all computers on the network about a change in configuration or retrieving information from multiple sources.
Different formats of IPv6 addresses
Since IPv6 addresses consist of 128 bits (in contrast to IPv4’s 32 bits), they allow for much greater variation and flexibility than IPv4. Three of the most common types of IPv6 addresses are global unicast, link local, and unique local addresses.
Global unicast address
Global unicast addresses are globally unique IP addresses assigned to a single interface or host. These addresses are used for communication between two systems over the public internet, or within a private network. Global unicast addresses are structured in eight 16-bit blocks, each separated by a colon (e.g., 2001:0db8:0000:0000:0000:ff00:0042:8329).
Link-local address
Link-local addresses are used for communication between nodes on the same local link or subnet. Link-local addresses are not routable over the public internet but can be used within a private network. Link-local addresses start with fe80::/10 and have a 64-bit interface identifier appended at the end (e.g., fe80::d3b0:f2f7:a5b1).
Unique local address
Unique local addresses (ULAs) are similar to global unicast addresses, but they are only intended for use within private networks and cannot be routed over the public internet. ULAs start with fc00::/7 and have a 40-bit randomly generated interface identifier appended at the end (e.g., fd37:6c82:f9a5::1).
How to find your IP address
Knowing your IP address can be useful in many different ways, from troubleshooting network issues to accessing geo-restricted content. Here’s how you can look up your IP address on Mac and Windows computers.
How to find your IP address on a Mac (OS X 10.5 and later)
There are two methods for finding your IP address on macOS devices: through your System Preferences, or in your macOS Terminal.
How to find your IP address in macOS using System Preferences
- Go to the Apple menu and select System Preferences.
- Click on Network.
- Select your active network connection, such as AirPort or Ethernet, from the list on the left.
- Your IP address will be displayed in the IPv4 Address field to the right.
How to find your IP address in macOS Terminal
- Open the Terminal application located in Applications > Utilities.
- For Ethernet: ipconfig getifaddr en1
- For Wi-Fi: ipconfig getifaddr en0
- For public IP address: curl ifconfig.me
- The command will return your IP address.
How to find your IP address on Windows 11
On Windows, you can find your IP address in your system settings, or via command prompt.
- How to find your IP address in your Windows Settings
- Open the Settings app.
- Click on Network & internet.
- Click Properties, and scroll down to see your IP address.
How to find your IP address in Windows using Command Prompt
- Open the Command Prompt by typing cmd into the Windows search bar.
- To find your public IP address, type nslookup myip.opendns.com. resolver1.opendns.com into the Command Prompt and press Enter.
- Your IP address will be listed under IPv4 Address.
How to find your IP address on any device
The fastest and easiest way to find your public IPv4 or IPv6 address is simply to fire up Google, type in “my ip,” and click search.
Why you might want to know your IP address
One of the most common reasons you would want to find your IP address is to troubleshoot network issues. Your IP address can help you identify problems with your internet connection or router, as well as help diagnose any technical issues you may be having with other devices on the same network.
You may also want to access geo-restricted content. Many websites and streaming services use your IP address to determine where you are located and block access if you’re outside their allowed area. Knowing your IP address can help you bypass these restrictions by using a virtual private network (VPN) .
In addition, knowing your IP address is necessary when setting up new devices on your network. For example, when configuring a wireless printer or router, you must know the IP address to connect it properly.
Further, if you need to access a device remotely over the internet, you’ll need to know its IP address and your own to configure the connection.
Finally, some people are just curious. It’s always interesting to know more about how the internet works, and understanding what an IP address is and how it functions can be a great way to learn more about the technology behind it all.
IP address security threats
IP address information is valuable to cybercriminals, as it can be used to track and target you or your business. Some of the main security threats include tracking and online stalking, spoofing, hacking your devices, or attacking your network.
- Tracking and online stalking: Criminals or people/entities with nefarious intentions can use IP address information to find out where you are geographically located and use other services to determine your identity or even where you live.
- Spoofing: Spoofing attacks are when a cyber attacker creates data packets with a false IP source address in order to trick the firewall or receiver into believing it’s safe.
- Hacking your devices: Knowing your IP address can allow malicious actors to identify vulnerabilities in your device and attempt to gain access or even seize control.
- Attacking your network: Cybercriminals can also use IP addresses to target a group of devices, such as a home network or business servers, in an attempt to gain access and carry out malicious activities. Knowing the IP addresses of an organization is also a prelude to a DDoS attack .
Many of these risks can be mitigated by using a virtual private network (VPN) or taking other security measures, such as regularly changing your IP address and maintaining an effective, advanced firewall .
Bottom line: Understanding IP addresses
IP addresses are an integral component of the internet and how it functions. It’s important to understand the basics of how IP addresses work and the different types of IP addresses.
Knowing your own IP address can come in handy for purposes as diverse as gaming, setting up remote access, or troubleshooting network issues.
It’s also important to be aware of the potential security threats associated with having an active IP address and take the necessary steps to mitigate the risks.
Using a virtual private network (VPN) to hide your IP address can help protect your network and let you browse more freely. Here’s a guide to the top VPN services available today.

Related Articles
Top 9 enterprise wi-fi solutions for businesses in 2024, what is a router in networking core function explained, what is optical networking complete explanation, get the free newsletter.
Subscribe to Daily Tech Insider for top news, trends, and analysis.
Latest Articles
9 best network switches for 2024: speed and features compared, 8 best firewalls for small & medium business (smb) networks, top 10 mobile security threats for devices, networks, and apps — and how to prevent them, follow us on social media, explore more.

Blog Post View
How are ip addresses assigned.

When you're connected to a network, your computer or smart device will obtain an IP address either from your ISP or your router. There are 2 ways how you can assign an IP address to your device: (1) dynamically via DHCP or (2) statically by manually assigning an IP address yourself. In either case, you must use the IP address that is provided to you by your ISP, or the IP range you allocated yourself within your private space (i.e. private IP address).
How are IP addresses allocated?
Before we can discuss IP assignment, we need to understand how IP addresses are allocated. There are two versions of IP addresses: IPv4 (version 4) and IPv6 (version 6). There are numerical differences , but they essentially serves the same purpose by uniquely identifying a device on the Internet. There are a few organizations that allocate and manage IP addresses globally, and they are:
- ICAAN (The Internet Corporation for Names & Numbers): ICANN manages supply of all IPv4 and IPv6 addresses as well as domain name system ( DNS ) and Root Servers.
- IANA (Internet Assigned Numbers Authority): IANA is a part of ICANN that maintains technical aspect of the DNS. DNS is the system that translates human-readable domain names to machine friendly IP addresses.
- ARIN (American Registry for Internet Numbers): ARIN is a region specific organization that manages IP addresses for the USA, Canada, Caribbean and North Atlantic islands.
- ISP (Internet Service Providers): ISPs reach out to ARIN and register blocks of IP addresses (i.e. class A, B and C). In addition to ISPs, large corporations may reach out to ARIN to register blocks of IP address for their corporate use.
- RIR (Regional Internet Registry): Much like the ARIN for managing IP address for North American region, RIR manages IP addresses for rest of the world.
As ARIN and RIR manages IP addresses for the region, they allocate and deallocate IP addresses for countries, ISPs and corporations. A larger blocks of IP addresses are assigned to countries, the accuracy of IP location for country level is approximately 95% - 98% depending on the provider.
