- Threats and vulnerabilities

Ransomware is malware that locks and encrypts a victim's data, files, devices or systems, rendering them inaccessible and unusable until the attacker receives a ransom payment. A ransomware attack can shut down a business for days, even weeks and -- even when the company pays the ransom -- there's no guarantee it will ever get its assets back, or that it won't be attacked again. This guide covers the history and basics of ransomware, identifies the most common targets and offers expert instructions on how to prevent an attack. Or, if the worst happens, how to recognize an attack's taken place and remove the ransomware as swiftly as possible.
Ransomware case study: recovery can be painful, in ransomware attacks, backups can save the day and the data. even so, recovery can still be expensive and painful, depending on the approach. learn more in this case study..

- Alissa Irei, Senior Site Editor
Seasoned IT consultant David Macias will never forget the day he visited a new client's website and watched in horror as it started automatically downloading ransomware before his eyes. He quickly disconnected his computer from the rest of the network, but not before the malware had encrypted 3 TB of data in a matter of seconds.
"I just couldn't believe it," said Macias, president and owner of ITRMS, a managed service provider in Riverside, Calif. "I'm an IT person, and I am [incredibly careful] about my security. I thought, 'How can this be happening to me?' I wasn't online gambling or shopping or going to any of the places you typically find this kind of stuff. I was just going to a website to help out a client, and bingo -- I got hit."
Macias received a message from the hackers demanding $800 in exchange for his data. "I told them they could go fly a kite," he said. He wiped his hard drive, performed a clean install and restored everything from backup. "I didn't lose anything other than about five days of work."
Ransomware case study: Attack #2
A few years later, another of Macias' clients -- the owner of a direct-mail printing service -- called to report he couldn't access his server. Macias logged into the network through a remote desktop and saw someone had broken through the firewall. "I told the client, 'Run as fast as you can and unplug all the computers in the network,'" he said. This short-circuited the attack, but the attacker still managed to encrypt the server, five out of 15 workstations and the local backup.
This article is part of
What is ransomware? How it works and how to remove it
- Which also includes:
- The 10 biggest ransomware attacks in history
- How to recover from a ransomware attack
- How to prevent ransomware in 6 steps
"What made this ransomware attack so bad was that it attacked the private partition that lets you restore the operating system," Macias added. Although the ransom demanded was again only $800, he advised against paying , since attackers often leave backdoors in a network and can return to steal data or demand more money.
What made this ransomware attack so bad was that it attacked the private partition that lets you restore the operating system. David Macias President, ITRMS
Fortunately, Macias had a full image-based backup of the client's network saved to a cloud service. Even so, recovery was expensive, tedious and time-consuming. He had to reformat the hard drive manually, rebuild the server from scratch and reinstall every single network device. The process took about a week and a half and cost $15,000. "The client was just incredibly grateful that all their data was intact," Macias said.
Although pleased the client's data loss was negligible, Macias wanted to find a more efficient, less painful disaster recovery strategy . Shortly after the second ransomware incident, he learned about a company called NeuShield that promised one-click backup restoration. He bought the technology for his own network and also sold it to the client that had been attacked. According to NeuShield, its Data Sentinel technology works by showing an attacker a mirror image of a computer's data, thus protecting the original files and maintaining access to them, even if encryption takes place.
Ransomware case study: Attack #3
The printing services company experienced another ransomware incident a couple of years later, when its owner was working from home and using a remote desktop without a VPN . A malicious hacker gained entry through TCP port 3389 and deployed ransomware, encrypting critical data.
In this instance, however, Macias said NeuShield enabled him to restore the system with a simple click and reboot. "When they got hit the first time, it took forever to restore. The second time, they were back up and running in a manner of minutes," he said.
While he praised NeuShield's technology, Macias noted it doesn't negate the need for antivirus protection to guard against common malware threats or for cloud backup in case of fires, earthquakes or other disasters. "Unfortunately, there's no one-stop solution," he said. "I wish there was one product that included everything, but there isn't."
Macias said he knows from personal experience, however, that investing upfront can prevent massive losses down the road. "I've had clients tell me, 'I'll worry about it when it happens.' But that's like driving without insurance. Once you get into an accident, it's too late."
How to create a ransomware incident response plan
Best practices for reporting ransomware attack
How to remove ransomware, step by step
17 ransomware removal tools to protect enterprise networks
4 tips to find cyber insurance coverage in 2023
Related Resources
- The Power of Native Cloud Detection and Response Services –AWS & SentinelOne
- The Buyer’s Guide to Software Supply Chain Security –ReversingLabs
- The Guide to Cyber Incident Response Planning –NCC Group
- Demystifying the myths of public cloud computing –TechTarget ComputerWeekly.com
Dig Deeper on Threats and vulnerabilities

MSP shares details of Kaseya VSA ransomware attack, recovery

Podcast: Ransomware, data protection and compliance

Ransomware, storage and backup: Impacts, limits and capabilities

How to prepare for ransomware
Network administrators subnet networks into segments for improved control and efficiency. IPv4 uses subnet masks, while IPv6 uses...
Cisco cuts its workforce by 7% and forms one unit for networking, security and collaboration to energize AI and security sales. ...
OWC transfers data using highly directional light in free space. While OWC delivers high-speed data transfers, it is susceptible ...
Businesses nationwide will be able to forego the U.S. Federal Trade Commission's Sept. 4 deadline for compliance with the ...
The next U.S. president will set the tone on tech issues such as AI regulation, data privacy and climate tech. This guide breaks ...
A challenge companies are facing while preparing for compliance with climate risk reporting rules is a lack of consistency among ...
Organizations looking to boost productivity for key Windows users should learn what Copilot+ PCs can offer and what workflows the...
There are numerous generative AI tools that focus on enhancing user productivity, so organizations should survey the market to ...
IT administrators had to jump into action after the CrowdStrike outage to recover faulty desktops. Learn how to use the Microsoft...
Wondering what to study to prepare for the CompTIA Cloud+ exam? Read about the new exam content from the author of 'The Official ...
Cloud pricing is complex, and there are lots of ways to waste money on services you don't need. Here's how to ensure you have ...
HPE has announced its acquisition of Morpheus Data, a move intended to bolster the hybrid, multi-cloud experience of HPE ...
Sophos X-Ops caught the Qilin ransomware gang stealing credentials stored by victims' employees in Google Chrome, heralding ...
The Police Digital Service has confirmed the appointment of an interim chief executive
The Autonomy and Darktrace co-founder is among the people who died after his luxury yacht was hit by a waterspout off the coast ...
This browser is no longer supported.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support.
Microsoft Incident Response ransomware case study
- 6 contributors
Human-operated ransomware continues to maintain its position as one of the most impactful cyberattack trends world-wide and is a significant threat that many organizations have faced in recent years. These attacks take advantage of network misconfigurations and thrive on an organization's weak interior security. Although these attacks pose a clear and present danger to organizations and their IT infrastructure and data, they are a preventable disaster .
The Microsoft Incident Response team (formerly DART/CRSP) responds to security compromises to help customers become cyber-resilient. Microsoft Incident Response provides onsite reactive incident response and remote proactive investigations. Microsoft Incident Response leverages Microsoft's strategic partnerships with security organizations around the world and internal Microsoft product groups to provide the most complete and thorough investigation possible.
This article describes how Microsoft Incident Response investigated a recent ransomware incident with details on the attack tactics and detection mechanisms.
See Part 1 and Part 2 of Microsoft Incident Response's guide to combatting human-operated ransomware for more information.
Microsoft Incident Response leverages incident response tools and tactics to identify threat actor behaviors for human operated ransomware. Public information regarding ransomware events focuses on the end impact, but rarely highlights the details of the operation and how threat actors were able to escalate their access undetected to discover, monetize, and extort.
Here are some common techniques that attackers use for ransomware attacks based on MITRE ATT&CK tactics .

Microsoft Incident Response used Microsoft Defender for Endpoint to track the attacker through the environment, create a story depicting the incident, and then eradicate the threat and remediate. Once deployed, Defender for Endpoint began detecting successful logons from a brute force attack. Upon discovering this, Microsoft Incident Response reviewed the security data and found several vulnerable Internet-facing devices using the Remote Desktop Protocol (RDP).
After initial access was gained, the threat actor used the Mimikatz credential harvesting tool to dump password hashes, scanned for credentials stored in plaintext, created backdoors with Sticky Key manipulation, and moved laterally throughout the network using remote desktop sessions.
For this case study, here is the highlighted path that the attacker took.

The following sections describe additional details based on the MITRE ATT&CK tactics and include examples of how the threat actor activities were detected with the Microsoft Defender portal.
Initial access
Ransomware campaigns use well-known vulnerabilities for their initial entry, typically using phishing emails or weaknesses in perimeter defense such as devices with the enabled Remote Desktop service exposed on the Internet.
For this incident, Microsoft Incident Response managed to locate a device that had TCP port 3389 for RDP exposed to the Internet. This allowed threat actors to perform a brute-force authentication attack and gain the initial foothold.
Defender for Endpoint used threat intelligence to determine that there were numerous sign-ins from known brute-force sources and displayed them in the Microsoft Defender portal. Here's an example.

Reconnaissance
Once the initial access was successful, environment enumeration and device discovery began. These activities allowed the threat actors to identify information about the organization's internal network and target critical systems such as domain controllers, backup servers, databases, and cloud resources. After the enumeration and device discovery, the threat actors performed similar activities to identify vulnerable user accounts, groups, permissions, and software.
The threat actor leveraged Advanced IP Scanner, an IP address scanning tool, to enumerate the IP addresses used in the environment and perform subsequent port scanning. By scanning for open ports, the threat actor discovered devices that were accessible from the initially compromised device.
This activity was detected in Defender for Endpoint and used as an indicator of compromise (IoC) for further investigation. Here's an example.

Credential theft
After gaining initial access, the threat actors performed credential harvesting using the Mimikatz password retrieval tool and by searching for files containing “password” on initially compromised systems. These actions enabled the threat actors to access additional systems with legitimate credentials. In many situations, threat actors use these accounts to create additional accounts to maintain persistence after the initial compromised accounts are identified and remediated.
Here's an example of the detected use of the Mimikatz in the Microsoft Defender portal.

Lateral movement
Movement across endpoints can vary between different organizations, but threat actors commonly use different varieties of remote management software that already exists on the device. By utilizing methods of remote access that the IT department commonly uses in their day-to-day activities, threat actors can fly under the radar for extended periods of time.
Using Microsoft Defender for Identity, Microsoft Incident Response was able to map out the path that the threat actor took between devices, displaying the accounts that were used and accessed. Here's an example.

Defense evasion
To avoid detection, the threat actors used defense evasion techniques to avoid identification and achieve their objectives throughout the attack cycle. These techniques include disabling or tampering with anti-virus products, uninstalling or disabling security products or features, modifying firewall rules, and using obfuscation techniques to hide the artifacts of an intrusion from security products and services.
The threat actor for this incident used PowerShell to disable real-time protection for Microsoft Defender on Windows 11 and Windows 10 devices and local networking tools to open TCP port 3389 and allow RDP connections. These changes decreased the chances of detection in an environment because they modified system services that detect and alert on malicious activity.
Defender for Endpoint, however, cannot be disabled from the local device and was able to detect this activity. Here's an example.

Persistence
Persistence techniques include actions by threat actors to maintain consistent access to systems after efforts are made by security staff to regain control of compromised systems.
The threat actors for this incident used the Sticky Keys hack because it allows for remote execution of a binary inside the Windows operating system without authentication. They then used this capability to launch a Command Prompt and perform further attacks.
Here's an example of the detection of the Sticky Keys hack in the Microsoft Defender portal.

Threat actors typically encrypt files using applications or features that already exist within the environment. The use of PsExec, Group Policy, and Microsoft Endpoint Configuration Management are methods of deployment that allow an actor to quickly reach endpoints and systems without disrupting normal operations.
The threat actor for this incident leveraged PsExec to remotely launch an interactive PowerShell Script from various remote shares. This attack method randomizes distribution points and makes remediation more difficult during the final phase of the ransomware attack.
Ransomware execution
Ransomware execution is one of the primary methods that a threat actor uses to monetize their attack. Regardless of the execution methodology, distinct ransomware frameworks tend to have a common behavioral pattern once deployed:
- Obfuscate threat actor actions
- Establish persistence
- Disable windows error recovery and automatic repair
- Stop a list of services
- Terminate a list of processes
- Delete shadow copies and backups
- Encrypt files, potentially specifying custom exclusions
- Create a ransomware note
Here's an example of a ransomware note.

Additional ransomware resources
Key information from Microsoft:
- The growing threat of ransomware , Microsoft On the Issues blog post on July 20, 2021
- Human-operated ransomware
- Rapidly protect against ransomware and extortion
- 2021 Microsoft Digital Defense Report (see pages 10-19)
- Ransomware: A pervasive and ongoing threat threat analytics report in the Microsoft Defender portal
- Microsoft Incident Response ransomware approach and best practices
Microsoft 365:
- Deploy ransomware protection for your Microsoft 365 tenant
- Maximize Ransomware Resiliency with Azure and Microsoft 365
- Recover from a ransomware attack
- Malware and ransomware protection
- Protect your Windows 10 PC from ransomware
- Handling ransomware in SharePoint Online
- Threat analytics reports for ransomware in the Microsoft Defender portal
Microsoft Defender XDR:
- Find ransomware with advanced hunting
Microsoft Defender for Cloud Apps:
- Create anomaly detection policies in Defender for Cloud Apps
Microsoft Azure:
- Azure Defenses for Ransomware Attack
- Backup and restore plan to protect against ransomware
- Help protect from ransomware with Microsoft Azure Backup (26 minute video)
- Recovering from systemic identity compromise
- Advanced multistage attack detection in Microsoft Sentinel
- Fusion Detection for Ransomware in Microsoft Sentinel
Microsoft Security team blog posts:
3 steps to prevent and recover from ransomware (September 2021)
A guide to combatting human-operated ransomware: Part 1 (September 2021)
Key steps on how Microsoft Incident Response conducts ransomware incident investigations.
A guide to combatting human-operated ransomware: Part 2 (September 2021)
Recommendations and best practices.
Becoming resilient by understanding cybersecurity risks: Part 4—navigating current threats (May 2021)
See the Ransomware section.
Human-operated ransomware attacks: A preventable disaster (March 2020)
Includes attack chain analyses of actual attacks.
Ransomware response—to pay or not to pay? (December 2019)
Norsk Hydro responds to ransomware attack with transparency (December 2019)
Was this page helpful?
Additional resources
For the best Oliver Wyman website experience, please upgrade your browser to IE9 or later

Surviving a Ransomware Attack: A Case Study
A project manager for ABC Inc., a manufacturer with $1 billion in annual revenue and operations in 30 countries steps off the elevator at company headquarters. She’s returning to her office after a lunch break and is eager to get back to work on a major order for a large client that is due next week. But something’s wrong.
When she sits down at her desk, she sees that her computer does not seem to be functioning. Instead of the usual desktop image on her monitor, she instead sees a lock and a disturbing message:
Your files are encrypted. If you do not submit payment to us — $5 million in bitcoin — within three days, your files will be lost forever.
Worried, she calls ABC’s IT manager on the other side of the floor, but the IT manager and his staff are too busy to answer. Other employees around the world are reporting that procurement and shipping software is inaccessible. At the company’s factories in China, India, and elsewhere, assembly lines have come to a halt. And that same message is being seen on computers at every company office.
The company is a victim of ransomware — an attack that is growing increasingly more frequent, severe, and sophisticated.
A ransomware attack can disrupt a business for weeks, cost millions of dollars in downtime and restoration costs, and damage reputations. Millions more is often needed to pay the actual ransom. Personal information may also be exposed, resulting in significant costs for breach notification and credit monitoring. But with the right advisor and with effective planning and preparation, a business can weather the storm and take action to protect its operations, systems, revenue, and reputation.
Marsh can be that advisor to your organization, delivering recommendations before, during, and after an incident. Here’s how a ransomware attack can play out, and how we can help you manage its impacts on your organization.
To Pay or Not to Pay
As critical data is held hostage and systems are rendered inoperable, ABC finds itself in an untenable situation. Operations are completely halted; the technology that powers ABC’s manufacturing line is down. Employees cannot perform critical tasks — they cannot order components that go into their products, nor can they ship finished goods to customers.
With contractual obligations not being met and assembly lines idling, the company is losing money — every hour, every minute, every second. And with the threat actor’s deadline looming, ABC’s risk management and leadership teams face a critical decision: Should we pay the ransom?
Several factors should go into this decision. These include the criticality of affected data and systems, availability and integrity of data backups, cost of the ransom versus the estimated cost of restoration, the likelihood of successful restoration (whether the ransom is paid or not), and regulatory implications.
Organizations should develop guidance regarding ransomware decision-making and build this into their incident response plans. Generally, choosing to pay or not requires careful consideration and input from key stakeholders, including in-house and outside legal counsel and vendors.
As ABC considers its options, it can rely on Marsh for help.
Scenario 1: Paying the Ransom
ABC makes the decision to pay the ransom after determining that restoring its systems, files, and data is not possible — or at all timely. ABC quickly engages a law firm with specific expertise in ransomware to serve as the incident response coordinator.
Computer forensic teams actively investigate the incident and try to determine its scope while working to limit the spread of the malware. Crisis management and public relations teams are engaged to manage reputational harm.
ABC, meanwhile, is also busy getting the necessary internal authorizations and working with third parties to prepare for a cryptocurrency payment. Legal and regulatory checks must be performed, such as a review of whether payment is possible under rules established by the Office of Foreign Asset Control , which prohibits payment to certain sanctioned foreign parties.
A ransomware response vendor, meanwhile, begins negotiating with attackers on ABC’s behalf for a reduction in payment demands and a later deadline. The vendor’s specialists have seen this strain of ransomware before and understand how the threat actor group operates.
After initial communication with the threat actor group’s “PR department,” the vendor engages the threat actor group’s “finance department” and succeeds in extending the payment deadline and cutting the required payment to $2 million in bitcoin. The ransomware response firm also tests the decryption keys to make sure they work.
ABC is ready to make payment. The company works with its legal advisors and ransomware response vendor to make a bitcoin payment to the cyber-attackers four days after the ransomware message first appeared. In exchange, its IT team receives a decryption key to restore access to the network.
The work, however, is far from over. It may take weeks to deploy the decryption keys across ABC’s network and restore all impacted systems to full functionality. Additional forensics may be necessary to confirm there are no remnants of the malware, that backdoors are identified and eliminated, and that systems have been scrubbed clean.
Backups will need to be reconfigured and tested and data may need to be restored. To prevent incident reoccurrence, new hardware or software may also be needed as a part of reengineering IT systems and boundaries. The overall focus of reengineering is to improve the overall security environment and support improved cybersecurity monitoring.
ABC’s cyber insurance coverage, secured with the help of its brokers at Marsh, can prove useful. ABC’s cyber policy will reimburse the ransomware payment and cover the costs of the vendors that helped with the negotiation. Incident response, including attorney fees, PR expenses, and data restoration costs will also be covered, as is lost income during ABC’s downtime and extra expenses that might have been incurred to keep operating.
In addition to securing your cyber policy, Marsh can help you navigate the carrier's vendor and ransomware reimbursement consent requirements. And we can help you prepare a business interruption claim to ensure that you maximize your cyber insurance coverage.
As ABC returns to some semblance of normalcy, the assembly line once again begins to hum.
Scenario 2: Not Paying the Ransom
In ABC’s executive offices, the ransomware demand sparks heated debate. While some argue in favor of paying quickly to minimize the damage and resume operations as quickly as possible, company leadership ultimately concludes that the company will be able to make a near full recovery using its offline backups.
After engaging a ransomware response vendor, ABC also learns that the attackers hardly ever deliver a working decryptor key. For these reasons, ABC decides not to pay the ransom.
Instead, ABC works with its advisors — including consultants from Marsh, experienced cyber legal counsel, forensic analysts, and others — to determine the extent of attackers’ presence within their networks and what data and systems may be compromised. Efforts are taken to contain the malware and to isolate and remediate impacted systems. Once the network is scrubbed clean, ABC then takes steps to restore backups and rebuild critical datasets.
ABC’s cyber insurance coverage can again prove useful, responding in many of the same ways as if the company had paid the ransom. Its policy provides coverage for incident response, data restoration, business interruption, and extra expenses.
One week after the ransomware message first appeared, ABC successfully starts restoring access to its core systems and backup data, though the process is still a long one. As ABC rebuilds its IT infrastructure, some legacy systems need to be replaced. While operations can resume as active monitoring for indicators of compromise (IoCs) continues, ABC is only operating at 50% capacity. Once the network is scrubbed clean and purged of malware, the company gradually increases its capacity to get back up and running again.
Three weeks out, factory operations resume at 100% capacity and affected employees fully return to work. ABC can once again focus on its core mission of delivering high-quality manufactured goods to its customers.
Managing Claims
With cyber insurance responding in either scenario, the next phase for ABC is to seek recovery.
With help from Marsh, which regularly communicated with insurers as the company responded to the ransomware attack, ABC’s risk management team gets to work capturing loss estimates tied to its downtime following the attack and cataloguing extra expenses incurred while responding. Documenting and capturing decisions regarding activities and resources during the incident as they are made is critical to ABC’s successful claim development — and Marsh supports the process to help maximize insurance recovery
Once this information is in hand, ABC provides its cyber insurer with a detailed submission. Ultimately, the company is able to recoup the reasonable and necessary costs from the incident — subject to self-insured retentions — under the terms of its well-crafted cyber insurance policy.
Post-Incident Steps
The ransomware attack is over; ABC has weathered the storm. But there’s still one final step in the process.
As part of its cyber incident response plan, ABC’s final action is to conduct an after-action review. The purpose of this exercise is to understand and document what went well and what didn’t — and how to address any gaps or weaknesses. That’s a critical step to take in order to ensure ABC learns from the incident and is better prepared for the possibility of a future attack, which may be similar to the last one — or completely different.
With the help of a forensics provider, ABC learns that the ransomware entered its networks through a phishing campaign and was able to spread across its network with ease, scooping up administrative credentials along the way and even credentials for the company’s industrial control systems. Armed with these findings, ABC develops an action plan to harden its cybersecurity with additional phishing tests, new multifactor authentication initiatives, and improved network segmentation based on system and data criticality. ABC also re-evaluates its cyber insurance limits as risk transfer has proven to be both critical and complementary to ABC’s risk mitigation efforts.
As part of this exercise, the both Marsh and ABC review ABC’s cyber incident response plan. Like a number of its peers, ABC’s plan — while robust in many ways — did not specifically address a ransomware attack. But developing a plan specific to ransomware is critical to making timely decisions.
Working with Marsh and external partners, ABC is able to update its internal guidance around ransomware attacks, perform an IoC assessment, identify and document vulnerabilities or gaps, and review its backup strategy – and critically, align all key stakeholders around ABC’s strategies to manage the organization’s cyber risk. The bottom line: ABC is more confident, more aligned, better prepared, and better protected in the event of another ransomware attack in the future.
How Else Can Marsh Help You Manage Ransomware Threats?
Beyond providing support following an attack, Marsh can also help your organization address potential ransomware threats on an ongoing basis. We can offer:
- Ransomware Insights: An intelligence briefing detailing the ransomware environment, your potential vulnerabilities, top attack vectors, best practices for you to follow, and potential cost estimates.
- Insurance Program Design: Advice and guidance on key policy terms and conditions and program structures, insight into underwriters’ priorities and objectives, and aggressive marketing on your behalf.
- Ransomware Readiness Assessment: A review of your current operations, with feedback and analysis based on best practices sourced from assessments of more than 1,400 businesses.
- Cyber Financial Stress Test: An estimate of the potential total cost of a ransomware or other cyber incident on your organization, which can inform critical decisions about cyber insurance and risk management strategies and investments.
- Cyber Incident Response Plan: Assistance in building or revising an existing plan to help you respond to a cyber event, with specific considerations for ransomware.
- Cybersecurity Program Review: A review of an organization’s cybersecurity policies, plans, procedures, and training that culminates in a maturity assessment and actionable recommendations for improvement.

Reid Sawyer
Head, US Cyber Risk Consulting, Marsh

James Holtzclaw
Senior Vice President, Cybersecurity Consulting and Advisory Services, Marsh Risk Consulting (MRC)

Susan Young
Managing Director, Cyber Practice, Marsh US

- Incident response
- Microsoft Incident Response
The five-day job: A BlackByte ransomware intrusion case study
- By Microsoft Incident Response
- Threat intelligence
- Microsoft Defender
Microsoft Defender for Endpoint
Microsoft Defender Vulnerability Management
- Microsoft Defender XDR
- Microsoft Security Experts
Microsoft Sentinel
- Attacker techniques, tools, and infrastructure
- Vulnerabilities and exploits
- Credential theft
- Elevation of privilege
- Living off the land
As ransomware attacks continue to grow in number and sophistication, threat actors can quickly impact business operations if organizations are not well prepared. In a recent investigation by Microsoft Incident Response (previously known as Microsoft Detection and Response Team – DART) of an intrusion, we found that the threat actor progressed through the full attack chain, from initial access to impact, in less than five days, causing significant business disruption for the victim organization.
Our investigation found that within those five days, the threat actor employed a range of tools and techniques, culminating in the deployment of BlackByte 2.0 ransomware, to achieve their objectives. These techniques included:
- Exploitation of unpatched internet-exposed Microsoft Exchange Servers
- Web shell deployment facilitating remote access
- Use of living-off-the-land tools for persistence and reconnaissance
- Deployment of Cobalt Strike beacons for command and control (C2)
- Process hollowing and the use of vulnerable drivers for defense evasion
- Deployment of custom-developed backdoors to facilitate persistence
- Deployment of a custom-developed data collection and exfiltration tool

In this blog, we share details of our investigation into the end-to-end attack chain, exposing security weaknesses that the threat actor exploited to advance their attack. As we learned from Microsoft’s tracking of ransomware attacks and the cybercriminal economy that enables them, disrupting common attack patterns could stop many of the attacker activities that precede ransomware deployment. This case highlights that common security hygiene practices go a long way in preventing, identifying, and responding to malicious activity as early as possible to mitigate the impact of ransomware attacks. We encourage organizations to follow the outlined mitigation steps, including ensuring that internet-facing assets are up to date and configured securely. We also share indicators of compromise, detection details, and hunting guidance to help organizations identify and respond to these attacks in their environments.
Forensic analysis
Initial access and privilege escalation.
To obtain initial access into the victim’s environment, the threat actor was observed exploiting the ProxyShell vulnerabilities CVE-2021-34473, CVE-2021-34523, and CVE-2021-31207 on unpatched Microsoft Exchange Servers. The exploitation of these vulnerabilities allowed the threat actor to:
- Attain system-level privileges on the compromised Exchange host
- Enumerate LegacyDN of users by sending Autodiscover requests, including SIDs of users
- Construct a valid authentication token and use it against the Exchange PowerShell backend
- Impersonate domain admin users and create a web shell by using the New-MailboxExportRequest cmdlet
- Create web shells to obtain remote control on affected servers
The threat actor was observed operating from the following IP to exploit ProxyShell and access the web shell:
- 185.225.73[.]244
Persistence
After gaining access to a device, the threat actor created the following registry run keys to run a payload each time a user signs in:
| Registry key | Value name | Value data |
| HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run | MsEdgeMsE | rundll32 C:\Users\user\Downloads\api-msvc.dll,Default |
| HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run | MsEdgeMsE | rundll32 C:\temp\api-msvc.dll,Default |
| HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run | MsEdgeMsE | rundll32 C:\systemtest\api-system.png,Default |
The file api-msvc.dll (SHA-256: 4a066569113a569a6feb8f44257ac8764ee8f2011765009fdfd82fe3f4b92d3e) was determined to be a backdoor capable of collecting system information, such as the installed antivirus products, device name, and IP address. This information is then sent via HTTP POST request to the following C2 channel:
- hxxps://myvisit[.]alteksecurity[.]org/t
The organization was not using Microsoft Defender Antivirus, which detects this malware as Trojan:Win32/Kovter!MSR, as the primary antivirus solution, and the backdoor was allowed to run.
An additional file, api-system.png , was identified to have similarities to api-msvc.dll . This file behaved like a DLL, had the same default export function, and also leveraged run keys for persistence.
Cobalt Strike Beacon
The threat actor leveraged Cobalt Strike to achieve persistence. The file sys.exe (SHA-256: 5f37b85687780c089607670040dbb3da2749b91b8adc0aa411fd6280b5fa7103), detected by Microsoft Defender Antivirus as Trojan:Win64/CobaltStrike!MSR, was determined to be a Cobalt Strike Beacon and was downloaded directly from the file sharing service temp[.]sh :
- hxxps://temp[.]sh/szAyn/sys.exe
This beacon was configured to communicate with the following C2 channel:
- 109.206.243[.]59:443
Threat actors leverage legitimate remote access tools during intrusions to blend into a victim network. In this case, the threat actor utilized the remote administration tool AnyDesk, to maintain persistence and move laterally within the network. AnyDesk was installed as a service and was run from the following paths:
- C:\systemtest\anydesk\AnyDesk.exe
- C:\Program Files (x86)\AnyDesk\AnyDesk.exe
- C:\Scripts\AnyDesk.exe
Successful connections were observed in the AnyDesk log file ad_svc.trace involving anonymizer service IP addresses linked to TOR and MULLVAD VPN, a common technique that threat actors employ to obscure their source IP ranges.
Reconnaissance
We found the presence and execution of the network discovery tool NetScan being used by the threat actor to perform network enumeration using the following file names:
- netscan.exe (SHA-256:1b9badb1c646a19cdf101ac4f6fdd23bc61eaab8c9f925eb41848cea9fd0738e)
- netapp.exe (SHA-256:1b9badb1c646a19cdf101ac4f6fdd23bc61eaab8c9f925eb41848cea9fd0738e)
Additionally, execution of AdFind (SHA-256: f157090fd3ccd4220298c06ce8734361b724d80459592b10ac632acc624f455e), an Active Directory reconnaissance tool, was observed in the environment.
Credential access
Evidence of likely usage of the credential theft tool Mimikatzwas also uncovered through the presence of a related log file mimikatz.log . Microsoft IR assesses that Mimikatz was likely used to attain credentials for privileged accounts.
Lateral movement
Using compromised domain admin credentials, the threat actor used Remote Desktop Protocol (RDP) and PowerShell remoting to obtain access to other servers in the environment, including domain controllers.
Data staging and exfiltration
In one server where Microsoft Defender Antivirus was installed, a suspicious file named explorer.exe was identified, detected as Trojan:Win64/WinGoObfusc.LK!MT, and quarantined. However, because tamper protection wasn’t enabled on this server, the threat actor was able to disable the Microsoft Defender Antivirus service, enabling the threat actor to run the file using the following command:
explorer.exe P@$$w0rd
After reverse engineering explorer.exe , we determined it to be ExByte, a GoLang-based tool developed and commonly used in BlackByte ransomware attacks for collection and exfiltration of files from victim networks. This tool is capable of enumerating files of interest across the network and, upon execution, creates a log file containing a list of files and associated metadata. Multiple log files were uncovered during the investigation in the path:
- C:\Exchange\MSExchLog.log
Analysis of the binary revealed a list of file extensions that are targeted for enumeration.

Forensic analysis identified a file named data.txt that was created and later deleted after ExByte execution. This file contained obfuscated credentials that ExByte leveraged to authenticate to the popular file sharing platform Mega NZ using the platform’s API at:
- hxxps://g.api.mega.co[.]nz