Once one or more blocks of IP addresses are assigned to an ISP or Corporation, the organization assigns the IP address to its customers. When you purchase the Internet Service from an ISP, you have an option to obtain static (non-changing) or dynamic (changing) IP Address(es). Most home users obtain a dynamic IP address, and small businesses may obtain static IP addresses. The IP addresses obtained from an ISP are "public" IP addresses which are a globally unique number within the Internet.
Once the IP address is obtained by your router from your ISP, you have an option to create a private network by assigning private IP addresses to your devices that are not globally unique, but unique within your private network.
IP addresses are governed by ICANN, and ARIN and RIR are responsible for allocating IP addresses to ISPs and Corporations within its regions. IANA manages DNS for translating domain names to IP addresses. The IP addresses are then assigned to individuals or small businesses either statically or dynamically via DHCP, and every computing devices on the Internet must have an IP address to communicate with each other.
Share this post
Comments (0), leave a comment.
All comments are moderated. Spammy and bot submitted comments are deleted. Please submit the comments that are helpful to others, and we'll approve your comments. A comment that includes outbound link will only be approved if the content is relevant to the topic, and has some value to our readers.
Reply Comment
Do not sell or share my personal information..
At IPLocation.net, we prioritize the privacy and security of our visitors. We want you to feel confident and comfortable when browsing our website. That's why we want to assure you that we do not sell or share any personal information collected from our website. Your trust is important to us. Whether you're browsing our site for information, or engaging with our content, rest assured that any data you provide remains strictly confidential. We adhere to stringent privacy policies and comply with all relevant regulations to safeguard your information. Your privacy matters, and we are committed to maintaining the highest standards of data protection. If you have any questions or concerns regarding our privacy practices, please don't hesitate to reach out to us.
© 2006 - 2024, Brand Media, Inc. All rights reserved.
ARIN Lookup
About arin lookup.
This test will query the American Registry for Internet Numbers (ARIN) database and tell you who an IP address is registered to. Generally speaking, you will input an IP address and find out what ISP or hosting provider uses that block for its customers. Very large end customers may have there own ARIN allocations. Normally, this is used for finding abuse contacts to report bad behavior.
Understanding IP Address Assignment: A Complete Guide

Introduction
In today's interconnected world, where almost every aspect of our lives relies on the internet, understanding IP address assignment is crucial for ensuring online security and efficient network management. An IP address serves as a unique identifier for devices connected to a network, allowing them to communicate with each other and access the vast resources available on the internet. Whether you're a technical professional, a network administrator, or simply an internet user, having a solid grasp of how IP addresses are assigned within the same network can greatly enhance your ability to troubleshoot connectivity issues and protect your data.
The Basics of IP Addresses
Before delving into the intricacies of IP address assignment in the same network, it's important to have a basic understanding of what an IP address is. In simple terms, an IP address is a numerical label assigned to each device connected to a computer network that uses the Internet Protocol for communication. It consists of four sets of numbers separated by periods (e.g., 192.168.0.1) and can be either IPv4 or IPv6 format.
IP Address Allocation Methods
There are several methods used for allocating IP addresses within a network. One commonly used method is Dynamic Host Configuration Protocol (DHCP). DHCP allows devices to obtain an IP address automatically from a central server, simplifying the process of managing large networks. Another method is static IP address assignment, where an administrator manually assigns specific addresses to devices within the network. This method provides more control but requires careful planning and documentation.
Considerations for Efficient IP Address Allocation
Efficient allocation of IP addresses is essential for optimizing network performance and avoiding conflicts. When assigning IP addresses, administrators need to consider factors such as subnetting, addressing schemes, and future scalability requirements. By carefully planning the allocation process and implementing best practices such as using private IP ranges and avoiding overlapping subnets, administrators can ensure smooth operation of their networks without running out of available addresses.
IP Address Assignment in the Same Network
When two routers are connected within the same network, they need to obtain unique IP addresses to communicate effectively. This can be achieved through various methods, such as using different subnets or configuring one router as a DHCP server and the other as a client. Understanding how IP address assignment works in this scenario is crucial for maintaining proper network functionality and avoiding conflicts.
Basics of IP Addresses
IP addresses are a fundamental aspect of computer networking that allows devices to communicate with each other over the internet. An IP address, short for Internet Protocol address, is a unique numerical label assigned to each device connected to a network. It serves as an identifier for both the source and destination of data packets transmitted across the network.
The structure of an IP address consists of four sets of numbers separated by periods (e.g., 192.168.0.1). Each set can range from 0 to 255, resulting in a total of approximately 4.3 billion possible unique combinations for IPv4 addresses. However, with the increasing number of devices connected to the internet, IPv6 addresses were introduced to provide a significantly larger pool of available addresses.
IPv4 addresses are still predominantly used today and are divided into different classes based on their range and purpose. Class A addresses have the first octet reserved for network identification, allowing for a large number of hosts within each network. Class B addresses reserve the first two octets for network identification and provide a balance between network size and number of hosts per network. Class C addresses allocate the first three octets for network identification and are commonly used in small networks.
With the depletion of available IPv4 addresses, IPv6 was developed to overcome this limitation by utilizing 128-bit addressing scheme, providing an enormous pool of potential IP addresses - approximately 3.4 x 10^38 unique combinations.
IPv6 addresses are represented in hexadecimal format separated by colons (e.g., 2001:0db8:85a3:0000:0000:8a2e:0370:7334). The longer length allows for more efficient routing and eliminates the need for Network Address Translation (NAT) due to its vast address space.
Understanding these basics is essential when it comes to assigning IP addresses in a network. Network administrators must consider various factors such as the number of devices, network topology, and security requirements when deciding on the IP address allocation method.
In the next section, we will explore different methods of IP address assignment, including Dynamic Host Configuration Protocol (DHCP) and static IP address assignment. These methods play a crucial role in efficiently managing IP addresses within a network and ensuring seamless communication between devices.
Methods of IP Address Assignment
IP address assignment is a crucial aspect of network management and plays a vital role in ensuring seamless connectivity and efficient data transfer. There are primarily two methods of assigning IP addresses in a network: dynamic IP address assignment using the Dynamic Host Configuration Protocol (DHCP) and static IP address assignment.
Dynamic IP Address Assignment using DHCP
Dynamic IP address assignment is the most commonly used method in modern networks. It involves the use of DHCP servers, which dynamically allocate IP addresses to devices on the network. When a device connects to the network, it sends a DHCP request to the DHCP server, which responds by assigning an available IP address from its pool.
One of the key benefits of dynamic IP address assignment is its simplicity and scalability. With dynamic allocation, network administrators don't have to manually configure each device's IP address. Instead, they can rely on the DHCP server to handle this task automatically. This significantly reduces administrative overhead and makes it easier to manage large networks with numerous devices.
Another advantage of dynamic allocation is that it allows for efficient utilization of available IP addresses. Since addresses are assigned on-demand, there is no wastage of unused addresses. This is particularly beneficial in scenarios where devices frequently connect and disconnect from the network, such as in public Wi-Fi hotspots or corporate environments with a high turnover rate.
However, dynamic allocation does have some drawbacks as well. One potential issue is that devices may receive different IP addresses each time they connect to the network. While this might not be an issue for most users, it can cause problems for certain applications or services that rely on consistent addressing.
Additionally, dynamic allocation introduces a dependency on the DHCP server. If the server goes down or becomes unreachable, devices will not be able to obtain an IP address and will be unable to connect to the network. To mitigate this risk, redundant DHCP servers can be deployed for high availability.
Static IP Address Assignment
Static IP address assignment involves manually configuring each device's IP address within the network. Unlike dynamic allocation, where addresses are assigned on-demand, static assignment requires administrators to assign a specific IP address to each device.
One of the main advantages of static IP address assignment is stability. Since devices have fixed addresses, there is no risk of them receiving different addresses each time they connect to the network. This can be beneficial for applications or services that require consistent addressing, such as servers hosting websites or databases.
Static assignment also provides greater control over network resources. Administrators can allocate specific IP addresses to devices based on their requirements or security considerations. For example, critical servers or network infrastructure devices can be assigned static addresses to ensure their availability and ease of management.
However, static IP address assignment has its limitations as well. It can be time-consuming and error-prone, especially in large networks with numerous devices. Any changes to the network topology or addition/removal of devices may require manual reconfiguration of IP addresses, which can be a tedious task.
Furthermore, static allocation can lead to inefficient utilization of available IP addresses. Each device is assigned a fixed address regardless of whether it is actively using the network or not. This can result in wastage of unused addresses and may pose challenges in scenarios where addressing space is limited.
In order to efficiently allocate IP addresses within a network, there are several important considerations that need to be taken into account. By carefully planning and managing the allocation process, network administrators can optimize their IP address usage and ensure smooth operation of their network.
One of the key factors to consider when assigning IP addresses is the size of the network. The number of devices that will be connected to the network determines the range of IP addresses that will be required. It is essential to accurately estimate the number of devices that will need an IP address in order to avoid running out of available addresses or wasting them unnecessarily.
Another consideration is the type of devices that will be connected to the network. Different devices have different requirements in terms of IP address assignment. For example, servers and other critical infrastructure typically require static IP addresses for stability and ease of access. On the other hand, client devices such as laptops and smartphones can often use dynamic IP addresses assigned by a DHCP server.
The physical layout of the network is also an important factor to consider. In larger networks with multiple subnets or VLANs, it may be necessary to segment IP address ranges accordingly. This allows for better organization and management of IP addresses, making it easier to troubleshoot issues and implement security measures.
Security is another crucial consideration when allocating IP addresses. Network administrators should implement measures such as firewalls and intrusion detection systems to protect against unauthorized access or malicious activities. Additionally, assigning unique IP addresses to each device enables better tracking and monitoring, facilitating quick identification and response in case of any security incidents.
Efficient utilization of IP address ranges can also be achieved through proper documentation and record-keeping. Maintaining an up-to-date inventory of all assigned IP addresses helps prevent conflicts or duplicate assignments. It also aids in identifying unused or underutilized portions of the address space, allowing for more efficient allocation in the future.
Furthermore, considering future growth and scalability is essential when allocating IP addresses. Network administrators should plan for potential expansion and allocate IP address ranges accordingly. This foresight ensures that there will be sufficient addresses available to accommodate new devices or additional network segments without disrupting the existing infrastructure.
In any network, the assignment of IP addresses is a crucial aspect that allows devices to communicate with each other effectively. When it comes to IP address assignment in the same network, there are specific considerations and methods to ensure efficient allocation. In this section, we will delve into how two routers in the same network obtain IP addresses and discuss subnetting and IP address range distribution.
To understand how two routers in the same network obtain IP addresses, it's essential to grasp the concept of subnetting. Subnetting involves dividing a larger network into smaller subnetworks or subnets. Each subnet has its own unique range of IP addresses that can be assigned to devices within that particular subnet. This division helps manage and organize large networks efficiently.
When it comes to assigning IP addresses within a subnet, there are various methods available. One common method is manual or static IP address assignment. In this approach, network administrators manually assign a specific IP address to each device within the network. Static IP addresses are typically used for devices that require consistent connectivity and need to be easily identifiable on the network.
Another widely used method for IP address assignment is Dynamic Host Configuration Protocol (DHCP). DHCP is a networking protocol that enables automatic allocation of IP addresses within a network. With DHCP, a server is responsible for assigning IP addresses dynamically as devices connect to the network. This dynamic allocation ensures efficient utilization of available IP addresses by temporarily assigning them to connected devices when needed.
When considering efficient allocation of IP addresses in the same network, several factors come into play. One important consideration is proper planning and design of subnets based on anticipated device count and future growth projections. By carefully analyzing these factors, administrators can allocate appropriate ranges of IP addresses for each subnet, minimizing wastage and ensuring scalability.
Additionally, implementing proper security measures is crucial when assigning IP addresses in the same network. Network administrators should consider implementing firewalls, access control lists (ACLs), and other security mechanisms to protect against unauthorized access and potential IP address conflicts.
Furthermore, monitoring and managing IP address usage is essential for efficient allocation. Regular audits can help identify any unused or underutilized IP addresses that can be reclaimed and allocated to devices as needed. This proactive approach ensures that IP addresses are utilized optimally within the network.
The proper assignment of IP addresses is crucial for maintaining network security and efficiency. Throughout this guide, we have covered the basics of IP addresses, explored different methods of IP address assignment, and discussed considerations for efficient allocation.
In conclusion, understanding IP address assignment in the same network is essential for network administrators and technical professionals. By following proper allocation methods such as DHCP or static IP assignment, organizations can ensure that each device on their network has a unique identifier. This not only enables effective communication and data transfer but also enhances network security by preventing unauthorized access.
Moreover, considering factors like subnetting, scalability, and future growth can help optimize IP address allocation within a network. Network administrators should carefully plan and allocate IP addresses to avoid conflicts or wastage of resources.
Overall, a well-managed IP address assignment process is vital for the smooth functioning of any network. It allows devices to connect seamlessly while ensuring security measures are in place. By adhering to best practices and staying updated with advancements in networking technology, organizations can effectively manage their IP address assignments.
In conclusion, this guide has provided a comprehensive overview of IP address assignment in the same network. We hope it has equipped you with the knowledge needed to make informed decisions regarding your network's IP address allocation. Remember that proper IP address assignment is not only important for connectivity but also plays a significant role in maintaining online security and optimizing network performance.
Enhance Online Security: The Ultimate Guide to Conceal Your IP Address
Alternative Methods to Conceal Your IP Address Without a VPN
Maintain Privacy: Learn How to Alter Your IP Address
The Significance of IP Address for Online Security and Privacy
Comprehensive Handbook on VPNs, IP Addresses, and Proxy Servers
The IP Address Governance Regime
To understand the controversy surrounding IPv4 address depletion and transfer markets, some description of current institutional arrangements around address management is necessary. Address assignments are made in a hierarchical fashion. At the top of the hierarchy is ICANN, whose IANA function distributes large blocks of 16,777,216 addresses (known as /8’s) to one of five regional Internet address registries (RIRs). The RIRs then accept applications from organizations with networks that need addresses within their territory. Some larger blocks may be assigned directly to end user organizations, but most will go to Internet service providers who will then re-assign them to their customers.
RIRs were created in the 1990s as the Internet protocols began to be widely adopted. The first Regional Internet Registry, RIPE-NCC , was created in 1991 to serve the European region. In 1995 APNIC was created as the RIR to serve the Asia Pacific region. Both were incorporated as private sector nonprofits. In 1997, parallel to the creation of ICANN, the address administration functions performed by several U.S. government contractors were privatized and placed in the hands of a new nonprofit entity known as the American Registry for Internet Numbers (ARIN) . All three of the RIRs rely on a private sector-based, contractual model of governance.