We also determined that this version of Exbyte was crafted specifically for the victim, as it contained a hardcoded device name belonging to the victim and an internal IP address.
ExByte execution flow
Upon execution, ExByte decodes several strings and checks if the process is running with privileged access by reading \\.\PHYSICALDRIVE0 :
- If this check fails, ShellExecuteW is invoked with the IpOperation parameter RunAs , which runs explorer.exe with elevated privileges.
After this access check, explorer.exe attempts to read the data.txt file in the current location:
- If the text file doesn’t exist, it invokes a command for self-deletion and exits from memory:
- If data.txt exists, explorer.exe reads the file, passes the buffer to Base64 decode function, and then decrypts the data using the key provided in the command line. The decrypted data is then parsed as JSON below and fed for login function:
Finally, it forms a URL for sign-in to the API of the service MEGA NZ:
- hxxps://g.api.mega.co[.]nz/cs?id=1674017543
Data encryption and destruction
On devices where files were successfully encrypted, we identified suspicious executables, detected by Microsoft Defender Antivirus as Trojan:Win64/BlackByte!MSR, with the following names:
- schillerized.exe
The files were analyzed and determined to be BlackByte 2.0 binaries responsible for encryption across the environment. The binaries require an 8-digit key number to encrypt files.
Two modes of execution were identified:
- When the -s parameter is provided, the ransomware self-deletes and encrypts the machine it was executed on.
- When the -a parameter is provided, the ransomware conducts enumeration and uses an Ultimate Packer Executable (UPX) packed version of PsExec to deploy across the network. Several domain admin credentials were hardcoded in the binary, facilitating the deployment of the binary across the network.
Depending on the switch ( -s or -a ), execution may create the following files:
- C:\SystemData\M8yl89s7.exe (UPX-packed PsExec with a random name; SHA-256: ba3ec3f445683d0d0407157fda0c26fd669c0b8cc03f21770285a20b3133098f)
- C:\SystemData\wEFT.exe (Additional BlackByte binary)
- C:\SystemData\MsExchangeLog1.log (Log file)
- C:\SystemData\rENEgOtiAtES (A vulnerable (CVE-2019-16098) driver RtCore64.sys used to evade detection by installed antivirus software; SHA-256: 01aa278b07b58dc46c84bd0b1b5c8e9ee4e62ea0bf7a695862444af32e87f1fd)
- C:\SystemData\iHu6c4.ico (Random name – BlackBytes icon)
- C:\SystemData\BB_Readme_file.txt (BlackByte ReadMe file)
- C:\SystemData\skip_bypass.txt (Unknown)
BlackByte 2.0 ransomware capabilities
Some capabilities identified for the BlackByte 2.0 ransomware were:
- The file rENEgOtiAtES created matches RTCore64.sys , a vulnerable driver (CVE-2049-16098) that allows any authenticated user to read or write to arbitrary memory
- The BlackByte binary then creates and starts a service named RABAsSaa calling rENEgOtiAtES , and exploits this service to evade detection by installed antivirus software
- cmd.exe /c ping 1.1.1.1 -n 10 > Nul & Del “PATH_TO_BLACKBYTE” /F /Q
- cmd /c netsh advfirewall set allprofiles state off
- cmd /c netsh advfirewall firewall set rule group=”File and Printer Sharing” new enable=Yes
- cmd /c netsh advfirewall firewall set rule group=”Network Discovery” new enable=Yes
- cmd /c vssadmin Resize ShadowStorge /For=B:\ /On=B:\ /MaxSize=401MB
- cmd /c vssadmin Resize ShadowStorage /For=B:\ /On=B:\ /MaxSize=UNBOUNDED
- cmd /c reg add HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System /v LocalAccountTokenFilterPolicy /t REG_DWORD /d 1 /f
- cmd /c reg add HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System /v EnableLinkedConnections /t REG_DWORD /d 1 /f
- cmd /c reg add HKLM\\SYSTEM\\CurrentControlSet\\Control\\FileSystem /v LongPathsEnabled /t REG_DWORD /d 1 /f
- Ability to terminate running services and processes
- Ability to enumerate and mount volumes and network shares for encryption
- Perform anti-forensics technique timestomping (sets the file time of encrypted and ReadMe file to 2000-01-01 00:00:00)
- Ability to perform anti-debugging techniques
Recommendations
To guard against BlackByte ransomware attacks, Microsoft recommends the following:
- Ensure that you have a patch management process in place and that patching for internet-exposed devices is prioritized; Understand and assess your cyber exposure with advanced vulnerability and configuration assessment tools like Microsoft Defender Vulnerability Management
- Implement an endpoint detection and response (EDR) solution like Microsoft Defender for Endpoint to gain visibility into malicious activity in real time across your network
- Ensure antivirus protections are updated regularly by turning on cloud-based protection and that your antivirus solution is configured to block threats
- Enable tamper protection to prevent components of Microsoft Defender Antivirus from being disabled
- Block inbound traffic from IPs specified in the indicators of compromise section of this report
- Block inbound traffic from TOR exit nodes
- Block inbound access from unauthorized public VPN services
- Restrict administrative privileges to prevent authorized system changes
BlackByte ransomware attacks target organizations that have infrastructure with unpatched vulnerabilities. As outlined in the Microsoft Digital Defense Report , common security hygiene practices, including keeping systems up to date, could protect against 98% of attacks.
As new tools are being developed by threat actors, a modern threat protection solution like Microsoft 365 Defender is necessary to prevent and detect the multiple techniques used in the attack chain, especially where the threat actor attempts to evade or disable specific defense mechanisms. Hunting for malicious behavior should be performed regularly in order to detect potential attacks that could evade detections, as a complementary activity for continuous monitoring from security tools alerts and incidents.
To understand how Microsoft can help you secure your network and respond to network compromise, visit https://aka.ms/MicrosoftIR.
Microsoft 365 Defender detections
Microsoft 365 Defender is becoming Microsoft Defender XDR. Learn more .
Microsoft Defender Antivirus
Microsoft Defender Antivirus detects this threat as the following malware:
- Trojan:Win32/Kovter!MSR
- Trojan:Win64/WinGoObfusc.LK!MT
- Trojan:Win64/BlackByte!MSR
- HackTool:Win32/AdFind!MSR
- Trojan:Win64/CobaltStrike!MSR
The following alerts might indicate threat activity related to this threat. Note, however, that these alerts can be also triggered by unrelated threat activity.
- ‘CVE-2021-31207’ exploit malware was detected
- An active ‘NetShDisableFireWall’ malware in a command line was prevented from executing.
- Suspicious registry modification.
- ‘Rtcore64’ hacktool was detected
- Possible ongoing hands-on-keyboard activity (Cobalt Strike)
- A file or network connection related to a ransomware-linked emerging threat activity group detected
- Suspicious sequence of exploration activities
- A process was injected with potentially malicious code
- Suspicious behavior by cmd.exe was observed
- ‘Blackbyte’ ransomware was detected
Microsoft Defender Vulnerability Management surfaces devices that may be affected by the following vulnerabilities used in this threat:
- CVE-2021-34473
- CVE-2021-34523
- CVE-2021-31207
- CVE-2019-16098
Hunting queries
Microsoft 365 Defender
Microsoft 365 Defender customers can run the following query to find related activity in their networks:
ProxyShell web shell creation events
Suspicious vssadmin events
Detection for persistence creation using Registry Run keys
Microsoft Sentinel customers can use the TI Mapping analytics (a series of analytics all prefixed with ‘TI map’) to automatically match the malicious domain indicators mentioned in this blog post with data in their workspace. If the TI Map analytics are not currently deployed, customers can install the Threat Intelligence solution from the Microsoft Sentinel Content Hub to have the analytics rule deployed in their Sentinel workspace. More details on the Content Hub can be found here: https://learn.microsoft.com/azure/sentinel/sentinel-solutions-deploy
Microsoft Sentinel also has a range of detection and threat hunting content that customers can use to detect the post exploitation activity detailed in this blog in addition to Microsoft 365 Defender detections list above.
- Web shell activity
- Suspicious file downloads on Exchange Servers
- Firewall rule changes
- Shadow copy deletion
- Anamolous RDP activity
Indicators of compromise
The table below shows IOCs observed during our investigation. We encourage our customers to investigate these indicators in their environments and implement detections and protections to identify past related activity and prevent future attacks against their systems.
| Indicator | Type | Description |
| 4a066569113a569a6feb8f44257ac8764ee8f2011765009fdfd82fe3f4b92d3e | SHA-256 | api-msvc.dll (Backdoor installed through RunKeys) |
| 5f37b85687780c089607670040dbb3da2749b91b8adc0aa411fd6280b5fa7103 | SHA-256 | sys.exe (Cobalt Strike Beacon) |
| 01aa278b07b58dc46c84bd0b1b5c8e9ee4e62ea0bf7a695862444af32e87f1fd | SHA-256 | rENEgOtiAtES (Vulnerable driver RtCore64.sys created by BlackByte binary) |
| ba3ec3f445683d0d0407157fda0c26fd669c0b8cc03f21770285a20b3133098f | SHA-256 | [RANDOM_NAME].exe (UPX Packed PsExec created by BlackByte binary) |
| 1b9badb1c646a19cdf101ac4f6fdd23bc61eaab8c9f925eb41848cea9fd0738e | SHA-256 | “netscan.exe”, “netapp.exe (Netscan network discovery tool) |
| f157090fd3ccd4220298c06ce8734361b724d80459592b10ac632acc624f455e | SHA-256 | AdFind.exe (Active Directory information gathering tool) |
| hxxps://myvisit[.]alteksecurity[.]org/t | URL | C2 for backdoor api-msvc.dll |
| hxxps://temp[.]sh/szAyn/sys.exe | URL | Download URL for sys.exe |
| 109.206.243[.]59 | IP Address | C2 for Cobalt Strike Beacon sys.exe |
| 185.225.73[.]244 | IP Address | Originating IP address for ProxyShell exploitation and web shell interaction |
NOTE: These indicators should not be considered exhaustive for this observed activity.
File extensions targeted by BlackByte binary for encryption:
| .4dd | .4dl | .accdb | .accdc | .accde | .accdr | .accdt | .accft |
| .adb | .ade | .adf | .adp | .arc | .ora | .alf | .ask |
| .btr | .bdf | .cat | .cdb | .ckp | .cma | .cpd | .dacpac |
| .dad | .dadiagrams | .daschema | .db | .db-shm | .db-wal | .db3 | .dbc |
| .dbf | .dbs | .dbt | .dbv | . dbx | . dcb | . dct | . dcx |
| . ddl | . dlis | . dp1 | . dqy | . dsk | . dsn | . dtsx | . dxl |
| . eco | . ecx | . edb | . epim | . exb | . fcd | . fdb | . fic |
| . fmp | . fmp12 | . fmpsl | . fol | .fp3 | . fp4 | . fp5 | . fp7 |
| . fpt | . frm | . gdb | . grdb | . gwi | . hdb | . his | . ib |
| . idb | . ihx | . itdb | . itw | . jet | . jtx | . kdb | . kexi |
| . kexic | . kexis | . lgc | . lwx | . maf | . maq | . mar | . masmav |
| . mdb | . mpd | . mrg | . mud | . mwb | . myd | . ndf | . nnt |
| . nrmlib | . ns2 | . ns3 | . ns4 | . nsf | . nv | . nv2 | . nwdb |
| . nyf | . odb | . ogy | . orx | . owc | . p96 | . p97 | . pan |
| . pdb | . pdm | . pnz | . qry | . qvd | . rbf | . rctd | . rod |
| . rodx | . rpd | . rsd | . sas7bdat | . sbf | . scx | . sdb | . sdc |
| . sdf | . sis | . spg | . sql | . sqlite | . sqlite3 | . sqlitedb | . te |
| . temx | . tmd | . tps | . trc | . trm | . udb | . udl | . usr |
| . v12 | . vis | . vpd | . vvv | . wdb | . wmdb | . wrk | . xdb |
| . xld | . xmlff | . abcddb | . abs | . abx | . accdw | . and | . db2 |
| . fm5 | . hjt | . icg | . icr | . kdb | . lut | . maw | . mdn |
| . mdt |
Shared folders targeted for encryption (Example: \\[IP address]\Downloads ):
| Users | Backup | Veeam | homes | home |
| media | common | Storage Server | Public | Web |
| Images | Downloads | BackupData | ActiveBackupForBusiness | Backups |
| NAS-DC | DCBACKUP | DirectorFiles | share |
File extensions ignored:
| .ini | .url | .msilog | .log | .ldf | .lock | .theme | .msi |
| .sys | .wpx | .cpl | .adv | .msc | .scr | .key | .ico |
| .dll | .hta | .deskthemepack | .nomedia | .msu | .rtp | .msp | .idx |
| .ani | .386 | .diagcfg | .bin | .mod | .ics | .com | .hlp |
| .spl | .nls | .cab | .exe | .diagpkg | .icl | .ocx | .rom |
| .prf | .thempack | .msstyles | .icns | .mpa | .drv | .cur | .diagcab |
| .cmd | .shs |
Folders ignored:
| windows | boot | program files (x86) | windows.old | programdata |
| intel | bitdefender | trend micro | windowsapps | appdata |
| application data | system volume information | perflogs | msocache |
Files ignored:
| bootnxt | ntldr | bootmgr | thumbs.db |
| ntuser.dat | bootsect.bak | autoexec.bat | iconcache.db |
| bootfont.bin |
Processes terminated:
| teracopy | teamviewer | nsservice | nsctrl | uranium |
| processhacker | procmon | pestudio | procmon64 | x32dbg |
| x64dbg | cff explorer | procexp | pslist | tcpview |
| tcpvcon | dbgview | rammap | rammap64 | vmmap |
| ollydbg | autoruns | autorunssc | filemon | regmon |
| idaq | idaq64 | immunitydebugger | wireshark | dumpcap |
| hookexplorer | importrec | petools | lordpe | sysinspector |
| proc_analyzer | sysanalyzer | sniff_hit | windbg | joeboxcontrol |
| joeboxserver | resourcehacker | fiddler | httpdebugger | dumpit |
| rammap | rammap64 | vmmap | agntsvc | cntaosmgr |
| dbeng50 | dbsnmp | encsvc | infopath | isqlplussvc |
| mbamtray | msaccess | msftesql | mspub | mydesktopqos |
| mydesktopservice | mysqld | mysqld-nt | mysqld-opt | Ntrtscan |
| ocautoupds | ocomm | ocssd | onenote | oracle |
| outlook | PccNTMon | powerpnt | sqbcoreservice | sql |
| sqlagent | sqlbrowser | sqlservr | sqlwriter | steam |
| synctime | tbirdconfig | thebat | thebat64 | thunderbird |
| tmlisten | visio | winword | wordpad | xfssvccon |
| zoolz |
Services terminated:
| CybereasonRansomFree | vnetd | bpcd | SamSs | TeraCopyService |
| msftesql | nsService | klvssbridge64 | vapiendpoint | ShMonitor |
| Smcinst | SmcService | SntpService | svcGenericHost | Swi_ |
| TmCCSF | tmlisten | TrueKey | TrueKeyScheduler | TrueKeyServiceHelper |
| WRSVC | McTaskManager | OracleClientCache80 | mfefire | wbengine |
| mfemms | RESvc | mfevtp | sacsvr | SAVAdminService |
| SepMasterService | PDVFSService | ESHASRV | SDRSVC | FA_Scheduler |
| KAVFS | KAVFS_KAVFSGT | kavfsslp | klnagent | macmnsvc |
| masvc | MBAMService | MBEndpointAgent | McShield | audioendpointbuilder |
| Antivirus | AVP | DCAgent | bedbg | EhttpSrv |
| MMS | ekrn | EPSecurityService | EPUpdateService | ntrtscan |
| EsgShKernel | msexchangeadtopology | AcrSch2Svc | MSOLAP$TPSAMA | Intel(R) PROSet Monitoring |
| msexchangeimap4 | ARSM | unistoresvc_1af40a | ReportServer$TPS | MSOLAP$SYSTEM_BGC |
| W3Svc | MSExchangeSRS | ReportServer$TPSAMA | Zoolz 2 Service | MSOLAP$TPS |
| aphidmonitorservice | SstpSvc | MSExchangeMTA | ReportServer$SYSTEM_BGC | Symantec System Recovery |
| UI0Detect | MSExchangeSA | MSExchangeIS | ReportServer | MsDtsServer110 |
| POP3Svc | MSExchangeMGMT | SMTPSvc | MsDtsServer | IisAdmin |
| MSExchangeES | EraserSvc11710 | Enterprise Client Service | MsDtsServer100 | NetMsmqActivator |
| stc_raw_agent | VSNAPVSS | PDVFSService | AcrSch2Svc | Acronis |
| CASAD2DWebSvc | CAARCUpdateSvc | McAfee | avpsus | DLPAgentService |
| mfewc | BMR Boot Service | DefWatch | ccEvtMgr | ccSetMgr |
| SavRoam | RTVsc screenconnect | ransom | sqltelemetry | msexch |
| vnc | teamviewer | msolap | veeam | backup |
| sql | memtas | vss | sophos | svc$ |
| mepocs | wuauserv |
Drivers that Blackbyte can bypass:
| 360avflt.sys | 360box.sys | 360fsflt.sys | 360qpesv.sys | 5nine.cbt.sys |
| a2acc.sys | a2acc64.sys | a2ertpx64.sys | a2ertpx86.sys | a2gffi64.sys |
| a2gffx64.sys | a2gffx86.sys | aaf.sys | aalprotect.sys | abrpmon.sys |
| accessvalidator.sys | acdriver.sys | acdrv.sys | adaptivaclientcache32.sys | adaptivaclientcache64.sys |
| adcvcsnt.sys | adspiderdoc.sys | aefilter.sys | agentrtm64.sys | agfsmon.sys |
| agseclock.sys | agsyslock.sys | ahkamflt.sys | ahksvpro.sys | ahkusbfw.sys |
| ahnrghlh.sys | aictracedrv_am.sys | airship-filter.sys | ajfsprot.sys | alcapture.sys |
| alfaff.sys | altcbt.sys | amfd.sys | amfsm.sys | amm6460.sys |
| amm8660.sys | amsfilter.sys | amznmon.sys | antileakfilter.sys | antispyfilter.sys |
| anvfsm.sys | apexsqlfilterdriver.sys | appcheckd.sys | appguard.sys | appvmon.sys |
| arfmonnt.sys | arta.sys | arwflt.sys | asgard.sys | ashavscan.sys |
| asiofms.sys | aswfsblk.sys | aswmonflt.sys | aswsnx.sys | aswsp.sys |
| aszfltnt.sys | atamptnt.sys | atc.sys | atdragent.sys | atdragent64.sys |
| aternityregistryhook.sys | atflt.sys | atrsdfw.sys | auditflt.sys | aupdrv.sys |
| avapsfd.sys | avc3.sys | avckf.sys | avfsmn.sys | avgmfi64.sys |
| avgmfrs.sys | avgmfx64.sys | avgmfx86.sys | avgntflt.sys | avgtpx64.sys |
| avgtpx86.sys | avipbb.sys | avkmgr.sys | avmf.sys | awarecore.sys |
| axfltdrv.sys | axfsysmon.sys | ayfilter.sys | b9kernel.sys | backupreader.sys |
| bamfltr.sys | bapfecpt.sys | bbfilter.sys | bd0003.sys | bddevflt.sys |
| bdfiledefend.sys | bdfilespy.sys | bdfm.sys | bdfsfltr.sys | bdprivmon.sys |
| bdrdfolder.sys | bdsdkit.sys | bdsfilter.sys | bdsflt.sys | bdsvm.sys |
| bdsysmon.sys | bedaisy.sys | bemk.sys | bfaccess.sys | bfilter.sys |
| bfmon.sys | bhdrvx64.sys | bhdrvx86.sys | bhkavka.sys | bhkavki.sys |
| bkavautoflt.sys | bkavsdflt.sys | blackbirdfsa.sys | blackcat.sys | bmfsdrv.sys |
| bmregdrv.sys | boscmflt.sys | bosfsfltr.sys | bouncer.sys | boxifier.sys |
| brcow_x_x_x_x.sys | brfilter.sys | brnfilelock.sys | brnseclock.sys | browsermon.sys |
| bsrfsflt.sys | bssaudit.sys | bsyaed.sys | bsyar.sys | bsydf.sys |
| bsyirmf.sys | bsyrtm.sys | bsysp.sys | bsywl.sys | bwfsdrv.sys |
| bzsenspdrv.sys | bzsenth.sys | bzsenyaradrv.sys | caadflt.sys | caavfltr.sys |
| cancelsafe.sys | carbonblackk.sys | catflt.sys | catmf.sys | cbelam.sys |
| cbfilter20.sys | cbfltfs4.sys | cbfsfilter2017.sys | cbfsfilter2020.sys | cbsampledrv.sys |
| cdo.sys | cdrrsflt.sys | cdsgfsfilter.sys | centrifyfsf.sys | cfrmd.sys |
| cfsfdrv | cgwmf.sys | change.sys | changelog.sys | chemometecfilter.sys |
| ciscoampcefwdriver.sys | ciscoampheurdriver.sys | ciscosam.sys | clumiochangeblockmf.sys | cmdccav.sys |
| cmdcwagt.sys | cmdguard.sys | cmdmnefs.sys | cmflt.sys | code42filter.sys |
| codex.sys | conduantfsfltr.sys | containermonitor.sys | cpavfilter.sys | cpavkernel.sys |
| cpepmon.sys | crexecprev.sys | crncache32.sys | crncache64.sys | crnsysm.sys |
| cruncopy.sys | csaam.sys | csaav.sys | csacentr.sys | csaenh.sys |
| csagent.sys | csareg.sys | csascr.sys | csbfilter.sys | csdevicecontrol.sys |
| csfirmwareanalysis.sys | csflt.sys | csmon.sys | cssdlp.sys | ctamflt.sys |
| ctifile.sys | ctinet.sys | ctrpamon.sys | ctx.sys | cvcbt.sys |
| cvofflineflt32.sys | cvofflineflt64.sys | cvsflt.sys | cwdriver.sys | cwmem2k64.sys |
| cybkerneltracker.sys | cylancedrv64.sys | cyoptics.sys | cyprotectdrv32.sys | cyprotectdrv64.sys |
| cytmon.sys | cyverak.sys | cyvrfsfd.sys | cyvrlpc.sys | cyvrmtgn.sys |
| datanow_driver.sys | dattofsf.sys | da_ctl.sys | dcfafilter.sys | dcfsgrd.sys |
| dcsnaprestore.sys | deepinsfs.sys | delete_flt.sys | devmonminifilter.sys | dfmfilter.sys |
| dgedriver.sys | dgfilter.sys | dgsafe.sys | dhwatchdog.sys | diflt.sys |
| diskactmon.sys | dkdrv.sys | dkrtwrt.sys | dktlfsmf.sys | dnafsmonitor.sys |
| docvmonk.sys | docvmonk64.sys | dpmfilter.sys | drbdlock.sys | drivesentryfilterdriver2lite.sys |
| drsfile.sys | drvhookcsmf.sys | drvhookcsmf_amd64.sys | drwebfwflt.sys | drwebfwft.sys |
| dsark.sys | dsdriver.sys | dsfemon.sys | dsflt.sys | dsfltfs.sys |
| dskmn.sys | dtdsel.sys | dtpl.sys | dwprot.sys | dwshield.sys |
| dwshield64.sys | eamonm.sys | easeflt.sys | easyanticheat.sys | eaw.sys |
| ecatdriver.sys | edevmon.sys | ednemfsfilter.sys | edrdrv.sys | edrsensor.sys |
| edsigk.sys | eectrl.sys | eetd32.sys | eetd64.sys | eeyehv.sys |
| eeyehv64.sys | egambit.sys | egfilterk.sys | egminflt.sys | egnfsflt.sys |
| ehdrv.sys | elock2fsctldriver.sys | emxdrv2.sys | enigmafilemondriver.sys | enmon.sys |
| epdrv.sys | epfw.sys | epfwwfp.sys | epicfilter.sys | epklib.sys |
| epp64.sys | epregflt.sys | eps.sys | epsmn.sys | equ8_helper.sys |
| eraser.sys | esensor.sys | esprobe.sys | estprmon.sys | estprp.sys |
| estregmon.sys | estregp.sys | estrkmon.sys | estrkr.sys | eventmon.sys |
| evmf.sys | evscase.sys | excfs.sys | exprevdriver.sys | failattach.sys |
| failmount.sys | fam.sys | fangcloud_autolock_driver.sys | fapmonitor.sys | farflt.sys |
| farwflt.sys | fasdriver | fcnotify.sys | fcontrol.sys | fdrtrace.sys |
| fekern.sys | fencry.sys | ffcfilt.sys | ffdriver.sys | fildds.sys |
| filefilter.sys | fileflt.sys | fileguard.sys | filehubagent.sys | filemon.sys |
| filemonitor.sys | filenamevalidator.sys | filescan.sys | filesharemon.sys | filesightmf.sys |
| filesystemcbt.sys | filetrace.sys | file_monitor.sys | file_protector.sys | file_tracker.sys |
| filrdriver.sys | fim.sys | fiometer.sys | fiopolicyfilter.sys | fjgsdis2.sys |
| fjseparettifilterredirect.sys | flashaccelfs.sys | flightrecorder.sys | fltrs329.sys | flyfs.sys |
| fmdrive.sys | fmkkc.sys | fmm.sys | fortiaptfilter.sys | fortimon2.sys |
| fortirmon.sys | fortishield.sys | fpav_rtp.sys | fpepflt.sys | fsafilter.sys |
| fsatp.sys | fsfilter.sys | fsgk.sys | fshs.sys | fsmon.sys |
| fsmonitor.sys | fsnk.sys | fsrfilter.sys | fstrace.sys | fsulgk.sys |
| fsw31rj1.sys | gagsecurity.sys | gbpkm.sys | gcffilter.sys | gddcv.sys |
| gefcmp.sys | gemma.sys | geprotection.sys | ggc.sys | gibepcore.sys |
| gkff.sys | gkff64.sys | gkpfcb.sys | gkpfcb64.sys | gofsmf.sys |
| gpminifilter.sys | groundling32.sys | groundling64.sys | gtkdrv.sys | gumhfilter.sys |
| gzflt.sys | hafsnk.sys | hbflt.sys | hbfsfltr.sys | hcp_kernel_acq.sys |
| hdcorrelatefdrv.sys | hdfilemon.sys | hdransomoffdrv.sys | hdrfs.sys | heimdall.sys |
| hexisfsmonitor.sys | hfileflt.sys | hiofs.sys | hmpalert.sys | hookcentre.sys |
| hooksys.sys | hpreg.sys | hsmltmon.sys | hsmltwhl.sys | hssfwhl.sys |
| hvlminifilter.sys | ibr2fsk.sys | iccfileioad.sys | iccfilteraudit.sys | iccfiltersc.sys |
| icfclientflt.sys | icrlmonitor.sys | iderafilterdriver.sys | ielcp.sys | ieslp.sys |
| ifs64.sys | ignis.sys | iguard.sys | iiscache.sys | ikfilesec.sys |
| im.sys | imffilter.sys | imfilter.sys | imgguard.sys | immflex.sys |
| immunetprotect.sys | immunetselfprotect.sys | inisbdrv64.sys | ino_fltr.sys | intelcas.sys |
| intmfs.sys | inuse.sys | invprotectdrv.sys | invprotectdrv64.sys | ionmonwdrv.sys |
| iothorfs.sys | ipcomfltr.sys | ipfilter.sys | iprotect.sys | iridiumswitch.sys |
| irongatefd.sys | isafekrnl.sys | isafekrnlmon.sys | isafermon | isecureflt.sys |
| isedrv.sys | isfpdrv.sys | isirmfmon.sys | isregflt.sys | isregflt64.sys |
| issfltr.sys | issregistry.sys | it2drv.sys | it2reg.sys | ivappmon.sys |
| iwdmfs.sys | iwhlp.sys | iwhlp2.sys | iwhlpxp.sys | jdppsf.sys |
| jdppwf.sys | jkppob.sys | jkppok.sys | jkpppf.sys | jkppxk.sys |
| k7sentry.sys | kavnsi.sys | kawachfsminifilter.sys | kc3.sys | kconv.sys |
| kernelagent32.sys | kewf.sys | kfac.sys | kfileflt.sys | kisknl.sys |
| klam.sys | klbg.sys | klboot.sys | kldback.sys | kldlinf.sys |
| kldtool.sys | klfdefsf.sys | klflt.sys | klgse.sys | klhk.sys |
| klif.sys | klifaa.sys | klifks.sys | klifsm.sys | klrsps.sys |
| klsnsr.sys | klupd_klif_arkmon.sys | kmkuflt.sys | kmnwch.sys | kmxagent.sys |
| kmxfile.sys | kmxsbx.sys | ksfsflt.sys | ktfsfilter.sys | ktsyncfsflt.sys |
| kubwksp.sys | lafs.sys | lbd.sys | lbprotect.sys | lcgadmon.sys |
| lcgfile.sys | lcgfilemon.sys | lcmadmon.sys | lcmfile.sys | lcmfilemon.sys |
| lcmprintmon.sys | ldsecdrv.sys | libwamf.sys | livedrivefilter.sys | llfilter.sys |
| lmdriver.sys | lnvscenter.sys | locksmith.sys | lragentmf.sys | lrtp.sys |
| magicbackupmonitor.sys | magicprotect.sys | majoradvapi.sys | marspy.sys | maxcryptmon.sys |
| maxproc64.sys | maxprotector.sys | mbae64.sys | mbam.sys | mbamchameleon.sys |
| mbamshuriken.sys | mbamswissarmy.sys | mbamwatchdog.sys | mblmon.sys | mcfilemon32.sys |
| mcfilemon64.sys | mcstrg.sys | mearwfltdriver.sys | message.sys | mfdriver.sys |
| mfeaack.sys | mfeaskm.sys | mfeavfk.sys | mfeclnrk.sys | mfeelamk.sys |
| mfefirek.sys | mfehidk.sys | mfencbdc.sys | mfencfilter.sys | mfencoas.sys |
| mfencrk.sys | mfeplk.sys | mfewfpk.sys | miniicpt.sys | minispy.sys |
| minitrc.sys | mlsaff.sys | mmpsy32.sys | mmpsy64.sys | monsterk.sys |
| mozycorpfilter.sys | mozyenterprisefilter.sys | mozyentfilter.sys | mozyhomefilter.sys | mozynextfilter.sys |
| mozyoemfilter.sys | mozyprofilter.sys | mpfilter.sys | mpkernel.sys | mpksldrv.sys |
| mpxmon.sys | mracdrv.sys | mrxgoogle.sys | mscan-rt.sys | msiodrv4.sys |
| msixpackagingtoolmonitor.sys | msnfsflt.sys | mspy.sys | mssecflt.sys | mtsvcdf.sys |
| mumdi.sys | mwac.sys | mwatcher.sys | mwfsmfltr.sys | mydlpmf.sys |
| namechanger.sys | nanoavmf.sys | naswsp.sys | ndgdmk.sys | neokerbyfilter |
| netaccctrl.sys | netaccctrl64.sys | netguard.sys | netpeeker.sys | ngscan.sys |
| nlcbhelpi64.sys | nlcbhelpx64.sys | nlcbhelpx86.sys | nlxff.sys | nmlhssrv01.sys |
| nmpfilter.sys | nntinfo.sys | novashield.sys | nowonmf.sys | npetw.sys |
| nprosec.sys | npxgd.sys | npxgd64.sys | nravwka.sys | nrcomgrdka.sys |
| nrcomgrdki.sys | nregsec.sys | nrpmonka.sys | nrpmonki.sys | nsminflt.sys |
| nsminflt64.sys | ntest.sys | ntfsf.sys | ntguard.sys | ntps_fa.sys |
| nullfilter.sys | nvcmflt.sys | nvmon.sys | nwedriver.sys | nxfsmon.sys |
| nxrmflt.sys | oadevice.sys | oavfm.sys | oczminifilter.sys | odfsfilter.sys |
| odfsfimfilter.sys | odfstokenfilter.sys | offsm.sys | omfltlh.sys | osiris.sys |
| ospfile_mini.sys | ospmon.sys | parity.sys | passthrough.sys | path8flt.sys |
| pavdrv.sys | pcpifd.sys | pctcore.sys | pctcore64.sys | pdgenfam.sys |
| pecfilter.sys | perfectworldanticheatsys.sys | pervac.sys | pfkrnl.sys | pfracdrv.sys |
| pgpfs.sys | pgpwdefs.sys | phantomd.sys | phdcbtdrv.sys | pkgfilter.sys |
| pkticpt.sys | plgfltr.sys | plpoffdrv.sys | pointguardvista64f.sys | pointguardvistaf.sys |
| pointguardvistar32.sys | pointguardvistar64.sys | procmon11.sys | proggerdriver.sys | psacfileaccessfilter.sys |
| pscff.sys | psgdflt.sys | psgfoctrl.sys | psinfile.sys | psinproc.sys |
| psisolator.sys | pwipf6.sys | pwprotect.sys | pzdrvxp.sys | qdocumentref.sys |
| qfapflt.sys | qfilter.sys | qfimdvr.sys | qfmon.sys | qminspec.sys |
| qmon.sys | qqprotect.sys | qqprotectx64.sys | qqsysmon.sys | qqsysmonx64.sys |
| qutmdrv.sys | ranpodfs.sys | ransomdefensexxx.sys | ransomdetect.sys | reaqtor.sys |
| redlight.sys | regguard.sys | reghook.sys | regmonex.sys | repdrv.sys |
| repmon.sys | revefltmgr.sys | reveprocprotection.sys | revonetdriver.sys | rflog.sys |
| rgnt.sys | rmdiskmon.sys | rmphvmonitor.sys | rpwatcher.sys | rrmon32.sys |
| rrmon64.sys | rsfdrv.sys | rsflt.sys | rspcrtw.sys | rsrtw.sys |
| rswctrl.sys | rswmon.sys | rtologon.sys | rtw.sys | ruaff.sys |
| rubrikfileaudit.sys | ruidiskfs.sys | ruieye.sys | ruifileaccess.sys | ruimachine.sys |
| ruiminispy.sys | rvsavd.sys | rvsmon.sys | rw7fsflt.sys | rwchangedrv.sys |
| ryfilter.sys | ryguard.sys | safe-agent.sys | safsfilter.sys | sagntflt.sys |
| sahara.sys | sakfile.sys | sakmfile.sys | samflt.sys | samsungrapidfsfltr.sys |
| sanddriver.sys | santa.sys | sascan.sys | savant.sys | savonaccess.sys |
| scaegis.sys | scauthfsflt.sys | scauthiodrv.sys | scensemon.sys | scfltr.sys |
| scifsflt.sys | sciptflt.sys | sconnect.sys | scred.sys | sdactmon.sys |
| sddrvldr.sys | sdvfilter.sys | se46filter.sys | secdodriver.sys | secone_filemon10.sys |
| secone_proc10.sys | secone_reg10.sys | secone_usb.sys | secrmm.sys | secufile.sys |
| secure_os.sys | secure_os_mf.sys | securofsd_x64.sys | sefo.sys | segf.sys |
| segiraflt.sys | segmd.sys | segmp.sys | sentinelmonitor.sys | serdr.sys |
| serfs.sys | sfac.sys | sfavflt.sys | sfdfilter.sys | sfpmonitor.sys |
| sgresflt.sys | shdlpmedia.sys | shdlpsf.sys | sheedantivirusfilterdriver.sys | sheedselfprotection.sys |
| shldflt.sys | si32_file.sys | si64_file.sys | sieflt.sys | simrep.sys |
| sisipsfilefilter | sk.sys | skyamdrv.sys | skyrgdrv.sys | skywpdrv.sys |
| slb_guard.sys | sld.sys | smbresilfilter.sys | smdrvnt.sys | sndacs.sys |
| snexequota.sys | snilog.sys | snimg.sys | snscore.sys | snsrflt.sys |
| sodatpfl.sys | softfilterxxx.sys | soidriver.sys | solitkm.sys | sonar.sys |
| sophosdt2.sys | sophosed.sys | sophosntplwf.sys | sophossupport.sys | spbbcdrv.sys |
| spellmon.sys | spider3g.sys | spiderg3.sys | spiminifilter.sys | spotlight.sys |
| sprtdrv.sys | sqlsafefilterdriver.sys | srminifilterdrv.sys | srtsp.sys | srtsp64.sys |
| srtspit.sys | ssfmonm.sys | ssrfsf.sys | ssvhook.sys | stcvsm.sys |
| stegoprotect.sys | stest.sys | stflt.sys | stkrnl64.sys | storagedrv.sys |
| strapvista.sys | strapvista64.sys | svcbt.sys | swcommfltr.sys | swfsfltr.sys |
| swfsfltrv2.sys | swin.sys | symafr.sys | symefa.sys | symefa64.sys |
| symefasi.sys | symevent.sys | symevent64x86.sys | symevnt.sys | symevnt32.sys |
| symhsm.sys | symrg.sys | sysdiag.sys | sysmon.sys | sysmondrv.sys |
| sysplant.sys | szardrv.sys | szdfmdrv.sys | szdfmdrv_usb.sys | szedrdrv.sys |
| szpcmdrv.sys | taniumrecorderdrv.sys | taobserveflt.sys | tbfsfilt.sys | tbmninifilter.sys |
| tbrdrv.sys | tdevflt.sys | tedrdrv.sys | tenrsafe2.sys | tesmon.sys |
| tesxnginx.sys | tesxporter.sys | tffregnt.sys | tfsflt.sys | tgfsmf.sys |
| thetta.sys | thfilter.sys | threatstackfim.sys | tkdac2k.sys | tkdacxp.sys |
| tkdacxp64.sys | tkfsavxp.sys | tkfsavxp64.sys | tkfsft.sys | tkfsft64.sys |
| tkpcftcb.sys | tkpcftcb64.sys | tkpl2k.sys | tkpl2k64.sys | tksp2k.sys |
| tkspxp.sys | tkspxp64.sys | tmactmon.sys | tmcomm.sys | tmesflt.sys |
| tmevtmgr.sys | tmeyes.sys | tmfsdrv2.sys | tmkmsnsr.sys | tmnciesc.sys |
| tmpreflt.sys | tmumh.sys | tmums.sys | tmusa.sys | tmxpflt.sys |
| topdogfsfilt.sys | trace.sys | trfsfilter.sys | tritiumfltr.sys | trpmnflt.sys |
| trufos.sys | trustededgeffd.sys | tsifilemon.sys | tss.sys | tstfilter.sys |
| tstfsredir.sys | tstregredir.sys | tsyscare.sys | tvdriver.sys | tvfiltr.sys |
| tvmfltr.sys | tvptfile.sys | tvspfltr.sys | twbdcfilter.sys | txfilefilter.sys |
| txregmon.sys | uamflt.sys | ucafltdriver.sys | ufdfilter.sys | uncheater.sys |
| upguardrealtime.sys | usbl_ifsfltr.sys | usbpdh.sys | usbtest.sys | uvmcifsf.sys |
| uwfreg.sys | uwfs.sys | v3flt2k.sys | v3flu2k.sys | v3ift2k.sys |
| v3iftmnt.sys | v3mifint.sys | varpffmon.sys | vast.sys | vcdriv.sys |
| vchle.sys | vcmfilter.sys | vcreg.sys | veeamfct.sys | vfdrv.sys |
| vfilefilter.sys | vfpd.sys | vfsenc.sys | vhddelta.sys | vhdtrack.sys |
| vidderfs.sys | vintmfs.sys | virtfile.sys | virtualagent.sys | vk_fsf.sys |
| vlflt.sys | vmwvvpfsd.sys | vollock.sys | vpdrvnt.sys | vradfil2.sys |
| vraptdef.sys | vraptflt.sys | vrarnflt.sys | vrbbdflt.sys | vrexpdrv.sys |
| vrfsftm.sys | vrfsftmx.sys | vrnsfilter.sys | vrsdam.sys | vrsdcore.sys |
| vrsdetri.sys | vrsdetrix.sys | vrsdfmx.sys | vrvbrfsfilter.sys | vsepflt.sys |
| vsscanner.sys | vtsysflt.sys | vxfsrep.sys | wats_se.sys | wbfilter.sys |
| wcsdriver.sys | wdcfilter.sys | wdfilter.sys | wdocsafe.sys | wfp_mrt.sys |
| wgfile.sys | whiteshield.sys | windbdrv.sys | windd.sys | winfladrv.sys |
| winflahdrv.sys | winfldrv.sys | winfpdrv.sys | winload.sys | winteonminifilter.sys |
| wiper.sys | wlminisecmod.sys | wntgpdrv.sys | wraekernel.sys | wrcore.sys |
| wrcore.x64.sys | wrdwizfileprot.sys | wrdwizregprot.sys | wrdwizscanner.sys | wrdwizsecure64.sys |
| wrkrn.sys | wrpfv.sys | wsafefilter.sys | wscm.sys | xcpl.sys |
| xendowflt.sys | xfsgk.sys | xhunter1.sys | xhunter64.sys | xiaobaifs.sys |
| xiaobaifsr.sys | xkfsfd.sys | xoiv8x64.sys | xomfcbt8x64.sys | yahoostorage.sys |
| yfsd.sys | yfsd2.sys | yfsdr.sys | yfsrd.sys | zampit_ml.sys |
| zesfsmf.sys | zqfilter.sys | zsfprt.sys | zwasatom.sys | zwpxesvr.sys |
| zxfsfilt.sys | zyfm.sys | zzpensys.sys |
Further reading
For the latest security research from the Microsoft Threat Intelligence community, check out the Microsoft Threat Intelligence Blog: https://aka.ms/threatintelblog .
To get notified about new publications and to join discussions on social media, follow us on Twitter at https://twitter.com/MsftSecIntel .
Related Posts

- Best practices
Why a proactive detection and incident response plan is crucial for your organization
Matt Suiche of Magnet Forensics talks about top security threats for organizations and strategies for effective incident response.

- Threat actors
Volt Typhoon targets US critical infrastructure with living-off-the-land techniques
Chinese state-sponsored actor Volt Typhoon is using stealthy techniques to target US critical infrastructure, conduct espionage, and dwell in compromised environments.

Guidance for investigating attacks using CVE-2022-21894: The BlackLotus campaign
This guide provides steps that organizations can take to assess whether users have been targeted or compromised by threat actors exploiting CVE-2022-21894 via a Unified Extensible Firmware Interface (UEFI) bootkit called BlackLotus.

- Security operations
Why you should practice rollbacks to prevent data loss in a ransomware attack
Tanya Janca, Founder and Chief Executive Officer of We Hack Purple, shares insights on application security and offers strategies to protect against data loss from ransomware attacks.
Cyber Case Study: UVM Health Network Ransomware Attack
by Kelli Young | Dec 6, 2021 | Case Study , Cyber Liability Insurance
In October 2020, the University of Vermont (UVM) Health Network—a six-hospital health care organization that serves over 1 million patients throughout Vermont and upstate New York—discovered that its systems had been compromised by cybercriminals in a ransomware attack. The UVM Health Network ransomware attack led to major disruptions across the organization’s infrastructure, shutting down critical technology and delaying patient care.
This attack—which ultimately stemmed from an employee error—resulted in significant recovery costs and reputational damages for UVM Health Network, emphasizing the severity of cyber incidents within the health care industry. There are various cybersecurity lessons that organizations can learn by reviewing the details of this incident, its impact and the mistakes UVM Health Network made along the way.
The Details of the UVM Health Network Ransomware Attack
At the beginning of October 2020, a UVM Health Network employee took their work laptop on vacation with them. During this vacation, the employee used the laptop to check their personal emails. One of these emails was from the employee’s local homeowners association. Although the email seemed legitimate, the homeowners association had recently been hacked by cybercriminals. As a result, the email was actually a phishing scam. By opening the email, the employee unknowingly allowed cybercriminals to launch malware on their work laptop. When the employee came back to work and connected their laptop to the UVM Health Network’s systems, the cybercriminals then utilized that malware to target the entire organization.
While the text file didn’t contain a specific ransom demand, UVM Health Network’s IT department was fairly confident that contacting the cybercriminals would only result in such a demand—a demand that the organization did not want to satisfy. After all, there was no guarantee that the cybercriminals would actually restore the organization’s systems and data after the ransom was paid. Therefore, instead of complying with the cybercriminals’ orders, the organization contacted the FBI for assistance. From there, UVM Health Network worked closely with the FBI to identify the source of the attack and resolve the incident. In the coming weeks, Vermont Gov. Phil Scott also deployed the state’s National Guard to further assist in the matter.
Fortunately, the organization confirmed that no sensitive data (e.g., patient records or employee information) was stolen or exposed during the attack. Rather, UVM Health Network’s existing cybersecurity measures allowed the organization to regain access to most of its data through safely stored back-up copies. Nevertheless, the attack still largely disrupted the organization’s operations for several weeks while it worked to fully recover its data, remove the malware (as well as any digital backdoors created by the malware) from all infected technology and rebuild its damaged infrastructure. During this time, hundreds of employees were unable to perform their job responsibilities due to the computer and phone systems remaining shut down. What’s worse, many patients faced delayed test results, experienced appointment cancellations and had to reschedule elective medical procedures while UVM Health Network recovered from the incident. In total, it took multiple months for the organization to totally restore its infrastructure.
The Impact of the UVM Health Network Ransomware Attack
UVM Health Network ransomware attack caused a range of consequences, including the following:
Recovery costs and lost revenue The organization incurred significant recovery expenses as a result of the attack. This includes costs related to UVM Health Network rebuilding 1,300 damaged servers, restoring 600 disabled applications, scanning and cleaning 5,000 malware-ridden computers, and repopulating its overall infrastructure with backed-up data. In addition, the organization lost a considerable amount of revenue in the time it took to recover from the incident—totaling nearly $1.5 million per day. As a whole, the attack is estimated to have cost UVM Health Network over $63 million . These costs greatly exceeded the organization’s existing cyber insurance protection, as it was only insured for $30 million.
Reputational damages Apart from recovery expenses, the organization encountered widespread scrutiny due to the attack. Specifically, UVM Health Network was criticized for allowing employees to access their personal emails on workplace devices—a flaw that essentially led to the incident. Although the organization’s existing cybersecurity measures effectively prevented the attack from resulting in a data breach, UVM Health Network was still scrutinized for its lengthy incident recovery process, especially considering that this process resulted in delayed patient care.
Delayed system updates Lastly, the attack forced the organization to modify its timeline for rolling out an updated electronic health record system. This system was intended to replace the organization’s current patchwork of health record applications and create a more integrated system to be utilized for both inpatient and outpatient care. While UVM Health Network had already implemented the first phase of this rollout in November 2019, the second and third phases were pushed back to November 2021 and April 2022, respectively.
Lessons Learned
There are several cybersecurity takeaways from the UVM Health Network ransomware attack. In particular, the incident showcased these key lessons:
Employee education can’t be ignored. Employees are often the first line of defense against cyberattacks. In fact, as many as 90% of such attacks stem from human error. This issue was certainly emphasized during UVM Health Network’s cyber incident. If the organization had educated its employees on safe email protocols and phishing detection measures, it’s possible that this attack could have been avoided altogether. As such, it’s crucial to share the following cybersecurity best practices with employees:
- Avoid opening or responding to emails from unfamiliar individuals or organizations. If an email claims to be from a trusted source, verify their identity by double-checking the address.
- Never click on suspicious links or pop-ups, whether they’re in an email or on a website. Don’t download attachments or software programs from unknown sources or locations.
- Utilize unique, complicated passwords for all workplace accounts. Never share credentials or other sensitive information online.
- Only browse safe and secure websites on workplace devices. Refrain from using these devices for answering personal emails or browsing the internet on topics unrelated to work.
- Contact a supervisor or the IT department if suspicious activity arises.
Effective secu rity software is a must. After the attack, UVM Health Network made it a priority to block employees’ access to their personal emails on all workplace devices, as well as equip this technology with more advanced security software. While this software may seem like an expensive investment, it’s worth it to minimize the impacts of potentially devastating cyber incidents. Software to consider includes network-monitoring systems, antivirus programs, firewalls, endpoint-detection products and patch-management tools. Also, it’s valuable to conduct routine penetration testing to determine whether this software possesses any security gaps. If such testing reveals any problems, these issues should be addressed immediately.
Cyber incident response plans make a difference. UVM Health Network took an extended period of time to recover from this incident, ultimately increasing disruption concerns, delaying patient care and compounding the overall costs of the attack. Such lengthy recovery issues highlight how essential it is to have an effective cyber incident response plan in place. This type of plan can help an organization establish timely response protocols for remaining operational and mitigating losses amid a cyber event. A successful incident response plan should outline potential cyberattack scenarios, methods for maintaining key functions during these scenarios and the individuals responsible for carrying out such functions. This plan should be routinely reviewed through different activities—such as tabletop exercises—to ensure effectiveness and identify ongoing vulnerabilities. Based on the results from these activities, the plan should be adjusted as needed.