The creation of the RIRs led to tighter and more formalized address allocation and assignment policies, and more careful registration and tracking policies. Before they were created, however, a large portion of the IPv4 address space had already been assigned or allocated, perhaps as much as half. Many of these “legacy allocations” made before 1997 are still held without any contractual obligations.
A Common Pool Model? The RIRs have developed a consistent ideology about address management policies, which are codified in their own policy documents. Address resources are considered a “ shared public resource ” and the RIRs are considered their “stewards.” Addresses are said to be “loaned” to private users, not sold , and users are not supposed to gain any property rights in an address block they are granted. Although RIRs finance themselves via address-related fees and membership charges, they insist that members are not “buying” addresses but are merely paying the RIR for services associated with administering the address space and its registry. The RIRs formally prohibit assignees from reselling or transferring the addresses directly to other private users. But the line between permitted and not-permitted transfers is gray, not bright and clear. Internet service providers who hold address allocations sell services commercially to their customers, and among these services are fixed IP addresses, with specific charges associated with addresses. Also, when companies with IP address allocations or assignments are merged or acquired, RIRs allow the address resources to be transferred along with ownership of the company.
The RIR ideology of resource stewardship has some similarities to the economic model of a common pool resource . The common pool model is used to govern natural resource use in other contexts, such as unlicensed radio spectrum , forests, water or marine fisheries. Common pool governance is typically employed when two conditions are met: consumption of the resource is rival (i.e., one person’s use or consumption prevents another person from also using/consuming it), and it is difficult to exclude people from appropriating the resource (which makes the model of markets based on private property rights difficult to apply). The task for a governance agency is to regulate appropriation of the resource in a way that maintains its value.
Under certain conditions, common pool governance has very good economic and social properties. Simple, collectively applicable limits on the number of trees one can cut or fish one can remove, for example, conserves the resource pool while maintaining easy access to the resource and very low transaction costs. In the case of unlicensed spectrum, anyone who wants to offer service in an unlicensed wireless band can enter freely without prior permission from regulatory authorities. Appropriation is governed by technical limits on transmission power and protocol specifications, which prevent any single transmitter from hogging too much of the spectrum resource.
Despite the appealing ideology of common resource stewardship that appears to underlay RIR policies, there are major failings in the application of the common pool model to IP address resources. Address consumption is rival, but it is not that difficult to exclude unauthorized people from using them. Under the RIR regimes, appropriation from the common pool is not based on a simple and uniformly applicable appropriation limit, but on complex, expensive, case-by-case administrative procedures. In order to get resources from the address pool, applicants must individually request resources from the RIR and demonstrate their “need.” The RIR does engineering studies of the applicant’s plans and demands a lot of commercially sensitive information. This is more like a central planning regime than classical common pool governance. Under conditions of intense scarcity, such a process is not only costly but inherently inaccurate because of the asymmetry of information between the requestor and the granting agency.
Another crucial difference between the RIR regime and what we normally think of as common pool management is that when IP addresses are not used by those to whom they have been allocated, they do not automatically return into the common pool for use by others. Those who have been allocated or assigned address resources retain exclusivity over an address block regardless of whether they are using the resources. Cumbersome administrative processes are required to move resources from a nonuser to a prospective user. In a true common pool model, the IP address space would work like a gigantic DHCP address pool . Organizations would grab addresses (like catching fish) only when they were actually using them, and as soon as they were not using them the addresses would be released back into the common pool for use by others. That is not how things work. Organizations that have been given IP addresses retain them until they choose to give them up, and users have very weak incentives to return addresses to RIRs. If they don’t give them back, nothing bad happens. If they do give them back, they incur both administrative costs (the cost of altering their records and interacting with the RIR) and opportunity costs (the cost of foregoing future use of the addresses). RIRs’ ability to monitor the actual usage of assignments is limited. Even if they did have perfect information about actual usage and “needs” of applicants, their enforcement powers are weak. They cannot impose financial penalties on organizations; they can only terminate a service contract and threaten never to assign the organization any more addresses. Even this does not directly deprive the users of addresses; it only signals to Internet service providers that the organization is not the legitimate holder of the address block, which may lead ISPs to refuse to route packets to those addresses. Another crucial limitation on RIRs is the large number of legacy address allocations which are held without any contractual obligations. Legacy allocations were made before the RIRs existed, and RIRs lack the authority to recover them until and unless the holders of the address resources voluntarily choose to sign “ Legacy Registry Service Agreements .”
In sum, the RIR regime captures only half, possibly less, of the standard benefits associated with common pool management. It regulates appropriation effectively, but it raises the cost of access and does a very poor job of facilitating reclamation and reuse.
Latent markets and Unused Resources Given the major imperfections in the realization of common pool objectives, it is not surprising to discover latent markets for address resources and underground transfers taking place. In June 2008, for example, an item on eBay appeared offering “IPv4 swamp space – one Class C block (a /24)” for US$ 1,000. The same month, a private sector participant stated publicly on the ARIN Public Policy Mailing list, “I have been aware of people …buying, selling and using subterfuge to obtain IP allocations for as long as I have been in the industry (the past 8 years).” The examples provided by this person are worth quoting at length:
a. Three companies merged into one. For many months after they merged they continued to interact with ARIN as separate entities, obtaining far more IP allocations than they would have been able to as a single entity. Even today, this single entity (which has now recently merged again), interacts with ARIN using two separate, but related entity names and two separate ORG IDs.
b. Every month I run into people who are willing to sell me their /18, /19, /20 for a fee. It is my understanding that such transactions are usually structured so that other [usually worthless] assets or an entire shell entity are included in the sale to pass ARIN scrutiny.
c. For a time, I did work for an entity that had previous bad blood with ARIN… and managed to obtain 3 /18s on the after market. From what I gather, this is not all that unusual.
d. There are consultants out there who, for a fee, guarantee you will get an IP allocation from ARIN. They are able to accomplish [this] because they control a large amount of IP space for entities that they work for, and they SWIP out space from those entities to the entity paying them for the direct allocation. …
e. ARIN members continue to report IP usage by customers that have long since left their network, inflating their actual need and utilization percentages, allowing them to obtain unnecessary allocations from ARIN.
As our analysis of incentives above suggested, reclamation of unused IP addresses should be a weak point in the regime. Empirical evidence supports this expectation. There are strong reasons to believe that a very large part of the allocated IPv4 address space is unused, and thus eligible to be transferred. This is especially true in the North American region. An OECD report cited Geoff Huston, Chief Scientist at APNIC, that 90% of RIR-allocated space is routed while only 40% of legacy space is routed. The same OECD report cites surveys that examine the population of visible IPv4 Internet hosts, and find that “only a low percentage of advertised addresses respond, which could mean that even among routed address space, significant address space is unused.” One study finds that only 3.6% of allocated addresses are actually occupied by visible hosts.