Proper coverage can provide much-needed protection. Finally, this attack made it clear that no organization—not even a major health care organization—is immune to cyber-related losses. That’s why it’s crucial to ensure adequate protection against potential cyber incidents by securing proper coverage. Considering how expensive cyber events can be (especially ransomware attacks), it’s best to carefully select a policy limit that will provide sufficient protection amid a costly incident. Consult a trusted insurance professional when navigating these coverage decisions.
We are here to help.
If you’d like additional information and resources, we’re here to help you analyze your needs and make the right coverage decisions to protect your operations from unnecessary risk. You can download a free copy of our eBook , or if you’re ready to make Cyber Liability Insurance a part of your insurance portfolio, Request a Proposal or download our Cyber & Data Breach Insurance Application and we’ll get to work for you.
Recent Posts
- The Value of Inland Marine Insurance
- Cyber Solutions: Defending AI Systems From Malicious Data Poisoning Attacks
- Live Well Work Well – August 2024
- Cybersecurity Awareness Programs: Benefits and Implementation
- Cyber Case Study: Colonial Pipeline Ransomware Attack
- Search Menu
- Sign in through your institution
- Editor's Choice
- Author Guidelines
- Submission Site
- Open Access
- About Journal of Cybersecurity
- Editorial Board
- Advertising and Corporate Services
- Journals Career Network
- Self-Archiving Policy
- Journals on Oxford Academic
- Books on Oxford Academic