In the legacy allocations especially, it is well known that large swaths of unused address blocks are so underutilized that they can be surreptitiously taken over by spammers, illegal pornographers, or other Internet malefactors with a need to operate under cover. An antispam website from 2004 maintains a long list of hijacked IP address blocks, which includes an entire /8 originally allocated to Halliburton in the 1980s. An article by Ronald F. Guilmette documents how two /16 address blocks, containing tens of thousands of IPv4 addresses, were hijacked from NASA and a small software company and used to facilitate spamming. In these two cases, the address blocks were essentially abandoned, as their delegated users had completely lost track of their status and were not even aware of their appropriation by a third party.
When the Free Pool Runs Out The model of common pool resource management assumes that there are free, unallocated resources in the wild, and the task of the resource manager is to set appropriation rules. The appropriation rules of the RIRs were based on a “justified need” criterion where assessments of “need” were based on simple engineering studies.
As the IPv4 free pool runs out, the justified need approach to IPv4 address management loses its relevance. As the number of unallocated blocks approaches zero, IPv4 addresses can only be acquired through transfers from one holder of address resources to another, not through initial appropriation from a free pool. Traditional need assessment methods are of no relevance in this situation. In the post-free pool world, engineering plans that “justify” the use of a certain number of addresses may or may not justify taking addresses away from someone else. To allocate the resource under these new circumstances, an RIR would have to decide which plan was more important or more valuable, and remove addresses from one user to give them to another. To justify transferring address resources from one user to another, one must make judgments about relative need and the social value of the resource in alternate uses.
The only feasible way to discover how valuable the address resources are in alternate uses is to institute competitive bidding for them. The alternative to competitive bidding is an ongoing series of “beauty contests” in which a centralized agency tries to assess the relative merit of every internet-related business in their region. In addition to more closely scrutinizing existing uses and users, RIRs would also have to give themselves more power to take away resources from parties they decided didn’t really need them, or were needed more by someone else. Such a policy would make RIRs into dictators of who could enter the Internet economy and which business plans were more valuable than others. RIRs lack the authority, the resources and the knowledge to judge relative need and aggressively re-allocate address resources across an entire world region. Also, RIR decisions to take away addresses from one party and give them to another would likely become ensnared in controversies and litigation. Future resource allocation must rely on decentralized judgments about the value of resources by the actual holders of address resources. RIRs should act more as title agencies than resource managers.
Next: A comparative analysis of address transfer policies at the three main RIRs.

Will The Internet Fragment?
“In characteristically rigorous fashion, Mueller’s outstanding book punctures the alarmist myth of Internet fragmentation and helps us to understand what is really at stake as nations and other groups vie for power over the Internet.”
Jack Goldsmith, Harvard Law School
- Settings Profile and security information
Reporting Reassignments
On this page.
Scroll for more
Note: ARIN retired its original email template processor on 3 June 2024 . If you are an ARIN customer who relied on templates to manage your registration records, we encourage you to use our Reg-RWS service. You may also utilize our open-source template processor .
The Big Picture
Before using or designing software to manage records within ARIN’s database, it is important to understand ARIN’s relational database, and how ARIN maintains records and interacts with customers.
IP Address and Autonomous System Number (ASN) Distribution
ARIN is one of five Regional Internet Registries (RIRs). RIRs are nonprofit corporations that administer and issue IP address space and ASNs within defined regions . RIRs receive address space in large blocks from the Internet Assigned Numbers Authority (IANA), and allocate smaller address blocks to organizations within their regions. These organizations then assign IP addresses to consumers.
Allocations vs. Assignments
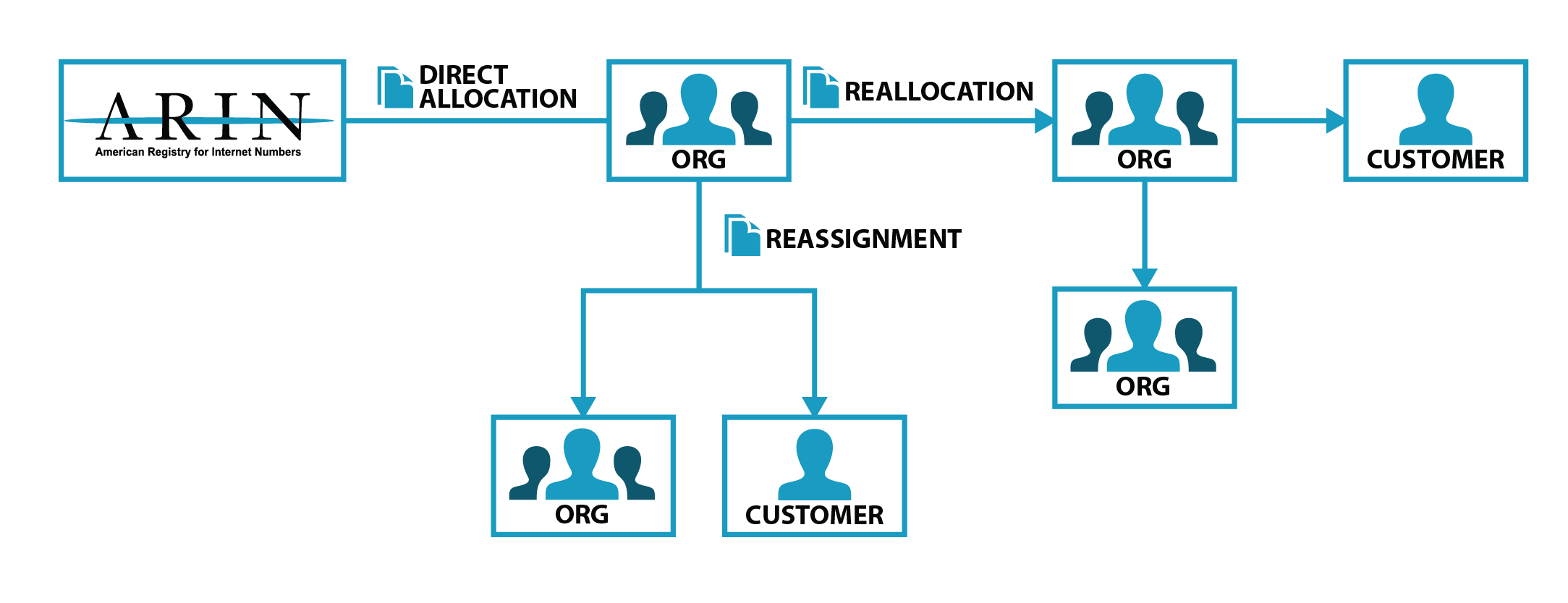
- When ARIN issues a block of IP addresses to a customer planning to issue pieces of that block to its own customers, this is known as an direct allocation or allocation .
When an ARIN customer issues a piece of their allocation to a customer of their own, this is known as a reallocation or reassignment, depending on whether their customer intends to issue pieces of that block to customers of their own (reallocation) or if it is intended for internal use (reassignment).
Note : Reallocations and reassignments may only be made from an allocation.
Autonomous System Numbers (ASNs)
ASNs are assigned individually by ARIN and may not be allocated.
Simple vs. Detailed Reassignments
Simple reassignments are those where the customer does not need to maintain their own in-addr.arpa delegation (reverse name server), display their own Point of Contact information, or divide their address space further among their own customers. A detailed reassignment is one in which the customer does not need to further divide the address space but does need to maintain its own in-addr.arpa delegation and/or display separate Point of Contact information.
Resource Requests
In order for ARIN to properly issue Internet number resources to organizations within its region, those organizations submit a resource request, stating which type of resources they need, and how they intend to use them. ARIN requires that requests include utilization plans, so that ARIN can allocate them fairly among organizations as they continue to expand their networks and customer bases.