Article Contents
Introduction, review of prior work, hypotheses development, research method and analysis of findings, interpretation and discussion, conclusions, acknowledgements, appendix 1: profile of participant organizations and corresponding attacks characteristics, appendix 2: sample interview questions (phase 1), appendix 3: impact assessment exercise exemplar, appendix 4: sample interview questions (phase 2), appendix 5: criteria used to assess the security posture of organizations, appendix 6: security posture exemplars, appendix 7: profile of organizations.
- < Previous
An empirical study of ransomware attacks on organizations: an assessment of severity and salient factors affecting vulnerability
- Article contents
- Figures & tables
- Supplementary Data
Lena Yuryna Connolly, David S Wall, Michael Lang, Bruce Oddson, An empirical study of ransomware attacks on organizations: an assessment of severity and salient factors affecting vulnerability, Journal of Cybersecurity , Volume 6, Issue 1, 2020, tyaa023, https://doi.org/10.1093/cybsec/tyaa023
- Permissions Icon Permissions
This study looks at the experiences of organizations that have fallen victim to ransomware attacks. Using quantitative and qualitative data of 55 ransomware cases drawn from 50 organizations in the UK and North America, we assessed the severity of the crypto-ransomware attacks experienced and looked at various factors to test if they had an influence on the degree of severity. An organization’s size was found to have no effect on the degree of severity of the attack, but the sector was found to be relevant, with private sector organizations feeling the pain much more severely than those in the public sector. Moreover, an organization’s security posture influences the degree of severity of a ransomware attack. We did not find that the attack target (i.e. human or machine) or the crypto-ransomware propagation class had any significant bearing on the severity of the outcome, but attacks that were purposefully directed at specific victims wreaked more damage than opportunistic ones.
In recent years, Europol’s annual Internet Organised Crime Threat Assessment report has consistently identified ransomware as a top priority; their latest bulletin states that ‘ransomware remains one of the, if not the, most dominant threats, especially for public and private organisations within as well as outside Europe’ [ 1 ]. Furthermore, as starkly evidenced by an international survey of 5000 IT managers, the incidence of ransomware attacks is growing exponentially [ 2 ]. Similar trends have been observed by government and law enforcement bodies [ 3 , 4 ]. Ransomware attacks can potentially generate substantial financial rewards for offenders, but the ransom – which in most cases is not paid – is just a fraction of the overall cost of the attack in terms of reputational damage and loss of business [ 3 , 5 ].
Since ransomware first arrived on the scene in a major way about the year 2013, the volume of academic literature produced on this topic has mushroomed. Important advances such as sophisticated detection methods and innovative intrusion prevention systems have been put forward. Organizations are advised to implement effective security education, introduce policies and technical controls, install antivirus software, promote strong e-mail hygiene, upgrade old systems, execute regular patching, apply the ‘least privileges’ approach, segregate the network perimeter and implement effective backup practices [ 6 , 7 ]. Although the aforementioned types of work are of tremendous importance to a preventative strategy, they are not by themselves sufficient. This is because most of the research on ransomware to date has focused primarily on its technical aspects, with comparatively little attention being given to understanding the socio-technical side of the attack or the characteristics of organizations [ 8 ]. So, while there is a strong emphasis on developing ransomware countermeasures, there is a lack of studies that examine the real experiences of organizations that have actually fallen victim to ransomware attacks.
It may be tempting to assume certain things about what makes an organization more or less vulnerable to an attack, but we should not be so presumptuous. Although research on cybercrime victimization has significantly expanded over the past two decades, the majority of studies focus on individual-level offences such as online bullying, harassment and stalking. Holt and Bossler [ 9 ] make the point that for some types of cybercrime, such as malware and ransomware, our understanding of what causes individuals and organizations to fall victim is not well developed. Our work addresses this limitation by focusing on ransomware crime and collecting data from the actual victims of ransomware.
Generally, the risk of cybercrime victimization has been addressed by studying characteristics of the offender [ 10 ], the victim [ 11 ] and the crime itself [ 12 ]. Our article focuses on the latter two and is motivated by several calls in the literature to better understand typical victims of ransomware attacks, with a view towards developing solutions that prevent or mitigate this sinister problem [ 9 , 13 , 14 ].
To date, only a small number of studies have directly looked at the experiences of organizations that have fallen victim to ransomware. Of these few (see Table 1 ), the majority consider things at a rather cursory level. Our study, which is based on a substantial sample of 55 ransomware attacks and draws upon qualitative and quantitative data, helps to address this gap in the literature by presenting detailed findings on the antecedents and consequences of actual ransomware attacks within 50 organizations. Our objectives were to
Previous empirical studies of ransomware attacks on organizations
| Authors . | Country . | Method . | Sample . | Main findings . |
|---|---|---|---|---|
| Choi . [ ] | USA | Quantitative analysis of secondary data | 13 reported attacks on police departments from 2013 to 2016 | Online lifestyle and cybersecurity stance contribute to ransomware victimization |
| Zhao . [ ] | USA | Mixed methods case study: questionnaire and interviews | Medical students and surgeons in a hospital that experienced a SamSam ransomware attack (29 survey respondents; 8 interviewees) | Students who are ‘digital natives’ were seriously stressed by lack of access to electronic resources and were not well adapted to adjust to paper-based workflows |
| Zhang-Kennedy . [ ] | USA | Mixed methods case study: questionnaire and interviews | Staff and students in a large university that experienced a ransomware attack at a critical time (150 survey respondents; 30 interviewees) | It took several days to recover basic services and the after-effects on user productivity were felt for a considerable time afterward. Substantial data loss and emotional effects on staff. |
| Hull . [ ] | UK | Mixed methods: questionnaire and interviews | 46 questionnaire respondents and 8 interviews (university staff, students and SMEs) | Universities are more likely to be attacked than SMEs; ransomware victims only had basic defences in place |
| Shinde . [ ] | The Netherlands | Mixed methods: questionnaire and interviews | Snowball sample of 23 individuals and 2 semi-structured interviews | Most ransomware attacks use an untargeted ‘shotgun’ approach; security awareness among victims was low |
| Ioanid . [ ] | Romania | Questionnaire | Survey of 123 SMEs | Organization size and turnover is positively correlated with number of attacks; manager education is key prevention factor |
| Byrne and Thorpe [ ] | Ireland | Brief interviews | Three organizations that had suffered attacks | E-mail filtering software had been removed because of the overhead it was placing on IT departments; in the wake of attacks, security training and awareness programmes were ramped up. |
| Riglietti [ ] | Not stated | Content analysis of discussions | 301 posts extracted from four online security blogs | Content analysis technique can increase our understanding of security challenges within organizations |
| Authors . | Country . | Method . | Sample . | Main findings . |
|---|---|---|---|---|
| Choi . [ ] | USA | Quantitative analysis of secondary data | 13 reported attacks on police departments from 2013 to 2016 | Online lifestyle and cybersecurity stance contribute to ransomware victimization |
| Zhao . [ ] | USA | Mixed methods case study: questionnaire and interviews | Medical students and surgeons in a hospital that experienced a SamSam ransomware attack (29 survey respondents; 8 interviewees) | Students who are ‘digital natives’ were seriously stressed by lack of access to electronic resources and were not well adapted to adjust to paper-based workflows |
| Zhang-Kennedy . [ ] | USA | Mixed methods case study: questionnaire and interviews | Staff and students in a large university that experienced a ransomware attack at a critical time (150 survey respondents; 30 interviewees) | It took several days to recover basic services and the after-effects on user productivity were felt for a considerable time afterward. Substantial data loss and emotional effects on staff. |
| Hull . [ ] | UK | Mixed methods: questionnaire and interviews | 46 questionnaire respondents and 8 interviews (university staff, students and SMEs) | Universities are more likely to be attacked than SMEs; ransomware victims only had basic defences in place |
| Shinde . [ ] | The Netherlands | Mixed methods: questionnaire and interviews | Snowball sample of 23 individuals and 2 semi-structured interviews | Most ransomware attacks use an untargeted ‘shotgun’ approach; security awareness among victims was low |
| Ioanid . [ ] | Romania | Questionnaire | Survey of 123 SMEs | Organization size and turnover is positively correlated with number of attacks; manager education is key prevention factor |
| Byrne and Thorpe [ ] | Ireland | Brief interviews | Three organizations that had suffered attacks | E-mail filtering software had been removed because of the overhead it was placing on IT departments; in the wake of attacks, security training and awareness programmes were ramped up. |
| Riglietti [ ] | Not stated | Content analysis of discussions | 301 posts extracted from four online security blogs | Content analysis technique can increase our understanding of security challenges within organizations |
Assess the degree of severity of ransomware attacks within organizations;
Explore how characteristics of the organization and characteristics of the attack affect the severity of the outcome.
Within the literature on cybercrime in general, there have been various efforts to understand the factors that make individuals more prone to becoming victims. Drawing upon Lifestyle Theory and Routine Activity Theory, Agustina [ 23 ] proposes several behavioural and environmental factors that should, in theory at least, elevate the risk of being victimized. In practice, however, as found by Ngo and Paternoster [ 24 ], these theories do not hold up to empirical scrutiny. Our work differs from these previous studies in two ways: first, we are looking not at cybercrime in general, but specifically at ransomware attacks; secondly, our focus is not on individual victims, but rather on organizations.
Although several reports [ 1–4 ] suggest that the number of ransomware attacks against businesses continues to rise steadily, it is hard to form any clear sense of the true extent of ransomware attacks. The difficulty of accurately measuring and comparing cybercrime rates has been remarked upon by Furnell et al . [ 25 ]. Statistics about the incidence of ransomware attacks vary wildly. In an international study based on 574 participants across 77 countries, BCI [ 26 ] reported that 31% of respondents had been afflicted by ransomware. In contrast, a large-scale survey of Internet users in Germany revealed that only 3.6% of individuals had suffered a ransomware attack [ 27 ]. Simoiu et al . [ 5 ] estimated that about 2–3% of their sample of 1180 American adults were hit by ransomware between 2016 and 2017. Similarly, Ioanid et al . [ 20 ] reported that 2% of their sample of 103 Romanian small-to-medium enterprises (SMEs) were affected by the WannaCry attack that year. Against those low incidence rates, Hull et al . [ 18 ] found that as many as 61% of UK respondents had experienced at least one attack, and Shinde et al . [ 19 ] reported that 20% of respondents to their survey in the Netherlands were victims of ransomware, although it must be acknowledged that both those studies were based on quite small samples. All of these conflicting survey findings create a rather muddled picture. This, of course, can be put down to differences in sampling methods, response rates, temporal factors and units of analysis, but our essential point is this: it is generally agreed that ransomware presents a grave threat and has adversely affected many organizations, yet we know very little about the experiences of organizations that were attacked or the root causes that left them open to a successful violation.
There are very few empirical studies of the impact of ransomware within organizations or the factors that make organizations vulnerable. Al-Rimy et al . [ 28 ] present a literature survey of ransomware threat success factors, but the scope of their work extends only to infection vectors and enabling technologies (i.e. cryptography techniques, payment methods, ransomware development kits). They do not consider any organizational or socio-technical factors.
Our extensive search of the literature revealed just a handful of studies that looked directly at the experiences of organizations that were victims of ransomware (see Table 1 ). To summarize the key findings of these studies: ransomware attacks had major financial and emotional impact on victims, and the common factors that led to the attacks seemed to be a lack of security education or diligence, with organization type and size also emerging as possible factors impacting the likelihood of an attack.
Byrne and Thorpe [ 21 ] observe that ‘there is a gap in the literature with regards to examining the issue [of ransomware] from a company's perspective and that of its user base.’ Our study aims to make a contribution towards addressing this gap. In the next sections, we present a number of factors that we believe might affect the vulnerability of an organization to a ransomware attack, as well as characteristics of the attack weapon and method that could affect the severity of impact.
Organization characteristics: size and sector
As with so much of the reported facts and figures pertaining to ransomware, there is disagreement as to whether an organization’s size makes it more or less susceptible to attack. An international survey conducted by BCI [ 26 ] found that ransomware attacks are a substantially more common problem for large enterprises than they are for SMEs. However, contradictory findings are reported by Beazley [ 27 ] who state that SMEs were disproportionately hit by ransomware attacks in 2018, with 71% of all infections occurring within such organizations.
Many SMEs based in the UK believe that they are not likely to be targeted by ransomware attacks; while they place high value on the importance of IT to their business, they are generally not worried about the threat of data loss [ 29 , 30 ]. SMEs, by their entrepreneurial nature, are more likely to engage in risk-taking behaviour [ 31 ]. However, SMEs may underestimate the value to hackers of their information systems and may not realize that they could be targeted as a hop to gain entry into their partners’ networks. As Smith [ 32 ] puts it, ‘even if you think your company has nothing worth stealing, losing access to all your data is no longer an unlikely event.’ Kurpjuhn [ 33 ] makes the point that SMEs must accept that they are exposed to similar levels of risk as large enterprises but have lower budgets and lesser resources to address those risks.
An argument could be made that larger organizations, simply because they employ more people, are at greater risk of infection due to human error; it only takes one reckless act by a single individual to compromise an entire network. Although not quite the same thing, Bergmann et al . [ 34 ] found no correlation between the size of a household and the rate of cybercrime victimization experienced by members of that household. How that finding would scale up to larger units in a non-domestic setting is a matter of conjecture, but it seems reasonable to assume that the potential for human error increases relative to the size of the unit.
Hypothesis 1a: An organization’s size influences the impact severity of a ransomware attack.
Hypothesis 1b : An organization’s sector influences the impact severity of a ransomware attack.
Security posture
Because ransomware combines technical and social characteristics to create its impact, we explore the organizational victim responses to attacks through the lens of ‘security posture’. Security posture is defined as ‘the security status of an enterprise’s networks, information, and systems based on information assurance resources (e.g., people, hardware, software, policies) and capabilities in place to manage the defense of the enterprise and to react as the situation changes’ [ 36 ]. Prior research into ransomware attacks on organizations shows that a lack of basic security practices, or failure to comply with them, was a common failing [ 15 , 18 ]. Organizations that do not have adequate and effective backup strategies are much more likely to end up having to pay the ransom to retrieve their data [ 15 , 28 ]. Connolly and Wall [ 8 ] developed a taxonomy of ransomware countermeasures, emphasizing a multi-layered approach in protecting organizations against ransomware.
While technical defence mechanisms are very important, so too is individual behaviour and good ‘online lifestyle’. Inadequate care by employees when choosing to open e-mail attachments or hyperlinks, downloading ‘free’ versions of software or cracked games, browsing adult content or illegal sports live streams, and installing apps from untrusted sources are all examples of poor online hygiene that can increase the risk of a ransomware infection. Riglietti [ 28 ] observed that ‘looking at what users say, avoiding infection appears to be a matter of spreading the right security culture within an organisation rather than a technical issue.’ A key part of this is education and awareness [ 37 , 38 ]. In their studies of ransomware victims, Shinde et al . [ 19 ] and Zhang-Kennedy et al . [ 27 ] both observed a tendency by employees to assume that cybersecurity was essentially the responsibility of the IT Department. While it is to be expected that the IT Department should take the lead on security and actively promote a strong posture, there is an onus on individuals to utilize good personal security practices and not engage in irresponsible behaviour.
Hypothesis 1c: An organization’s security posture influences the impact severity of a ransomware attack.
Crypto-ransomware propagation class
Since crypto-ransomware was incapable of propagating on networks prior to 2013, we decided to create a simple taxonomy according to the degree of infectiousness (see Table 2 ). Different propagation classes of crypto-ransomware may have a lesser or greater effect on the outcome of a crypto-ransomware attack as a result of the volume of infection spread.
Classification by crypto-ransomware propagation
| Crypto-ransomware propagation class . | Description . | Examples . |
|---|---|---|
| Generation I | Early variants of crypto-ransomware were not able to spread on networks and had limited propagation capabilities even within an infected machine (prior 2013). | AIDS Information GPCoder |
| Generation II | First emerged in 2013, this type can propagate by taking advantage of network paths. Generation II crypto-ransomware can encrypt devices that are physically and logically (e.g. ‘write’ access to server shares) connected to the infected machine. A common attack vector of Generation II crypto-ransomware is a malicious e-mail. | CryptoLocker CryptoWall CryptoDefence |
| Generation III.a (Trojans) | First emerged in 2016, this type uses various tools (e.g. password-stealer Mimikatz) and takes advantage of network weaknesses to propagate on infected networks. These variants can infect entire networks, completely crippling an organization’s ability to function. Generation III.a crypto-ransomware normally penetrates network via vulnerable servers. | Samas BitPaymer |
| Generation III.b (Worms) | First emerged in 2017, Generation III.b crypto-ransomware, also commonly referred as ‘crypto-worms’, takes advantage of software vulnerabilities. Similar to variants like Samas and BitPaymer, crypto-worms can infect entire networks. | WannaCry NotPetya |
| Crypto-ransomware propagation class . | Description . | Examples . |
|---|---|---|
| Generation I | Early variants of crypto-ransomware were not able to spread on networks and had limited propagation capabilities even within an infected machine (prior 2013). | AIDS Information GPCoder |
| Generation II | First emerged in 2013, this type can propagate by taking advantage of network paths. Generation II crypto-ransomware can encrypt devices that are physically and logically (e.g. ‘write’ access to server shares) connected to the infected machine. A common attack vector of Generation II crypto-ransomware is a malicious e-mail. | CryptoLocker CryptoWall CryptoDefence |
| Generation III.a (Trojans) | First emerged in 2016, this type uses various tools (e.g. password-stealer Mimikatz) and takes advantage of network weaknesses to propagate on infected networks. These variants can infect entire networks, completely crippling an organization’s ability to function. Generation III.a crypto-ransomware normally penetrates network via vulnerable servers. | Samas BitPaymer |
| Generation III.b (Worms) | First emerged in 2017, Generation III.b crypto-ransomware, also commonly referred as ‘crypto-worms’, takes advantage of software vulnerabilities. Similar to variants like Samas and BitPaymer, crypto-worms can infect entire networks. | WannaCry NotPetya |
What we term ‘Generation I’ crypto-ransomware was not particularly effective in extorting money due to several technological shortcomings, such as the use of easy-to-break encryption, inefficient management of decryption keys and limited propagation capabilities. It is highly likely that Generation I variants are obsolete.
We refer to variants such as CryptoWall, CryptoLocker and CryptoDefence as ‘Generation II’. These forms of ransomware initially penetrate networks via desktops or laptops and subsequently take advantage of the local user security context to spread via network paths, encrypting network shares that the user has ‘write’ access to. They can also encrypt devices physically connected to the infected machine.
What we refer to as ‘Generation III.a’ malware are those such as Samas and BitPaymer that tend to breach networks via vulnerabilities found in servers [e.g. a weak password in Remote Desktop Protocol (RDP)]. Once inside the server, attackers manually and/or automatically search for various weaknesses within the network (e.g. poor authentication controls, a flat network structure, the lack of network visibility and detection mechanisms). Such vulnerabilities permit attackers to stay undetected and hijack multiple devices and the entire network in some cases. Crypto-worms like WannaCry (‘Generation III.b’ in our classification) have a similar devastating effect, the chief difference being that they take advantage exclusively of software vulnerabilities in order to propagate.
Hypothesis 2a: The crypto-ransomware propagation class influences the impact severity of a ransomware attack.
Attack type and target
Hypothesis 2b : The attack type, i.e. opportunistic or targeted, influences the impact severity of a ransomware attack.
Hypothesis 2c : The attack target, i.e. human or machine, influences the impact severity of a ransomware attack
This study used a mixed methods approach following an exploratory sequential design [ 43 ]. Phase 1 was qualitative. In order to assess the degree of severity of ransomware attacks (our first objective), we required a measurement instrument. A literature search revealed that there are no readily available tools for this particular purpose. Since crypto-ransomware incidents entail some unique consequences (e.g. encrypted data, disabled systems), we could not use substitutes from other cybercrime studies; the assessment instrument had to be specific to crypto-ransomware attacks. Hence, the aim of Phase 1 was to inductively develop an Impact Assessment Instrument (grounded in empirical data) that can be used to effectively evaluate the severity of crypto-ransomware attacks on organizations in our sample. In Phase 2, we gathered additional quantitative data so as to be able to statistically test our hypotheses.
The Ethics Committee at the University of Leeds approved this research. Consent forms were signed by all study participants. All necessary precautions were followed to ensure the anonymity of study participants and the confidentiality of collected data. The majority of participants were from the UK but there were also a few from North America. Where the names of organizations are subsequently referred to in this article, aliases are used to protect the anonymity of respondents (see Appendix 1 ). Additionally, interviewees from UK Police Cybercrime Units are given the aliases of CyberRM, CyberLM, CyberTL, CyberBR, CyberBL, CyberTR and CyberCU. Incidents took place between 2014 and 2018.
Sampling strategy and data collection
A purposeful sampling approach was employed to collect data in Phase 1. We conducted 10 semi-structured interviews with professionals from organizations that became victims of ransomware attacks. Interviewees were IT/Security Managers and Executive Managers with an average of 17 years of professional experience. There was one respondent per organization. Since some organizations were attacked more than once, accounts of 15 ransomware incidents were elicited from 10 organizations. Appendix 1 (please refer to first 15 incidents) contains information about the characteristics of attacks and organizations that were interviewed in Phase 1.
In order to enhance the reliability and richness of data, we sought access to individuals who had direct experience of responding to crypto-ransomware incidents. As for crypto-ransomware attacks, the key selection criteria was to include a range of consequences for the victims, varying from low severity (e.g. minimum disruption to business, minimum loss of information, swift recovery) to high impact (e.g. business disruption that lasted for several months, significant loss of critical information, slow recovery).
An interview guide was designed with the aim to learn about participants’ perceptions of the attacks’ impact and the factors that aggravated or moderated the consequences of these incidents. This exercise guided the development of the Impact Assessment Instrument. Since we planned to use these initial 15 cases in Phase 2 of data analyses, we also ensured to collect profile information about organizations (e.g. size, sector and industry), causes of crypto-ransomware attacks, information about security postures and characteristics of attacks (e.g. attack type, crypto-ransomware propagation class and attack vector). Sample interview questions are provided in Appendix 2 . Six interviews were conducted face-to-face, three via Skype with overseas respondents and one via e-mail correspondence.
The decision to stop data collection in qualitative research is made when additional insights are not emerging with new observations. This point is typically achieved after a dozen or so observations [ 44 ]. We felt that after examining about 10 ransomware incidents, the incremental learning stopped. But to ensure that the point of ‘theoretical saturation’ is sufficiently reached, we collected data on 15 cases in total.
Impact Assessment Instrument development (qualitative data analysis)
An inductive content analysis method was used to analyse data and develop the Impact Assessment Instrument. Within the interview transcripts, the impact of crypto-ransomware incidents emerged as a major topic. Interviewees eagerly described their experiences of being attacked, particularly focusing on the consequences of crypto-ransomware attacks. For example, respondents from GovSecJN, EducInstFB, LawEnfM, GovSecA and HealthSerJU spoke in great detail about the despair and distress they experienced. An IT/Security Manager from GovSecJN, a large public sector organization, explained how business continuity disruption affected them:
There was an impact on service delivery – we could not do what we were supposed to do. It was significant for us. Besides, all our resources were directed towards the incident instead of doing our job.
An IT/Security Manager from LawEnfJU reported a similar experience:
Ransomware encrypted all of our data files, which, in effect, took the agency offline for about 10 days. This was extremely critical as we could not do our job. We had the server up-and-running in 10 days and then it took another 10 days to manually re-enter all data. So, the attack critically affected the operations of the department for about 20 days … . The overall impact of this attack was severe, definitely.
An Executive Manager from EducInstFB, a large public organization, shared with us that a Generation III.a crypto-ransomware encrypted hundreds of machines (desktops, laptops and servers). As a result, several critical business functions were disabled and important data were inaccessible. The victim disclosed that various security holes – including ineffective backups, poor patching regimes, the lack of network visibility and feeble access control management practices – led to infection and subsequent dramatic consequences.
GovSecA, a large public organization, suffered an unprecedented attack by Generation III.a crypto-ransomware, where close on 100 servers got encrypted, affecting the operations of the organization for months. Most importantly, the victim lost a lot of critical data because they only had partial backups. At the time of the interview, GovSecA was already in post-attack recovery for 8 months. The interviewee shared that the recovery was still not completed at this point. An IT/Security Manager from GovSecA described their experience as follows:
We all came back to work on Tuesday morning after a bank holiday weekend and the sun was streaming in through the windows. The cleaners have been in, the office looked great. Everyone felt refreshed after the long weekend. And it took a while for us to realise what happened; that all computing had been turned to stone [encrypted]. Virtually nothing was left untouched. If half of the building had fallen off, you would understand that something has happened. But everything looked great. But it was not – the organisation could not operate.
An Executive Police Officer from LawEnfM, a public SME, described how the organization suffered two ransomware attacks within 2 weeks, affecting critical data:
We are a full-service law enforcement agency and we have a wide variety of data, some of which is very sensitive. For example, data relevant to criminal incidents like manslaughter cases, child pornography, child sex cases. Several months worth of this data was encrypted, which was pretty significant to us … . While we were recovering after the first attack, we were very unfortunate to get infected by ransomware again.
Comments such as in these few selected excerpts featured regularly in the interviews. We observed that when victims described the impact of ransomware attacks, they focused on factors such as business continuity disruption, recovery time, the number of devices affected, how critical encrypted information was to business and information loss.
On the contrary, interviewees from LawEnfJ and GovSecJ talked about factors that effectively saved the organization from far worse outcomes and emphasized that organizations must be prepared for these attacks or suffer severe consequences. For example, an IT/Security Manager from LawEnfJ, a public SME, shared the following:
We practice good basic security principles. We have backups in multiple locations … . It comes down to basics like staying up to date with industry. Just recently we went through this massive patching for Intel processors and other processes that could be leveraged into a whole host of attacks … . We were well-prepared for the attack … . We restored everything over a weekend. We were infected on Friday and back up-and-running on Monday.
Similarly, an IT/Security Manager from GovSecJ, a large public organization, explained how they were able to recover with little inconvenience:
An Incident Management Plan is crucial during cyber-attacks. Instead of running around with our hands up in the area, screaming for help, our response was logical and structured … . We lost some data due to incremental backups but nothing significant that would have stopped an organisation from functioning … . The infection took place at approximately 9 in the morning. By the end of the day, data was restored, and everything was back to normal.
As a result of our data analysis in Phase 1, five categories of negative outcomes emerged from the data, namely ‘business continuity disruption timeline’, ‘recovery time’, ‘affected devices’, ‘encrypted information critical to business’ and ‘information loss’. Under each of these categories, the data enabled us to build impact descriptors ranging across three degrees of severity (low, medium and high). In Table 3 , we present the severity descriptors for the five impact categories and corresponding attacks.
Impact Assessment Instrument and corresponding victims
| Impact item . | Degree of severity (3-point ordinal scale) | ||
|---|---|---|---|
| 1 = Low . | 2 = Medium . | 3 = High . | |
| Business continuity disruption timeframe | Up to 1 week | Up to 2 weeks | More than 2 weeks |
| Recovery time | Up to 1 week | Up to 1 month | Several months or more, if at all |
| Affected devices | One or more user devices, possibly including shares on one or more servers | Several devices and more than one server; or where a central server is encrypted affecting not just individual users but the functioning of a whole department | All or majority of devices, completely or almost completely crippling IT systems |
| Encrypted information critical to business | Some data compromised, but nothing critical | Data critical to some business functions of low to medium priority | Data critical to majority of business functions, or some high priority function(s) |
| Information loss | No loss, or some loss acceptable with incremental backups | Loss affecting some critical business functions | Loss affecting all or majority of critical business functions |
| Impact item . | Degree of severity (3-point ordinal scale) | ||
|---|---|---|---|
| 1 = Low . | 2 = Medium . | 3 = High . | |
| Business continuity disruption timeframe | Up to 1 week | Up to 2 weeks | More than 2 weeks |
| Recovery time | Up to 1 week | Up to 1 month | Several months or more, if at all |
| Affected devices | One or more user devices, possibly including shares on one or more servers | Several devices and more than one server; or where a central server is encrypted affecting not just individual users but the functioning of a whole department | All or majority of devices, completely or almost completely crippling IT systems |
| Encrypted information critical to business | Some data compromised, but nothing critical | Data critical to some business functions of low to medium priority | Data critical to majority of business functions, or some high priority function(s) |
| Information loss | No loss, or some loss acceptable with incremental backups | Loss affecting some critical business functions | Loss affecting all or majority of critical business functions |
Given the broad range of organization types and sectors in our sample, we anticipated that it would be difficult to arrive at a consensus on what constitutes ‘Low’, ‘Medium’ and ‘High’ levels of severity. For example, an outcome that might be regarded as being of ‘Low’ severity by one respondent could possibly be regarded as ‘High’ by another, depending on the nature of their business and level of dependency on critical IT systems. However, there was a remarkable degree of consistency among the respondents. There is a general acceptance that any ransomware attack, however minor, is likely to result in an interruption of at least a few days rather than hours. Thus, recovery times and business continuity disruption of a number of days (up to a week) were rated as being on the ‘Low’ end of the spectrum because, although any disruption is traumatic, in relative terms that is the least amount of time that is expected to be lost. As one interviewee put it,
Considering the impact and seriousness of the ransomware, it is going to sound strange, but I think that to only lose twelve hours worth of data is an acceptable outcome. If we had not backed up, we would have lost 47,000 files, clearly that would have been a far more significant issue. (IT/Security Manager, GovSecJN)
The Impact Assessment Instrument presented in Table 3 is derived from empirical data and reflects the actual consequences of crypto-ransomware attacks as described by the victims. All five of the items shown in the table are components of the overall severity of a ransomware attack. Because the five items are measured on a three-point ordinal scale, as opposed to a multiple-point continuous scale, we used the ordinal alpha coefficient [ 45 ] to test for internal reliability. The value for ordinal α = 0.96 which indicates a high degree of agreement between the five items.
To compute a composite score for overall severity, we considered using the average or median of the five items but decided to use the maximum. The logic behind this reasoning is that if any of the items is evaluated as ‘High’, it means that the attack represented a serious shock to the organization with major consequences. Therefore, a ‘High’ severity value for any single item trumps all the others, even if they all have lesser values. This also gets around the aforementioned problem whereby the assessment instrument might misevaluate a particular item as ‘Low’ when in fact, because of the organization’s circumstances, it should be ‘High’; in such cases, the likelihood is that at least one other item would have a ‘High’ rating and hence the overall severity would correctly be evaluated as ‘High’.
Next, using the Impact Assessment Instrument shown in Table 3 , we analysed all of the initial 15 cases (interview transcripts) to determine the extent of the attack impact. We assigned the degree of severity for all five categories for each impact item. An exemplar of this assessment exercise is provided in Appendix 3 .
We were conscious of the limitation that the initial version of the Impact Assessment Instrument was based on data collected from 10 public organizations, with no private businesses. To remedy this, as we collected data on a further 45 cases, including both public and private organizations, we asked interviewees to assess the severity of ransomware attacks using our scale (i.e. low, medium, high) and comment on the reasons for their answer. The purpose of this exercise was to validate our instrument and confirm that the categories that emerged initially were relevant across the whole sample. We also validated the instrument by consulting with experienced police officers. We found that the instrument gave a reliable measure of the severity of an incident as perceived by the victim.
In order to test our hypotheses, we required to collect more data on crypto-ransomware incidents. It has been widely acknowledged that collecting data on cyberattacks is extremely difficult. In Phase 1, it took us over 6 months to find organizations that were willing to share sensitive matters relevant to the attacks. Therefore, we made a decision to approach the data collection matter differently in Phase 2. Instead, we sought out police officers from UK Cybercrime Units who had extensive experience in dealing with crypto-ransomware attacks. Mainly, such experience included helping organizations to effectively respond to the attacks, understanding what caused them, providing emotional support to victims if necessary and offering post-attack advice. Our expectation was that each police officer would be able to provide relevant information on several ransomware incidents at the time, which would make the process of data collection more manageable.
We succeeded to connect with 10 police officers (four Detective Sergeants and six Detective Constables) and 1 Civilian Cybercrime Investigator, who provided information on 22 usable ransomware incidents via semi-structured interviews and one focus group. Two police officers were interviewed twice as they were able to add new information. The average professional experience of the study respondents was 19 years. We also managed to collect data on 22 more cases with a Detective Inspector, who, unfortunately, was not able to meet with us face-to-face but agreed to provide data via a structured questionnaire (sent over e-mail). Additionally, we interviewed an IT/Security Manager with over 20 years of professional experience, which added one final case to our database of ransomware incidents. Relevant information is available in Appendix 1 (Cases 16–60). Due to the aforementioned access constraints, a snowballing technique was used to collect data for Phase 2.
The questionnaire and second phase interview guide (see Appendix 4 ) were based on the Impact Assessment Instrument and hypotheses. We asked questions that would help us to assess the impact of an attack. We also collected profile information on organizations (e.g. size, sector and industry) and characteristics of attacks (e.g. attack type, crypto-ransomware propagation class and attack target). Additionally, we included questions that would help us classify the security posture of each organization. For this purpose, we used the taxonomy of crypto-ransomware countermeasures developed in our previous work [ 8 ]. The headings from this taxonomy served as a guide for questions. Therefore, in order to assess a security posture of organization victims, we asked interviewees about security education, policies and practices, technical measures and network security, the incident response strategy and the attitudes of management towards cybersecurity (see Appendix 5 ).
Overall, 45 additional cases of ransomware attacks were examined in Phase 2, bringing the total to 60 cases. For five of the 60 cases, there was insufficient data to be able to determine the overall impact severity, so those cases were discarded as being unusable, leaving us with 55 usable cases. Although a snowballing technique was used to collect data in Phase 2, our overall sample included organizations of different sizes and from different sectors. Attacks were recorded against both humans and machines by different crypto-ransomware propagation classes. Different levels of security posture were noted among participants, ranging from weak to strong. Finally, the sample contained opportunistic attacks as well as targeted ones.
For a few of the cases, we did not have values for all of the five items in the Impact Assessment; in those cases, we evaluated the overall impact based on the maximum of the items for which we had values, supported by an inspection of qualitative data from those cases. We found that this method of computing the composite score for overall severity gave the most accurate results, as validated using participants’ personal assessment of the attack impact and our own judgement based on what we gleaned from interviews. Results of the assessment exercise are available in Table 4 .
Impact Assessment Instrument and observed frequencies among respondents ( n = 55)
| Impact item . | Degree of severity (3-point ordinal scale) | ||
|---|---|---|---|
| 1 = Low . | 2 = Medium . | 3 = High . | |
| Business continuity disruption timeframe ( = 52) | Up to 1 week (65%) | Up to 2 weeks (14%) | More than 2 weeks (21%) |
| Recovery time ( = 51) | Up to 1 week (59%) | Up to 1 month (22%) | Several months or more, if at all (19%) |
| Affected devices ( = 53) | One or more user devices, possibly including shares on one or more servers (53%) | Several devices and more than one server; or where a central server is encrypted affecting not just individual users but the functioning of a whole department (19%) | All or majority of devices, completely or almost completely crippling IT systems (28%) |
| Encrypted information critical to business ( = 51) | Some data compromised, but nothing critical (29%) | Data critical to some business functions of low to medium priority (24%) | Data critical to majority of business functions, or some high priority function(s) (47%) |
| Information loss ( = 47) | No loss or some loss acceptable with incremental backups (57%) | Loss affecting some critical business functions (32%) | Loss affecting all or majority of critical business functions (11%) |
| Overall impact severity (composite score) ( = 55) | Low (27%) | Medium (20%) | High (53%) |
| Impact item . | Degree of severity (3-point ordinal scale) | ||
|---|---|---|---|
| 1 = Low . | 2 = Medium . | 3 = High . | |
| Business continuity disruption timeframe ( = 52) | Up to 1 week (65%) | Up to 2 weeks (14%) | More than 2 weeks (21%) |
| Recovery time ( = 51) | Up to 1 week (59%) | Up to 1 month (22%) | Several months or more, if at all (19%) |
| Affected devices ( = 53) | One or more user devices, possibly including shares on one or more servers (53%) | Several devices and more than one server; or where a central server is encrypted affecting not just individual users but the functioning of a whole department (19%) | All or majority of devices, completely or almost completely crippling IT systems (28%) |
| Encrypted information critical to business ( = 51) | Some data compromised, but nothing critical (29%) | Data critical to some business functions of low to medium priority (24%) | Data critical to majority of business functions, or some high priority function(s) (47%) |
| Information loss ( = 47) | No loss or some loss acceptable with incremental backups (57%) | Loss affecting some critical business functions (32%) | Loss affecting all or majority of critical business functions (11%) |
| Overall impact severity (composite score) ( = 55) | Low (27%) | Medium (20%) | High (53%) |
Note: Overall n = 55 but item response rates ranged from 85% (47) to 96% (53).
Quantitative data analysis
Overall, our sample included 50 organizations of different sizes, sectors (i.e. public or private) and industries (55 usable cases of crypto-ransomware attacks). Totally, 35 (70%) of the organizations were SMEs, while 15 (30%) were large organizations. We used the European Commission guidance to define the organization’s size [ 46 ]. The industries were broad and varied, including IT, government, law enforcement, education, healthcare, financial services, construction, retail, logistics, utility providers and several other categories. Of the 50 organizations, 19 (38%) were in the public sector and 31 (62%) were in the private sector. Five (10%) were located in the North America and 45 (90%) in the UK (see Appendix 7 ). Security postures were determined for 34 of the 50 organizations (see Table 5 ). Twenty organizations (59%) had a weak security posture, 13 (38%) had a medium-security posture and only one had a strong posture. We used the criteria outlined in Appendices 5 and 6 to assess the security postures of organizations.
Cross-tabulations for Hypotheses 1a, 1 b and 1c
| . | Attack severity, (%) | ||
|---|---|---|---|
| Low . | Medium . | High . | |
| H1a: Organization size ( = 50) | |||
| SME | 7 (20) | 8 (23) | 20 (57) |
| Large | 5 (33) | 2 (13) | 8 (53) |
| H1b: Sector ( = 50) | |||
| Public | 5 (26) | 7 (37) | 7 (37) |
| Private | 7 (23) | 3 (10) | 21 (68) |
| H1c: Security posture ( = 34) | |||
| Weak | 0 (0) | 4 (20) | 16 (80) |
| Medium | 4 (31) | 6 (46) | 3 (23) |
| Strong | 1 (100) | 0 (0) | 0 (0) |
| . | Attack severity, (%) | ||
|---|---|---|---|
| Low . | Medium . | High . | |
| H1a: Organization size ( = 50) | |||
| SME | 7 (20) | 8 (23) | 20 (57) |
| Large | 5 (33) | 2 (13) | 8 (53) |
| H1b: Sector ( = 50) | |||
| Public | 5 (26) | 7 (37) | 7 (37) |
| Private | 7 (23) | 3 (10) | 21 (68) |
| H1c: Security posture ( = 34) | |||
| Weak | 0 (0) | 4 (20) | 16 (80) |
| Medium | 4 (31) | 6 (46) | 3 (23) |
| Strong | 1 (100) | 0 (0) | 0 (0) |
P < 0.05; *** P < 0.001.
Except where otherwise stated, the hypotheses were assessed using two-sided Fisher’s Exact tests. The size of our sample provides acceptable power to detect moderate-to-large relationships between categorical variables using this technique. Where data was missing, cases were excluded; the number of relevant cases ( n ) is stated in the results of each test.
We found that the degree of severity of a ransomware attack did not vary by organizational size, P = 0.542. Indeed, the majority of attacks in both SMEs and large organizations were of high severity (57% and 53%, respectively).
The severity did, however, vary according to organizational sector. Private organizations were considerably more likely than public organizations to experience serious negative consequences as a result of ransomware attacks, P = 0.044. Of the private organizations, 68% were hit by attacks of the highest severity, whereas a much lower percentage (37%) of public organizations were as badly affected. This finding supports Hypothesis 1b.
Most tellingly, impacts also varied with organizational security posture, such that those organizations with weak security postures were far more likely to experience a severe impact than were those with medium or strong postures, n = 34, P < 0.001. Of the organizations that had a weak posture, 80% had been hit by ransomware attacks of high severity. Thus, Hypothesis 1c is also supported.
Post hoc, we found that security posture did not differ according to organization size, with the majority of organizations – 57% of SMEs and 64% of large organizations – having a weak security posture. However, when looking at the relationship between organization sector and security posture, a significant difference ( P = 0.035) was observed. Public organizations had considerably stronger security postures than those in the private sector. This may partly explain why the impact of attacks on public sector organizations was not as severe.
As can be seen in Appendix 1 , the 50 organizations spanned 23 different industries (i.e. financial services, healthcare, retail, etc.) so it was not meaningful to conduct correlation analysis on this variable as the numbers were spread too thin. However, one observation that stands out is that of the seven respondents from the IT industry, six of them (86%) experienced attacks of high severity. This is above average and somewhat surprising, although with such a small sub-sample it is not possible to draw reliable inferences.
Looking then at the crypto-ransomware propagation classes, 32 (58%) were of type Generation II, while 23 (42%) were of type Generation III (Generation III.a and Generation III.b classes were merged in data analysis due to similar propagation characteristics). Totally, 38 attacks (72%) were opportunistic and 15 (28%) were targeted. Twenty-five attacks (47%) were targeted at humans and 28 (53%) aimed at machines (see Table 6 ).
Cross-tabulations for Hypotheses 2a, 2 b and 2c
| . | Attack severity, (%) | ||
|---|---|---|---|
| Low . | Medium . | High . | |
| H2a: Crypto-ransomware type ( = 55) | |||
| Generation II | 10 (31) | 8 (25) | 14 (44) |
| Generation III | 5 (22) | 3 (13) | 15 (65) |
| H2b: Attack target ( = 53) | |||
| Human | 5 (20) | 6 (24) | 14 (56) |
| Machine | 8 (29) | 5 (18) | 15 (54) |
| H2c: Attack type ( = 53) | |||
| Opportunistic | 12 (32) | 9 (24) | 17 (45) |
| Targeted | 1 (7) | 2 (13) | 12 (80) |
| . | Attack severity, (%) | ||
|---|---|---|---|
| Low . | Medium . | High . | |
| H2a: Crypto-ransomware type ( = 55) | |||
| Generation II | 10 (31) | 8 (25) | 14 (44) |
| Generation III | 5 (22) | 3 (13) | 15 (65) |
| H2b: Attack target ( = 53) | |||
| Human | 5 (20) | 6 (24) | 14 (56) |
| Machine | 8 (29) | 5 (18) | 15 (54) |
| H2c: Attack type ( = 53) | |||
| Opportunistic | 12 (32) | 9 (24) | 17 (45) |
| Targeted | 1 (7) | 2 (13) | 12 (80) |
P < 0.1.
The degree of severity did not vary with the crypto-ransomware propagation class (i.e. Generation II vs. Generation III) n = 55, P = 0.334, nor with the attack target (i.e. human vs. machine), n = 53, P = 0.813.
The type of the attack (opportunistic vs. targeted) was also considered. Targeted attacks were more likely than opportunistic ones to lead to severe consequences, n = 53, P = 0.063. 80% of targeted attacks gave rise to impacts of high severity, whereas a considerably lower proportion of opportunistic attacks (45%) had high negative consequences. This difference is statistically significant (Mann–Whitney U = 177, P = 0.02) so we are inclined to accept Hypothesis 2b.
Post hoc, companies with a weak posture were much more likely to be targeted via machine vulnerabilities as a point of entry, whereas companies with medium or strong security postures were more likely to be attacked via social engineering tricks ( n = 34, P = 0.019). We also observed that 91% of targeted attacks were against organizations that had weak security posture. Table 7 demonstrates results of hypotheses tests.
Results of hypothesis tests
| Hypothesis . | Result . |
|---|---|
| Hypothesis 1a: An organization’s size influences the degree of severity of a ransomware attack | Rejected |
| Hypothesis 1b: An organization’s sector influences the degree of severity of a ransomware attack | Accepted |
| Hypothesis 1c: An organization’s security posture influences the degree of severity of a ransomware attack | Accepted |
| Hypothesis 2a: The crypto-ransomware propagation class influences the impact severity of a ransomware attack | Rejected |
| Hypothesis 2b: The attack type, i.e. opportunistic or targeted, influences the degree of severity of a ransomware attack | Accepted |
| Hypothesis 2c: The attack target, i.e. human or machine, influences the degree of severity of a ransomware attack | Rejected |
| Hypothesis . | Result . |
|---|---|
| Hypothesis 1a: An organization’s size influences the degree of severity of a ransomware attack | Rejected |
| Hypothesis 1b: An organization’s sector influences the degree of severity of a ransomware attack | Accepted |
| Hypothesis 1c: An organization’s security posture influences the degree of severity of a ransomware attack | Accepted |
| Hypothesis 2a: The crypto-ransomware propagation class influences the impact severity of a ransomware attack | Rejected |
| Hypothesis 2b: The attack type, i.e. opportunistic or targeted, influences the degree of severity of a ransomware attack | Accepted |
| Hypothesis 2c: The attack target, i.e. human or machine, influences the degree of severity of a ransomware attack | Rejected |
| Attack ID . | Crypto-ransomware propagation class; attack target; attack type . | Organization alias . | Industry; size; sector . |
|---|---|---|---|
| 1 | Generation II; human; opportunistic | LawEnfJ | Law enforcement; SME; public |
| 2 | Generation II; human; opportunistic | GovSecJN | Government; large; public |
| 3 | Generation II; machine; opportunistic | GovSecJ | Government; large; public |
| 4 | Generation II; human; opportunistic | ||
| 5 | Generation II; machine; opportunistic | ||
| 6 | Generation II; machine; opportunistic | ||
| 7 | Generation II; machine; opportunistic | EducInstF | Education; large; public |
| 8 | Generation III.a; machine; targeted | EducInstFB | Education; large; public |
| 9 | Generation II; human; opportunistic | LawEnfM | Law enforcement; SME; public |
| 10 | Generation II; human; opportunistic | ||
| 11 | Generation III.a; machine; targeted | GovSecA | Government; large; public |
| 12 | Generation II; human; opportunistic | LawEnfJU | Law enforcement; SME; public |
| 13 | Generation III.b; machine; opportunistic | HealthSerJU | Health service; large; public |
| 14 | Generation III.a; human; targeted | ||
| 15 | Generation II; human; opportunistic | LawEnfF | Law enforcement; SME; public |
| 16 | Generation II; machine; opportunistic | ITOrgA | IT; SME; private |
| 17 | Generation III.a; machine; opportunistic | ConstrSupA | Construction; SME; private |
| 18 | Generation III.a; machine; targeted | EducOrgA | Education; SME; public |
| 19 | Generation II; human; opportunistic | SecOrgM | IT; SME; private |
| 20 | Generation III.a; machine; targeted | ITOrgJL | IT; SME; private |
| 21 | Generation II; human; opportunistic | CloudProvJL | IT; SME; private |
| 22 | Generation III.a; machine; targeted | InfOrgJL | Infrastructure; SME; private |
| 23 | Generation III.a; machine; opportunistic | ConstrSupJ | Construction; SME; private |
| 24 | Generation II; human; opportunistic | RelOrgJ | Religion; SME; private |
| 25 | Generation III.a; machine; targeted | SportClubJ | Entertainment; large; private |
| 26 | Generation III.a; machine; targeted | UtilOrgD | Utilities; large; private |
| 27 | Generation III.a; e-mail; targeted | VirtOrgD | IT; SME; private |
| 28 | Generation III.a; machine; opportunistic | CleanOrgD | Cleaning; SME; private |
| 29 | Generation II; human; opportunistic | EducOrgD | Education; SME; public |
| 30 | Generation II; human; opportunistic | SerOrgD | Waste; SME; private |
| 31 | Generation III.a; machine; opportunistic | EducCompD | Education; SME; public |
| 32 | Generation III.a; machine; opportunistic | PrimOrgD | Education; SME; public |
| 33 | Generation III.a; machine; opportunistic | LogOrgD | Logistics; SME; private |
| 34 | Generation III.a; machine; opportunistic | ITCompD | IT; SME; private |
| 35 | Generation III.a; machine; opportunistic | LogWarJ | Logistics; large; private |
| 36 | Generation III.a; machine; targeted | TranspOrgJ | Transport; large; private |
| 37 | Generation II; human; targeted | CharOrgJ | Charity; SME; public |
| 38 | Generation II; human; opportunistic | EducInstJ | Education; large; public |
| 39 | Generation II; human; opportunistic | DigMedM | Retailer; SME; private |
| 40 | Generation II; human; opportunistic | ConstrSupAP | Construction; SME; private |
| 41 | Generation II; human; opportunistic | FinOrgAP | Finance; SME; private |
| 42 | Generation II; unknown; unknown | ConstrOrgAP | Construction; SME; private |
| 43 | Generation II; unknown; unknown | LetAgenAP | Letting agency; SME; private |
| 44 | Generation III.a; machine; targeted | EducOrgAP | Education; large; public |
| 45 | Generation II; human; opportunistic | ConstrArcAP | Construction; SME; private |
| 46 | Generation II; human; opportunistic | LegalOrgAP | Legal; SME; private |
| 47 | Generation II; human; opportunistic | BevOrgAP | Beverages; SME; private |
| 48 | Generation II; human; opportunistic | ChCarAP | Childcare; SME; public |
| 49 | Generation III.a; machine; opportunistic | EducPrimAP | Education; large; public |
| 50 | Generation II; human; opportunistic | RetOrgAP | Retailer; large; private |
| 51 | Generation III.a; machine; opportunistic | ||
| 52 | Generation III.a; machine; targeted | ITOrgAP | IT; SME; private |
| 53 | Generation III.a; machine; opportunistic | MarkOrgAP | Marketing; SME; private |
| 54 | Generation III.a; machine; opportunistic | ChemOrgAP | Chemical; SME; private |
| 55 | Generation III.a; machine; opportunistic | EducHscAP | Education; large; public |
| 56 | Generation III.a; machine; opportunistic | HospOrgAP | Hospitality; large; private |
| 57 | Generation II; human; opportunistic | WasteOrgAP | Waste; SME; private |
| 58 | Generation III.a; machine; opportunistic | FinCompAP | Finance; large; private |
| 59 | Generation II; human; targeted | LegAdvAP | Legal; SME; private |
| 60 | Generation III.a; machine; opportunistic | LegSolcAP | Legal; SME; private |
| Questions . |
|---|
| Can you please tell me about the attack? |
| How would you rate the attack in terms of the level of severity? |
| Was your business affected by the ransomware attack? |
| If yes, then to what extent? |
| What functions were affected? |
| Were your data affected by the ransomware attack? |
| If yes, then to what extent? |
| Did you manage to restore the data that were encrypted? |
| In your opinion, are there any other negative impacts the ransomware attack had on your organization? |
| In your opinion, was the ransomware attack effective? |
| If yes, why do you think ransomware was effective? |
| What factors contributed to the effectiveness of this attack? |
| Crypto attacks . | Category . | Item → corresponding impact level → corresponding digit . |
|---|---|---|
| Attack 1 . | Business continuity disruption timeframe . | Up to 1 week → ‘Low’ → 1 . |
| Encrypted information critical to business . | Not critical → ‘Low’ → 1 . | |
| Information loss . | Some loss acceptable with incremental backups → ‘Low’ → 1 . | |
| Affected devices . | One desktop and shares on a server → ‘Low’ → 1 . | |
| Recovery time . | Up to 2 weeks → ‘Low’ → 1 . | |
| Maximum value | 1 | |
| Attack impact level | Low | |
| Attack 9 | Business continuity disruption timeframe | Up to 1 week → ‘Low’ → 1 |
| Encrypted information critical to business | Critical to high priority functions → ‘High’ → 3 | |
| Information loss | Some loss acceptable with incremental backups → ‘Low’ → 1 | |
| Affected devices | Several desktops and shares on servers → ‘Low’ → 1 | |
| Recovery time | Up to 1 month → ‘Medium’ → 2 | |
| Maximum value | 3 | |
| Attack impact level | High | |
Organization size does not matter, ransomware is indiscriminate
Within the observed sample, organization size, by itself, did not affect the severity of attacks. As outlined in ‘Organisation characteristics: size and sector’ section, prior findings and opinions on the relationship between organization size and the incidence of ransomware attacks are rather inconsistent, with some saying that ransomware is mainly a problem for large enterprises and others saying that SMEs make up the bulk of the victims. Of the organizations that we observed, SMEs and large organizations were similarly impacted by ransomware attacks and in most cases the impact felt was of high severity. This result is consistent with interpretations expressed by police officers from UK Cybercrime Units:
Ransomware is indiscriminate. It does not choose its victims. It chooses computers and those computers can be owned by anybody. (Detective Sergeant, CyberBL)
Ransomware does not target organisations of a particular size. All organisations, small, medium and large, are equally affected. (Detective Sergeant, CyberRM)
We observed several large organizations that experienced severe consequences of crypto-ransomware attacks (e.g. EducInstFB, GovSecA, HealthSerJU, SportClubJ, etc.) as well as SMEs (e.g. LawEnfJU, LawEnfF, ITOrgA, ConstrSupA, etc.). Therefore, regardless of how large or small an organization is, there is no room for complacency. SMEs often baulk at spending their limited funds on IT security measures, weighing things up on the basis of the financial cost of countermeasures vs. the expected probability and expected impact of an attack [ 30 ]. While we cannot offer any insights into the probability of an attack, we can speak about impact. Our findings show that if an organization has weak defence mechanisms, then regardless of whether it is an indigenous start-up or a large multi-national corporation, it is likely to experience very severe consequences in the event of a ransomware attack, such as having critical systems knocked out, heavy data losses and major disruptions of several weeks or more.
Private sector organizations are more likely to experience severe effects
Private sector organizations were more likely to report severe impacts than were those in the public sector in the sample observed in this study. This finding can be explained by the very nature of public organizations as compared to private businesses. Public sector organizations are generally state-owned with an obligation to provide some universal service such as healthcare, education, policing, or civic administration. The private sector, on the contrary, is mainly composed of organizations whose ultimate purpose is not to serve the public but to generate profit. Cyberattacks on profit-driven organizations normally lead to substantial financial losses, reputational damage and loss of customers; the series of security breaches on TalkTalk is one such example [ 47 ]. If public organizations such as councils, state agencies and police departments experience a cyberattack, they may lose public confidence, but as sole suppliers they are not going to lose customers or revenue as they are publicly funded. As an IT/Security Manager from GovSecJN (a public organization fully funded by the UK government) explained:
Yes, there was a financial impact because resources were directed towards dealing with the cyber-attack. But it is difficult for us to quantify the financial impact … . The impact is different for us. It is the impact on service delivery to public. How we care for children. How we care for adults. Even road potholes – people could not report potholes because our systems were down.
Information from interviews with police officers working in the UK Cybercrime Units confirmed our impression that private sector organizations suffer more severe consequences; e.g. a specialist detective within the CyberTL unit told us based on his extensive experience that:
Cybercriminals know that the private sector depends on customer service. They know that these organisations will pay. Especially, we find that a lot of IT companies have been hit. I do not think this is because IT companies are more prone to targeting. It is just because when they are hit by ransomware, it is so much more devastating for them due to their dependency on customers.
This observation is in line with our finding that 86% of respondents from the IT industry experienced attacks of high severity. However, it should be noted that our sample is based on attack victims only and is not representative of the number of potential organizations in each industry. Additionally, public or semi-public institutions may experience an equivalent attack as being less critical simply because they are not in competition with other providers.
Against the threat of ransomware, a vigilant security posture is vital
Our hypothesis that there is a relationship between organizational security posture and attack severity was supported. Most specifically, a weak security posture leads to a preponderance of very severe attacks. This suggests that the attacks were detected late, handled badly, or inadequately isolated. Although this observation is relevant to any type of cybercrime, successful ransomware attacks entail unique and rather devastating consequences such as disabled systems, encrypted data and, subsequently, halted business operations. A security weakness that could be easily fixed might cause substantial damage to the victim and even bankruptcy. For example, LogOrgD was infected via a server vulnerability that was widely documented by academics, security vendors and government bodies. Subsequently, the organization lost access to all critical data, including backups. The victim was rapidly losing its customer base and the business was close to bankruptcy. The business owner was particularly distressed and at some point, even had suicidal thoughts – a lifetime of hard work was about to turn into ashes. Ultimately, the company managed to survive but the recovery was timely, costly and extremely challenging. Therefore, IT/Security professionals must be extremely vigilant when it comes to protecting their organizations against ransomware. There is no simple technological ‘silver bullet’ that will wipe out the crypto-ransomware threat. Rather, a multi-layered approach is needed which consists of socio-technical measures, zealous front-line managers and active support from senior management [ 8 ]. As an IT/Security Manager from LawEnfJ puts it:
You have to have the fundamentals in place. If you are talking about backups after the event, you are dead in the water. You must have your system set up in a way that actively thwarts these attacks. If you are playing catch-up, then I am sorry, but the game is over at that point. You must stay up-to-date. If you are not staying current in the industry, you are going to get in trouble really quick.
Several respondents commented that if vulnerabilities are not closed down following ransomware attacks, organizations will get attacked again. For example, GovSecJ was attacked 4 times within 6 months. Although the IT/Security Manager wrote a report recommending organizational changes, senior management did not act upon it. Subsequently, three more attacks followed.
Though LawEnfM made a decision to implement all appropriate changes following the first ransomware attack, ransomware struck second time during the recovery process, taking advantage of the same vulnerabilities. Since the organization suffered considerably as a result of two consequent attacks, the external IT provider made a decision to pay the ransom as they felt responsible. Following this devastating experience (two attacks within 2 weeks), LawEnfM made several important changes in its approach to cybersecurity. HealthSerJU had to experience two very severe attacks before senior management realized the importance of security controls and measures:
I think both attacks fundamentally came down to the fact that there was an under-appreciation of the importance of IT and, therefore, the focus on ensuring that those systems were properly protected was not there … . If we wanted to take a positive from the attacks, it would be that finally executive management gave IT a profile that it has never had before. (IT/Security Manager, HealthSerJU)
Within our sample, public organizations had considerably stronger security postures than those in the private sector. Totally, 78% of the private organizations that we looked at had weak security postures, as opposed to 38% in the public sector. This may be because public institutions have a stronger regulatory mandate to have IT security policies in place. In the UK, the Cyber Essentials scheme was introduced in 2014 and is required for all central government contracts [ 48 ]. In contrast, in the private sector, the majority of organizations do not mandate their suppliers to have cybersecurity standards in operation [ 4 ].
Of course, the promotion of security standards is one matter, adoption is another and actual compliance yet another again. In the past 12 months, 17 452 Cyber Essentials certificates were issued by the UK government [ 49 ] which, going by the estimated 2.6 million businesses in the country [ 50 ] represents just 0.7% of the population. Within higher education institutions – from which division 29% of our public sector sample was drawn – there has been considerable resistance to the uptake of the Cyber Essentials standard [ 51 ]. The ISO27001 standard has been more widely adopted in the UK, but less so in public administration and educational organizations than elsewhere [ 52 ]. The annual UK Cyber Breaches Surveys of recent years reveal that a growing number of businesses are adopting Cyber Essentials, ISO27001, or other similar policies, but it still remains at about half who have no such measures in place [ 4 ].
Ransomware attacks, even of the less sophisticated type, can wreak havoc
There was no pronounced effect of the crypto-ransomware propagation class upon attack impact in the sample examined in this study. This is an interesting finding because Generation III crypto-ransomware has the ability to propagate across large networks and completely paralyse organizational operations. As a Detective Sergeant from CyberTR pointed out:
When I first started, the virus was very specific to the machine. The machine that clicked on the email was the machine that got the virus and the ransomware and that was it. More recent variants of ransomware have the ability to spread. There is definitely a distinction between ransomware that will hit a computer and encrypt any physically connected devices such as USBs, storage devices, and it is a lot more simple, and the likes of WannaCry that will travel across networks and spread to all computers. We have seen this evolution, where suspects are using vulnerabilities to spread across networks. This type of ransomware is more prevalent than it ever was because it gives hackers an advantage.
Rationally, Generation III should bring more devastation. However, our data show otherwise. For example, SecOrgM was infected with the less sophisticated Generation II crypto-ransomware. The victim declared bankruptcy shortly after the attack because the organization did not have backups, could not operate without hijacked data and at the same time was not able to meet ransom demands. Similarly, GovSecJN was hit with the Generation II ransomware class but it had a detrimental effect on the victim. Although GovSecJN recovered relatively quickly, data critical to high priority functions was encrypted, affecting essential functions of the organization. Such organizations provide vital services to the local community and many people depend on these services.
On the contrary, EducInstFB was attacked with Generation III crypto-ransomware that infected hundreds of devices. EducInstFB and its staff lost access to an enormous volume of data, which had scientific value. Several critical systems were disabled that stopped the victim from performing their normal daily tasks. The management made a decision to pay the ransom. Although the recovery was lengthy and challenging, EducInstFB eventually repaired its systems and recovered the majority of data. Another victim of Generation III crypto-ransomware – HealthSerJU – was attacked twice and on both occasions over a thousand devices were infected. Although these attacks had a significant negative effect on the delivery of services, HealthSerJU had effective backups and, therefore, promptly restored its systems. EducOrgA was also infected with Generation III crypto-ransomware, affecting the whole network. However, due to the nature of its business, EducOrgA continued its work as a primary school and teaching activities were not interrupted (while administrative data were gradually restored).
Following these observations, we concluded that the crypto-ransomware propagation class alone may not have a direct impact on the consequences of these attacks. Rather, a combination of factors (e.g. the nature of business, availability of resources to recover data or pay the ransom, the type of systems affected, level of preparedness, etc.) are at play.
Beware the ‘weakest link’
Although Hypothesis 2c was rejected, indicating that the severity of a ransomware attack is not influenced by the attack target (i.e. human or machine), we observed that organizations with a weak posture were much more likely to be targeted via machine vulnerabilities as a point of entry, whereas those with medium or strong security postures were more likely to be attacked via social engineering tricks. This finding could be explained by the fact that many of our study participants trust that technical controls provide an adequate defence against cyberthreats, which is also a commonly accepted belief among industry professionals. Consequently, IT/Security professionals focus on implementing measures like e-mail hygiene, vulnerability and upgrade management and sophisticated monitoring and detection systems, but seemed to neglect the ‘human factor’ problem and do not have strong security education and training, the importance of which as a security countermeasure is well established [ 6 , 37 , 38 ]. Therefore, these organizations are attacked via ‘the weakest link’ – they may have an adequate defence from a technical perspective, but weak employee security practices. As the IT/Security Manager from GovSecJ put it:
Effective defence always starts with a user. You need to make sure that along with teaching people how to use your applications, IT systems, you incorporate in there a good amount of cyber security.
In our sample, 27 attacks were successful due to humans opening malicious attachments or clicking on links. Several respondents alluded to shortcomings regarding human error and made appropriate changes. For example, LawEnfM replaced online security training with face-to-face tuition after an employee failed to notice rather obvious signs of a malicious e-mail. A staff member from LawEnfJU shut down their own machine after receiving a ransom note and booted several other machines using their credentials. Although the employee hoped to solve the problem, they instead infected more machines and lost precious time to contain infection. Since then, LawEnfJU implemented a new policy that obliges employees to report any out-of-ordinary activity, no matter how insignificant it seems. The organization regularly sends its employees ‘call and verify’ warnings to remind them of this new rule. However, even with effective security education in place, humans are continually prone to make mistakes and do things they know they probably shouldn’t. For example, an employee from GovSecJN who had recently completed security training still proceeded to open an e-mail attachment, even though he felt it was quite suspicious and potentially risky.
Don’t become an easy target, be careful what you reveal about your organization
Targeted attacks were more likely than opportunistic ones to lead to severe consequences in the observed sample. This result is expected as targeted attacks require a lot of preparation, but the ‘prize’ is much higher:
There is a recent trend of a particular variant of ransomware called BitPaymer, which is seen as a big problem. It seems to me to be very targeted because cybercriminals are making extremely large demands on the businesses, which I have never seen before – £30,000 –so they are clearly very targeted. Cybercriminals know the targets they are going after. (Detective Sergeant, CyberTL)
Such attacks suggest that there is some kind of network reconnaissance behind, so cybercriminals know what company they are targeting and how much to ask for. Cybercriminals will say, ‘Wait there, your turnover is £400m so you can pay maybe £2m’. There are victims out there that have paid up to £1,000,000 or even more to get the decryption key. (Detective Constable, CyberBR)
Clearly, such extravagant amounts would have a more severe effect on an organization than, e.g. the typical £300–500 ransom. In our own sample, one small IT company (VirtOrgD) was asked to pay 75 bitcoins (approximate value £352 000 at the time of the attack), a ransom amount the victim could not afford to pay. After intense negotiations, hackers agreed to reduce the ransom amount to 65 bitcoins, but it was still too high for VirtOrgD. The victim had no choice but to recover from partial backups. In the first stages of recovery the management was not sure if the business was going to survive this attack as the VirtOrgD was rapidly losing its customer base. Through tremendous efforts of staff and with the help of external specialists, VirtOrgD managed to restore its business, although, inevitably, some substantial losses occurred. Similarly, another company (ITOrgJL) was asked to pay 100 bitcoins (approximate value of £470 000 at the time of the attack). ITOrgJL was able to negotiate the ransom down to 15 bitcoins and effectively recovered with a decryption key provided by hackers.
Both organizations VirtOrgD and ITOrgJL had weak security postures, which allowed hackers not only to penetrate their networks but also stay undetected for several days searching for loopholes to spread within the network and encrypt multiple devices, including servers that contained crucial data and systems. This confirms our observation that the majority of targeted attacks were executed against organizations that had weak security posture. The lethality of targeted attacks lies within hackers’ ability to execute network reconnaissance in order to find the most critical company’s assets (e.g. backup server, customer data, etc.) and security weaknesses that will allow to hijack these assets. It is up to organizations to take appropriate measures to avoid such dramatic consequences.
Our research findings demonstrate that several factors, including ‘organization sector’, ‘security posture’ and ‘attack type’, influence the degree of severity of ransomware attacks. More specifically, within our sample, private organizations were more likely to experience severe consequences compared to public ones. Interestingly, public organizations investigated in this study had considerably stronger security postures than those in the private sector. Private organizations typically operate to generate profit and any interruptions to services can cause grave damage to them. Public organizations, on the contrary, are funded by the government to serve the public. Subsequently, financial implications are not always relevant to them. We assert that private organizations need to recognize this vulnerability and ‘up their game’ in the security realm.
Furthermore, organizations that had weak security postures suffered harsher outcomes of ransomware attacks as opposed to companies with stronger postures. This finding indicates that the need to strengthen security postures in a bid to defend organizational assets against ransomware attacks is greater than ever. Hackers are relentlessly taking advantage of well-documented issues (e.g. RDP brute-force, poor security training, insufficient vulnerability management). It is important to note that organizations must focus on technical and non-technical controls as both are vital; one without the other is futile. As our results demonstrate, targeted attacks are mainly preying on technical shortcomings but even if all technical loopholes are closed down, hackers can still hit a potential victim by exploiting human weaknesses.
Moreover, targeted attacks brought more devastation to affected organizations in our sample compared to those who were hit opportunistically. Offenders normally invest more effort into targeted attacks and hence, expect higher yields. For example, a thorough investigation of the target may take place, so the hackers can understand how profitable the business is, what information is critical to its continuity and how much the victim can potentially afford to pay. Whether or not the victim pays, they are still going to suffer substantially. In a scenario where they pay, the ransom is going to be very high and the organization is going to experience considerable financial losses. In a situation where the victim does not pay, they are going to suffer not only financially (in many cases, recovery is more expensive than the ransom payment), but also experience significant disruptions to business operations. Therefore, it is worth making cybersecurity investments rather than face consequences of the targeted ransomware attacks. As our findings suggest, organizations with stronger security postures are less vulnerable to targeted attacks.
Our results also indicate that ‘organization size’, ‘crypto-ransomware propagation class’ and ‘attack target’ have no significant impact on the severity level of ransomware attacks. Within our sample, organizations of all sizes were afflicted by ransomware attacks, with consequences ranging from less severe (e.g. relatively short business continuity disruption timeline and insignificant information loss) to highly severe, where organizations faced a challenging recovery and, in many cases, came very close to business bankruptcy. In fact, one organization in our sample (SecOrgM) did not survive the ransomware attack. This finding underlines the indiscriminate nature of ransomware and serves as caution against common but dangerous attitudes such as ‘hackers could not possibly gain anything from attacking us – we are too small’, ‘we do not hold any state secrets or any other sensitive information that would be of interest to hackers’, ‘hackers are normally after banks as this is where the money is’, etc.
Since 2013, ransomware has evolved considerably and become much more technically advanced and dangerous. Generation III is substantially more of a menace than Generation II because of its greater degree of contagiousness and ability to self-propagate across infected networks. However, we found that the propagation class of crypto-ransomware by itself had no effect on the severity of crypto-ransomware attacks in the observed sample. Regarding the attack target (i.e. machine vs. human), crypto-ransomware equally impacts victims despite the network access method.
As ransomware attacks continue to hurt businesses around the globe, our results convey several important messages. First, we urge organizations of all sizes, small, medium and large, to strengthen their security posture. Secondly, we specifically stress that the vulnerabilities of private companies to ransomware attacks must be realized and addressed. Offenders are aware of their dependency on data and systems and take advantage of it. Thirdly, we conclude that the strength of ransomware is not in its technical capabilities and rapid evolution; rather, it lies within relentlessness of hackers who are persistently searching for a range of weaknesses within organizations. Security holes are widely exploited by perpetrators, but hackers also understand the sentimental value organizations may have to their owners who possibly spent a lifetime building their business (e.g. LogOrgD case). Criminals exploit the sense of responsibility that IT and Cyber Security professionals may experience if a company is significantly suffering from an attack (e.g. LawEnfM), or the responsibility management may feel because their staff is facing very challenging working conditions during attacks and potential harsh consequences post-attacks (e.g. EducInstFB). All of these factors inevitably make ransomware attacks ever so painful, while hackers are persistently doing their homework on potential victims; and this is why targeted attacks hit even harder.
This work makes a number of valuable contributions to the existing body of academic literature on ransomware. It increases knowledge about factors that can make crypto-ransomware attacks absolutely unbearable for affected organizations. We urge readers to learn from the experiences of victims presented in this work and take appropriate preventative actions to avoid, transfer or mitigate the risks of a crypto-ransomware attack. The article also introduces (see ‘Crypto-ransomware propagation class’ section) a simple but useful set of terms that can be used by various parties (e.g. academics, industry professionals, government bodies, etc.) to refer to different classes of this threat according to the degree of infectiousness, i.e. ‘Generation I’, ‘Generation II’, etc. Finally, we developed an Impact Assessment Instrument, which can be applied in further academic works that specifically focus on the crypto-ransomware impact.
This study has a number of limitations. As always, studying cybercrime is a challenge because researchers are faced with incomplete data, skewed surveys and questionable assumptions. The majority of our respondents were based in one country (the UK). Our sample size of 55, though respectable, is still quite small. Therefore, statistically speaking, the findings cannot be generalized outside the given sample and are only applicable within the observed 55 ransomware attacks. A logical follow-on would be to test our conclusions against a larger, more international data set – but a practical problem is how to readily obtain such data. Typically, ransomware victims do not disclose the full reality of their experiences in official complaints or incident reports [ 3 ]. Insurance companies such as Advisen have databases of incidents, but these only include organizations that were insured against cyberattacks and made claims. Unfortunately, these sorts of sampling and access issues are typical in cybersecurity research [ 25 ] and, as we earlier saw in Table 1 , it greatly complicates comparability between studies. We executed our study as rigorously as we could, combining quantitative and qualitative data, and although we believe it is robust and broadly generalizable, that is a point of conjecture.
Furthermore, in terms of limitations, in Phase 1, we interviewed one participant per organization. This is a very common limitation in qualitative data collection, where the principal interviewee typically plays the role of a ‘gatekeeper’, especially when the subject matter pertains to highly sensitive and confidential matters within the organization. We used a snowballing sampling strategy in Phase 2 of data collection which, though not ideal, was the only pragmatic way we could collect data on ransomware attacks.
As regard future research, in the next step we are planning to learn what makes ransomware so effective in a wider cybercrime eco-system. While in this study we assessed factors that make these attacks impactful, ransomware is a very complex threat and organized criminals employ various tactics to make these attacks successful. Therefore, we intend to learn about numerous vulnerabilities that cybercriminals prey on (whether technical, social or psychological), specifically focusing on victims’ decision-making processes regarding ransom payments. The ultimate purpose of this study will be to identify a series of measures that could potentially reduce ransom payments.
We would like to extend our sincere gratitude to all study participants for their invaluable contribution to this research. We greatly appreciate interviewees’ time and genuine effort. We realize some questions may have brought back emotions experienced by victims during attacks; we would like to thank you for your bravery and willingness to tell your story. It is very important that other organizations learn from your experiences. Special thanks to Robert McArdle, the Director of Cybercrime Research Team at Trend Micro, who provided expert advice on technical measures against crypto-ransomware attacks. We would like to acknowledge the relentless commitment of police officers from UK Regional Cybercrime Units in providing data and advising on study results. Please note that the views expressed in this work are ours alone and do not necessarily reflect those of the participants, the commentators or the funding body.
This work was supported by the Engineering and Physical Sciences Research Council [EP/P011721/1].
| Questions . |
|---|
| Can you please comment on the volume of infection spread? |
| Did ransomware take advantage of the local user security context and only encrypted server shares? |
| Or did it spread across network, taking advantage of software vulnerabilities or weak admin passwords? |
| Did disruption to business continuity last for: |
| Up to 1 week |
| Up to 2 month |
| Several months or more |
| How much information was lost as a result of this attack? |
| No loss or some loss acceptable with incremental backups |
| Information loss affecting some critical business functions |
| Information loss affecting majority or all critical business functions |
| In your expert opinion, what was the severity of the consequence of this attack on victim organization (‘Low’, ‘Medium’, ‘High’)? |
| Why do you think so? |
| : LawEnfJ had partnerships with other organizations, which involved sharing some systems including e-mail. An employee received a malicious e-mail into the external partner’s inbox and opened it on the machine belonging to LawEnfJ, infecting the network. An investigation revealed that the partner-organization did not have appropriate e-mail hygiene that could have stopped this e-mail from entering the inbox. Nevertheless, LawEnfJ had an acute awareness of the ransomware threat and abundant knowledge on how to prevent and mitigate ransomware attacks. When the ransomware hit, the organization responded timely and methodically. All systems and data were recovered over one weekend. Some data were lost as part of the incremental backups practice, which is an acceptable industry practice. Following the attack, LawEnfJ instigated a formal agreement with all external partners on minimal security measures that they must implement. . |
|---|
| : GovSecJN had multiple layers of security controls to protect its business from cyberthreats. However, when the ransomware attack took place, GovSecJN realized that some controls were not equipped to deal with the incident. For example, a communication plan did not consider the fact that crypto-ransomware has the ability to encrypt systems, including e-mail, stripping organizations of the most common communication methods; business continuity plans did not take into consideration the loss of IT. Although all systems and data were restored in 1 week (from backups), some critical services were unavailable for several days, inevitably affecting customers and staff. Following the attack, GovSecJN implemented several changes, including updated communication and business continuity plans. |
| : EducInstFB had several serious network oversights (e.g. the lack of network visibility, a flat network structure, poor access control management, poor security practices, ineffective backups) that led to severe consequences, where crypto-ransomware infected the whole network comprised hundreds of devices. Subsequently, many vital systems became unresponsive, crippling important business functions. A large amount of data would have been lost as a result of this attack if the organization had not paid the ransom. The recovery process was very challenging and lasted for months. |
Europol. Internet Organised Crime Threat Assessment , 2020 . https://www.europol.europa.eu/sites/default/files/documents/internet_organised_crime_threat_assessment_iocta_2020.pdf
Sophos . The State of Ransomware 2020: Results of an independent survey across 26 countries , 2020 . https://www.sophos.com/en-us/medialibrary/Gated-Assets/white-papers/sophos-the-state-of-ransomware-2020-wp.pdf
FBI . 2019 Internet Crime Report , 2020 . https://pdf.ic3.gov/2019_IC3Report.pdf [Accessed January 2020]
UK Government . Cyber Security Breaches Survey 2020 , 2020 . https://www.gov.uk/government/publications/cyber-security-breaches-survey-2020/cyber-security-breaches-survey-2020
Simoiu C , Gates C , Bonneau J , et al. “I was told to buy a software or lose my computer. I ignored it”: A study of ransomware. In: Proceedings of USENIX Symposium on Usable Privacy and Security (SOUPS) , Santa Clara, CA, 11–13 August 2019 .
Connolly LY , Lang M , Gathegi J , et al. Organisational culture, procedural countermeasures, and employee security behaviour: a qualitative study . Inf Comp Secur 2017 ; 25 : 118 – 36 .
Google Scholar
Richardson R , North M. Ransomware: evolution, mitigation and prevention . Int Manage Rev 2017 ; 13 : 10 – 21 .
Connolly L , Wall SD. The rise of crypto-ransomware in a changing cybercrime landscape: taxonomising countermeasures . Comput Secur 2019 ; 87 : 1 – 18 .
Holt T , Bossler A. An assessment of the current state of cybercrime scholarship . Deviant Behav 2014 ; 35 : 20 – 40 .
Rege A. Incorporating the human element in anticipatory and dynamic cyber defense. In: Proceedings of the 2016 IEEE International Conference on Cybercrime and Computer Forensic , Vancouver, BC, 12–14 June 2016 , 1 – 7 .
Connolly L , Borrion H. Your money or your business: Decision-making processes in ransomware attacks. In: Proceedings of 2020 International Conference in Information Systems . Association for Information Systems, 14–16 December 2020 .
Payne BK , Hawkins B , Xin C. Using labelling theory as a guide to examine the patterns, characteristics, and sanctions given to cybercrimes . Am J Crim Justice 2019 ; 44 : 230 – 47 .
Maimon D , Louderback E. Cyber-dependent crimes: an interdisciplinary review . Annu Rev Criminol 2019 ; 2 : 191 – 216 .
Atapour-Abarghouei A , Bonner S , McGough AS. Volenti non fit injuria: ransomware and its victims. In: 2019 IEEE International Conference on Big Data , IEEE, December 2019 , 4701 – 7 .
Choi KS , Scott TM , LeClair DP. Ransomware against police: diagnosis of risk factors via application of cyber-routing activities theory . Int J Forensic Sci Pathol 2016 ; 4 : 253 – 8 .
Zhao JY , Kessler EG , Yu J , et al. Impact of trauma hospital ransomware attack on surgical residency training . J Surg Res 2018 ; 232 : 389 – 97 .
Zhang-Kennedy L , Assal H , Rocheleau J , et al. The aftermath of a crypto-ransomware attack at a large academic institution. In: Proceedings of the 27th USENIX Security Symposium . Baltimore, MD, 15–17 August 2018 , 1061 – 78 . ISBN 978-1-939133-04-5.
Hull G , John H , Arief B. Ransomware deployment methods and analysis: views from a predictive model and human responses . Crime Science 2019 ; 8 : 2 – 22 .
Shinde R , Van der Veeken P , Van Schooten S , et al. Ransomware: studying transfer and mitigation. In: Proceedings of the 2016 International Conference on Computing, Analytics and Security Trends (CAST) . Pune: IEEE, 19–21 December 2016 , 90 – 5 .
Ioanid A , Scarlat C , Militaru G. The effect of cybercrime on Romanian SMEs in the context of wannacry ransomware attacks. In: Proceedings of the European Conference on Innovation and Entrepreneurship , Paris : Academic Conferences International Limited , 21–22 September 2017 , 307 – 13 .
Google Preview
Byrne D , Thorpe C. Jigsaw: an investigation and countermeasure for ransomware attacks. In: Proceedings of the European Conference on Cyber Warfare and Security . Dublin : Academic Conferences International Limited , 29–30 June 2017 , 656 – 65 .
Riglietti G. Cyber security talks: a content analysis of online discussions on ransomware . Cyber Secur 2017 ; 1 : 156 – 64 .
Agustina JR. Understanding cyber victimization: digital architectures and the disinhibition effect . Int J Cyber Criminol 2015 ; 9 : 35 – 54 .
Ngo FT , Paternoster R. Cybercrime victimization: an examination of Individual and situational level factors . Int J Cyber Criminol 2011 ; 5 : 773 – 93 .
Furnell S , Emm D , Papadaki M. The challenge of measuring cyber-dependent crimes . Comput Fraud Secur 2015 ; 2015 : 5 – 12 .
Business Continuity Institute [BCI]. BCI Cyber Resilience Report . Business Continuity Institute, 2018 .
Beazley. Breach Briefing , 2019 . https://www.beazley.com/Documents/2019/beazley-breach-briefing-2019.pdf
Al-Rimy BAS , Maarof MA , Shaid SZM. Ransomware threat success factors, taxonomy, and countermeasures: a survey and research directions . Comput Secur 2018 ; 74 : 144 – 66 .
Mansfield-Devine S. Securing small and medium-size businesses . Network Secur 2016 ; 2016 : 14 – 20 .
Renaud K. How smaller businesses struggle with security advice . Comput Fraud Secur 2016 ; 2016 : 10 – 18 .
Browne S , Lang M , Golden W. Linking threat avoidance and security adoption: a theoretical model for SMEs. BLED 2015 Proceedings , 2015 , 35. http://aisel.aisnet.org/bled2015/35
Smith R. Ransomware is indiscriminate – secure your systems now, Petri , June 7, 2017 . https://www.petri.com/ransomware-indiscriminate-secure-systems-now
Kurpjuhn T. The SME security challenge . Comput Fraud Sec 2015 ; 2015 : 5 – 7 .
Bergmann MC , Dreißigacker D , Skarczinski B , et al. Cyber-dependent crime victimization: the same risk for everyone? Cyberpsychol Behav Soc Network 2018 ; 21 : 84 – 90 .
Parkinson S. Are public sector organisations more at risk from cyber-attacks on old computers?, The Conversation , 16 May 2017 . https://theconversation.com/are-public-sector-organisations-more-at-risk-from-cyber-attacks-on-old-computers-77802
NIST . Guide for Conducting Risk Assessments, Information Security, NIST Special Publication 800-30 . National Institute of Standards and Technology, Gaithersburg, MD, 2012 . https://nvlpubs.nist.gov/nistpubs/Legacy/SP/nistspecialpublication800-30r1.pdf
Connolly L , Lang M , Wall DS. Information security behavior: a cross-cultural comparison of employees in Ireland and United States . Inf Syst Manage 2019 ; 36 : 306 – 22 .
Connolly L , Lang M , Tygar JD. Employee security behaviour: the importance of education and policies in organisational settings. In: Paspallis N , Raspopulos M , Barry C , et al. (eds.), Advances in Information Systems Development Methods, Tools and Management. Lecture Notes in Information Systems and Organisation . Springer : New York , 2018 : 79 – 96 .
Brewer R. Ransomware attacks: detection, prevention and cure . Network Secur 2016 ; 2016 : 5 – 9 .
Connolly L , Wall SD. Hackers are making personalised ransomware to target the most profitable and vulnerable, The Conversation , 2019 . https://theconversation.com/hackers-are-making-personalised-ransomware-to-target-the-most-profitable-and-vulnerable-113583
Williams M. 10 disturbing facts about employees and cyber security, Pensar , 13 December 2018 . https://www.pensar.co.uk/blog/infographic-10-disturbing-facts-about-employees-and-cyber-security
Browne S , Lang M , Golden W. The insider threat - understanding the aberrant thinking of the rogue ‘Trusted Agent’. In: Proceedings of European Conference on Information Systems , Münster, Germany, 26–29 May 2015 .
Creswell JW , Plano Clark VL. Designing and Conducting Mixed Methods Research , 2nd edn. Thousand Oaks, CA : Sage Publications , 2011 .
Eisenhardt KM. Building theories from case study research . Acad Manage Rev 1989 ; 14 : 532 – 50 .
Zumbo BD , Gadermann AM , Zeisser C. Ordinal versions of coefficients alpha and theta for Likert rating scales . J Mod Appl Stat Meth 2007 ; 6 : 21 – 9 .
Eurostat . Your key European statistics, Eurostat , 2020 . https://ec.europa.eu/eurostat/web/structural-business-statistics/structural-business-statistics/sme
Porcedda MG , Wall DS. Cascade and chain effects in big data cybercrime: lessons from the TalkTalk hack. In: Proceedings of WACCO 2019: 1st Workshop on Attackers and Cyber-Crime Operations , IEEE EuroS&P 2019, Stockholm , 20 June 2019 .
48. UK Government . Procurement Policy Note 09/14: Cyber Essentials Scheme Certification , 2014 . https://www.gov.uk/government/publications/procurement-policy-note-0914-cyber-essentials-scheme-certification
UK National Cyber Security Centre: Certificate Search . https://www.ncsc.gov.uk/cyberessentials/search
Eurostat, 2020b . https://ec.europa.eu/eurostat/tgm/table.do? tab=table&init=1&language=en&pcode=tin00170&plugin=1
Chapman J , Chinnaswamy A , Garcia-Perez A. The severity of cyber attacks on education and research institutions: a function of their security posture. In: Proceedings of ICCWS 2018 13th International Conference on Cyber Warfare and Security . Academic Conferences and Publishing Limited, 2018 , 111 – 9 .
ISO. ISO Survey, 2019 . https://www.iso.org/the-iso-survey.html
| Month: | Total Views: |
|---|---|
| December 2020 | 339 |
| January 2021 | 700 |
| February 2021 | 1,000 |
| March 2021 | 753 |
| April 2021 | 527 |
| May 2021 | 587 |
| June 2021 | 763 |
| July 2021 | 547 |
| August 2021 | 334 |
| September 2021 | 495 |
| October 2021 | 577 |
| November 2021 | 474 |
| December 2021 | 371 |
| January 2022 | 394 |
| February 2022 | 479 |
| March 2022 | 630 |
| April 2022 | 679 |
| May 2022 | 685 |
| June 2022 | 335 |
| July 2022 | 302 |
| August 2022 | 306 |
| September 2022 | 453 |
| October 2022 | 593 |
| November 2022 | 400 |
| December 2022 | 330 |
| January 2023 | 361 |
| February 2023 | 440 |
| March 2023 | 652 |
| April 2023 | 616 |
| May 2023 | 657 |
| June 2023 | 408 |
| July 2023 | 456 |
| August 2023 | 369 |
| September 2023 | 533 |
| October 2023 | 772 |
| November 2023 | 769 |
| December 2023 | 563 |
| January 2024 | 781 |
| February 2024 | 812 |
| March 2024 | 1,034 |
| April 2024 | 1,259 |
| May 2024 | 991 |
| June 2024 | 582 |
| July 2024 | 530 |
| August 2024 | 556 |
Email alerts
Citing articles via, affiliations.
- Online ISSN 2057-2093
- Print ISSN 2057-2085
- Copyright © 2024 Oxford University Press
- About Oxford Academic
- Publish journals with us
- University press partners
- What we publish
- New features
- Open access
- Institutional account management
- Rights and permissions
- Get help with access
- Accessibility
- Advertising
- Media enquiries
- Oxford University Press
- Oxford Languages
- University of Oxford
Oxford University Press is a department of the University of Oxford. It furthers the University's objective of excellence in research, scholarship, and education by publishing worldwide
- Copyright © 2024 Oxford University Press
- Cookie settings
- Cookie policy
- Privacy policy
- Legal notice
This Feature Is Available To Subscribers Only
Sign In or Create an Account
This PDF is available to Subscribers Only
For full access to this pdf, sign in to an existing account, or purchase an annual subscription.
- Harvard Business School →
- Faculty & Research →
- HBS Case Collection
Ransomware Attack at Colonial Pipeline Company
- Format: Print
- | Language: English
- | Pages: 20
About The Author
Suraj Srinivasan
Related work.
- Faculty Research
- Ransomware Attack at Colonial Pipeline Company By: Suraj Srinivasan and Li-Kuan Ni
11 real and famous cases of malware attacks
- Updated at June 4, 2021
- Blog , Threat Research

Many cases of famous hacker attacks use malware at some point. For example, first, the cybercriminal can send you a phishing email . No attachment. No links. Text only. After he gains your trust , in a second moment, he can send you a malicious attachment , that is, malware disguised as a legitimate file.
Malware is a malicious software designed to infect computers and other devices. The intent behind the infection varies. Why? Because the cybercriminal can use malware to make money, to steal secret information that can give strategic advantages, to prevent a business from running or even just to have fun.
Yes, there are hackers who act for pleasure.
In fact, malware is a broad term. It’s like a category. Within this category are different types of threats, such as virus , worm , trojan , and ransomware .
To fight malware delivered via email, here at Gatefy we offer a secure email gateway solution and an anti-fraud solution based on DMARC . You can request a demo or more information .
To get an idea, according to the FBI , damages caused by ransomware amounted to more than USD 29.1 million just in 2020. And one of the most widely used form of malware spreading continues to be via email . As a Verizon report confirmed : 30% of the malware was directly installed by the actor, 23% was sent there by email and 20% was dropped from a web application.
The cases listed below show how malware attacks can work and give you a glimpse of the harm they cause to businesses and individuals.
In this post, we’ll cover the following malware cases:
Table of Contents

Check out 11 real cases of malware attacks
1. covidlock, ransomware, 2020.
Fear in relation to the Coronavirus (COVID-19) has been widely exploited by cybercriminals. CovidLock ransomware is an example. This type of ransomware infects victims via malicious files promising to offer more information about the disease.
The problem is that, once installed, CovidLock encrypts data from Android devices and denies data access to victims. To be granted access, you must pay a ransom of USD 100 per device.
2. LockerGoga, ransomware, 2019
LockerGoga is a ransomware that hit the news in 2019 for infecting large corporations in the world, such as Altran Technologies and Hydro. It’s estimated that it caused millions of dollars in damage in advanced and targeted attacks.
LockerGoga infections involve malicious emails , phishing scams and also credentials theft. LockerGoga is considered a very dangerous threat because it completely blocks victims’ access to the system.
3. Emotet, trojan, 2018
Emotet is a trojan that became famous in 2018 after the U.S. Department of Homeland Security defined it as one of the most dangerous and destructive malware. The reason for so much attention is that Emotet is widely used in cases of financial information theft, such as bank logins and cryptocurrencies.
The main vectors for Emotet’s spread are malicious emails in the form of spam and phishing campaigns . 2 striking examples are the case of the Chilean bank Consorcio, with damages of USD 2 million, and the case of the city of Allentown, Pennsylvania, with losses of USD 1 million.
4. WannaCry, ransomware, 2017
One of the worst ransomware attacks in history goes by the name of WannaCry , introduced via phishing emails in 2017. The threat exploits a vulnerability in Windows.
It’s estimated that more than 200,000 people have been reached worldwide by WannaCry, including hospitals, universities and large companies, such as FedEx, Telefonica, Nissan and Renault. The losses caused by WannaCry exceed USD 4 billion.
By the way, have you seen our article about the 7 real and famous cases of ransomware attacks ?
5. Petya, ransomware, 2016
Unlike most ransomware , Petya acts by blocking the machine’s entire operating system. We mean, Windows system. To release it, the victim has to pay a ransom.
It’s estimated that the losses involving Petya and its more new and destructive variations amount to USD 10 billion since it was released in 2016. Among the victims are banks, airports and oil and shipping companies from different parts of the world.
6. CryptoLocker, ransomware, 2013
The CryptoLocker is one of the most famous ransomware in history because, when it was released in 2013, it used a very large encryption key, which made the experts’ work difficult. It’s believed that it has caused more than USD 3 million in damage, infecting more than 200,000 Windows systems.
This type of ransomware was mainly distributed via emails, through malicious files that looked like PDF files , but, obviously, weren’t.
7. Stuxnet, worm, 2010
The Stuxnet deserves special mention on this list for being used in a political attack, in 2010, on Iran’s nuclear program and for exploiting numerous Windows zero-day vulnerabilities . This super-sophisticated worm has the ability to infect devices via USB drives, so there is no need for an internet connection.
Once installed, the malware is responsible for taking control of the system. It’s believed that it has been developed at the behest of some government. Read: USA and Israel.
8. Zeus, trojan, 2007
Zeus is a trojan distributed through malicious files hidden in emails and fake websites, in cases involving phishing . It’s well known for propagating quickly and for copying keystrokes, which led it to be widely used in cases of credential and passwords theft, such as email accounts and bank accounts.
The Zeus attacks hit major companies such as Amazon, Bank of America and Cisco. The damage caused by Zeus and its variations is estimated at more than USD 100 million since it was created in 2007.
9. MyDoom, worm, 2004
In 2004, the MyDoom worm became known and famous for trying to hit major technology companies, such as Google and Microsoft. It used to be spread by email using attention-grabbing subjects, such as “Error”, “Test” and “Mail Delivery System”.
MyDoom was used for DDoS attacks and as a backdoor to allow remote control. The losses are estimated, according to reports, in millions of dollars.
10. ILOVEYOU, worm, 2000
The ILOVEYOU worm was used to disguise itself as a love letter, received via email. Reports say that it infected more than 45 million people in the 2000s, causing more than USD 15 billion in damages.
ILOVEYOU is also considered as one of the first cases of social engineering used in malware attacks. Once executed, it had the ability to self-replicate using the victim’s email.
Also see 10 real and famous cases of social engineering .
11. Melissa, virus, 1999
The Melissa virus infected thousands of computers worldwide by the end of 1999. The threat was spread by email, using a malicious Word attachment and a catchy subject: “Important Message from (someone’s name)”.
Melissa is considered one of the earliest cases of social engineering in history. The virus had the ability to spread automatically via email. Reports from that time say that it infected many companies and people, causing losses estimated at USD 80 million.
How to fight malware attacks
There are 2 important points or fronts to fight and prevent infections caused by malware.
1. Cybersecurity awareness
The first point is the issue regarding cybersecurity awareness. You need to be aware on the internet. That means: watch out for suspicious websites and emails . And that old tip continues: if you’re not sure what you’re doing, don’t click on the links and don’t open attachments.
2. Technology to fight malware
The second point involves the use of technology . It’s important that you have an anti-malware solution on your computer or device. For end-users, there are several free and good options on the market.
For companies, in addition to this type of solution, we always recommend strengthening the protection of your email network. As already explained, email is the main malware vector. So, an email security solution can rid your business of major headaches.
Here at Gatefy we offer an email gateway solution and a DMARC solution . By the way, you can request a demo by clicking here or ask for more information . Our team of cybersecurity experts will contact you shortly to help.

Latest news
10 real and famous cases of bec (business email compromise), 8 reasons to use dmarc in your business, what is mail server.

An official website of the United States government
The .gov means it’s official. Federal government websites often end in .gov or .mil. Before sharing sensitive information, make sure you’re on a federal government site.
The site is secure. The https:// ensures that you are connecting to the official website and that any information you provide is encrypted and transmitted securely.
- Publications
- Account settings
Preview improvements coming to the PMC website in October 2024. Learn More or Try it out now .
- Advanced Search
- Journal List
- Elsevier - PMC COVID-19 Collection

Ransomware: Recent advances, analysis, challenges and future research directions
Craig beaman.
a Canadian Institute for Cybersecurity, Faculty of Computer Science, University of New Brunswick, Canada
Ashley Barkworth
Toluwalope david akande, saqib hakak, muhammad khurram khan.
b Center of Excellence in Information Assurance, College of Computer and Information Sciences, King Saud University, Riyadh 11653, Saudi Arabia
The COVID-19 pandemic has witnessed a huge surge in the number of ransomware attacks. Different institutions such as healthcare, financial, and government have been targeted. There can be numerous reasons for such a sudden rise in attacks, but it appears working remotely in home-based environments (which is less secure compared to traditional institutional networks) could be one of the reasons. Cybercriminals are constantly exploring different approaches like social engineering attacks, such as phishing attacks, to spread ransomware. Hence, in this paper, we explored recent advances in ransomware prevention and detection and highlighted future research challenges and directions. We also carried out an analysis of a few popular ransomware samples and developed our own experimental ransomware, AESthetic, that was able to evade detection against eight popular antivirus programs.
1. Introduction
The COVID-19 pandemic has led to an increase in the rate of cyberattacks. As the workplace paradigm shifted to home-based scenarios—resulting in weaker security controls—attackers lured people through COVID-19 themed ransomware phishing emails. For example, many phishing campaigns prompted users to click on specific links to get sensitive information related to a COVID-19 vaccine, shortage of surgical masks, etc. Attackers made good use of fake COVID-19 related information as a hook to launch more successful phishing campaigns. Higher levels of unemployment can be another factor that motivates people towards cybercrime, such as launching ransomware attacks and disrupting critical IT services, in order to support themselves ( Lallie et al., 2020 ).
Cyber extortion methods have existed since the 1980s. The first ransomware sample dates back to 1989 with the PC Cyborg Trojan ( Tailor and Patel, 2017 ). After the target computer was restarted 90 times, PC Cyborg hid directories and encrypted the names of all files on the C drive, rendering the system unusable. In the 1990s and early 2000s, ransomware attacks were mostly carried out by hobbyist hackers who aimed to gain notoriety through cyber pranks and vandalism ( Srinivasan, 2017 ). Modern ransomware emerged around 2005 and quickly became a viable business strategy for attackers ( Richardson, North, 2017 , Wilner, Jeffery, Lalor, Matthews, Robinson, Rosolska, Yorgoro, 2019 ). Targets shifted from individuals to companies and organizations in order to fetch larger ransoms ( Muslim et al., 2019 ). The following industries were particularly targeted: transportation, healthcare, financial services, and government ( Alshaikh et al., 2020 ). The number of ransomware attacks has grown exponentially thanks to easily obtainable ransomware toolkits and ransomware-as-a-service (RaaS) that allows novices to launch ransomware attacks ( Sharmeen et al., 2020 ).
Ransomware is a type of malware designed to facilitate different nefarious activities, such as preventing access to personal data unless a ransom is paid ( Khammas, 2020 , Komatwar, Kokare, 2020 , Meland, Bayoumy, Sindre, 2020 ). This ransom typically uses cryptocurrency like Bitcoin, which makes it difficult to track the recipient of the transaction and is ideal for attackers to evade law enforcement agencies ( Kara, Aydos, 2020 , Karapapas, Pittaras, Fotiou, Polyzos, 2020 ). There has been a surge in ransomware attacks in the past few years. For example, during the ongoing COVID-19 pandemic, an Android app called CovidLock was developed to monitor heat map visuals and statistics on COVID-19 ( Saeed, 2020 ). The application tricked users by locking user contacts, pictures, videos, and access to social media accounts as soon as they installed it. To regain access, users were asked to pay some ransom in Bitcoin; otherwise, their data was made public ( Hakak et al., 2020c ). Another notorious example of ransomware is the WannaCry worm, which spread rapidly across many computer networks in May 2017 ( Akbanov, Vassilakis, Logothetis, 2019 , Mackenzie, 2019 ). Within days, it had infected over 200,000 computers spanning across 150 countries ( Mattei, 2017 ). Hospitals across the U.K. were knocked offline ( Chen and Bridges, 2017 ); government systems, railway networks, and private companies were affected as well ( Cosic et al., 2019 ).
Ransomware can be categorized into three main forms - locker, crypto, and scareware ( Gomez-Hernandez, Alvarez-Gonzalez, Garcia-Teodoro, 2018 , Kok, Abdullah, Jhanjhi, Supramaniam, 2019 ) - as shown in Fig. 1 . Scareware may use pop-up ads to manipulate users into assuming that they are required to download certain software, thereby using coercion techniques for downloading malware. In scareware, the cyber crooks exploit the fear rather than lock the device or encrypt any data ( Andronio et al., 2015 ). This form of ransomware does not do any harm to the victim’s computer. The aim of locker ransomware is to block primary computer functions. Locker ransomware may encrypt certain files which can lock the computer screen and/or keyboard, but it is generally easy to overcome and can often be resolved by rebooting the computer in safe mode or running an on-demand virus scanner ( Adamu and Awan, 2019 ). Locker ransomware may allow limited user access. Crypto ransomware encrypts the user’s sensitive files but does not interfere with basic computer functions. Unlike locker ransomware, crypto ransomware is often irreversible as current encryption techniques (e.g., AES and RSA) are nearly impossible to revert if implemented properly ( Gomez-Hernandez, Alvarez-Gonzalez, Garcia-Teodoro, 2018 , Nadir, Bakhshi, 2018 ). Table 1 presents a few popular ransomware families. Crypto ransomware can use one of three encryption schemes: symmetric, asymmetric, or hybrid ( Cicala and Bertino, 2020 ). A purely symmetric approach is problematic as the encryption key must be embedded in the ransomware ( Dargahi et al., 2019 ). This makes this approach vulnerable to reverse engineering. The second approach is to use asymmetric encryption. The issue with this approach is that asymmetric encryption is slow compared to symmetric encryption and hence struggles to encrypt larger files ( Bajpai et al., 2018 ).

Categories of ransomware ( Andronio et al., 2015 ).
List of popular ransomware strains.
| Name | Type | Main Propagation Method | Year | Source |
|---|---|---|---|---|
| Maze | Crypto | Exploits kits, Phishing emails, Remote desktop connection password cracking | 2019 | |
| REvil | Crypto | Oracle WebLogic vulnerabilities, Phishing emails, Remote desktop connection password cracking | 2019 | |
| Locky | Crypto | Phishing emails | 2016 | |
| WannaCry | Crypto | Worm | 2017 | |
| Bad Rabbit | Crypto | Drive-by downloads | 2017 | |
| Ryuk | Crypto | Phishing emails | 2018 | |
| Troldesh | Crypto | Phishing emails | 2014 | |
| Jigsaw | Crypto | Phishing emails | 2016 | |
| Petya | Locker | Phishing emails | 2016 |
The most effective approach (i.e., the hardest to decrypt) is hybrid encryption, which uses both symmetric and asymmetric encryption. An overview of the hybrid approach is given in Fig. 2 . For hybrid encryption, the first step is to create a random symmetric key. The ransomware usually creates this key by calling a cryptographic API on the user’s operating system ( Zimba et al., 2019 ). The symmetric key encrypts the victim’s files as the ransomware traverses through the file system. Once all files are encrypted, a public-private key pair is generated by a command and control (C&C) server which the ransomware connects to. The public key is sent to the ransomware and is used to encrypt the symmetric key, while the private key is held by the C&C server. The plaintext version of the symmetric key is then deleted to ensure that the victim cannot use it to recover their files. Instructions for how to pay the ransom are left for the victim. If the ransom is paid, then the decryption process will begin. Decryption starts by requesting the private key from the C&C server. Once obtained, the private key is used to decrypt the symmetric key. Finally, the symmetric key is used to recover the victim’s files. Generally, a unique public-private key pair is generated for each new ransomware infection; this prevents victims from sharing private keys with other victims to enable them to recover the symmetric key.

The typical steps used by ransomware to encrypt and decrypt a user’s data. This illustrates a hybrid approach where both symmetric and asymmetric cryptography are used.
Ransomware attacks can cause significant financial damage, reduce productivity, disrupt normal business operations, and harm the reputations of individuals or companies ( Jain, Rani, 2020 , Zhang-Kennedy, Assal, Rocheleau, Mohamed, Baig, Chiasson, 2018 ). The global survey ‘The State of Ransomware 2021’ commissioned by Sophos announced in its findings that, among roughly 2000 respondents whose organizations had been hit by a ransomware attack, the average total cost to an organization to rectify the impacts of a ransomware attack (considering downtime, people time, device cost, network cost, lost opportunity, ransom paid etc.) was US$1.85 million, which is more than double the US$761,106 cost reported in 2020 ( ran, 2021 ). These attacks may also result in a permanent loss of information or files. Paying the ransom does not guarantee that the locked system or files will be released ( for Cyber Security, 2018 ). For companies who pay the ransom, the cost of recovering from the attack doubles on average ( Ltd., 2020 ). By the end of the year 2021, ransomware attacks are expected to cost the world $20 billion, up from $325 million in 2015 ( Alshaikh et al., 2020 ). These attacks have been particularly devastating since the COVID-19 pandemic and started by targeting hospitals, vaccine research labs, and contact tracing apps ( Pranggono and Arabo, 2020 ). From all these statistics, it is clear that we need to understand the behaviour of ransomware and its variants to effectively detect and mitigate future attacks. Due to its profitability, new variants of ransomware continue to emerge that circumvent traditional antivirus applications and other detection methods. Hence, it is critical to come up with a new generation of efficient countermeasures.
There is an emerging need to highlight the recent advancements in the area of ransomware. The contribution of this paper is as follows:
- • Recent state-of-the-art ransomware detection and prevention approaches are presented.
- • Different ransomware samples are tested in a virtual environment.
- • A new experimental ransomware known as AESthetic is proposed and tested on eight popular antivirus programs.
- • The effectiveness of a few popular ransomware countermeasures on implemented ransomware samples is analyzed.
- • Future research challenges and directions are identified and elaborated on.
The rest of the article is organized as follows. Section 2 surveys the recent literature on ransomware detection and prevention approaches. Section 3 presents our new ransomware sample, AESthetic, and the experimental test-bed setup along with in-depth analysis. A discussion of our literature survey and test results is in Section 4 . Section 5 highlights future research challenges and directions. Finally, Section 6 concludes the article.
2. Literature review
Before our own survey, we searched for and identified relevant surveys on ransomware and summarized their contributions in Table 2 . Most existing surveys were outdated and focused on papers from 2014 to 2017. Hence, for our own literature review, we sourced papers on ransomware solutions from 2017 onwards. The papers came from the following article databases: IEEE Xplore, ACM, Science Direct, and Springer. Our searches were made using combinations of the following keywords: ‘ransomware detection’, ‘ransomware prevention’, ‘crypto-ransomware’, ‘malware detection’, ‘key backup’, ‘data backup’, ‘access control’, ‘honeypots’, ‘machine learning’, and ‘intrusion/anomaly detection’. We categorized the surveyed papers into ransomware prevention and detection approaches. Most of the existing works within these two categories involved the preliminary step of malware analysis, which is explained below:
Existing review studies.
| Study | Contribution | Year |
|---|---|---|
| ; | Various ransomware detection and mitigation techniques are presented from literature, along with their pros and cons | 2017,2020 |
| In this article, the history of ransomware and best practices to mitigate it are presented | 2017 | |
| In this study, a review on ransomware detection and prevention is carried out | 2017 | |
| In this study, emerging ransomware attacks and a few security challenges are highlighted | 2017 | |
| This article provides a general overview of ransomware and how it works | 2016 | |
| A detailed review on ransomware attack methodology is conducted | 2017 | |
| In this study, the authors carried out a survey on Windows-based ransomware | 2020 | |
| In this study, the authors focused on detection techniques with the core focus on crypto ransomware | 2019 |
2.1. Malware analysis
Malware analysis is a standard approach to understand the components and behaviour of malware, ransomware included. This analysis is useful to detect malware attacks and prevent similar attacks in the future. Malware analysis is broadly categorized into static and dynamic analysis. Static analysis analyzes binary file contents, whereas dynamic analysis studies the behaviour and actions of a process during execution ( Or-Meir, Nissim, Elovici, Rokach, 2019 , Sharafaldin, Lashkari, Hakak, Ghorbani, 2019 , Shijo, Salim, 2015 ).
Signature-based malware detection is a static analysis approach that uses the unique patterns within the malicious file in order to detect it. For ransomware, this includes the unique sequences of bytes within the binary file, the order of function calls, or the analysis of ransomware notes ( Alshaikh, Nagy, Hefny, 2020 , Aslan, Samet, 2020 , Nahmias, Cohen, Nissim, Elovici, 2020 ). The signature can then be checked against the signatures of known malware samples. The main advantages of signature-based detection are that it is fast and has a low false-positive rate; for these reasons, signature-based detection is very popular. However, if malware is concealed through code obfuscation techniques like binary packing, then it may evade detection ( Khan et al., 2020 ). Dynamic analysis is less susceptible to these evasion techniques because, unlike static analysis, it does not rely on analyzing the binary code itself and instead looks for meaningful patterns or signatures that imply the maliciousness of the analyzed file ( Or-Meir et al., 2019 ). Additionally, signature-based approaches will fail against newly created malware ( Aghakhani, Gritti, Mecca, Lindorfer, Ortolani, Balzarotti, Vigna, Kruegel, 2020 , Kok, Abdullah, Jhanjhi, Supramaniam, 2019 ).
Analysis can reveal some of the steps ransomware takes to infect a user’s computer. For example, Bajpai and Enbody ( Bajpai and Enbody, 2020a ) performed static and dynamic analysis on decompiled .NET ransomware samples and found that .NET ransomware first attempts to gain execution privileges and then contacts a C&C server to obtain the encryption key. Zimba and Mulenga ( Zimba and Mulenga, 2018 ) examined the static and behavioural properties of WannaCry ransomware; they discovered that WannaCry retrieves the network adapter properties to determine whether it’s residing in a private or public subnet in order to effectuate substantial network propagation and subsequent damage. Malware analysis can discover the unique characteristics of ransomware which can then be used to help design prevention or detection mechanisms.
2.2. Recent advances in ransomware research
As mentioned previously, most existing studies have analyzed the nature of malware. Based on their analysis, they have proposed different approaches to prevent or detect ransomware. We have classified the existing studies based on their goal, which is to either prevent ransomware infection or to detect ransomware once it has infected the system. A classification diagram of the utilized tools from the reviewed studies can be found in Fig. 3 .