Keeping Track of Who Uses What
ARIN maintains a database that contains detailed records of which resources have been allocated and assigned, as well as which organizations and Points of Contact are authoritative over those resource records.
Before You Get Started
Requirements.
When an organization reallocates or reassigns address space, they report reallocation/reassignment information to ARIN. This information is vital, as ARIN makes allocations based on an organization’s utilization history, projected requirements, and other information. While initial allocations may be relatively small, subsequent allocation sizes are scaled based partially on growth shown via reallocation/reassignment information received by ARIN.
ARIN policy requires organizations to submit information for all IPv4 reassignments/reallocations of /29 or more and IPv6 reassignments/reallocations of /47 or more within seven days of the subdelegation. For IPv4 blocks of /30 or less, ISPs may choose to provide utilization data using one of the methods described on this page or manually upon request. There are special reporting requirements for residential cable ISPs and residential customers. Organizations may only submit reassignment data for records within their allocated blocks. ARIN may request reassignment/reallocation information at any time. If the organization does not supply the information, ARIN may withhold future allocations, and in extreme cases, existing allocations may be affected.
Note : Organization Identifiers (Org IDs) containing a -Z are not eligible to receive reallocations/reassignments.
Create an ARIN Online Account
Your first step is to create an ARIN Online account , regardless of the reporting method you intend to use.
Create an API Key
After creating your account and logging in to ARIN Online, you need to create an API key to be able to report reassignment/reallocation information using Registration Restful Service (Reg-RWS). An API key provides a means of secure communication with ARIN.
Create a Point of Contact and Give it Authority
Before reporting reallocation/reassignment data, your ARIN Online account must have the authority to do so. ARIN’s Reg-RWS will not process any modifications to a database record unless you have an ARIN Online account linked to a Point of Contact with proper authority over that record. Visit Creating a Points of Contact for more information.
After you create or find the correct Points of Contact in ARIN’s database, that Point of Contact must be linked to your ARIN Online account. Visit Linking a Point of Contact to Your ARIN Online Account for more information.
Finally, you will need to create or find the appropriate Organization Identifier (Org ID) to add your Point of Contact to it as an Admin and/or Tech Point of Contact. This allows your Point of Contact (and your ARIN Online account) to make changes to ARIN’s database regarding your Org ID and any resources attached to it. Visit Creating an Org ID for more information.
ARIN Customers have three options when it comes to reporting their reallocation/reassignment data: Reg-RWS, Referral Whois (RWhois), and ARIN Online.
Reporting Reallocation/Reassignment Data using Reg-RWS
Reg-RWS is a secure and efficient method for interacting with ARIN’s database and managing your registration records. Reg-RWS is most handy for repetitive, mundane tasks done in high volume with no needed human communication, such as reporting reassignments using the Shared Whois Project (SWIP). Generally, most users of ARIN’s Reg-RWS are engineers who code software that works with the Reg-RWS API to automate large numbers of transactions with the ARIN database. Although Reg-RWS commands can be entered individually into a browser, most users who want to run simple queries or report a few transactions use easier methods such as ARIN Online to do so. More information about this method is available on the Automating Record Management with Reg-RWS page .
Reporting Reallocation/Reassignment Data using RWhois
RWhois is an extension of the original Whois protocol and service. It focuses on the distribution of data representing networks and Points of Contact, and uses the inherently hierarchical nature of these network objects (domain names, IP networks, email addresses) to more accurately discover the requested information. RWhois allows organizations to advertise their reallocation/reassignment from an internal server, rather than actively sending it to ARIN. There are numerous requirements for using this sort of distribution server for reallocation/reassignment information, including 24/7 server functionality, response qualification, and continuity of data. For details, see Section 3.2 of ARIN’s Number Resource Policy Manual (NRPM) . More information about this method is available on the Referral Whois (RWhois) page .
Reporting Reallocation/Reassignment Data using ARIN Online.
Creating reassignments.
To reassign network address space, you have the following options:
Option 1: View free blocks and reassign:
- In ARIN Online, choose IP Addresses > Reassign Addresses from the navigation menu. A list of unassigned address space is displayed. (Note that users with over 11,000 NETS will not see this list. See the note at the end of this section.)
- In the list of networks, choose the network space that you want to reassign.
- Choose the size of the CIDR block to reassign, then choose Reassign .
Option 2: View networks and enter a range to reassign:
- From the Dashboard, under Account Snapshot, choose Networks (NETs) to access the Manage Your Networks page. A list of NETS associated with your account is displayed. (Note that users with over 11,000 NETS will not see a list of associated NETS. See the note at the end of this section.)
- In the list of networks, expand the informational panel for the network portion that you want to reassign by selecting the plus sign located to the right of the Org ID. The actions available to you (depending on permissions and resources) appear under NET Actions .
Tip : Copy the Network Range so that you can easily enter it later in the Reassignment Details screen.
Note for Users With 11,000 or More Associated NETS:
- Choosing IP Addresses > Reassign Addresses will not provide the list of free blocks. You’ll need to enter the IP address in the IP Address Range field in the Reassignment Details page and follow the instructions in the subsequent screens.
- Choosing IP Addresses > Search will not display a list of NETS associated with you. You’ll need to enter an IP address in its entirety and choose Search to display it.
Deleting Reassignments
First, find the network that was reassigned by selecting IP Addresses > Manage Networks from the navigation menu. Search for the reassignment to be deleted. Be sure that you have selected the option to “Include the ### networks you’ve reassigned in your search.”
To delete a reassigned/reallocated NET:
- In the list of search results, expand the informational panel for the NET by selecting the plus sign located to the right of the Org ID.
- Under NET Actions , choose Delete to open the Delete Network page. The page provides information about the reassigned/reallocated space and any additional reassignments contained that were made under the reallocation.
- Choose Delete to remove the NET. Any additional reassignments that were made after the initial reallocation are also removed.
Caution : You can’t undo this deletion.
To remove individual reassignments from a list of reassignments of a space:
- In the list of search results, click the Net Handle to open the Manage Network page for that NET.
- From the Actions button, choose Delete Reassignments . A list of the reassignments is displayed.
- On the Delete Reassignments page, choose an individual network by clicking on the Net Handle .
- On the Manage Network page, choose Delete .
To delete all reassignments under a network:
- From the Actions button, choose Delete Reassignments. A list of the reassignments is displayed.
- Choose Delete All Reassignments .
- Confirm the deletion.
Making Changes to Simple Reassigned Orgs Using ARIN Online
To make changes to simple reassigned Orgs, you have the following options:
- Choose IP Addresses, then Manage Networks from the navigation menu. This page will allow you to search your associated networks.
- In the search field, enter the network that you want to make changes to.
- Check the box ‘Include the ### networks you’ve reassigned in your search’ option and select Search.
- In the search results, select the Net Handle for the network.
- In the Network Information panel select Actions , then Modify will present you with the options to modify your network record; Or, in the Network Information panel, under Actions menu, Modify Customer will present you with the options to modify your customer record.
Note: Updating this information keeps the registered date for the Org unchanged.