An overview of the utilized tools observed in literature for both ransomware prevention/mitigation and detection.
2.2.1. Ransomware prevention approaches
Preventative solutions aim to block, mitigate, or reverse the damage done by ransomware. Common preventative approaches include: enforcing strict access control, storing data and/or key backups, and increasing user awareness and training. Raising user awareness of ransomware attacks and training users on how to avoid them can prevent attacks before they occur. A summary of the utilized tools found to be used in the surveyed literature on ransomware prevention can be found in Table 3 .
Overview of surveyed literature on ransomware prevention.
| Tool | Papers |
|---|---|
| Access Control | ; ; ; ; |
| Data Backup | ; ; ; ; ; |
| Key Management | ; ; ; |
| User Awareness | ; |
Access Control
Access control prevents ransomware encryption by restricting access to the file system.
Parkinson Parkinson (2017) examined how to use built-in security controls to prevent ransomware from executing in the host computer via elevated privileges. One way that ransomware gains access to files is through a user’s credentials if the user has a high level of permissions. He proposed implementing least privilege and separation of duties through role-based access control; restricting data access as far up the directory hierarchy as possible; and routinely auditing permissions and roles.
Kim and Lee Kim and Lee (2020) proposed an access control list that whitelists specific programs for each file type. Only whitelisted programs are allowed to access files. This implicitly blocks malicious processes from accessing and encrypting files. Whereas a blacklist cannot stop ransomware that it does not contain a code signature for, a whitelist can effectively block new and unknown ransomware.
Ami et al. Ami et al. (2018) developed a solution known as AntiBotics containing three key components: a policy enforcement driver, a policy specification interface, and a challenge-response. This program makes use of both biometric authentication (e.g., a fingerprint) and human response (e.g., CAPTCHA) to prevent the deletion or modification of data. AntiBotics enforces access control by presenting periodic identification challenges. This program assigns access permissions to executable objects based on a rule specified by an administrator as well as the feedback of the challenges presented upon attempts to modify or delete files. One of this program’s limitations is that it is only tested on Windows OS. Also, although modern ransomware failed to evade AntiBotics , it’s possible that future ransomware could adapt to AntiBotics . For example, ransomware could avoid AntiBotics by injecting itself into a permitted process while waiting until the process is granted permission. A case where ransomware may attempt to rename a protected folder and conceal itself may arise, but AntiBotics can block such a process by presenting a challenge when a rename operation is carried out.
McIntosh et al. McIntosh et al. (2021) proposed a framework that enables access control decision making to a filesystem to be deferred when required, in order to observe the consequence of such an access request to the file system and to roll back changes if required. The authors suggested that their framework could be applied to implement a malware-resilient file system and potentionally deter ransomware attacks. They demonstrated the practicality of their framework through a prototype testing, capturing relevant ransomware situations. The experimental results against a large ransomware dataset showed that their framework can be effectively applied in practice.
Genç et al. Genç et al. (2018) developed an access control mechanism with the insight that without access to true randomness, ransomware relies on the pseudo random number generators that modern operating systems make available to applications in order to generate keys. They proposed a strategy to mitigate ransomware attacks that considers pseudo random number generator functions as critical resources, controls accesses on their APIs, and stops unauthorized applications that call them. Their strategy was tested against 524 active real-world ransomware samples and stopped 94% of them, including WannaCry, Locky, CryptoLocker, CryptoWall, and NotPetya samples.
Data Backup
Keeping regular backups of the data stored on a computer or network can greatly minimize the impact of ransomware. Instead, the damage is simply limited to any data that has been created since the last backup. There is overhead in backing up large amounts of data, and so choosing how often backups should be taken and how long they will be kept are important decisions to be made.
Huang et al. Huang et al. (2017) proposed a solution called FlashGuard that does not rely on software at all. Instead, it uses the fact that Solid State Drives (SSD) don’t overwrite data right away - a garbage collector does this after a while. The authors modified SSD firmware so the garbage collector doesn’t remove data as quickly, and hence lost data can be restored. When tested against ransomware samples, FlashGuard successfully recovered encrypted data with little impact on SSD performance and life span.
Thomas and Galligher Thomas and Galligher (2018) conducted a literature review of the ransomware process, functional backup architecture paradigms, and the ability of backups to address ransomware attacks. They also provided suggestions to improve the information security risk assessments to better address ransomware threats, and presented a new tool for conducting backup system evaluations during information security risk assessments that enables auditors to effectively analyze backup systems and improve and organization’s ability to combat and recover from a ransomware attack.
Min et al. Min et al. (2018) proposed Amoeba, an autonomous backup and recovery SSD system to defend against ransomware attacks. Amoeba contains a hardware accelerator to detect the infection of pages by ransomware attacks at high speed, as well as a fine-grained backup control mechanism to minimize space overhead for original data backup. To evaluate their system, the authors extended the Microsoft SSD simulator to implement Amoeba and evaluated it using realistic block-level traces collected while running the actual ransomware. Their experiments found that Amoeba had negligible overhead and outperformed in performance and space efficiency over the state-of-the-art SSD, FlashGuard.
Kharraz and Kirda Kharraz and Kirda (2017) proposed Redemption, a system that requires minimal modification of the operating system to maintain a transparent buffer for all storage I/O. Redemption monitors the I/O request patterns of applications on a per-process basis for signs of ransomware-like behavior. If I/O request patterns are observed that indicate possible ransomware activity, the offending processes can be terminated and the data restored. The evaluation of their system showed that Redemption can ensure zero data loss against current ransomware families without detracting from the user experience or inducing alarm fatigue. Additionally, they proved that Redemption incurs modest overhead, averaging 2.6% for realistic workloads.
Key Management
Key management refers to recovering the encryption key that was used to encrypt files and using that to decrypt them without paying the ransom. For some ransomware samples, such as samples that hard code the key directly into their executable binary, this may be rather straightforward. For hybrid models, this can be more challenging, as the key is only available in plaintext while the files are actively being encrypted.
Bajpai and Enbody Bajpai and Enbody (2020a) decompiled eight different .NET ransomware variants and determined that some ransomware samples use poor key generation techniques that call common libraries. This insight can be utilized by ransomware countermeasures by keeping a backup of an attacker’s symmetric encryption key. This key can be used to recover any encrypted files later on. For example, Lee et al. Lee et al. (2018) observed that many ransomware programs use the CNG library, a cryptographic library for Windows machines, to generate the encryption key. They developed a prevention system that hooks these functions such that when ransomware calls them, the system stores the encryption key. For the evaluation of their system, Lee et al. Lee et al. (2018) implemented a sample ransomware program. They also implemented their prevention solution which attempts hooking into the process from the ransomware program that performs encryption so that it can extract the encryption key. After hooking, the prevention program displays the extracted encryption key when the sample ransomware generates the key for the encryption. In experiments where the ransomware program attempted encryption 10, 100, 1,000, 10,000, and 100,000 times, their ransomware prevention program was able to extract the encryption key 100% of the time. One limitation of this solution is the assumption that ransomware calls a specific library to obtain the encryption key; if the assumption is invalid, the solution fails.
Some ransomware programs use a symmetric session key for encryption. This key is stored in the victim’s computer which then encrypts the user’s files. Kolodenker et al. Kolodenker et al. (2017) developed a key backup solution called Paybreak which relies on signatures. PayBreak implements a key escrow approach that stores session keys in a vault, including the symmetric key that the attacker uses. When tested, PayBreak successfully recovered all files encrypted with known encryption signatures.
The security of the symmetric encryption key is vital for ransomware developers. Furthermore, a large subset of current ransomware exclusively deploy AES for data encryption. With this in mind, Bajpai and Enbody Bajpai and Enbody (2020) developed a side-channel attack on ransomware’s key management to extract exposed ransomware keys from system memory during the encryption process. Their attack leverages the knowledge that the encryption process is a white box on the host system; this approach is successful regardless of which cryptographic API is being used by the malware and regardless of whether a cryptographic API is being used by the malware at all. Their attack was able to identify exposed AES keys in ransomware process memory with a 100% success rate in preliminary experiments, including against NotPetya, WannaCry, LockCrypt, CryptoRoger, and AutoIT samples.
User Awareness
Chung Chung (2019) looked at preventing ransomware attacks within companies and organizations, arguing that they should help individual employees take precautions against ransomware scams. This is especially important since, as mentioned previously, ransomware attacks are increasingly targeting institutions such as financial or healthcare organizations. The author listed five prevention tips for employees to follow: install antivirus or anti-malware software on every computer and mobile device in use; choose strong and unique passwords for personal and work accounts; regularly back up files to an external hard drive; never open suspicious email attachments; and use mirror shielding technology such as NeuShield as a failsafe data protection measure.
Thomas Thomas (2018) also examined how users and employees within organizations can avoid ransomware attacks, but this paper focused on how individuals can avoid falling for phishing attacks, which are a common first step for ransomware. The author surveyed several security professionals and, based on the findings from the survey, proposed several recommendations. The first recommendation was to segment company employees based on factors such as their familiarity with phishing and the impact level of their jobs. After segmentation, the next recommendation was to develop targeted training for each group; this training should include real-life examples highlighting the seriousness and damage caused by phishing, use real case studies, and include actual incidents within the company. Sharing these actual and personal examples will result in a strong realization of the dangerous impact of spear phishing and will evoke a more personal protection response.
2.2.2. Ransomware detection approaches
Researchers have proposed various detection solutions to spot ongoing ransomware attacks. Once ransomware programs have been spotted, they can be stopped and removed. Below is a classification of different detection approaches. A summary of the tools used in the surveyed literature on ransomware detection can be found in Table 4 . An overview of the experimental results, which includes sensitivity and specificity rates, of the surveyed literature on ransomware detection can be found in Table 5 .
Overview of surveyed literature on ransomware detection.
| Tool | Papers |
|---|---|
| Analyzing System Information (Log Files) | |
| Analyzing System Information (Windows Registry) | ; |
| File Analysis (File Differences) | ; |
| File Analysis (File Entropy) | ; ; ; |
| File Analysis (File I/O) | ; ; ; |
| File Analysis (File Types) | ; |
| Finite State Machines | |
| Honeypots | ; ; ; |
| Machine Learning (API/System Calls) | ; ; ; ; ; , ; ; ; ; |
| Machine Learning (File I/O) | ; ; ; ; |
| Machine Learning (HPC Values) | , |
| Machine Learning (Log Files) | |
| Machine Learning (Network Traffic) | ; ; ; ; ; ; |
| Machine Learning (Opcode/Bytecode Sequences) | ; ; ; |
| Machine Learning (PE Header) | ; , |
| Machine Learning (Process Actions) | |
| Network Traffic Analysis (DGA Detection) | ; |
| Network Traffic Analysis (Malicious Domains) | ; ; |
| Network Traffic Analysis (Message Frequency) | ; |
| Network Traffic Analysis (Packet Size) | ; |
| Ransom Note Analysis | ; |
Experimental results from the surveyed ransomware detection literature.
| Paper | Number of ransomware samples | Number of ransomware families | True positive rate (TPR) | Number of benign samples | False positiverate (FPR) | Accuracy | Precision | Uses machine learning |
|---|---|---|---|---|---|---|---|---|
| 840 | 3 | 840 | 97.74% | |||||
| 582 | 11 | 942 | — | |||||
| 3 | — | — | — | — | — | ✗ | ||
| — | — | — | — | — | ||||
| 582 | 11 | 87.9% | 942 | 10% | 87.91% | 89.7% | ||
| 574 | 12 | 98.25% | 442 | 0.56% | — | — | ||
| 383 | 5 | 100% | — | — | — | |||
| 504 | 12 | 65 | 5.9% | — | — | ✗ | ||
| 1477 | 13 | — | — | — | — | — | ✗ | |
| 107 | 20 | 79.4% | — | — | — | — | ✗ | |
| 475 | 44 | 98.1% | 1500 | 0% | 99.5% | 100% | ✗ | |
| 492 | 14 | 100% | — | — | — | — | ✗ | |
| — | 14 | — | ||||||
| — | — | — | — | 100% | ||||
| 2121 | 12 | 96.3% | 172 | 0% | — | — | ✗ | |
| 904 | 11 | 942 | — | |||||
| 582 | 11 | 96.34% | 942 | 1.61% | 97.62% | — | ||
| 276 | — | 98.36% | 312 | — | 97.48% | — | ||
| 38,152 | 5 | — | 2.4% | — | 99.3% | |||
| 8283 | — | 90 | 4% | — | — | |||
| 39,378 | 15 | 16,057 | — | — | ||||
| 1000 | — | — | 1000 | — | 95.9% | — | ||
| 272 | 18 | — | — | |||||
| 942 | — | — | — | — | — | |||
| 4951 | — | — | 3025 | — | 81.44% | — | ||
| 500 | 5 | 500 | — | — | ||||
| 8152 | 15 | 98.97% | 1000 | 1.85% | 97.89% | 98.16% | ||
| 100 | 4 | — | — | — | — | — | ||
| — | 1 | — | — | — | ||||
| 6048 | 12 | — | 5.9% | — | — | |||
| 787 | 2 | — | — | — | ||||
| 90 | 6 | 180 | — | |||||
| 210 | 9 | 264 | — | |||||
| 54 | 19 | 100% | — | 1 out of 15 days | — | — | ✗ | |
| 100MB | — | 87% | 100MB | — | — | 83% | ||
| 1613 | 8 | 87.6% | 100 | — | 89.5% | 87.5% | ||
| 230 | 5 | 229 | — | 100% | ||||
| 1000 | 4 | 93.4% | 1000 | — | — | 93.33% | ||
| 178 | 13 | 178 | ||||||
| 292 | — | — | 292 | — | 98.59% | — | ||
| 864 | 6 | 97.2% | 219 | 2.7% | — | — | ||
| 25 | 56% (14/25) | — | 0% | — | — | ✗ | ||
| 100 | — | 91% | 200 | — | — | — | ✗ | |
| — | 4 | 99.9% | — | 4.6% | 99.9% | 92.3% | ||
| — | — | 98.5% | — | 1.3% | — | — |
* Entries that contain a dash were not found in the reviewed source.
Analyzing System Information
A few of the surveyed papers used system information, such as log files or changes to the Windows Registry, as a method of detecting ransomware. A brief summary of all those works is presented below.
Monika et al. Monika et al. (2016) noted that ransomware samples tend to add and modify many Windows registry values. They suggested that the continuous monitoring of Windows registry values, along with file system activity, can be used to detect ransomware attacks. Chen et al. Chen and Bridges (2017) analyzed system log files to detect ransomware activity. This was done by extracting various features from the log files that are relevant to malware activity. Ultimately they found that malware (ransomware included) can be effectively detected using their approach, even when the logs contain mostly benign events, and that their solution is resilient to polymorphism.
Ransom Note Analysis
After the execution of a ransomware attack, a ransom note is usually left behind. This note could be saved to the user’s computer in the form of a text file or displayed on the user’s screen. This note informs the user that their personal files have been encrypted - or, in the case of locker ransomware, are inaccessible - and gives steps on how to pay and retrieve them. Static and dynamic analysis can reveal the traits of ransomware notes. For example, Groenewegen et al. Groenewegen et al. (2020) performed static and dynamic behaviour analysis to identify the traits of the NEFILIM ransomware strain that targets Windows machines. They found that if a NEFILIM sample is executed with administrative privileges, the accompanying ransom note is written to the root directory of the machine (C:); otherwise, it is written to the user’s ”AppData” directory. Furthermore, the ransomware calls the ”CreateFileW” and ”WriteFile” Windows functions to create the ransomware note and write to it, respectively. Lastly, they determined that the ransomware note file is always named ”NEFILIM-DECRYPT.txt”. In the case where the ransom note is displayed on the screen, some researchers took screen captures and used image and text analysis methods to detect the presence of a ransom note ( Alzahrani, Alshehri, Alshahrani, Alharthi, Fu, Liu, Zhu, 2018 , Kharaz, Arshad, Mulliner, Robertson, Kirda, 2016 ).
As mentioned in Section 2.1 , ransomware typically displays a ransom note on the user’s computer to receive payment. Some researchers used static and/or dynamic analysis to detect the presence of such a note to ascertain whether a ransomware attack is underway.
Alzahrani et al. Alzahrani et al. (2018) proposed RanDroid, a framework to detect ransomware embedded in malicious Android applications by looking for ransom notes displayed during the app’s execution. RanDroid measures the structural similarity between a set of images collected from the inspected application and a set of threatening images collected from known ransomware variants. The framework first decompiles the Android Application Package (APK) which contains a set of files and folders. It then extracts images from the resources folder and XML layout files using static analysis. Dynamic analysis is performed with a UI-guided test input generator to interact with the application without instrumentation, in order to trigger the app’s events, capture the activities that appear while the app is running, and collect additional images. Several pre-processing steps are applied to the images, including extracting the text from the images. Image and text similarity measurements are calculated against a database of images and texts collected from known ransomware variants; both measurements are used for a final classification. RanDroid was tested by running 300 applications (100 ransomware and 200 goodware applications) and achieved a 91% accuracy rate.
Kharraz et al. Kharaz et al. (2016) designed a system called UNVEIL to detect ransomware; a core component of UNVEIL is aimed at detecting screen locker ransomware, with the key insight that ransom notes generally cover a significant part, if not all, of the display. UNVEIL monitors the desktop of the victim machine and takes screenshots of the desktop before and after a sample is executed. The series of screenshots are then analyzed and compared with image analysis methods to determine if a large part of the screen has changed substantially between captures. When evaluated against 148,223 samples, UNVEIL achieved a 96.3% detection rate with zero false positives.
File Analysis
Crypto ransomware modifies a file when encrypting it. Large changes made to many files in a computer’s file system could indicate that a ransomware attack is underway. There are several metrics that can be used to detect significant changes in files. The three metrics identified from the surveyed literature are entropy, file type, and file differences (i.e. similarity). In addition, several researchers analyzed file I/O operations to detect suspicious activity. These four methods of file analysis are defined below.
- • File entropy: This measures the ”randomness” of a file. Encrypted and compressed files have high entropy compared to plaintext files. Hence, calculating the entropy of the file and comparing the value to previous calculations for the same file can be used to determine whether a file has been infected by ransomware. Scaife et al. Scaife et al. (2016) calculated file entropy with Shannon’s formula and used it as one feature to detect ransomware. Mehnaz et al. Mehnaz et al. (2018) also used Shannon entropy as a metric for detecting ransomware. Lee et al. Lee et al. (2019) applied machine learning to classify infected files based on file entropy analysis.
- • File type: A file’s type refers to its extension. Ransomware typically changes the extension of any file that it encrypts. In addition to entropy, both Scaife et al. Scaife et al. (2016) and Mehnaz et al. Mehnaz et al. (2018) used file type changes as a feature to determine the presence of ransomware. The detection system designed by Ramesh and Menen Ramesh and Menen (2020) monitors for changes such as large numbers of files being created with the same extension or any files with more than one extension.
- • Similarity: In comparison with benign file changes, such as modifying parts of a file or adding new text, the contents of a file encrypted by ransomware should be completely dissimilar from the original plaintext content. Hence, measuring the similarity of two versions of the same file can be used to detect whether ransomware is present. Scaife et al. Scaife et al. (2016) measured the similarity between two files with a hash function sdhash, which outputs a similarity score from 0 to 100 that describes the confidence of similarity between two files. Comparisons between previous versions of a file and the encrypted version of the file should yield a score close to 0, as the ciphertext should be indistinguishable from random data. Mehnaz et al. Mehnaz et al. (2018) also used sdhash to perform similarity checks between file versions to determine if a file has been encrypted by ransomware.
- • File I/O: These operations are used to access the host computer’s file system. Examples of I/O operations include open, close, read, and write fil (2021) . Ransomware typically performs read operations to read user files without the user’s permission. It executes write operations either to create encrypted copies of the target files or to overwrite the original files. In the case of the former option, ransomware performs additional operations to delete the original files. Baek et al. Baek et al. (2018) developed a system to detect ransomware in SSDs which learns the behavioural characteristics of ransomware by observing the request headers of the I/O operations that it performs on data blocks. These request headers include the logical block address, the type of operation (read/write), and the size of the data. Natanzon et al. Natanzon et al. (2018) developed a system that generates a ransomware probability by comparing recent I/O activity to historical I/O activity; if the ransomware probability exceeds a specified threshold value, the system takes actions to mitigate the effects of ransomware within the host. The detection system proposed by Kharraz et al. Kharaz et al. (2016) extracts features from I/O requests during a sample’s execution such as the type of request (e.g., open, read, write). These events are then matched against a set of I/O access pattern signatures as evidence that the sample is in fact ransomware.
Finite State Machines
An abstract mathematical model that can be used to represent the state of a system and track changes. It has been noted that many ransomware samples tend to carry out similar sets of actions once they reach a target system. Also, the changes made by ransomware differ significantly from benign programs. Hence, ransomware can be quickly identified in most cases. FSM’s can be used to track those actions by associating system events with transitions between the states in the FSM. The state of the FSM can be monitored and if certain states are reached, the FSM can signal that a ransomware attack is underway. Monitoring the state changes that occur in the computer system in terms of utilization, persistence, and the lateral movement of resources can detect ransomware ( Ramesh and Menen, 2020 ).
Ramesh and Menen Ramesh and Menen (2020) proposed a finite state machine (FSM) with eight total states. The changes represented in the FSM include: changes in file entropy, as encrypted files have higher levels of entropy; changes in retention state, which occurs if a process has been added to the Run registry or startup directory; lateral movement, which checks for suspicious file names such as doubled file extensions (e.g..pdf.exe); and system resources, which looks for processes that modify the system-restore settings or stop a large number of other processes in a short amount of time. If the FSM ever moves into one of its four final states, then the system is considered to be under a ransomware attack. Their method was tested against 475 different ransomware samples and 1500 benign programs. It detected 98.1% of the tested samples and had a 0% false positive rate. The main drawbacks of this approach are its inability to detect locker-type ransomware and its inability to detect ransomware samples that use sophisticated code-obfuscation and incremental unpacking techniques, such as NotPetya.
Honeypots (or honeyfiles) are decoy files set up for the ransomware to attack. Once these files are attacked, the attack is detected and stopped. Honeyfiles are easy to set up and require little maintenance. However, there is no guarantee the attacker will target these decoys, so an attacker may encrypt other files while leaving the honeyfiles untouched Moore (2016) . Gómez-Hernández and Álvarez-González Gomez-Hernandez et al. (2018) proposed R-Locker , a tool for Unix platforms containing a ”trap layer” with a series of honeyfiles. Any process or application that accesses the trap layer is detected and stopped. Unfortunately, R-Locker only protects part of the complete file system, and the tool can be defeated by deleting the central trap file.
Similarly, Kharraz et al. Kharaz et al. (2016) designed UNVEIL to limit the damage that can be done by attackers before they are detected with honeyfiles. UNVEIL generates a virtual environment that aims to attract attackers. It then monitors its file system I/O and detects any presence of a screen locker. Their solution detected 96.3% of ransomware samples and had zero false positives.
Shaukat and Rebeiro Shaukat and Ribeiro (2018) proposed RansomWall , a multi-layered defense system that incorporates honeyfiles to protect against crypto-ransomware. When the trap layer suspects a process is malicious, any modified files are backed up until it is classified as either ransomware or benign by other layers. When tested, RansomWall had a 98.25% accuracy rate and generated zero false positives. One challenge is that some ransomware samples have limited file system activity.
Network Traffic Analysis
Network traffic analysis intercepts network packets and analyzes communication traffic patterns to detect ongoing malware attacks. For certain ransomware families, the communication between the victim host and the C&C server behaves much differently compared to normal conditions. This anomalous behavior can be revealed by studying certain traffic features. The four main features of network traffic used by researchers to detect ransomware are discussed below.
- • Packet size: The size of messages exchanged may be unusually large if they contain an encryption key or encryption instructions. Cabaj et al. Cabaj et al. (2018) analyzed CryptoLocker and Locky ransomware samples under execution and extracted the message size from HTTP packet headers to determine the average size of messages exchanged between the infected host and the C&C server, then used these statistics to build an anomaly detection system based on message size. Bekerman et al. Bekerman et al. (2015) used TCP packet size as a feature in a supervised-based system for detecting ransomware.
- • Message frequency: Determining an uptick in certain kinds of traffic can be used to detect the presence of a ransomware attack. Almasshadani et al. Almashhadani et al. (2019) observed that Locky ransomware significantly increases the number of HTTP POST request packets within the traffic stream compared to the normal traffic. Additionally, they found that there are numerous TCP RST and TCP ACK packets in Locky’s traffic used to terminate the malicious TCP connections abnormally. The authors used these features and others as part of a multi-classifier intrusion detection system. Bekerman et al. Bekerman et al. (2015) used the number of TCP RST packets, TCP ACK packets, and duplicate ACK packets as well as the number of sessions in communication as features for their supervised ransomware classification model.
- • Malicious domains: Communication between the ransomware and the C&C server can be blocked if the server’s domain is identified as malicious. Cabaj and Mazurczyk Cabaj and Mazurczyk (2016) proposed a software-defined networking solution that relies on dynamic blacklisting of proxy servers to block communication between the infected computer and the C&C server. Their proposal forwards all DNS traffic to a controller that checks the domains with a blacklist database. If a malicious domain is detected, the DNS message is discarded and traffic from the host is blocked.
- • DGA detection: Rather than using hardcoded domain addresses, which are susceptible to domain blacklisting, some types of ransomware employ a Domain Generation Algorithm (DGA) to generate a large number of domain names that can be used as rendezvous points for their C&C servers. Some detection systems such as the one proposed by Chadha and Kumar Chadha and Kumar (2017) and Salehi et al. Salehi et al. (2018) work by determining the DGA and subsequently blocking all generated domains.
- • Other features: Hundreds of other extracted network features from various OSI layers can also be used for ransomware detection. Many of these are outlined in Bekerman et al. (2015) , where they did not focus on ransomware detection specifically, but instead on general malware detection.
Machine Learning
Many studies proposed machine learning models that detect ransomware by classifying computer programs as either benign or ransomware based on their behaviour. With sufficient training data, these models can spot attacks with a high degree of accuracy. Additionally, they are frequently able to detect ransomware before it has a chance to encrypt any files. However, finding a suitable model requires trial and error, and biasness or overfitting may occur if proper measures are not taken ( Kok et al., 2019b ). What distinguishes the models proposed by different researchers are the classifier algorithms that are applied and the features that are used for training. The features used in the surveyed literature include the following:
- • APIs / System calls : API calls are functions that facilitate the exchange of data among applications, while system calls are service requests made by the ransomware to the OS or kernel api (2018) . Often, ransomware makes API calls to the C&C server to obtain an encryption or decryption key. Other API calls can be made to maintain execution privileges on the host computer, enumerate the list of files to encrypt, and access or modify files. Ransomware and benign programs have specific call patterns or a unique order of calls that can be used to differentiate them. Examples of system calls include create, delete, execute, and terminate Bajpai and Enbody (2020b) ; Qin et al. (2020) ; api (2018) .
- • Log files: Log files can come from a variety of sources and record information that can indicate whether a ransomware attack is underway. For instance, Herrera Silva and Hernández-Alvarez ( Silva and Hernandez-Alvarez, 2017 ) found that both WannaCry and Petya ransomware exploit DNS and NetBIOS and can be spotted by analyzing DNS and NetBIOS logs. I/O request packets are generated for each file operation and contain parameters such as the type of operation and the address and size of the data being read or written to. These parameters can be extracted from I/O request packet logs and used as features.
- • File I/O: Ransomware typically executes many more read operations than benign programs, since it must read every file it encrypts. Additionally, it executes more write operations on average. File operation metrics such as the number of files written to or read from; the average entropy of file-write operations; the number of file operations performed for each file extension; and the total number of files accessed can be used to gauge if the file operations being performed are benign or part of a ransomware attack( Continella, Guagnelli, Zingaro, Pasquale, Barenghi, Zanero, Maggi, 2016 , Sgandurra, Muñoz-González, Mohsen, Lupu, 2016 ).
- • HPC values: Hardware Performance Counters (HPCs) are a set of special-purpose registers that were first introduced to verify the static and dynamic integrity of programs in order to detect any malicious modifications to them ( Alam et al., 2020 ). The time-series data collected from these counters can be fed into a model to learn the behaviour of a system and detect malicious programs through any statistical deviations in the data.
- • Network traffic: Network traffic features include average packet size, the number of packets exchanged between the host and other machines, and the source and/or destination IP addresses contained within packet headers. Ransomware frequently displays anomalous communications patterns. For example, the work by Cabaj et al. Cabaj and Mazurczyk (2016) found that CryptoWall and Locky ransomware samples involve a defined sequence of HTTP packets exchanged between the host and a C&C server to distribute the encryption key; in addition, these packets tend to be larger than average. Machine learning models can learn normal and anomalous traffic features to distinguish normal communication from malicious communication. Chadha and Kumar Chadha and Kumar (2017) analyzed network traffic to obtain the names of benign and malicious domains to use as features for their model, which detects ransomware by predicting if incoming or outgoing packets transmitted to or from the host contains a malicious domain.
- • Opcode/Bytecode sequences: Opcodes (”operation codes”) specify the basic processor instructions to be performed by a machine, whereas bytecode is a form of instruction designed to be executed by a program interpreter (e.g., Java Virtual Machine). These sequences have rich context and semantic information that provide a snapshot of the program’s behaviour. This information can be extracted through dynamic analysis and fed into a model to predict if a given program is benign or malicious.
- • Process actions: This refers to the sequence of events that occur while a program or application is running. Ransomware will typically cause different events to occur compared to a benign program; these events can be transformed into feature vectors and learned by a model by extracting information such as text and encoding it as numerical values ( Homayoun et al., 2019 ).
- • Others: Many other features were used by researchers and extracted from assorted sources. Some of these features are derived from the raw bytes extracted from executable files using static analysis ( Khammas, 2020 ). Other features related to web domains (e.g., the length of the domain name, the number of days a domain is registered for Quinkert et al. (2018b) ) or DNS (e.g., the number of DNS name errors, the number of meaningless domain names ( Almashhadani et al., 2019 )). Portable Executable (PE) file headers, which show the structure of a file and contain important information about the nature of the executable file, have components that be used as features. Other sources for features include the CPU (e.g., power usage), k-mer substrings (e.g., frequencies), volatile memory, and the Windows Registry ( Azmoodeh, Dehghantanha, Conti, Choo, 2018 , Cohen, Nissim, 2018 , Sgandurra, Muñoz-González, Mohsen, Lupu, 2016 ).
A complete list of the works that focused on detecting ransomware using machine learning is highlighted in Table 6 .
Overview of surveyed machine learning detection approaches.
| Paper | Classifier Algorithm(s) | Features |
|---|---|---|
| Random Forest | Raw bytes | |
| Decision trees | APIs/system calls | |
| SVM, Random Forest | Strings, APIs/system calls | |
| Linear Regression | k-mer frequency | |
| Logistic Regression, SVM, ANN, Random Forest, Gradient Tree Boosting | APIs/system calls | |
| Random Forest | Log files | |
| Naïve Bayes, Logistic Regression, Decision trees, Random Forest | Log files | |
| KNN, Linear Regression, Logistic Regression, Decision trees, SVM, ANN | File I/O | |
| Random Forest | APIs/system calls | |
| Logistic Regression, SVM, Naïve Bayes | APIs/system calls, Registry keys, File I/O, Strings | |
| SVM | APIs/system calls | |
| SVM | APIs/system calls | |
| Logistic Regression, LDA, KNN, CART, Naïve Bayes, SVM, Decision trees, Random Forest | APIs/system calls | |
| Logistic Regression, SVM, Decision trees, Random Forest, KNN, Boosting, ANN | APIs/system calls | |
| CNN | APIs/system calls | |
| ANN | Log files | |
| Random Forest, Logistic Regression, Naïve Bayes, SGD, KNN, SVM | APIs/system calls | |
| Linear Regression, Decision trees | APIs/system calls | |
| Decision trees, Random Forest, Naïve Bayes, Bayesian networks, Logistic Regression, LogitBoost, Bagging, AdaBoost | Volatile memory dump features | |
| Linear Regression | APIs/system calls | |
| ANN (LSTM) | HPC values | |
| None (proof of concept) | Log files | |
| Random Forest, Bayesian Network, SVM | Network traffic | |
| Naïve Bayes, Decision trees, Random Forest | Network traffic | |
| KNN, ANN, SVM, Random Forest | CPU power usage | |
| Random Forest | Network traffic | |
| CNN | Opcodes | |
| SVM | Opcode/bytecode sequences | |
| CNN | PE header components | |
| Naïve Bayes, Logistic Regression, SVM, Random Forest, Decision trees | DLL function calls, Opcode/bytecode sequences | |
| Logistic Regression, SVM, Random Forest, Decision trees | DLL function calls, Opcode/bytecode sequences | |
| LSTM, CNN | Event sequences | |
| KNN, SVM, ANN | Network traffic | |
| -means Clustering | Network traffic | |
| SVM, Naïve Bayes | Network traffic | |
| ANN, KNN | Network traffic |
SVM: Support Vector Machines, ANN: Artificial Neural Networks, KNN: k -nearest neighbors, LDA: Linear discriminant analysis, CART: Classification and regression trees, SGD: Stochastic Gradient Descent, CNN: Convolutional Neural Networks, LSTM: Long short-term memory
3. Ransomware implementation and evaluation
In this section, we have highlighted the motivation of implementing existing ransomware samples and testing the effectiveness of existing countermeasures against those ransomware samples. A brief description of our new ransomware is also presented.
3.1. Motivation
From the literature review, few studies were found to test the effectiveness of existing ransomware countermeasures, such as antivirus products. There seems to be a research gap between research-based proposed solutions and existing practical solutions. To validate our claim, we decided to test different AV products against random known ransomware samples and a simple ransomware created by us. This was done to evaluate the effectiveness of existing practical countermeasures against both known and unknown ransomware samples. Also, our aim is not to claim that existing AV products are not able to detect ransomware samples, as it is possible that the tested AV products are able to detect other samples from other known ransomware families. Through these experiments, our motive is just to highlight the need of effective countermeasures against known/unknown ransomware samples.
3.2. Experimental setup
Testing was done using a VirtualBox virtual machine running the latest version of Windows 10. VirtualBox Guest Additions were not installed as some malware samples are known to detect these additions ( gue, 2017 ). Ransomware samples were taken from the work of sam (2021) . The samples were in a binary format and had to be extracted from an encrypted ZIP file before use. In most cases, the file extensions were manually added before the execution of the ransomware. To conduct the tests safely on these ransomware samples, a few precautions were taken. This included setting the network adaptor to host only, ensuring all software was up-to-date, and removing any shared folders between the guest and the host operating systems. On the host side, data was backed up to an external hard drive and the internet connection was disconnected. The reason for disconnecting the internet was to make sure ransomware did not escape the environment of the virtual machine. The ransomware samples were all taken from https://github.com/ytisf/theZoo in January of 2021.
Several test folders were placed in different areas of the file system including Desktop, Documents, and Picture folders. Test folders were also placed in protected areas of the file system such as Program Files, Program Files (x86), and Windows. One of the folders was placed in the Recycle Bin to analyze if the ransomware scans Recycle Bin or not. The test folders contained four different file formats that included rich-text, text, PDF, and image files. All these respective files had a non-zero size.
3.3. Testing
Testing consisted of three parts, where in each part various ransomware samples are pitted against various antivirus products. The first test was on well-known ransomware samples. The second test used a RaaS generator. The third and final test used a novel custom-made ransomware sample. All of the antivirus products were the most up-to-date versions as of January, 2021.
3.3.1. Well-Known ransomware tests
The first round of testing was simply a control test to see the impact of the ransomware samples when no security controls were in place; all antivirus applications were turned off. The User Access Control Settings of Windows were set to default. The ransomware samples tested were WannaCry ( Akbanov et al., 2019 ), Cerber ( Hassan, 2019 ), Thanos, and Jigsaw ( Hull et al., 2019 ). The results are shown in Table 7 , where it can be seen that most of the files within the Desktop, Documents, etc., got encrypted except for the protected operating system folders. Cerber ransomware failed to encrypt folders that the other samples encrypted. The explanation for this behaviour is unknown, but it could have just been programmed in that way.
Control test results where ransomware samples were tested without any form of protection.
| WannaCry | Cerber | Thanos | Jigsaw | |
|---|---|---|---|---|
| Encrypted | Encrypted | Encrypted | Encrypted | |
| Encrypted | Encrypted | Encrypted | Encrypted | |
| Encrypted | Safe | Encrypted | Encrypted | |
| Encrypted | Safe | Encrypted | Encrypted | |
| Deleted | Safe | Encrypted | Encrypted | |
| Encrypted | Encrypted | Encrypted | Encrypted | |
| Safe | Safe | Safe | Safe | |
| Safe | Safe | Safe | Safe | |
| Safe | Safe | Safe | Safe |
Other ransomware samples were also tested, but unfortunately, we were not able to analyze them. As mentioned earlier, some forms of ransomware need to connect via the internet to a C&C server before they can be executed. In our scenario, due to the testing being done offline, it was not possible to analyze that category of ransomware.
The same ransomware samples were then tested against eight popular antivirus programs. In all cases, the ransomware samples were rapidly detected and removed before any test files became encrypted. The samples were often removed before they were even clicked on.
3.3.2. RAASNet Testing
The second round of testing was done using a RaaS generator called RAASNet, which can be downloaded from https://github.com/leonv024/RAASNet . RAASNet is a free, cross-platform, and open-source software project designed to educate the public about how easy it is to create and use ransomware. It allows for custom ransomware to be created and tested. Although RAASNet generates real ransomware, the decryption key can be freely obtained from the author’s website.
A control test was performed for two different RAASNet generated ransomware samples with no antivirus software running. These two samples were identical except for the fact that one ran with administrator privileges while the other did not. The payloads of both samples were generated using the default settings of RAASNet. The results of this control test can be seen in Table 8 . Both of the samples were set to target all of the listed folder locations. The sample with administrator privileges was tested to see if it would be able to infect the protected operating system folders, but this was unsuccessful. The only difference between the two tests was that the one with administrator privileges generated a user account control (UAC) prompt message, but allowing access still did not let the ransomware modify the files.
A control test of two different RAASNet payloads, one with administrator privileges and one without.
| RAASNet (default) | RAASNet (admin) | |
|---|---|---|
| Encrypted | Encrypted | |
| Encrypted | Encrypted | |
| Encrypted | Encrypted | |
| Encrypted | Encrypted | |
| Encrypted | Encrypted | |
| Encrypted | Encrypted | |
| Safe | Safe | |
| Safe | Safe | |
| Safe | Safe |
The advantage of testing RAASNet ransomware over well-known ransomware samples (e.g. Jigsaw) is that RAASNet generated samples are not included in all antivirus signature databases. One of the generated payloads was uploaded to VirusTotal.com, and only 20 out of 72 antivirus engines detected the payload as malicious. Comparatively, Jigsaw’s sample was also uploaded and this was detected by 67 out of 72 engines. This means that the antivirus programs can be tested for their dynamic detection abilities rather than strictly through static-based detection. This is important since it is a better indication of how they might do against novel ransomware samples in the future where static analysis is more likely to fail.
A RAASNet generated payload (created with default settings and without administrator privileges) was then tested against several popular antivirus programs. The results of these tests can be found in Table 9 . Folders were placed in different locations across the file system and marked as either encrypted or safe depending on whether the ransomware encrypted them or not. The worst performing antivirus programs were Microsoft Defender, MalwareBytes (Free), and Avira (Free). All of the antivirus programs had real-time protection turned on. Overall, the antivirus programs did quite well and quickly caught the ransomware before it could do any real damage. However, the antivirus programs with the best results appeared to detect the ransomware samples through static analysis. This is evidenced by the fact that many of these antivirus programs gave messages indicating that they detected the ransomware by preemptively scanning the file, seemingly before they could run.
RAASNet test results for different antivirus software. Both Microsoft Defender and Avira failed to stop the sample.
| Desktop | Documents | Pictures | OneDrive | |
|---|---|---|---|---|
| Encrypted | Encrypted | Encrypted | Encrypted | |
| Encrypted | Encrypted | Encrypted | Encrypted | |
| Safe | Safe | Safe | Safe | |
| Safe | Safe | Safe | Safe | |
| Safe | Safe | Safe | Safe | |
| Safe | Safe | Safe | Safe | |
| Safe | Safe | Safe | Safe | |
| Safe | Safe | Safe | Safe |
It is worth noting that many antivirus programs, such as Microsoft Defender, do have an effective form of ransomware protection built-in. This protection comes in the form of folder protection which checks if a process is trusted. If it is not, the antivirus software denies the process from modifying the folder contents. A protected folder was set up on the Desktop using Microsoft Defender, and the contents in this folder were successfully protected. It would appear that a similar form of protection also safeguards important operating system folders, as evidenced by the fact that no ransomware sample was able to encrypt files in these areas of the file system.
3.3.3. AESthetic Ransomware testing
The final tests were done using the AESthetic ransomware sample. This sample was custom-made for this research and was created in Java. We created AESthetic using Java’s standard cryptographic package, javax.crypto. AESthetic uses a hybrid encryption approach with the help of a C&C server that runs on localhost. It starts by generating a symmetric key using secure cryptographic modules. It then recursively crawls through the file system from a specified target directory and will encrypt all specified file types using AES-256 in CBC mode. A unique and randomly generated initialization vector is used for each file, which gets appended to the beginning of the encrypted file for later use. A ransom note is placed in every directory that AESthetic traverses through. Once all of the files are encrypted, AESthetic connects to the C&C server to obtain an RSA public key that it uses to encrypt the symmetric key. Once the symmetric key is encrypted, the plaintext version of the symmetric key is deleted. New files are created to store the encrypted data and the original plaintext files are deleted. After ten seconds, it will automatically start to decrypt the encrypted files. To do this, it once again connects to the C&C server to obtain the corresponding RSA private key to decrypt the encrypted AES symmetric key. This sample was tested against eight popular antivirus programs (which are the same as those listed in Table 9 ). All of the test files got encrypted by AESthetic. None of the antivirus programs reported any suspicious activity. Both the source code and an executable JAR file were uploaded to VirusTotal.com, and in both cases, this resulted in zero detections. There were zero detections since the malware was made just for this research and its signature has not yet been added to any signature database.
4. Discussion
From the results of our literature review and experiments, we can make several observations on the current trends and limitations of ransomware countermeasure solutions. Most papers preferred to study ransomware using dynamic analysis over static analysis, or used a combination of the two. This is perhaps unsurprising, as static analysis can frequently be evaded through code obfuscation or polymorphic/metamorphic attacks ( Shaukat and Ribeiro, 2018 ). However, some papers found that certain dynamic analysis approaches can be evaded as well. For instance, the virtual environment in UNVEIL ( Kharaz et al., 2016 ) could potentially be detected and avoided by attackers. One limitation of both types of analysis is that the results cannot usually be generalized to all ransomware variants. For example, the key backup technique proposed by Lee et al. Lee et al. (2018) relies on their analysis that ransomware calls specific functions in the CNG library. The HTTP traffic characteristics that Cabaj et al. Cabaj et al. (2018) used to detect ransomware comes from studying ransomware families: CryptoWall and Locky. Almashhadani et al. Almashhadani et al. (2019) based their detection system on the behavioural analysis of one family – Locky.
Preventative techniques such as access control and key or data backups can reduce the damage that ransomware can inflict on systems and possibly deter future attacks. However, these prevention-based approaches suffer from several shortcomings as well. Firstly, they can have significant overhead. Access control or key backup schemes can incur significant computational costs ( Wang et al., 2015 ). Creating data backups can cause the system to take a significant performance hit, especially under high workloads ( Alshaikh et al., 2020 ).
Machine learning models were the most common technique for detecting ransomware. These models can be trained to recognize the general behaviour patterns of ransomware through suspicious behaviour or specific basic processor instruction patterns. The ability for machine learning to detect the general behaviour of ransomware is important, as ransomware is constantly evolving and can easily change its code signature, but has difficulty changing its attack pattern ( Kok et al., 2019b ). However, many of these models require an attack to already be underway in order to detect suspicious activity, such as file access or communication to a malicious domain. Khan et al.’s Khan et al. (2020) use of digital DNA sequencing is a promising approach since it is designed to detect ransomware before infection.
Based on the results of our experiments, which were conducted on a number of different ransomware samples, we have learned a few interesting things about ransomware. Our tests using RAASNet have shown how easy it is to acquire and use ransomware through RaaS software. RaaS lets ransomware developers sell or lease their ransomware variants to affiliates, who use these variants to perform attacks; both developers and affiliates get a cut of any profits. As previously mentioned, RaaS enables users without technical expertise to launch ransomware attacks, meaning that ransomware is no longer limited to the developers who create it. For developers, RaaS reduces their risk since they do not launch the attacks themselves. The RaaS model has gained popularity amongst cybercriminals and has caused a dramatic increase in the rate of ransomware attacks in recent years ( Al-rimy et al., 2018 ).
Although antivirus programs were successful against previously known samples, they did not fare quite so well against the lesser-known RAASNet sample and the completely novel AESthetic sample. The novel sample of course is not present in antivirus signature databases and it was completely undetected. This highlights that current antivirus software likely rely too heavily on simple signature-based static analysis detection and hence should invest more into the approaches seen in literature, especially in regards to dynamic analysis or honeypot approaches. For example, our ransomware AESthetic was designed with many tell-tale ransomware behaviors in mind, such as leaving ransom notes, reading and writing to many files throughout the file system, and using cryptographic libraries. These behaviors could have potentially been used to detect AESthetic as malicious using dynamic analysis. The only tested antivirus countermeasure that successfully repelled all of the tested ransomware samples was ransomware folder protection, such as ”Controlled folder access” which is offered by Windows Defender. Such an approach requires the user to manually decide which folders to protect however and it is not very user-friendly, as one needs to manually allow benign programs through the protection wall.