- Referral Whois (RWhois)
- Requesting Removal of Stale Reassignment and Reallocation Records
- Open-source Template Processor (TP)
- Detailed Reassignment and Reallocations
- Introduction to ARIN's Database
- Automating Record Management with Reg-RWS
Registration Services Help Desk 7:00 AM to 7:00 PM ET Phone: +1.703.227.0660 Fax: +1.703.997.8844
Tips for Calling the Help Desk
IPv6 Global Unicast Address Assignments
| Prefix | Designation | Date | WHOIS | RDAP | Status | Note |
|---|---|---|---|---|---|---|
| 2001:0000::/23 | IANA | 1999-07-01 | whois.iana.org | ALLOCATED | 2001:0000::/23 is reserved for IETF Protocol Assignments [ ]. 2001:0000::/32 is reserved for TEREDO [ ]. 2001:1::1/128 is reserved for Port Control Protocol Anycast [ ]. 2001:1::2/128 is reserved for Traversal Using Relays around NAT Anycast [ ]. 2001:1::3/128 is reserved for DNS-SD Service Registration Protocol Anycast [ ]. 2001:2::/48 is reserved for Benchmarking [ ][ ]. 2001:3::/32 is reserved for AMT [ ]. 2001:4:112::/48 is reserved for AS112-v6 [ ]. 2001:10::/28 is deprecated (previously ORCHID) [ ]. 2001:20::/28 is reserved for ORCHIDv2 [ ]. 2001:30::/28 is reserved for Drone Remote ID Protocol Entity Tags (DETs) [ ]. For complete registration details, see [ ]. | |
| 2001:0200::/23 | APNIC | 1999-07-01 | whois.apnic.net | https://rdap.apnic.net/ | ALLOCATED | |
| 2001:0400::/23 | ARIN | 1999-07-01 | whois.arin.net | https://rdap.arin.net/registry http://rdap.arin.net/registry | ALLOCATED | |
| 2001:0600::/23 | RIPE NCC | 1999-07-01 | whois.ripe.net | https://rdap.db.ripe.net/ | ALLOCATED | |
| 2001:0800::/22 | RIPE NCC | 2002-11-02 | whois.ripe.net | https://rdap.db.ripe.net/ | ALLOCATED | 2001:0800::/23 was allocated on 2002-05-02. The more recent allocation (2002-11-02) incorporates the previous allocation. |
| 2001:0c00::/23 | APNIC | 2002-05-02 | whois.apnic.net | https://rdap.apnic.net/ | ALLOCATED | 2001:db8::/32 reserved for Documentation [ ]. For complete registration details, see [ ]. |
| 2001:0e00::/23 | APNIC | 2003-01-01 | whois.apnic.net | https://rdap.apnic.net/ | ALLOCATED | |
| 2001:1200::/23 | LACNIC | 2002-11-01 | whois.lacnic.net | https://rdap.lacnic.net/rdap/ | ALLOCATED | |
| 2001:1400::/22 | RIPE NCC | 2003-07-01 | whois.ripe.net | https://rdap.db.ripe.net/ | ALLOCATED | 2001:1400::/23 was allocated on 2003-02-01. The more recent allocation (2003-07-01) incorporates the previous allocation. |
| 2001:1800::/23 | ARIN | 2003-04-01 | whois.arin.net | https://rdap.arin.net/registry http://rdap.arin.net/registry | ALLOCATED | |
| 2001:1a00::/23 | RIPE NCC | 2004-01-01 | whois.ripe.net | https://rdap.db.ripe.net/ | ALLOCATED | |
| 2001:1c00::/22 | RIPE NCC | 2004-05-04 | whois.ripe.net | https://rdap.db.ripe.net/ | ALLOCATED | |
| 2001:2000::/19 | RIPE NCC | 2019-03-12 | whois.ripe.net | https://rdap.db.ripe.net/ | ALLOCATED | 2001:2000::/20, 2001:3000::/21, and 2001:3800::/22 were allocated on 2004-05-04. The more recent allocation (2019-03-12) incorporates all these previous allocations. |
| 2001:4000::/23 | RIPE NCC | 2004-06-11 | whois.ripe.net | https://rdap.db.ripe.net/ | ALLOCATED | |
| 2001:4200::/23 | AFRINIC | 2004-06-01 | whois.afrinic.net | https://rdap.afrinic.net/rdap/ http://rdap.afrinic.net/rdap/ | ALLOCATED | |
| 2001:4400::/23 | APNIC | 2004-06-11 | whois.apnic.net | https://rdap.apnic.net/ | ALLOCATED | |
| 2001:4600::/23 | RIPE NCC | 2004-08-17 | whois.ripe.net | https://rdap.db.ripe.net/ | ALLOCATED | |
| 2001:4800::/23 | ARIN | 2004-08-24 | whois.arin.net | https://rdap.arin.net/registry http://rdap.arin.net/registry | ALLOCATED | |
| 2001:4a00::/23 | RIPE NCC | 2004-10-15 | whois.ripe.net | https://rdap.db.ripe.net/ | ALLOCATED | |
| 2001:4c00::/23 | RIPE NCC | 2004-12-17 | whois.ripe.net | https://rdap.db.ripe.net/ | ALLOCATED | |
| 2001:5000::/20 | RIPE NCC | 2004-09-10 | whois.ripe.net | https://rdap.db.ripe.net/ | ALLOCATED | |
| 2001:8000::/19 | APNIC | 2004-11-30 | whois.apnic.net | https://rdap.apnic.net/ | ALLOCATED | |
| 2001:a000::/20 | APNIC | 2004-11-30 | whois.apnic.net | https://rdap.apnic.net/ | ALLOCATED | |
| 2001:b000::/20 | APNIC | 2006-03-08 | whois.apnic.net | https://rdap.apnic.net/ | ALLOCATED | |
| 2002:0000::/16 | 6to4 | 2001-02-01 | ALLOCATED | 2002::/16 is reserved for 6to4 [ ]. For complete registration details, see [ ]. | ||
| 2003:0000::/18 | RIPE NCC | 2005-01-12 | whois.ripe.net | https://rdap.db.ripe.net/ | ALLOCATED | |
| 2400:0000::/12 | APNIC | 2006-10-03 | whois.apnic.net | https://rdap.apnic.net/ | ALLOCATED | 2400:0000::/19 was allocated on 2005-05-20. 2400:2000::/19 was allocated on 2005-07-08. 2400:4000::/21 was allocated on 2005-08-08. 2404:0000::/23 was allocated on 2006-01-19. The more recent allocation (2006-10-03) incorporates all these previous allocations. |
| 2600:0000::/12 | ARIN | 2006-10-03 | whois.arin.net | https://rdap.arin.net/registry http://rdap.arin.net/registry | ALLOCATED | 2600:0000::/22, 2604:0000::/22, 2608:0000::/22 and 260c:0000::/22 were allocated on 2005-04-19. The more recent allocation (2006-10-03) incorporates all these previous allocations. |
| 2610:0000::/23 | ARIN | 2005-11-17 | whois.arin.net | https://rdap.arin.net/registry http://rdap.arin.net/registry | ALLOCATED | |
| 2620:0000::/23 | ARIN | 2006-09-12 | whois.arin.net | https://rdap.arin.net/registry http://rdap.arin.net/registry | ALLOCATED | |
| 2630:0000::/12 | ARIN | 2019-11-06 | whois.arin.net | https://rdap.arin.net/registry http://rdap.arin.net/registry | ALLOCATED | |
| 2800:0000::/12 | LACNIC | 2006-10-03 | whois.lacnic.net | https://rdap.lacnic.net/rdap/ | ALLOCATED | 2800:0000::/23 was allocated on 2005-11-17. The more recent allocation (2006-10-03) incorporates the previous allocation. |
| 2a00:0000::/12 | RIPE NCC | 2006-10-03 | whois.ripe.net | https://rdap.db.ripe.net/ | ALLOCATED | 2a00:0000::/21 was originally allocated on 2005-04-19. 2a01:0000::/23 was allocated on 2005-07-14. 2a01:0000::/16 (incorporating the 2a01:0000::/23) was allocated on 2005-12-15. The more recent allocation (2006-10-03) incorporates these previous allocations. |
| 2a10:0000::/12 | RIPE NCC | 2019-06-05 | whois.ripe.net | https://rdap.db.ripe.net/ | ALLOCATED | |
| 2c00:0000::/12 | AFRINIC | 2006-10-03 | whois.afrinic.net | https://rdap.afrinic.net/rdap/ http://rdap.afrinic.net/rdap/ | ALLOCATED | |
| 2d00:0000::/8 | IANA | 1999-07-01 | RESERVED | |||
| 2e00:0000::/7 | IANA | 1999-07-01 | RESERVED | |||
| 3000:0000::/4 | IANA | 1999-07-01 | RESERVED | |||
| 3ffe::/16 | IANA | 2008-04 | RESERVED | 3ffe:831f::/32 was used for Teredo in some old but widely distributed networking stacks. This usage is deprecated in favor of 2001::/32, which was allocated for the purpose in [ ]. 3ffe::/16 and 5f00::/8 were used for the 6bone but were returned. [ ] | ||
| 3fff::/20 | Documentation | 2024-07-23 | RESERVED | 3fff::/20 is reserved for Documentation [ ]. For complete registration details, see [ ]. | ||
| 5f00::/16 | Segment Routing (SRv6) SIDs | 2024-04-23 | ALLOCATED | 5f00::/16 is reserved for Segment Routing (SRv6) SIDs [ ]. For complete registration details, see [ ]. | ||
| 5f01::/16 | IANA | 2008-04 | RESERVED | 3ffe::/16 and 5f00::/8 were used for the 6bone but were returned. [ ]. | ||
| 5f02::/15 | IANA | 2008-04 | RESERVED | 3ffe::/16 and 5f00::/8 were used for the 6bone but were returned. [ ]. | ||
| 5f04::/14 | IANA | 2008-04 | RESERVED | 3ffe::/16 and 5f00::/8 were used for the 6bone but were returned. [ ]. | ||
| 5f08::/13 | IANA | 2008-04 | RESERVED | 3ffe::/16 and 5f00::/8 were used for the 6bone but were returned. [ ]. | ||
| 5f10::/12 | IANA | 2008-04 | RESERVED | 3ffe::/16 and 5f00::/8 were used for the 6bone but were returned. [ ]. | ||
| 5f20::/11 | IANA | 2008-04 | RESERVED | 3ffe::/16 and 5f00::/8 were used for the 6bone but were returned. [ ]. | ||
| 5f40::/10 | IANA | 2008-04 | RESERVED | 3ffe::/16 and 5f00::/8 were used for the 6bone but were returned. [ ]. | ||
| 5f80::/9 | IANA | 2008-04 | RESERVED | 3ffe::/16 and 5f00::/8 were used for the 6bone but were returned. [ ]. |

IMAGES
VIDEO
COMMENTS
List of assigned /8 IPv4 address blocks
IANA IPv4 Address Space Registry
Number Resources
special purposes relating to protocol assignments. This registry. contains the current assignments made by the IETF from this address. block. Address prefixes listed in the Special-Purpose Address Registry are. not guaranteed routability in any particular local or global context. The IPv4 and IPv6 Special-Purpose Address Registries maintain the.
24 Subnet Mask, 30, 26, 27, 29, and other IP Address CIDR ...
1. IP addresses are assigned by ICANN, so that won't happen. But there's also a more fundamental reason. IP addresses are used for routing. When a packet comes into a router, it compares the IP address against entries in its routing table, and sends the packet on through the appropriate outgoing line.
IPs are assigned in blocks by IANA to the Regional Internet Registries (RIR). See this (list and map) of the RIRs. The RIRs then lease out smaller blocks IPs to individual companies (usually ISPs). There are requirements (including fees and proof of use) for getting a distribution and failing to maintain these means a loss of lease.
IP addresses are assigned to networks in different sized 'blocks'. The size of the 'block' assigned is written after an oblique (/), which shows the number of IP addresses contained in that block. For example, if an Internet Service Provider (ISP) is assigned a "/16", they receive around 64,000 IPv4 addresses.
IP addresses are managed by the Internet Assigned Numbers Authority (IANA), which has overall responsibility for the Internet Protocol (IP) address pool, and by the Regional Internet Registries (RIRs) to which IANA distributes large blocks of addresses. The RIRs manage, distribute, and publicly register IP addresses and related Internet number ...
Dynamic IP addresses are assigned to each computer or device on the network when they join it. External IP addresses are almost always dynamic. Special IP addresses. ... (IETF) for protocol assignments in the address block of 192.0.0.0/24. It consists of all the current IETF assignments from this particular address block and provides a ...
There are 2 ways how you can assign an IP address to your device: (1) dynamically via DHCP or (2) statically by manually assigning an IP address yourself. In either case, you must use the IP address that is provided to you by your ISP, or the IP range you allocated yourself within your private space (i.e. private IP address).
IP Lookup Tool - Check IP Block info at ARIN
In simple terms, an IP address is a numerical label assigned to each device connected to a computer network that uses the Internet Protocol for communication. It consists of four sets of numbers separated by periods (e.g., 192.168..1) and can be either IPv4 or IPv6 format. IP Address Allocation Methods.
Reserved IP addresses
Address assignments are made in a hierarchical fashion. At the top of the hierarchy is ICANN, whose IANA function distributes large blocks of 16,777,216 addresses (known as /8's) to one of five regional Internet address registries (RIRs). The RIRs then accept applications from organizations with networks that need addresses within their ...
Internet Assigned Numbers Authority
An Internet Protocol address (IP address) is a numerical label assigned to each device (e.g., computer, printer) participating in a computer network that uses the Internet Protocol for communication. ... ARIN allocates blocks of IP addresses to end users who request address space for their internal use in running their own networks, but not for ...
ARIN IPv4 Address Blocks. ARIN (or its predecessor registries) have performed allocation and assignment of IPv4 address blocks from specific address blocks assigned by IANA. The list of IPv4 address blocks is available here on the IANA website. ARIN's free pool of IPv4 address space was depleted on 24 September 2015. As a result, we are no ...
IANA IPv6 Special-Purpose Address Registry. not guaranteed routability in any particular local or global context. o Address Block - A block of IPv4 or IPv6 addresses that has been. registered for a special purpose. o Name - A descriptive name for the special-purpose address block. o RFC - The RFC through which the special-purpose address block was.
Understanding IP Addresses, Subnets, and CIDR Notation ...
Reporting Reassignments
IPv4 Multicast Address Space Registry. Host Extensions for IP Multicasting [RFC1112] specifies the extensions required of a host implementation of the Internet Protocol (IP) to support multicasting. The multicast addresses are in the range 224.0.0.0 through 239.255.255.255. Address assignments are listed below.
IPv6 Global Unicast Address Assignments