5. Research challenges and future research directions
In this section, we have highlighted key research challenges based on the literature review and explored future research directions. The identified research challenges include unawareness among users, lack of open-access ransomware libraries, and inadequate detection and false-positive rates for ransomware. Future research directions include edge and fog-assisted ransomware, DeepFake ransomware, remote working vulnerabilities, blockchain-based countermeasures, increases in RaaS attacks, and expansion to AESthetic.
5.1. Research challenges
1. Unawareness among users: Awareness among users is one of the fundamental challenges that needs to be addressed to reduce the impact of ransomware. For example, there is no full-proof automatic system that is able to consistently counter ransomware attacks that propagate through phishing campaigns. Although existing spam filters are efficient, there is always a possibility that some malicious emails will make their way into your inbox. In that scenario, basic knowledge of recognizing spam can save a victim from being infected. There are currently many workshops, programs, and online websites available to educate users of such threats, but based on the statistics of ransomware attacks, it seems more efforts are needed.
2. Lack of Open-Access Ransomware Libraries: In order to propose and develop new solutions that can tackle ransomware, there is an emerging need for open ransomware libraries. The availability of such libraries will help researchers to better understand the varying features behind existing ransomware samples, including their working mechanism, etc. Based on that understanding, researchers can propose better solutions in a faster time span. As it stands, it is a tedious task to implement a particular ransomware sample and then test out the countermeasure. However, collecting many of the existing ransomware samples is itself a big research challenge that needs international research collaboration, as well as a huge amount of funding to obtain the necessary resources, etc.
3. Inadequate Detection and False Positive Rates: Existing ransomware detection systems face a difficult challenge achieving both a high detection rate and few false alarms. A large number of false alarms is frustrating for administrators, whereas a low detection rate makes the system ineffective ( Maimó et al., 2019 ). Signature-based detection systems may miss attacks if the signature is too specific; conversely, the system may flag too many benign programs as ransomware if the signature is too generic. Anomaly-based detection systems flag behaviour that is sufficiently far from normal ( Kathareios et al., 2017 ). However, not all abnormal behaviour is malicious. Consequently, these systems can generate a high number of false alarms and require a human to manually review each alarm. This manual validation adds to the system workload and reduces the system’s practicality. Al-Rimy et al. Al-rimy et al. (2018) were able to achieve both high detection and low false-positive rates by combining two behavioural detection methods into a single model. However, their system relies on a time-based threshold. Hence, more research is needed to improve ransomware detection models and to increase their applicability.
5.2. Future research directions
1. Edge and Fog-assisted Ransomware Detection and Prevention using Federated Learning: There have been huge advancements in the area of Edge and Fog-based related technologies. Mukherjee et al. (2018) , Hakak et al. (2020c) , Hakak et al. (2020) , Pham et al. (2020) . Besides, with the arrival of federated learning ( Yang et al., 2019 ), numerous opportunities in terms of improving state-of-the-art machine-learning-based approaches have emerged. There is a huge possibility of utilizing these concepts to detect and prevent ransomware, based on machine learning approaches ( Liu et al., 2020 ). One of the possibilities arises by training and deploying machine learning-based algorithms into Edge/Fog-based nodes to detect and prevent ransomware. Through Federated learning, we can personalize the learning process of each respective node.
2. DeepFake Ransomware : Deepfakes are the manipulated digital representations such as images, videos where an attacker tries to mimic the real person ( Güera and Delp, 2018 ). In the future, it could be possible for attackers to create ransomware that will automatically generate DeepFake content of a victim performing some incriminatory or intimate action which he/she never did. The victim will be asked to pay the ransom in order to avoid that content being published online. To mitigate such ransomware attacks will be challenging due to the velocity of data and the availability of numerous social media channels to spread the content.
3. Remote Working Vulnerabilities : The recent COVID-19 pandemic made it mandatory for several institutions to initiate the work-from-home scenarios or implement bring your own devices (BYOD) policies ( Palanisamy et al., 2020 ). As a result of which, several vulnerabilities ( Curran, 2020 ) were exploited by the attackers that resulted in several ransomware attacks. In one of the reports by SkyBox Security, the ransomware attacks witnessed 72 percent growth compared to the previous years. Hence, it is one of the future research directions to look at mitigating such attacks during remote working scenarios.
4. Blockchain-based Countermeasures : Blockchain is an immutable decentralized ledger that makes tampering difficult ( Hakak et al., 2020a ) due to its decentralized nature along with linked hash function, timestamp function and consensus mechanism ( Hakak, Khan, Gilkar, Imran, Guizani, 2020 , Hakak, W.Z. Khan, Gilkar, Haider, Imran, Alkatheiri, 2020 ). It seems to have potential and it is an interesting research direction where blockchain-based solutions can be used to mitigate ransomware-based attacks. The first step in this direction is the work of Delgado-Mohatar et al. (2020) where the authors have highlighted the use of smart contracts for the limited payment of ransoms to get the decryption keys.
5. Increase in Ransomware-as-a-service (RaaS) Attacks : Ransomware as a service or RaaS is gaining popularity from the past few years ( Keijzer, 2020 ). In RaaS model, an experienced attacker creates ransomware and offers that code to script kiddies or gray-hat hackers for some price ( Meland, Bayoumy, Sindre, 2020 , Puat, Rahman, 2020 ). The script kiddies or gray-hat hackers then use that code to carry out their own attacks. The Cerber ransomware attack is one example of the RaaS model in action. With emerging technologies and an increasing number of internet users, there is a strong possibility for a surge in these types of attacks. Hence, mitigating such attacks in the future seems to be a potential research direction.
6. AESthetic Ransomware Artifact Development : The source code of AESthetic ransomware has been posted to GitHub at https://github.com/kregg34/AESthetic and has been made private. As we are still in initial phases of developing decryption tool for AESthetic, we aim to create artifacts for AESthetic ransomware so that researchers can evaluate the efficacy of their solutions against ransomware. On the other hand, once the decryption tool is finalised, we will release the code of AESthetic.
7. AESthetic Performance : The antivirus products were likely able to detect the other, well-known samples due to their known signatures. However, our ransomware AESthetic has no known signatures and went undetected. This may indicate that these products are relying on static analysis too much, and not effectively utilizing dynamic analysis. Dynamic analysis may be able to detect AESthetic as this was designed to have many of the tell-tale-signs of ransomware behaviour. However, to validate this claim, more research is needed owing to the blackbox nature of antivirus products.
6. Conclusion
In this work, recent advances in ransomware analysis, detection, and prevention were explored. It was found that the focus of the state-of-the-art ransomware detection techniques mostly revolve around honeypots, network traffic analysis, and machine learning based approaches. Prevention techniques mostly focused on access control, data and key backups, and hardware-based solutions. However, it seems that there is a trend in using machine learning based approaches to detect ransomware. We have conducted a number of experiments on ransomware samples, through which it was observed that there is a need for more intelligent approaches to detect and prevent ransomware. Through the experiments, it was also observed that ransomware can be easily created and used. In the end, we highlighted the existing research challenges and enumerated some future research directions in the field of ransomware.
Credit Author Statment
Craig Beaman conducted the literature review, worked on implementation details, and was involved in drafting the manuscript.
Ashley Barkworth conducted the literature review and was involved in drafting the manuscript, with particular focus on Ransomware Prevention Approaches and subsections 2.2.2.3 and 2.2.2.5-2.2.2.7 under Section 2.2.2 (“Ransomware Detection Approaches”).
Toluwalope David Akande conducted the literature review and was involved in drafting the manuscript.
Saqib Hakak designed the study, assisted in classification, worked on future research challenges & directions section, and coordinated the whole work.
M.Khurram Khan provided potential useful recommendations and directions to improve the work, assisted in addressing reviewer comments and proof-reading.
Declaration of Competing Interest
The authors declare that they have no known competing financial interests or personal relationships that could have appeared to influence the work reported in this paper.
Acknowledgements
All persons who have made substantial contributions to the work reported in the manuscript (e.g., technical help, writing and editing assistance, general support), but who do not meet the criteria for authorship, are named in the Acknowledgements and have given us their written permission to be named. If we have not included an Acknowledgements, then that indicates that we have not received substantial contributions from non-authors. The work of Muhammad Khurram Khan is supported by King Saud University, Riyadh, Saudi Arabia under the project number (RSP-2021/12).
Biographies
Craig Beaman is a graduate student at the University of New Brunswick, where he is completing a Master of Applied Cybersecurity. Craig received a B.Sc. (Honours) from the University of New Brunswick with a major in physics and minors in mathematics and computer science. His research interests include cryptography, network security, and malware detection and prevention.
Ashley Barkworth is a graduate student at the University of New Brunswick, where she is completing a masters in applied cybersecurity. Ashley received a B.Sc. (Honours) from the University of British Columbia with a major in computer science and a minor in mathematics in 2020. Her research interests include information security, cryptography, and data management in centralized systems.
Toluwalope David Akande is a graduate student at the University of New Brunswick, where he is completing a Master of Applied Cybersecurity. He received a B.Sc. (Honours) from Obafemi Awolowo University with a major in Computer Engineering. His research interests include network security, intrusion detection using machine learning and cloud computing security.
Saqib Hakak is an assistant professor at the Canadian Institute for Cybersecurity (CIC), Faculty of Computer Science, University of New Brunswick (UNB). Having more than 5+ years of industrial and academic experience, he has received several Gold/Silver awards in international innovation competitions and is serving as the technical committee member/reviewer of several reputed conference/journal venues. His current research interests include Risk management, Fake news detection using AI, Security and Privacy concerns in IoE, Applications of Federated Learning in IoT, and blockchain technology.
Muhammad Khurram Khan is currently working as a Professor of Cybersecurity at the Center of Excellence in Information Assurance, King Saud University, Kingdom of Saudi Arabia. He is founder and CEO of the ‘Global Foundation for Cyber Studies and Research’, an independent and non-partisan cybersecurity think-tank in Washington D.C, USA. He is the Editor-in-Chief of ‘Telecommunication Systems’ published by Springer-Nature with its recent impact factor of 2.314 (JCR 2021). He is also the Editor-in-Chief of Cyber Insights Magazine. He is on the editorial board of several journals including, IEEE Communications Surveys & Tutorials, IEEE Communications Magazine, IEEE Internet of Things Journal, IEEE Transactions on Consumer Electronics, Journal of Network & Computer Applications (Elsevier), IEEE Access, IEEE Consumer Electronics Magazine, PLOS ONE, and Electronic Commerce Research, etc. He has published more than 400 papers in the journals and conferences of international repute. In addition, he is an inventor of 10 US/PCT patents. He has edited 10 books/proceedings published by Springer-Verlag, Taylor & Francis and IEEE. His research areas of interest are Cybersecurity, digital authentication, IoT security, biometrics, multimedia security, cloud computing security, cyber policy, and technological innovation management. He is a fellow of the IET (UK), a fellow of the BCS (UK), and a fellow of the FTRA (Korea). His detailed profile can be visited at http://www.professorkhurram.com .
- Adamu U., Awan I. 2019 7th International Conference on Future Internet of Things and Cloud (FiCloud) 2019. Ransomware prediction using supervised learning algorithms; pp. 57–63. [ CrossRef ] [ Google Scholar ]
- Aghakhani H., Gritti F., Mecca F., Lindorfer M., Ortolani S., Balzarotti D., Vigna G., Kruegel C. Network and Distributed Systems Security (NDSS) Symposium 2020. 2020. When malware is packin’heat; limits of machine learning classifiers based on static analysis features. [ Google Scholar ]
- Akbanov M., Vassilakis V., Logothetis M. Wannacry ransomware: analysis of infection, persistence, recovery prevention and propagation mechanisms. Journal of Telecommunications and Information Technology. 2019 [ Google Scholar ]
- Al-Rimy B., Maarof M., Alazab M., Alsolami F., Shaid S., Ghaleb F., Al-Hadhrami T., Ali A. A pseudo feedback-based annotated tf-idf technique for dynamic crypto-ransomware pre-encryption boundary delineation and features extraction. IEEE Access. 2020; 8 :140586–140598. [ Google Scholar ]
- Al-rimy B., Maarof M., Prasetyo Y., Shaid S., Ariffin A. Zero-day aware decision fusion-based model for crypto-ransomware early detection. International Journal of Integrated Engineering. 2018; 10 (6) [ Google Scholar ]
- Al-rimy B., Maarof M., Shaid S. Ransomware threat success factors, taxonomy, and countermeasures: a survey and research directions. Computers & Security. 2018; 74 :144–166. [ Google Scholar ]
- Al-rimy B., Maarof M., Shaid S. Crypto-ransomware early detection model using novel incremental bagging with enhanced semi-random subspace selection. Future Generation Computer Systems. 2019; 101 :476–491. [ Google Scholar ]
- Alam M., Bhattacharya S., Dutta S., Sinha S., Mukhopadhyay D., Chattopadhyay A. 2019 IEEE International Symposium on Hardware Oriented Security and Trust (HOST) 2019. Ratafia: ransomware analysis using time and frequency informed autoencoders; pp. 218–227. [ Google Scholar ]
- Alam M., Sinha S., Bhattacharya S., Dutta S., Mukhopadhyay D., Chattopadhyay A. Rapper: ransomware prevention via performance counters. arXiv preprint arXiv:2004.01712. 2020 [ Google Scholar ]
- Alhawi O., Baldwin J., Dehghantanha A. Cyber Threat Intelligence. Springer; 2018. Leveraging Machine Learning Techniques for Windows Ransomware Network Traffic Detection; pp. 93–106. [ Google Scholar ]
- Almashhadani A., Kaiiali M., Sezer S., O’Kane P. A multi-classifier network-based crypto ransomware detection system: a case study of locky ransomware. IEEE Access. 2019; 7 :47053–47067. [ Google Scholar ]
- Alshaikh H., Nagy N.R., Hefny H. Ransomware prevention and mitigation techniques. Int J Comput Appl. 2020; 177 (40):31–39. [ Google Scholar ]
- Alzahrani A., Alshehri A., Alshahrani H., Alharthi R., Fu H., Liu A., Zhu Y. 2018 IEEE International Conference on Electro/Information Technology (EIT) IEEE; 2018. Randroid: Structural similarity approach for detecting ransomware applications in android platform; pp. 0892–0897. [ Google Scholar ]
- Ami O., Elovici Y., Hendler D. Proceedings of the 33rd Annual ACM Symposium on Applied Computing. 2018. Ransomware prevention using application authentication-based file access control; pp. 1610–1619. [ Google Scholar ]
- Andronio N., Zanero S., Maggi F. Springer-Verlag; Berlin, Heidelberg: 2015. Heldroid: Dissecting and detecting mobile ransomware; pp. 382–404. [ CrossRef ] [ Google Scholar ]
- Aslan O., Samet R. A comprehensive review on malware detection approaches. IEEE Access. 2020; 8 :6249–6271. [ Google Scholar ]
- Aurangzeb S., Aleem M., Iqbal M., Islam M., et al. Ransomware: a survey and trends. J. Inf. Assur. Secur. 2017; 6 (2):48–58. [ Google Scholar ]
- Ayub M.A., Continella A., Siraj A. 2020. An i/o request packet (irp) driven effective ransomware detection scheme using artificial neural network; pp. 319–324. [ CrossRef ] [ Google Scholar ]
- Azmoodeh A., Dehghantanha A., Conti M., Choo K.-K.R. Detecting crypto-ransomware in iot networks based on energy consumption footprint. J Ambient Intell Humaniz Comput. 2018; 9 (4):1141–1152. [ Google Scholar ]
- Bae S., Lee G., Im E. Ransomware detection using machine learning algorithms. Concurrency and Computation: Practice and Experience. 2020; 32 (18):e5422. [ Google Scholar ]
- Baek S., Jung Y., Mohaisen A., Lee S., Nyang D. 2018 IEEE 38th International Conference on Distributed Computing Systems (ICDCS) IEEE; 2018. Ssd-insider: Internal defense of solid-state drive against ransomware with perfect data recovery; pp. 875–884. [ Google Scholar ]
- Bajpai P., Enbody R. Attacking key management in ransomware. IT Prof. 2020; 22 (2):21–27. [ Google Scholar ]
- Bajpai P., Enbody R. Dissecting.net ransomware: key generation, encryption and operation. Network Security. 2020; 2020 (2):8–14. [ Google Scholar ]
- Bajpai P., Enbody R. 2020 IEEE International Conference on Electro Information Technology (EIT) 2020. An empirical study of api calls in ransomware; pp. 443–448. [ CrossRef ] [ Google Scholar ]
- Bajpai P., Sood A.K., Enbody R. 2018 APWG Symposium on Electronic Crime Research (eCrime) 2018. A key-management-based taxonomy for ransomware; pp. 1–12. [ CrossRef ] [ Google Scholar ]
- Baldwin J., Dehghantanha A. Cyber Threat Intelligence. Springer; 2018. Leveraging Support Vector Machine for Opcode Density Based Detection of Crypto-ransomware; pp. 107–136. [ Google Scholar ]
- Bekerman D., Shapira B., Rokach L., Bar A. 2015 IEEE Conference on Communications and Network Security (CNS) IEEE; 2015. Unknown malware detection using network traffic classification; pp. 134–142. [ Google Scholar ]
- Berrueta Irigoyen E., Morató Osés D., Magaña Lizarrondo E., Izal Azcárate M. A survey on detection techniques for cryptographic ransomware. IEEE Access, 2019, 7, 144925–144944. 2019 [ Google Scholar ]
- Brewer R. Ransomware attacks: detection, prevention and cure. Network Security. 2016; 2016 (9):5–9. [ Google Scholar ]
- Cabaj K., Gregorczyk M., Mazurczyk W. Software-defined networking-based crypto ransomware detection using http traffic characteristics. Computers & Electrical Engineering. 2018; 66 :353–368. [ Google Scholar ]
- Cabaj K., Mazurczyk W. Using software-defined networking for ransomware mitigation: the case of cryptowall. IEEE Netw. 2016; 30 (6):14–20. [ Google Scholar ]
- Chadha S., Kumar U. 2017 International Conference on Computing, Communication and Automation (ICCCA) IEEE; 2017. Ransomware: Let’s fight back! pp. 925–930. [ Google Scholar ]
- Chen Q., Bridges R.A. 2017 16th IEEE International Conference on Machine Learning and Applications (ICMLA) 2017. Automated behavioral analysis of malware: A case study of wannacry ransomware; pp. 454–460. [ CrossRef ] [ Google Scholar ]
- Chung M. Why employees matter in the fight against ransomware. Computer Fraud & Security. 2019; 2019 (8):8–11. [ Google Scholar ]
- Cicala F., Bertino E. Analysis of encryption key generation in modern crypto ransomware. IEEE Trans Dependable Secure Comput. 2020 doi: 10.1109/TDSC.2020.3005976. [ CrossRef ] [ Google Scholar ] 1–1
- Cohen A., Nissim N. Trusted detection of ransomware in a private cloud using machine learning methods leveraging meta-features from volatile memory. Expert Syst Appl. 2018; 102 :158–178. [ Google Scholar ]
- Continella A., Guagnelli A., Zingaro G., Pasquale G.D., Barenghi A., Zanero S., Maggi F. Proceedings of the 32nd Annual Conference on Computer Security Applications. 2016. Shieldfs: a self-healing, ransomware-aware filesystem; pp. 336–347. [ Google Scholar ]
- Cosic J., Schlehuber C., Morog D. 2019 IEEE 15th International Scientific Conference on Informatics. 2019. New challenges in forensic analysis in railway domain; pp. 000061–000064. [ CrossRef ] [ Google Scholar ]
- Creating a simple free malware analysis environment, 2017 https://www.malwaretech.com/2017/11/creating-a-simple-free-malware-analysis-environment.html .
- Curran K. Cyber security and the remote workforce. Computer Fraud & Security. 2020; 2020 (6):11–12. [ Google Scholar ]
- Cusack G., Michel O., Keller E. Proceedings of the 2018 ACM International Workshop on Security in Software Defined Networks & Network Function Virtualization. 2018. Machine learning-based detection of ransomware using sdn; pp. 1–6. [ Google Scholar ]
- file i/o, 2021 https://www.pcmag.com/encyclopedia/term/file-io .
- for Cyber Security, C. C., 2018. Ransomware: How to prevent and recover (itsap.00.099). https://www.cyber.gc.ca/en/guidance/ransomware-how-prevent-and-recover-itsap00099 .
- Dargahi T., Dehghantanha A., Bahrami P.N., Conti M., Bianchi G., Benedetto L. A cyber-kill-chain based taxonomy of crypto-ransomware features. Journal of Computer Virology and Hacking Techniques. 2019; 15 :277–305. [ Google Scholar ]
- Delgado-Mohatar O., Sierra-Cámara J., Anguiano E. Blockchain-based semi-autonomous ransomware. Future Generation Computer Systems. 2020 [ Google Scholar ]
- Genç Z., Lenzini G., Ryan P. International Conference on Detection of Intrusions and Malware, and Vulnerability Assessment. Springer; 2018. No random, no ransom: a key to stop cryptographic ransomware; pp. 234–255. [ Google Scholar ]
- Gomez-Hernandez J., Alvarez-Gonzalez L., Garcia-Teodoro P. R-Locker: thwarting ransomware action through a honeyfile-based approach. Computers & Security. 2018; 73 :389–398. [ Google Scholar ]
- Groenewegen A., Alqabandi M., Elamin M., Paardekooper P. 2020. A behavioral analysis of the ransomware strain nefilim. [ CrossRef ] [ Google Scholar ]
- Güera D., Delp E. 2018 15th IEEE International Conference on Advanced Video and Signal Based Surveillance (AVSS) IEEE; 2018. Deepfake video detection using recurrent neural networks; pp. 1–6. [ Google Scholar ]
- Hakak S., Khan W., Gilkar G., Assiri B., Alazab M., Bhattacharya S., Reddy G. Recent advances in blockchain technology: a survey on applications and challenges. arXiv preprint arXiv:2009.05718. 2020 [ Google Scholar ]
- Hakak S., Khan W., Gilkar G., Imran M., Guizani N. Securing smart cities through blockchain technology: architecture, requirements, and challenges. IEEE Netw. 2020; 34 (1):8–14. [ Google Scholar ]
- Hakak S., Khan W., Imran M., Choo K., Shoaib M. Have you been a victim of covid-19-related cyber incidents? survey, taxonomy, and mitigation strategies. IEEE Access. 2020; 8 :124134–124144. [ PMC free article ] [ PubMed ] [ Google Scholar ]
- Hakak, S., Ray, S., Khan, W., Scheme, E., 2020. A framework for edge-assisted healthcare data analytics using federated learning.
- Hakak S., W.Z. Khan W.Z., Gilkar G.A., Haider N., Imran M., Alkatheiri M.S. Industrial wastewater management using blockchain technology: architecture, requirements, and future directions. IEEE Internet of Things Magazine. 2020; 3 (2):38–43. [ Google Scholar ]
- Hassan N. Ransomware Revealed. Springer; 2019. Ransomware Families; pp. 47–68. [ Google Scholar ]
- Homayoun S., Dehghantanha A., Ahmadzadeh M., Hashemi S., Khayami R., Choo K., Newton D. Drthis: deep ransomware threat hunting and intelligence system at the fog layer. Future Generation Computer Systems. 2019; 90 :94–104. [ Google Scholar ]
- Huang J., Xu J., Xing X., Liu P., Qureshi M.K. Proceedings of the 2017 ACM SIGSAC Conference on Computer and Communications Security. 2017. Flashguard: Leveraging intrinsic flash properties to defend against encryption ransomware; pp. 2231–2244. [ Google Scholar ]
- Hull G., John H., Arief B. Ransomware deployment methods and analysis: views from a predictive model and human responses. Crime Sci. 2019; 8 (1):2. [ Google Scholar ]
- Jain G., Rani N. Springer Singapore; 2020. Awareness learning analysis of malware and ransomware in bitcoin; pp. 765–776. [ Google Scholar ]
- Javaheri D., Hosseinzadeh M., Rahmani A. Detection and elimination of spyware and ransomware by intercepting kernel-level system routines. IEEE Access. 2018; 6 :78321–78332. [ Google Scholar ]
- Jung S., Won Y. Ransomware detection method based on context-aware entropy analysis. Soft comput. 2018; 22 (20):6731–6740. [ Google Scholar ]
- Kara I., Aydos M. 2020 11th IEEE Annual Ubiquitous Computing, Electronics Mobile Communication Conference (UEMCON) 2020. Cyber fraud: Detection and analysis of the crypto-ransomware; pp. 0764–0769. [ CrossRef ] [ Google Scholar ]
- Karapapas C., Pittaras I., Fotiou N., Polyzos G.C. 2020 IEEE International Conference on Blockchain and Cryptocurrency (ICBC) 2020. Ransomware as a service using smart contracts and ipfs; pp. 1–5. [ CrossRef ] [ Google Scholar ]
- Kathareios G., Anghel A., Mate A., Clauberg R., Gusat M. Catch it if you can: real-time network anomaly detection with low false alarm rates. 2017 16th IEEE International Conference on Machine Learning and Applications (ICMLA) 2017 doi: 10.1109/icmla.2017.00-36. [ CrossRef ] [ Google Scholar ]
- Keijzer N. The new generation of ransomware: an in depth study of Ransomware-as-a-Service. University of Twente; 2020. [ Google Scholar ]
- Khammas B. Ransomware detection using random forest technique. ICT Express. 2020; 6 (4):325–331. [ Google Scholar ]
- Khan F., Ncube C., Ramasamy L.K., Kadry S., Nam Y. A digital dna sequencing engine for ransomware detection using machine learning. IEEE Access. 2020; 8 :119710–119719. doi: 10.1109/ACCESS.2020.3003785. [ CrossRef ] [ Google Scholar ]
- Kharaz A., Arshad S., Mulliner C., Robertson W., Kirda E. 25th { USENIX } Security Symposium ( { USENIX } Security 16) 2016. { UNVEIL } : A large-scale, automated approach to detecting ransomware; pp. 757–772. [ Google Scholar ]
- Kharraz A., Kirda E. International Symposium on Research in Attacks, Intrusions, and Defenses. Springer; 2017. Redemption: Real-time protection against ransomware at end-hosts; pp. 98–119. [ Google Scholar ]
- Kim D., Lee J. Blacklist vs. whitelist-based ransomware solutions. IEEE Consum. Electron. Mag. 2020; 9 (3):22–28. doi: 10.1109/MCE.2019.2956192. [ CrossRef ] [ Google Scholar ]
- Kok S., Abdullah A., Jhanjhi N. Early detection of crypto-ransomware using pre-encryption detection algorithm. Journal of King Saud University-Computer and Information Sciences. 2020 [ Google Scholar ]
- Kok S., Abdullah A., Jhanjhi N., Supramaniam M. Prevention of crypto-ransomware using a pre-encryption detection algorithm. Computers. 2019; 8 (4):79. [ Google Scholar ]
- Kok S., Abdullah A., Jhanjhi N., Supramaniam M. Ransomware, threat and detection techniques: areview. Int. J. Comput. Sci. Netw. Secur. 2019; 19 (2):136. [ Google Scholar ]
- Kolodenker E., Koch W., Stringhini G., Egele M. Proceedings of the 2017 ACM on Asia Conference on Computer and Communications Security. 2017. Paybreak: Defense against cryptographic ransomware; pp. 599–611. [ Google Scholar ]
- Komatwar R., Kokare M. A survey on malware detection and classification. Journal of Applied Security Research. 2020:1–31. [ Google Scholar ]
- Lallie H., Shepherd L., Nurse J., Erola A., Epiphaniou G., Maple C., Bellekens X. Cyber security in the age of covid-19: a timeline and analysis of cyber-crime and cyber-attacks during the pandemic. arXiv preprint arXiv:2006.11929. 2020 [ PMC free article ] [ PubMed ] [ Google Scholar ]
- Lee K., Lee S., Yim K. Machine learning based file entropy analysis for ransomware detection in backup systems. IEEE Access. 2019; 7 :110205–110215. [ Google Scholar ]
- Lee K., Yim K., Seo J. Ransomware prevention technique using key backup. Concurrency and Computation: Practice and Experience. 2018; 30 (3):e4337. [ Google Scholar ]
- Liu X., Li H., Xu G., Lu R., He M. Adaptive privacy-preserving federated learning. PEER-TO-PEER NETWORKING AND APPLICATIONS. 2020 [ Google Scholar ]
- Ltd., S., 2020. Paying the ransom doubles cost of recovering from a ransomware attack, according to sophos. https://www.globenewswire.com/news-release/2020/05/12/2031961/0/en/Paying-the-Ransom-Doubles-Cost-of-Recovering-from-a-Ransomware-Attack-According-to-Sophos.html .
- Mackenzie P. Wannacry aftershock. Sophos, disponible en ligne: https://www. sophos. com/en-us/medialibrary/PDFs/technical-papers/WannaCry-Aftershock. pdf. 2019 [ Google Scholar ]
- Maimó L., Celdran A., Gomez A., Clemente F., Weimer J., Lee I. Intelligent and dynamic ransomware spread detection and mitigation in integrated clinical environments. Sensors. 2019; 19 (5):1114. doi: 10.3390/s19051114. [ PMC free article ] [ PubMed ] [ CrossRef ] [ Google Scholar ]
- Manavi F., Hamzeh A. A new method for ransomware detection based on pe header using convolutional neural networks. 2020 17th International ISC Conference on Information Security and Cryptology (ISCISC) 2020 doi: 10.1109/ISCISC51277.2020.9261903. [ CrossRef ] [ Google Scholar ]
- Mattei T. Privacy, confidentiality, and security of health care information: lessons from the recent wannacry cyberattack. World Neurosurg. 2017; 104 :972–974. [ PubMed ] [ Google Scholar ]
- McIntosh T., Watters P., Kayes A., Ng A., Chen Y. Enforcing situation-aware access control to build malware-resilient file systems. Future Generation Computer Systems. 2021; 115 :568–582. doi: 10.1016/j.future.2020.09.035. [ CrossRef ] [ Google Scholar ]
- Mehnaz S., Mudgerikar A., Bertino E. International Symposium on Research in Attacks, Intrusions, and Defenses. Springer; 2018. Rwguard: A real-time detection system against cryptographic ransomware; pp. 114–136. [ Google Scholar ]
- Meland P., Bayoumy Y., Sindre G. The ransomware-as-a-service economy within the darknet. Computers & Security. 2020:101762. [ Google Scholar ]
- Min D., Park D., Ahn J., Walker R., Lee J., Park S., Kim Y. Amoeba: an autonomous backup and recovery ssd for ransomware attack defense. IEEE Comput. Archit. Lett. 2018; 17 (2):245–248. [ Google Scholar ]
- Monika, Zavarsky P., Lindskog D. Experimental analysis of ransomware on windows and android platforms: evolution and characterization. Procedia Comput Sci. 2016; 94 :465–472. [ Google Scholar ]
- Moore C. 2016 Cybersecurity and Cyberforensics Conference (CCC) IEEE; 2016. Detecting ransomware with honeypot techniques; pp. 77–81. [ Google Scholar ]
- Morato D., Berrueta E., Magaña E., Izal M. Ransomware early detection by the analysis of file sharing traffic. Journal of Network and Computer Applications. 2018; 124 :14–32. [ Google Scholar ]
- Mukherjee M., Shu L., Wang D. Survey of fog computing: fundamental, network applications, and research challenges. IEEE Communications Surveys & Tutorials. 2018; 20 (3):1826–1857. [ Google Scholar ]
- Muslim A., Dzulkifli D., Nadhim M.H., Abdellah R. 2019. A study of ransomware attacks: Evolution and prevention. [ Google Scholar ]
- Nadir I., Bakhshi T. 2018 International Conference on Computing, Mathematics and Engineering Technologies (iCoMET) 2018. Contemporary cybercrime: A taxonomy of ransomware threats mitigation techniques; pp. 1–7. [ CrossRef ] [ Google Scholar ]
- Nahmias D., Cohen A., Nissim N., Elovici Y. Deep feature transfer learning for trusted and automated malware signature generation in private cloud environments. Neural Networks. 2020; 124 :243–257. [ PubMed ] [ Google Scholar ]
- Naseer A., Mir R., Mir A., Aleem M. Windows-based ransomware: a survey. Journal of Information Assurance & Security. 2020; 15 (3) [ Google Scholar ]
- Natanzon, A., Derbeko, P., Stern, U., Bakshi, M., Manusov, Y., 2018. Ransomware detection using i/o patterns. US Patent 10,078,459.
- Or-Meir O., Nissim N., Elovici Y., Rokach L. Dynamic malware analysis in the modern era’a state of the art survey. ACM Computing Surveys (CSUR) 2019; 52 (5):1–48. [ Google Scholar ]
- Or-Meir O., Nissim N., Elovici Y., Rokach L. Dynamic malware analysis in the modern era’a state of the art survey. ACM Comput. Surv. 2019; 52 (5) doi: 10.1145/3329786. [ CrossRef ] [ Google Scholar ]
- Palanisamy R., Norman A., Kiah M. Byod policy compliance: risks and strategies in organizations. Journal of Computer Information Systems. 2020:1–12. [ Google Scholar ]
- Parkinson S. Use of access control to minimise ransomware impact. Network Security. 2017; 2017 (7):5–8. [ Google Scholar ]
- Pham Q., Fang F., Ha V., Piran M., Le M., Le L., Hwang W., Ding Z. A survey of multi-access edge computing in 5g and beyond: fundamentals, technology integration, and state-of-the-art. IEEE Access. 2020; 8 :116974–117017. [ Google Scholar ]
- Poudyal S., Dasgupta D., Akhtar Z., Gupta K. 14th International Conference on Malicious and Unwanted Software” MALCON. 2019. A multi-level ransomware detection framework using natural language processing and machine learning. [ Google Scholar ]
- Poudyal S., Subedi K.P., Dasgupta D. 2018 IEEE Symposium Series on Computational Intelligence (SSCI) IEEE; 2018. A framework for analyzing ransomware using machine learning; pp. 1692–1699. [ Google Scholar ]
- Pranggono B., Arabo A. Covid-19 pandemic cybersecurity issues. Internet Technology Letters. 2020; n/a (n/a) doi: 10.1002/itl2.247. [ CrossRef ] [ Google Scholar ]
- Puat H., Rahman N. Ransomware as a service and public awareness. PalArch’s Journal of Archaeology of Egypt/Egyptology. 2020; 17 (7):5277–5292. [ Google Scholar ]
- Qin B., Wang Y., Ma C. 2020 International Conference on Big Data, Artificial Intelligence and Internet of Things Engineering (ICBAIE) 2020. Api call based ransomware dynamic detection approach using textcnn; pp. 162–166. [ CrossRef ] [ Google Scholar ]
- Quinkert, F., Holz, T., Hossain, K., Ferrara, E., Lerman, K., 2018a. Raptor: Ransomware attack predictor. 1803.01598.
- Quinkert F., Holz T., Hossain K., Ferrara E., Lerman K. Raptor: ransomware attack predictor. arXiv preprint arXiv:1803.01598. 2018 [ Google Scholar ]
- Ramesh G., Menen A. Automated dynamic approach for detecting ransomware using finite-state machine. Decis Support Syst. 2020; 138 :113400. [ Google Scholar ]
- Richardson R., North M. Ransomware: evolution, mitigation and prevention. International Management Review. 2017; 13 (1):10–21. [ Google Scholar ]
- Saeed M. Malware in computer systems: problems and solutions. IJID (International Journal on Informatics for Development) 2020; 9 (1):1–8. [ Google Scholar ]
- Salehi S., Shahriari H., Ahmadian M.M., Tazik L. 2018 15th International ISC (Iranian Society of Cryptology) Conference on Information Security and Cryptology (ISCISC) 2018. A novel approach for detecting dga-based ransomwares; pp. 1–7. [ CrossRef ] [ Google Scholar ]
- Scaife N., Carter H., Traynor P., Butler K.R.B. 2016 IEEE 36th International Conference on Distributed Computing Systems (ICDCS) 2016. Cryptolock (and drop it): Stopping ransomware attacks on user data; pp. 303–312. [ CrossRef ] [ Google Scholar ]
- Sgandurra D., Muñoz-González L., Mohsen R., Lupu E.C. Automated dynamic analysis of ransomware: benefits, limitations and use for detection. arXiv preprint arXiv:1609.03020. 2016 [ Google Scholar ]
- Sharafaldin I., Lashkari A., Hakak S., Ghorbani A. 2019 International Carnahan Conference on Security Technology (ICCST) IEEE; 2019. Developing realistic distributed denial of service (ddos) attack dataset and taxonomy; pp. 1–8. [ Google Scholar ]
- Sharmeen S., Ahmed Y.A., Huda S., Koçer B.A., Hassan M.M. Avoiding future digital extortion through robust protection against ransomware threats using deep learning based adaptive approaches. IEEE Access. 2020; 8 :24522–24534. doi: 10.1109/ACCESS.2020.2970466. [ CrossRef ] [ Google Scholar ]
- Shaukat S., Ribeiro V. 2018 10th International Conference on Communication Systems & Networks (COMSNETS) IEEE; 2018. Ransomwall: A layered defense system against cryptographic ransomware attacks using machine learning; pp. 356–363. [ Google Scholar ]
- Shijo P., Salim A. Integrated static and dynamic analysis for malware detection. Procedia Comput Sci. 2015; 46 :804–811. [ Google Scholar ]
- Silva J., Hernandez-Alvarez M. 2017 IEEE Second Ecuador Technical Chapters Meeting (ETCM) IEEE; 2017. Large scale ransomware detection by cognitive security; pp. 1–4. [ Google Scholar ]
- Srinivasan C. Hobby hackers to billion-dollar industry: the evolution of ransomware. Computer Fraud & Security. 2017; 2017 (11):7–9. doi: 10.1016/S1361-3723(17)30081-7. [ CrossRef ] [ Google Scholar ]
- Tailor J., Patel A. A comprehensive survey: ransomware attacks prevention, monitoring and damage control. International Journal of Research and Scientific Innovation (IJRSI) 2017; 4 :2321–2705. [ Google Scholar ]
- Takeuchi Y., Sakai K., Fukumoto S. Proceedings of the 47th International Conference on Parallel Processing Companion. 2018. Detecting ransomware using support vector machines; pp. 1–6. [ Google Scholar ]
- Thezoo, 2021 https://github.com/ytisf/theZoo/tree/master/malwares/Binaries .
- Thomas J. Individual cyber security: empowering employees to resist spear phishing to prevent identity theft and ransomware attacks. Thomas, JE (2018). Individual cyber security: Empowering employees to resist spear phishing to prevent identity theft and ransomware attacks. International Journal of Business Management. 2018; 12 (3):1–23. [ Google Scholar ]
- Thomas J., Galligher G. Improving backup system evaluations in information security risk assessments to combat ransomware. Computer and Information Science. 2018; 11 (1) [ Google Scholar ]
- url, 2021 https://www.sophos.com/en-us/press-office/press-releases/2021/04/ransomware-recovery-cost-reaches-nearly-dollar-2-million-more-than-doubling-in-a-year.aspx .
- Walker A., Sengupta S. MILCOM 2019-2019 IEEE Military Communications Conference (MILCOM) IEEE; 2019. Insights into malware detection via behavioral frequency analysis using machine learning; pp. 1–6. [ Google Scholar ]
- Wang Z., Huang D., Zhu Y., Li B., Chung C. Efficient attribute-based comparable data access control. IEEE Trans. Comput. 2015; 64 (12):3430–3443. [ Google Scholar ]
- What is the difference between api and system call. 2018 https://pediaa.com/what-is-the-difference-between-api-and-system-call .
- Wilner A., Jeffery A., Lalor J., Matthews K., Robinson K., Rosolska A., Yorgoro C. On the social science of ransomware: technology, security, and society. Comparative Strategy. 2019; 38 (4):347–370. [ Google Scholar ]
- Yang Q., Liu Y., Chen T., Tong Y. Federated machine learning: concept and applications. ACM Transactions on Intelligent Systems and Technology (TIST) 2019; 10 (2):1–19. [ Google Scholar ]
- Yaqoob I., Ahmed E., ur Rehman M., Ahmed A., Al-garadi M., Imran M., Guizani M. The rise of ransomware and emerging security challenges in the internet of things. Comput. Networks. 2017; 129 :444–458. [ Google Scholar ]
- Zhang B., Xiao W., Xiao X., Sangaiah A., Zhang W., Zhang J. Ransomware classification using patch-based cnn and self-attention network on embedded n-grams of opcodes. Future Generation Computer Systems. 2020; 110 :708–720. [ Google Scholar ]
- Zhang-Kennedy L., Assal H., Rocheleau J., Mohamed R., Baig K., Chiasson S. 27th { USENIX } Security Symposium ( { USENIX } Security 18) 2018. The aftermath of a crypto-ransomware attack at a large academic institution; pp. 1061–1078. [ Google Scholar ]
- Zimba A., Mulenga M. A dive into the deep: demystifying wannacry crypto ransomware network attacks via digital forensics. International Journal on Information Technologies and Security. 2018; 10 :57–68. [ Google Scholar ]
- Zimba A., Wang Z., Chen H., Mulenga M. Recent advances in cryptovirology: state-of-the-art crypto mining and crypto ransomware attacks. KSII Trans. Internet Inf. Syst. 2019; 13 :3258–3279. doi: 10.3837/tiis.2019.06.027. [ CrossRef ] [ Google Scholar ]
It’s More Than Just Money: The Real-World Harms from Ransomware Attacks
- Conference paper
- First Online: 26 July 2023
- Cite this conference paper

- Nandita Pattnaik 17 ,
- Jason R. C. Nurse 17 , 18 ,
- Sarah Turner 17 ,
- Gareth Mott 17 ,
- Jamie MacColl 18 ,
- Pia Huesch 18 &
- James Sullivan 18
Part of the book series: IFIP Advances in Information and Communication Technology ((IFIPAICT,volume 674))
Included in the following conference series:
- International Symposium on Human Aspects of Information Security and Assurance
767 Accesses
4 Citations
21 Altmetric
As cyber-attacks continue to increase in frequency and sophistication, organisations must be better prepared to face the reality of an incident. Any organisational plan that intends to be successful at managing security risks must clearly understand the harm (i.e., negative impact) and the various parties affected in the aftermath of an attack. To this end, this article conducts a novel exploration into the multitude of real-world harms that can arise from cyber-attacks, with a particular focus on ransomware incidents given their current prominence. This exploration also leads to the proposal of a new, robust methodology for modelling harms from such incidents. We draw on publicly-available case data on high-profile ransomware incidents to examine the types of harm that emerge at various stages after a ransomware attack and how harms (e.g., an offline enterprise server) may trigger other negative, potentially more substantial impacts for stakeholders (e.g., the inability for a customer to access their social welfare benefits or bank account). Prominent findings from our analysis include the identification of a notable set of social/human harms beyond the business itself (and beyond the financial payment of a ransom) and a complex web of harms that emerge after attacks regardless of the industry sector. We also observed that deciphering the full extent and sequence of harms can be a challenging undertaking because of the lack of complete data available. This paper consequently argues for more transparency on ransomware harms, as it would lead to a better understanding of the realities of these incidents to the benefit of organisations and society more generally.
This is a preview of subscription content, log in via an institution to check access.
Access this chapter
Subscribe and save.
- Get 10 units per month
- Download Article/Chapter or eBook
- 1 Unit = 1 Article or 1 Chapter
- Cancel anytime
- Available as PDF
- Read on any device
- Instant download
- Own it forever
- Available as EPUB and PDF
- Compact, lightweight edition
- Dispatched in 3 to 5 business days
- Free shipping worldwide - see info
- Durable hardcover edition
Tax calculation will be finalised at checkout
Purchases are for personal use only
Institutional subscriptions
https://www.mendeley.com/ .
Agrafiotis, I., Nurse, J.R.C., Goldsmith, M., Creese, S., Upton, D.: A taxonomy of cyber-harms: defining the impacts of cyber-attacks and understanding how they propagate. J. Cybersecurity 4 (1) (2018)
Google Scholar
Anna, I.: Travelex paid hackers multimillion-dollar ransom before hitting new obstacles (2020). https://www.wsj.com/articles/travelex-paid-hackers-multimillion-dollar-ransom-before-hitting-new-obstacles-11586440800
Axon, L., Erola, A., Agrafiotis, I., Goldsmith, M., Creese, S.: Analysing cyber-insurance claims to design harm-propagation trees. In: International Conference on Cyber Situational Awareness, Data Analytics and Assessment (2019)
BBCNews: Cyber attack: Hackers post hackney council’s ‘stolen documents’ - BBC news (2021). https://www.bbc.co.uk/news/uk-england-london-55574580
Heather, K.: Ransomware attacks are closing schools, delaying chemotherapy and derailing everyday life (2021). https://www.washingtonpost.com/technology/2021/07/08/ransomware-human-impact/
Knight, R., Nurse, J.R.C.: A framework for effective corporate communication after cyber security incidents. Comput. Secur. 99 , 102036 (2020)
Article Google Scholar
Mahtani, M., Macaya, M., Hayes, M., Rocha, V.: Latest on the us gas demand spikes (2021). https://edition.cnn.com/us/live-news/us-gas-demand-hack-05-11-21/index.html
Matt, B.: The Untold Story of a Crippling Ransomware Attack | WIRED UK (2023). https://www.wired.co.uk/article/ransomware-attack-recovery-hackney
Meurs, T., Junger, M., Tews, E., Abhishta, A.: Ransomware: how attacker’s effort, victim characteristics and context influence ransom requested, payment and financial loss. In: Symposium on Electronic Crime Research (eCrime) (2022)
Michael, K.S.: Colonial pipeline hack explained: Everything you need to know (2022). https://www.techtarget.com/whatis/feature/Colonial-Pipeline-hack-explained-Everything-you-need-to-know
NCSC: NCSC Annual Review 2022 (2022). https://www.ncsc.gov.uk/collection/annual-review-2022
Newman, L.H.: How vice society got away with a global ransomware spree (2022). https://www.wired.com/story/vice-society-ransomware-gang/
Newman, L.H.: Atlanta spent \$2.6 m to recover from a \$52,000 ransomware scare (2023). https://www.wired.com/story/atlanta-spent-26m-recover-from-ransomware-scare/
Oz, H., Aris, A., Levi, A., Uluagac, A.S.: A survey on ransomware: evolution, taxonomy, and defense solutions. ACM Comput. Surv. 54 (11s), 1–37 (2022)
PWC: Conti cyber attack on the HSE, independent post incident review (2021). https://www.hse.ie/eng/services/publications/conti-cyber-attack-on-the-hse-full-report.pdf
Schwartz, M.J.: Ireland set to notify 20,000 more health data breach victims (2023). https://www.bankinfosecurity.com/ireland-set-to-notify-20000-victims-2021-data-breach-a-21255
Shevchenko, P.V., Jang, J., Malavasi, M., Peters, G.W., Sofronov, G., Trück, S.: The nature of losses from cyber-related events: risk categories and business sectors. J. Cybersecurity 9 , 1–12 (2023)
Smart, W.: Lessons learned review of the WannaCry Ransomware Cyber Attack (2018). https://www.england.nhs.uk/wp-content/uploads/2018/02/lessons-learned-review-wannacry-ransomware-cyber-attack-cio-review.pdf
Statista: Global ransomware victimization rate 2022 | Statista (2023). https://www.statista.com/statistics/204457/businesses-ransomware-attack-rate/
Stupp, C.: London borough of hackney struggles with recovery months after ransomware attack (2021). https://www.wsj.com/articles/london-borough-of-hackney-struggles-with-recovery-months-after-ransomware-attack-11626427801
Tidy, J.: Travelex: Banks halt currency service after cyber-attack (2020). https://www.bbc.co.uk/news/business-51034731
UK Government: UK cracks down on ransomware actors (2023). https://www.gov.uk/government/news/uk-cracks-down-on-ransomware-actors
Wheeler, T., Alderdice, J.L.: Cyber collateral: Wannacry & the impact of cyberattacks on the mental health of critical infrastructure defenders. Changing Character of War Centre (CCW) (2022)
Wilner, A., et al.: On the social science of ransomware: technology, security, and society. Comp. Strategy 38 (4), 347–370 (2019)
Yamany, B., Azer, M.A., Abdelbaki, N.: Ransomware clustering and classification using similarity matrix. In: 2nd International Mobile, Intelligent, and Ubiquitous Computing Conference, pp. 41–46 (2022)
Download references
Acknowledgements
This research was funded by The Research Institute for Sociotechnical Cyber Security, a collaboration of the UK’s Engineering and Physical Sciences Research Council (EPSRC) and the National Cyber Security Centre (NCSC). We also thank Keenan Jones for contributions to the earlier parts of this research.
Author information
Authors and affiliations.
School of Computing & Institute of Cyber Security for Society (iCSS), University of Kent, Canterbury, UK
Nandita Pattnaik, Jason R. C. Nurse, Sarah Turner & Gareth Mott
Royal United Services Institute (RUSI), London, UK
Jason R. C. Nurse, Jamie MacColl, Pia Huesch & James Sullivan
You can also search for this author in PubMed Google Scholar
Corresponding author
Correspondence to Jason R. C. Nurse .
Editor information
Editors and affiliations.
University of Nottingham, Nottingham, UK
Steven Furnell
University of Plymouth, Plymouth, UK
Nathan Clarke
Rights and permissions
Reprints and permissions
Copyright information
© 2023 IFIP International Federation for Information Processing
About this paper
Cite this paper.
Pattnaik, N. et al. (2023). It’s More Than Just Money: The Real-World Harms from Ransomware Attacks. In: Furnell, S., Clarke, N. (eds) Human Aspects of Information Security and Assurance. HAISA 2023. IFIP Advances in Information and Communication Technology, vol 674. Springer, Cham. https://doi.org/10.1007/978-3-031-38530-8_21
Download citation
DOI : https://doi.org/10.1007/978-3-031-38530-8_21
Published : 26 July 2023
Publisher Name : Springer, Cham
Print ISBN : 978-3-031-38529-2
Online ISBN : 978-3-031-38530-8
eBook Packages : Computer Science Computer Science (R0)
Share this paper
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Publish with us
Policies and ethics
Societies and partnerships

- Find a journal
- Track your research
Real-World Cloud Attacks: The True Tasks of Cloud Ransomware Mitigation Real-World Cloud Attacks: The True Tasks of Cloud Ransomware Mitigation
Cloud breaches are inevitable — and so is cloud ransomware. (Second of two parts.)

September 1, 2022
In Part 1 of our tales of real-world cloud attacks , we examined real-world examples of two common cloud attacks. The first starting from a software-as-a-service (SaaS) marketplace, demonstrating the breadth of potential access vectors for cloud attacks and how it can enable lateral movement into other cloud resources, including a company's AWS environment. The second cloud attack demonstrated how attackers take over cloud infrastructure to inject cryptominers for their profit.
As we have witnessed, more attacks have moved onto the cloud, so it was only a matter of time before ransomware attacks did, too. Let's look at two scenarios where attackers leveraged ransomware to gain profits, and how unique cloud capabilities helped victims avoid paying the ransom.
MongoDB Ransomware Demand Mitigated
The first case (or rather cases, as this attack has appeared numerous times) is the notorious MongoDB ransomware , which has been ongoing for years. The attack itself is simple— attackers use a script to scan the internet (and now, common cloud vendor address spaces) for hosts running MongoDB exposed to the internet. The attackers then try to connect to the MongoDB with the empty admin password. If successful, the attack erases the database and replaces it with a double ransomware note: pay, and your data will be returned; don't pay, and your data will be leaked.
Intervention was necessary to address the second part of the extortion scheme: data leakage. Luckily, the company had data backups, so recovery was easy, but the database contained considerable amounts of personally identifiable information (PII), which, if leaked, would be a major crisis for the company. This forced them into the position of either paying a hefty ransom or dealing with the press. MongoDB default logging, unfortunately, cannot provide a definitive answer regarding the data accessed, as not all potential types of data collection commands are logged by default.
This is where the cloud infrastructure became an advantage. While MongoDB may not log every command, AWS logs the traffic going in and out of servers, because it charges for network costs. Correlating the network traffic going out of the attacked server with the times when the attackers were connected to the compromised MongoDB server provided proof that the data could not have been downloaded by the attackers.
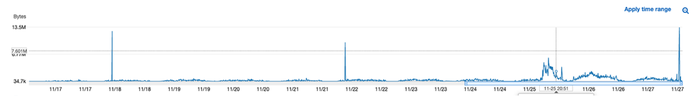
AWS traffic log over 10 day period. The marker represents the incident time. Source: Mitiga
This allowed the company to avoid paying the ransom and ignore the threat. As expected, nothing further was heard from the attackers.
Mitigating Ransomware in a Cloud Environment
Another company experienced an attack on its main servers running on AWS EC2 , where it was hit by a ransomware Trojan, not unlike those seen on on-premises servers. As often occurs these days, this was another double-extortion ransomware attack and the company needed help dealing with both issues.
Luckily, due to the company's cloud architecture and preparedness, there were AWS snapshots of the environment going back 14 days. The attackers were unaware of the snapshots and had not disabled them in their attack. This allowed the company to immediately revert to the day before the data encryption, resolving the first part of the attack with minimal effort. That still left two challenges to deal with: the potential data leak and the eradication of the attackers from the environment.
To address these challenges, there was a full investigation of the breach, which turned out to be quite complex due to the hybrid nature of their environment. The attackers compromised a single account with limited access, used by an IT person. They then identified a legacy on-premises server where that individual was an admin and used it to take over the Okta service account, allowing privilege escalation. Finally, using a decommissioned VPN service, they were able to hop to the cloud environment. Using the elevated privileges, they took over the EC2 servers and installed the malware.
The investigation yielded two significant findings. The first was the attack timeline. It showed that the compromise of all hosts occurred before the earliest snapshots were taken, indicating that the recovered servers were compromised and could not be used. New servers were installed, the data was transferred to them, and the original affected servers were purged.
The second finding was even more surprising. Malware analysis identified that the attackers used rclone.exe to copy the files to a remote location. The connection credentials were hardcoded in the malware, so the company was able to connect to the same location, identify, and remove their files, eliminating the attackers' access to the files, eradicating the extortion aspect of the attack.
Cloud Breaches Are Here to Stay
As these real-life scenarios reveal, attackers are infiltrating the cloud and cloud breaches are on the rise. It's time for organizations to prepare for cloud incidents. Cybercriminals are leveraging cloud capabilities in attacks, and you should use them, too, to protect your organization and prevent a crisis from hitting the headlines.
About the Author

CTO and Co-Founder, Mitiga
Ofer Maor is a leading technology expert and entrepreneur with 20+ years of experience in IT and security. In the past two decades, Ofer has helped successful security companies build and deliver technology innovation and products. His responsibilities ranged from hands-on technology research, development, networking, IT, and (ethical) hacking, through product building, strategy, marketing and sales, and all the way to M&A of multiple companies.
As CTO at Mitiga, Ofer is reshaping how organizations prepare for and deal with breaches, focusing on the new era of attacks across cloud, multi-cloud, and hybrid-cloud environments.
In the last few years, Ofer was part of an exciting journey with Synopsys (SNPS) to become the leader in software security and quality through the acquisition and integration of various leading technologies and solutions in this space. This journey offered him a unique point of view into how technologies are built, sold, and achieve market domination.
You May Also Like
Securing Your Cloud Assets
Determining Exposure and Risk In The Event of a Breach
Developing a Cyber Risk Assessment for the C-Suite
Catch the Threat Before it Catches you: Proactive Ransomware Defense
How to Evaluate Hybrid-Cloud Network Policies and Enhance Security
[Virtual Event] The Essential Guide to Cloud Management
Black Hat Europe - December 9-12 - Learn More
SecTor - Canada's IT Security Conference Oct 22-24 - Learn More
Editor's Choice

Threat Hunting's Evolution:From On-Premises to the Cloud
State of Enterprise Cloud Security
Managing Third-Party Risk Through Situational Awareness
2024 InformationWeek US IT Salary Report
The Foundation for Building Scalable Applications to Fuel Customer Satisfaction and Growth
Generative AI Gifts
5 Essential Insights into Generative AI for Security Leaders
5 Critical Controls for World-Class OT Cybersecurity
The Future of Audit, Risk, and Compliance: Exploring AI's Transformative Impact, Use Cases, and Risks
Threat Hunting in the Cloud: Adapting to the New Landscape
Leading Auto Manufacturer Hyundai Implements Workspot Enterprise Desktop Cloud. Learn More
Case Study: Top 10 Takeaways from a Ransomware Attack
Case Studies
PREVENTION IS ONLY PART OF THE PLAN, AND IT’S NOT ENOUGH!
An eye-opening experience, top 10 takeaways.
- Cybersecurity insurance is essential. Make sure you understand in detail what actions are required (or prohibited!) to ensure payout
- Keep the insurance policy and other highly sensitive contracts in a separate, secure location so they are not exfiltrated and used against you
- Have an Extended Detection and Response (XDR) or Managed Detection and Response (MDR) solution in place4. Implement a network vulnerability scanning tool
- Implement a network vulnerability scanning tool
- Conduct third party PEN testing on a yearly schedule
- Remove admin rights for physical PCs so people cannot install software; strengthen password policy
- Have 3 layers of backups: Local, Public Cloud, Immutable
- Conduct Employee training every October. Cybersecurity Awareness Month is a good time for additional focus on ransomware prevention and recovery planning. Communicate ongoing reminders about attack vectors
- Have cash on hand –you’ll have to pay up front as insurance companies only reimburse
- Workspot Cloud PCs were essential for recovering productivity within hours of the attack
IS THERE AN “ACCESS GAP” IN YOUR PLAN?
The new strategy for ransomware recovery: cloud pcs.
Cloud PC adoption continues to gain momentum as IT and business leaders discover the everyday security and agility benefits that take enterprise organizations into the future. Ransomware recovery is a use case for which the right Cloud PC solution is uniquely suited. Think of Workspot Cloud PCs as your offensive strategy for keeping your business running after an attack. In this situation, we did not have an existing relationship with the organization suffering the attack. One of their employees had experience with Workspot at a previous company, and he placed a call on a Sunday to the Workspot Customer Support Team. Our team of experts jumped in immediately to help and were able to deploy a large number of Cloud PCs and workstations to key individuals whose productivity was critical to meeting project deadlines. In less than 48 hours, these individuals were fully productive, accessing their cloud-based applications via their Workspot Cloud PCs in Microsoft Azure.Even though this customer had an “access” gap, and we were able to get their users to full productivity within two days, there are three key reasons companies should be more prepared for the recovery phase:
- Capacity: Each public cloud has capacity limitations in different parts of the world. It is unlikely that a large amount of capacity will be available on-demand in the public cloud region the customer choose to use.
- Isolation: The Cloud PCs should be staged and ready to go into an environment that is isolated from the infected network. This means setting up an alternative to Active Directory.
- Data & Applications: Once the Cloud PCs are up and running in an isolated environment, they need access to data and applications. We recommend that the customer stages and periodically tests integration between the isolated environment and the backup data and application sites.
ABOUT WORKSPOT
Latest resources.
We're here to help! Access these valuable resources to help guide your journey to cloud desktops.

WealthSimple partners with Workspot to migrate virtual desktops to GCP
WealthSimple reduces end user support tickets and improves end user satisfaction by moving virtual desktops from their data centers to using Workspot and Google Cloud.
Video: Siemens NX Corvette Running on a Workspot Cloud Workstation
In this video we’re running the latest Siemens NX software completely in the cloud, on a GPU-accelerated Workspot cloud workstation running on Azure.

A Suggested VDI Roadmap to Navigate Past Turbulent Times
Dan O’Farrell, Workspot VP of Product Marketing The modern data center was created by VMware, with most organizations today... Read more
What Do You Want To Do Today?

SAP Applications Application Virtualization Call Center Contractor Software Developer Remote Employee Mergers & Acquisitions 3D CAD Designer
Technologies?
Web Applications Windows & Linux Applications Windows & Linux Desktops Shared Hosted Desktops Non-persistent Desktops Persistent Desktops GPU Workstations

Nutanix AHV VMware vSphere Microsoft Hyper-V Azure GCP AWS
A 15-minute demo is all it takes! Let's discuss your growth strategy and how our Unified Digital Workplace Platform will help drive it.
SCHEDULE DEMO
- Artificial Intelligence
- Generative AI
- Business Operations
- IT Leadership
- Application Security
- Business Continuity
- Cloud Security
- Critical Infrastructure
- Identity and Access Management
- Network Security
- Physical Security
- Risk Management
- Security Infrastructure
- Vulnerabilities
- Software Development
- Enterprise Buyer’s Guides
- United States
- United Kingdom
- Newsletters
- Foundry Careers
- Terms of Service
- Privacy Policy
- Cookie Policy
- Member Preferences
- About AdChoices
- E-commerce Links
- Your California Privacy Rights
Our Network
- Computerworld
- Network World

11 infamous malware attacks: The first and the worst
Whether by dumb luck or ruthless skill, these malware attacks left their mark on the internet..

Viruses and other malware spreading for sinister or baffling reasons has been a staple of cyberpunk novels and real-life news stories alike for decades. And in truth, there have been computer viruses on the internet since before it was the internet. This article will take a look at some of the most important milestones in the evolution of malware: These entries each represent a novel idea, a lucky break that revealed a gaping security hole, or an attack that turned to be particularly damaging—and sometimes all three.
- Creeper virus (1971)
- Brain virus (1986)
- Morris worm (1988)
- ILOVEYOU worm (2000)
- Mydoom worm (2004)
- Zeus trojan (2007)
- CryptoLocker ransomware (2013)
- Emotet trojan (2014)
- Mirai botnet (2016)
- Petya ransomware/NotPetya wiper (2016/7)
- Clop ransomware (2019-Present)
1. Creeper virus (1971)
Computer pioneer John von Neumann’s posthumous work Theory of Self-Reproducing Automata , which posited the idea of computer code that could reproduce and spread itself, was published in 1966. Five years later, the first known computer virus, called Creeper , was a written by Bob Thomas. Written in PDP-10 assembly language, Creeper could reproduce itself and move from computer to computer across the nascent ARPANET.
Creeper did no harm to the systems it infected—Thomas developed it as a proof of concept, and its only effect was that it caused connected teletype machines to print a message that said “I’M THE CREEPER: CATCH ME IF YOU CAN.” We’re mentioning it here despite its benign nature because it was the first, and set the template for everything that followed. Shortly after Creeper’s release, Ray Tomlinson, best known for implementing the first email program, wrote a rival program called Reaper that spread from computer to computer eliminating Creeper’s code.
2. Brain virus (1986)
Creeper was designed to leap across computer networks, but for most of the 1970s and ’80s that infection vector was in limited simply because most computers operated in isolation. What malware did spread from computer to computer did so via floppy disks. The earliest example is Elk Cloner , which was created by a 15-year-old as a prank and infected Apple II computers. But probably the most important of this generation of viruses was one that came to be known as Brain, and started spreading worldwide in 1986.
Brain was developed by computer programmers (and brothers) Amjad and Basit Farooq Alvi, who lived in Pakistan and had a business selling medical software. Because their programs were often pirated, they created a virus that could infect the boot sector of pirated disks. It was mostly harmless but included contact information for them and an offer to “disinfect” the software.
Whether they could actually “fix” the problem isn’t clear, but as they explained 25 years later, they soon started receiving phone calls from all over the world , and were shocked by how quickly and how far Brain had spread (and how mad the people who had illegally copied their software were at them, for some reason). Today Brain is widely regarded as the first IBM PC virus, so we’re including it on our list despite its benign nature, and the brothers still have the same address and phone number that they sent out 25 years ago.
3. Morris worm (1988)
1988 saw the advent of a piece of malware called Morris, which could claim a number of firsts. It was the first widespread computer worm , which meant it could reproduce itself without needing another program to piggyback on. It targeted multiple vulnerabilities to help it spread faster and further. While not designed to do harm, it was probably the first malware to do real substantive financial damage, more than earning its place on this list. It spread incredibly swiftly—within 24 hours of its release, it had infected 10 percent of all internet-connected computers —and created multiple copies of itself on each machine, causing many of them to grind to a halt. Estimates of the costs of the attack ranged into the millions.
The worm is named after its creator Robert Morris , who was a Cornell grad student at the time and meant it as a proof-of-concept and demonstration of widespread security flaws. Morris didn’t anticipate that it would spread so quickly or that its ability to infect individual computers multiple times would cause so much trouble, and he tried to help undo the damage, but it was too late. He ended up the unfortunate subject of another first: The first person convicted under the 1986 Computer Fraud and Abuse Act.
4. ILOVEYOU worm (2000)
Unlike the previous malware creators on this list, Onel de Guzman, who was 24 in 2000 and living in the Philippines, crafted his creation with straightforward criminal intent: he couldn’t afford dialup service, so he built a worm that would steal other people’s passwords so he could piggyback off of their accounts. But the malware so cleverly took advantage of a number of flaws in Windows 95—especially the fact that Windows automatically hid the file extensions of email attachments so people didn’t realize they were launching executable files—that it spread like wildfire, and soon millions of infected computers were sending out copies of the worm and beaming passwords back to a Filipino email address . It also erased numerous files on target computers, causing millions of dollars in damage and briefly shutting down the U.K. Parliament’s computer system.
de Guzman was never charged with a crime, because nothing he did was illegal in the Philippines at the time, but he expressed regret in an interview 20 years later , saying he never intended the malware to spread as far as it did. He also ended up being something of a pioneer in social engineering : the worm got its name because it spread with emails with “ILOVEYOU” in the subject line . “I figured out that many people want a boyfriend, they want each other, they want love, so I called it that,” de Guzman said.
5. Mydoom worm (2004)
Mydoom may be almost 20 year old as of this writing, but as of today still holds a number of records. The Mydoom worm infected computers via email , then took control of the victim computer to email out more copies of itself, and did it so efficiently that at its height it accounted for a quarter of all emails sent worldwide, a feat that’s never been surpassed. The infection ended up doing more than $35 billion in damages, which, adjusted for inflation, has also never been topped.
The creator and ultimate purpose of Mydoom remain mysteries today. In addition to mailing out copies of the worm, infected computers were also used as a botnet to launch DDoS attacks on the SCO Group (a company that aggressively tried to claim intellectual property rights over Linux ) and Microsoft , which led many to suspect some rogue member of the open source community . But nothing specific has ever been proven.
6. Zeus trojan (2007)
Zeus was first spotted in 2007, at the tail end of the Web 1.0 era, but it showed the way for the future of what malware could be. A Trojan that infects via phishing and drive-by downloads from infected websites, isn’t just one kind of attacker; instead, it acts as a vehicle for all sorts of malicious payloads. Its source code and operating manual leaked in 2011, which helped both security researchers and criminals who wanted to exploit its capabilities .
You’ll usually hear Zeus referred to as a “banking Trojan,” since that’s where its variants focus much of their energy. A 2014 variant, for instance, manages to interpose itself between a user and their banking website , intercepting passwords, keystrokes, and more. But Zeus goes beyond banks, with another variation slurping up Salesforce.com info .
7. CryptoLocker ransomware (2013)
Zeus could also be used to create botnets of controlled computers held in reserve for some later sinister purpose. The controllers of one such botnet, called Gameover Zeus, infected their bots with CryptoLocker, one of the earliest prominent versions of what became known as ransomware . Ransomware encrypts many of the files on the victim’s machine and demands a payment in cryptocurrency in order to restore access.
CryptoLocker became famous for its rapid spread and its powerful asymmetric encryption that was (at the time) uniquely difficult to break. It also became famous due to something unusual in the malware world: a happy ending. In 2014, the U.S. DoJ and peer agencies overseas managed to take control of the Gameover Zeus botnet , and restore the files of CryptoLocker victims free of charge. Unfortunately, CryptoLocker spread via good old-fashioned phishing as well, and variants are still around.
8. Emotet trojan (2014)
Emotet is another piece of malware whose functionality has shifted and changed of the years that it has remained active. In fact, Emotet is a prime example of what’s known as polymorphic malware , with its code changing slightly every time it’s accessed, the better to avoid recognition by endpoint security programs . Emotet is a Trojan that, like others on this list, primarily spreads via phishing (repeat after us: do not open unknown email attachments ).
Emotet first appeared in 2014, but like Zeus, is now a modular program most often used to deliver other forms of malware, with Trickster and Ryuk being two prominent examples. Emotet is so good at what it does that Arne Schoenbohm, head of the German Federal Office for Information Security, calls it the “king of malware.”
9. Mirai botnet (2016)
All the viruses and other malware we’ve been discussing so far have afflicted what we think of as “computers”—the PCs and laptops that we use for work and play. But in the 21st century, there are millions of devices with more computing power than anything that Creeper could have infected. These internet of things (IoT) devices are omnipresent, ignored, and often go unpatched for years.
The Mirai botnet was actually similar to some of the early malware we discussed because it exploited a previously unknown vulnerability and wreaked far more havoc than its creator intended. In this case, the malware found and took over IoT gadgets (mostly CCTV cameras) that hadn’t had their default passwords changed. Paras Jha, the college student who created the Mirai malware, intended to use the botnets he created for DoS attacks that would help settle scores in the obscure world of Minecraft server hosting, but instead he unleashed an attack that focused on a major DNS provider and cut off much of the U.S. east coast from the internet for the better part of a day.
10. Petya ransomware/NotPetya wiper (2016/7)
The ransomware Trojan dubbed Petra started afflicting computers in 2016. Though it had a clever mechanism for locking down its victims’ data—it encrypts the master file table, which the OS uses to find files—it spread via conventional phishing scams and wasn’t considered particularly virulent.
It would probably be forgotten today if not for what happened the following year. A new self-reproducing worm variant emerged that used the NSA’s leaked EternalBlue and EternalRomance exploits to spread from computer to computer. Originally distributed via a backdoor in a popular Ukrainian accounting software package, the new version— dubbed NotPetya —quickly wreaked havoc across Europe. The worst part? Though NotPetya still looked like ransomware, it was a wiper designed wholly to ruin computers, as the address displayed where users could send their ransom was randomly generated and did no good. Researchers believe that Russian intelligence repurposed the more ordinary Petya malware to use as a cyberweapon against Ukraine—and so, in addition to the massive damage it caused, NotPetya earns its place on this list by illustrating the symbiotic relationship between state sponsored and criminal hackers.
11. Clop ransomware (2019-Present)
Clop (sometimes written Cl0p) is another ransomware variant that emerged on the scene in 2019 and has grown increasingly prevalent since, to the extent that it was dubbed one of the top malware threats of 2022 . In addition to preventing victims from accessing their data, Clop allows the attacker to exfiltrate that data as well. McAfee has a breakdown of the technical details , including a review of ways it can bypass security software.
What makes Clop so interesting and dangerous, however, is not how it’s deployed, but by whom. It’s at the forefront of a trend called Ransomware-as-a-Service , in which a professionalized group of hackers does all the work for whoever will pay them enough (or share in a percentage of the ransomware riches they extract from victims). The earlier entries in this list are from a day when the internet was for hobbyists and lone wolves; today, it seems even cybercrime is largely the province of governments and the professionals.
More on malware:
- New campaign uses malware ‘cluster bomb’ to effect maximum impact
- CISA opens its malware analysis and threat hunting tool for public use
- Surge in “hunter-killer” malware poses significant challenge to security teams
Related content
Equiniti settles sec charges stemming from a pair of cyber intrusions, iranian cyberespionage group deploys new blacksmith malware in sophisticated spear-phishing campaign, microsoft outlook security hole lets attackers in without opening a tainted message, north korean group infiltrated 100-plus companies with imposter it pros: crowdstrike report, from our editors straight to your inbox.

Josh Fruhlinger is a writer and editor who lives in Los Angeles.
More from this author
Was ist social engineering, what is the cia triad a principled framework for defining infosec policies, sbom erklärt: was ist eine software bill of materials, crisc certification: exam, requirements, training, potential salary, tabletop exercise scenarios: 10 tips, 6 examples, what is swatting criminal harassment falsely involving armed police, ccsp certification: exam, cost, requirements, training, salary, certified ethical hacker (ceh): certification cost, training, and value, most popular authors.

- Gyana Swain
Show me more
Wordpress users not on windows urged to update due to critical litespeed cache flaw.

Chinese APT group Velvet Ant deployed custom backdoor on Cisco Nexus switches

GitHub fixes critical Enterprise Server bug granting admin privileges

CSO Executive Sessions: Guardians of the Games - How to keep the Olympics and other major events cyber safe

CSO Executive Session India with Dr Susil Kumar Meher, Head Health IT, AIIMS (New Delhi)

CSO Executive Session India with Charanjit Bhatia, Head of Cybersecurity, COE, Bata Brands

Cybersecurity Insights for Tech Leaders: Addressing Dynamic Threats and AI Risks with Resilience

Case study: Data protection trends and ransomware defense in the real world

Presented by
Cristophe Bertrand | Colm Keegan | Saurabh Sensharma | Rob Petrone
About this talk
More from this channel.
TechRepublic
Account information.

Share with Your Friends
Most Ransomware Attacks Occur When Security Staff Are Asleep, Study Finds
Your email has been sent

Threat actors are taking advantage of when security professionals are off-duty to stage their ransomware attacks, new research has found. The ThreatDown 2024 State of Ransomware report from Malwarebytes has revealed most incidents in the last year occurred between 1 a.m. and 5 a.m.
The report’s authors used data from the ThreatDown Managed Detection and Response team to conduct their research. It found that global ransomware attacks increased by 33% in the last year, with the top-targeted countries seeing the largest rises. The U.K. experienced a 67% hike in known attacks, and the U.S. saw a 63% increase.
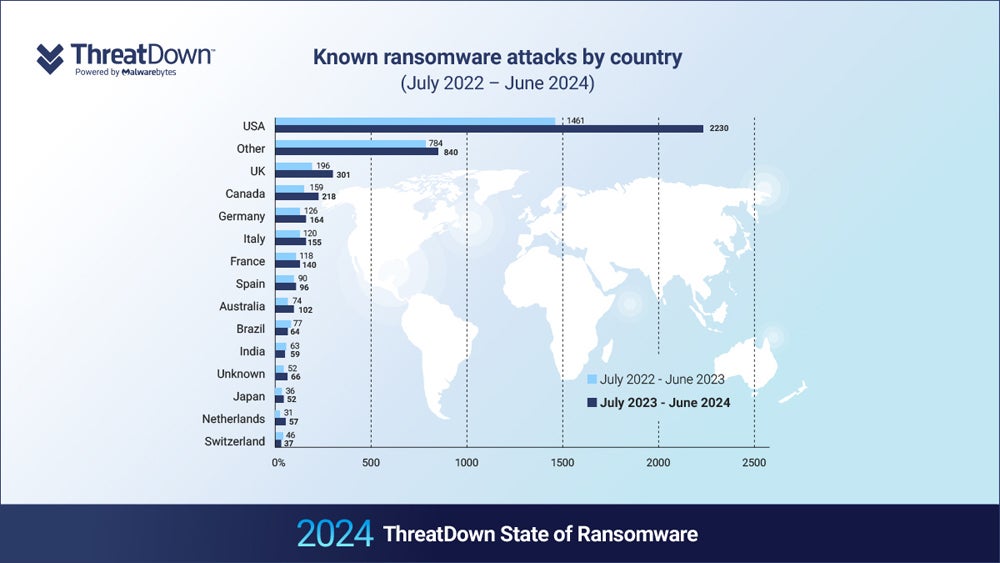
“The question I ask organizations is ‘do you have someone prepared to stop an attack at 2 a.m. on a Sunday with your existing technology stack and staff resources?’” Chris Kissel, research vice president at IDC’s Security & Trust Products group, said in a press release .
“They may have a tool to pick up the alert on Monday morning, but by then it will be too late. Threat actors are moving fast to compromise networks, download data and deploy ransomware.”
Marcin Kleczynski, founder and CEO of Malwarebytes, added, “Ransomware gangs have time and motivation on their side. They constantly evolve to respond to the latest technologies chasing at their tails.
“We’ve seen this very distinctly over the past year as widespread adoption of technologies like EDR has helped identify attackers before they launch malware, pushing ransomware gangs to work more quickly and put more effort into hiding themselves. Organizations and MSPs need additional support and continuous coverage to outmaneuver today’s criminals.”
Smaller ransomware groups are becoming more prolific
The proportion of ransomware attacks being conducted by small gangs outside the top 15 most active groups rose from 25% to 31% last year. This indicates that staging ransomware attacks is becoming more accessible to less experienced attackers.
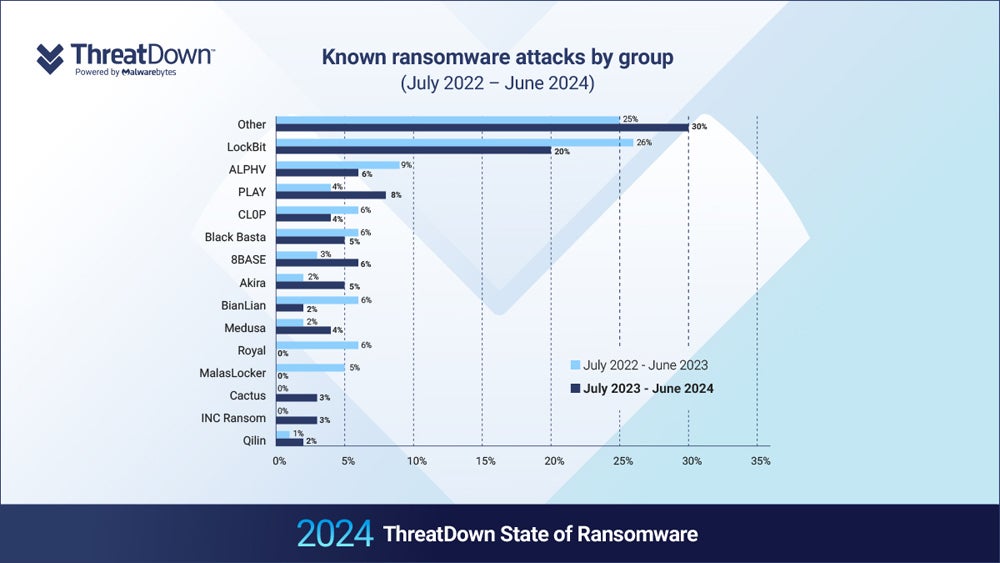
In January 2024, the U.K.’s National Cyber Security Centre warned that the threat of ransomware was expected to rise even further due to the new availability of AI technologies decreasing the barrier to entry. For example, Google Cloud analysts said that generative AI may be used in call centres running ransomware negotiations .
The Malwarebytes report also found that the proportion of ransomware attacks that dominant ransomware-as-a-service group LockBit claimed responsibility for decreased from 26% to 20% over the past year, despite carrying out more individual attacks.
SEE: 94% of Ransomware Victims Have Their Backups Targeted
LockBit’s dominance may have taken a hit after the U.K. National Crime Agency’s Cyber Division, the FBI, and international partners successfully cut off access to its website , which had been used as a large ransomware-as-a-service storefront , in February.
However, a few days later, the group resumed operations at a different Dark Web address and continues to claim responsibility for global ransomware attacks.
ALPHV, the second-most prolific ransomware group, also created a vacancy after a sloppily executed cyber attack against Change Healthcare in February. The group did not pay an affiliate their percentage of the $22 million ransom, so the affiliate exposed them, prompting ALPHV to fake a law enforcement takeover and cease operations.
Furthermore, a recent report from WithSecure found that, of the 67 ransomware groups it tracked in 2023, 31 are no longer operational as of Q2 2024. This further suggests that law enforcement takedowns, like those of ALPHV and Dispossessor , are proving effective against the more-established gangs while simultaneously opening up new opportunities for smaller groups.
The Malwarebytes report authors wrote, “With ALPHV gone and LockBit’s future uncertain, other gangs are certain to be trying to attract their affiliates and supplant them as the dominant forces in ransomware.”
SEE: Report: Impacts of AI on Cyber Security Landscape
Top targeted industries for ransomware in the U.S. and worldwide in 2024
Ransomware is a growing threat all over the world, with the number of enterprises attacked increasing by 27% in 2023 and payouts exceeding $1 billion (£790 million) for the first time. Globally, ransomware damage costs are predicted to exceed $265 billion by 2031 .
According to the Malwarebytes report, the services industry is the worst affected, accounting for almost a quarter of global ransomware attacks. Compromising critical national infrastructure can lead to widespread disruption, making it a prime target for ransomware.
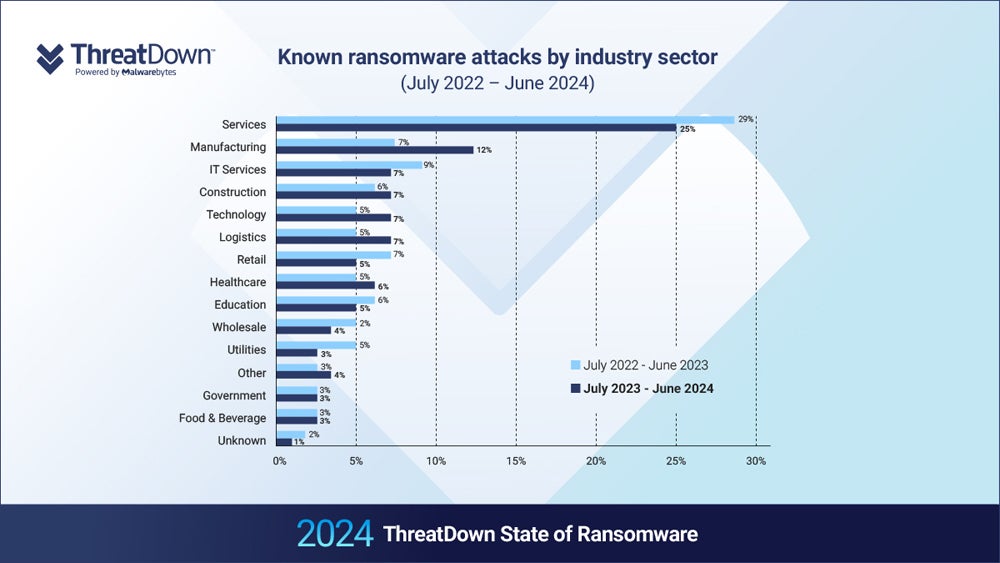
In May, the U.K.’s National Cyber Security Centre and other international cyber authorities, including the FBI, warned about cyber attacks targeting providers of operational technology . The advisory came in light of “continued malicious cyber activity” against water, energy, and food and agriculture businesses between 2022 and April 2024.
SEE: How hackers infiltrate critical infrastructure
The report also found that, while the U.S. accounts for nearly half of all ransomware attacks worldwide, it takes on 60% of global attacks on the education sector and 71% of them on healthcare.
This could be related to its highly privatised, and therefore wealthy, healthcare system and higher education institutions, as well as strict regulations such as HIPAA and FERPA that pressure organisations into paying the ransom to avoid fines.
The global manufacturing sector saw a 71% year-on-year increase in ransomware attacks, corresponding with increasing software spend in the sector.
“The most likely explanation therefore is that the number of available targets in the manufacturing sector has increased over the last two years, perhaps because of increasing digitization within the sector,” the authors wrote.
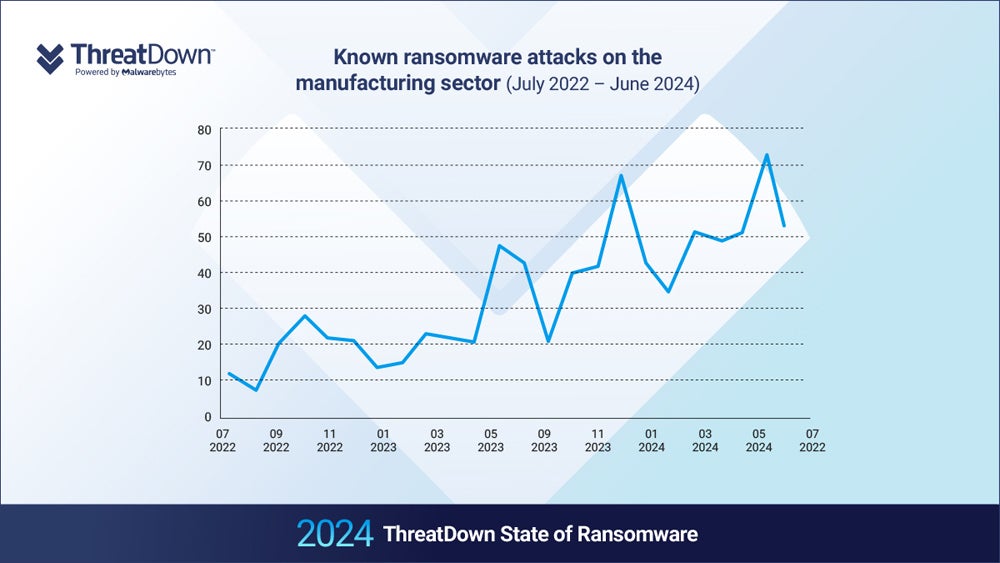
Tactical shifts of ransomware attackers in 2024
The ThreatDown MDR team noted a rise in living-off-the-land techniques being used by ransomware gangs, such as LockBit, Akira, and Medusa. Living-off-the-land is the use of legitimate, pre-installed tools and software within a target environment during an attack to help evade detection.
This can reduce the overall complexity of the malware by allowing the attacker to weaponize existing features that have already been security tested by the organisation, as well as making detection and prevention more challenging. The M-Trends 2024 report, from Google subsidiary Mandiant, also noted an increase in living-off-the-land attacks back in May.
The M-Trends report also found that the median dwell time — the amount of time attackers remain undetected within a target environment — of global organisations fell from 16 days in 2022 to 10 days in 2023.
Malwarebytes’ report indicates this faster attack timeline too, with ThreatDown Incident Response data showing how the entire ransomware attack chain, from initial access to data encryption, has reduced from weeks to hours.
Subscribe to the TechRepublic UK Newsletter
Catch up on the week’s essential technology news, must-read posts, and discussions that would be of interest to IT pros working in the UK and Europe. Delivered Wednesdays
- CrowdStrike 2024 Global Threat Report: 6 Key Takeaways
- Ransomware Cheat Sheet for 2024
- What Is ShrinkLocker? New Ransomware Targets Microsoft BitLocker Encryption Feature
- Ransomware’s Impact Could Include Heart Attacks, Strokes & PTSD
- Cybersecurity: More Must-Read Coverage

Create a TechRepublic Account
Get the web's best business technology news, tutorials, reviews, trends, and analysis—in your inbox. Let's start with the basics.
* - indicates required fields
Sign in to TechRepublic
Lost your password? Request a new password
Reset Password
Please enter your email adress. You will receive an email message with instructions on how to reset your password.
Check your email for a password reset link. If you didn't receive an email don't forgot to check your spam folder, otherwise contact support .
Welcome. Tell us a little bit about you.
This will help us provide you with customized content.
Want to receive more TechRepublic news?
You're all set.
Thanks for signing up! Keep an eye out for a confirmation email from our team. To ensure any newsletters you subscribed to hit your inbox, make sure to add [email protected] to your contacts list.

Main Targets of Ransomware Attacks & What They Look For
Zephin Livingston
eSecurity Planet content and product recommendations are editorially independent. We may make money when you click on links to our partners. Learn More .
Ransomware has become a potent tool for cybercriminals looking to exploit companies’ sensitive data for profit. Ransomware attacks have affected businesses across all sizes, locations, and industries, from banking and financial services to utilities to education.
When trying to keep your business safe from potential attacks, just as important as any kind of ransomware protection solution is to understand some of the factors and signs a ransomware hacker looks for when picking their next target. These factors can include data value, geographic locations, or a company’s use of remote workers.
Table of Contents
What Industries Are the Most Likely Ransomware Targets?
A unifying factor of most of the industries popular with ransomware attackers is their access to incredible amounts of sensitive data that an organization might want or even need to keep private, thus making them more likely to pay the ransom. Here are the most targeted industries.
Banking and Financial Services
The reasons for targeting banking and financial services companies are fairly clear. On top of having access to the capital needed to pay large ransom amounts, they often have access to extremely sensitive client information — and assets.
The world of banking and financial services is especially vulnerable to cyber attacks, and companies in this industry were the most likely to be targeted by ransomware attackers according to cybersecurity firm Trellix’s report for 2021.
Education shares similar vulnerabilities to local government institutions, often lacking the resources necessary to install anti-ransomware strategies. Their access to private information from faculty and students alike also makes them appealing targets.
In recent years, education has become a popular target for ransomware attackers. 2022 research conducted by antimalware vendor Emsisoft revealed that 88 ransomware incidents were reported by institutions in the US in 2021 . This led to the disruption of day-to-day operations for over 1,000 schools across the nation. In half of these incidents, personal data from both teachers and students was leaked online.
The total financial impact of these attacks can’t be known with any certainty, but, like any other industry hit by ransomware, the costs are likely severe. A Sophos report on the state of ransomware in education found that lower education institutions spent $1.58 million on ransomware in 2021 . Higher education institutions spent $1.42 million.
Want to Find Out More About How to Backup Your Data in the Event of a Ransomware Attack? Take a Look at Best Backup Solutions for Ransomware Protection
Energy and Utilities
Utilities are a popular target both for attackers looking to cause damage to infrastructure and for cybercriminals looking to get paid. In a 2022 report, cybersecurity firm CyberSaint reported that 43% of energy, oil, and utilities companies hit by ransomware ended up paying the ransom.
Because they provide such critical infrastructure, energy, and utility firms are more pressured than other ransomware targets to resolve the matter as quickly as possible, which sometimes means paying the ransom, Colonial Pipeline being the most notable example in recent memory.
Much like utilities, government organizations are a popular target for attackers looking to cause damage to the day-to-day infrastructure needed to keep society running. Government entities also often have some of the most sensitive data ransomware users can get their hands on.
Additionally, government organizations on the local level, such as city or county administrations, often lack the time and resources necessary to implement robust cybersecurity measures and tend to use outdated technology. In some cases, this can lead to them being especially easy targets for ransomware and result in the theft of incredibly personal data, such as land deeds and social security numbers, with less effort on the attackers’ part.
Manufacturing
Of popular ransomware targets, manufacturing companies are also the most likely to have their stolen data leaked online , with cyber criminals posting the data of 45 manufacturing companies in 2020 alone, according to Palo Alto Networks’ Unit 42. IBM reported that it resolved more cyber attacks for the manufacturing industry in 2021 than any other.
There is some good news for industrial companies, however. A 2021 survey of the industry by Sophos found that 36% of respondents were hit by ransomware attacks , and nearly half of those had their data encrypted. However, that same survey also found that only 19% of companies affected paid the ransom. This can potentially be chalked up to the fact that companies in the manufacturing industry are more prepared than other industries to restore data from backups, as decrypting stolen files rarely works .
Need to Know More About Ransomware Attackers and How They Operate? Read The Link Between Ransomware and Cryptocurrency
Key Signs and Vulnerabilities Ransomware Attackers Look For
Like any planned assault, ransomware attackers have certain vulnerabilities and factors they watch for when evaluating targets. Companies with the funds and resources to pay large sums, companies with access to sensitive data, and companies without the security infrastructure to resist a ransomware attack are favorite prey for a hacker. Understanding the key signs and vulnerabilities ransomware attackers look for is a vital part of protecting yourself against future attacks.
Valuable Data
The most important factor to ransomware attackers is the value of an organization’s data. If threat actors can steal or encrypt highly sensitive information, their victims may be more willing to pay a higher ransom. Even if they don’t receive a ransom, more sensitive data will fetch a higher price from Dark Web buyers.
You can see this preference in the types of organizations ransomware attacks have targeted recently. Professional services, financial services, and manufacturing were the most popular targets for ransomware in 2021, with energy, retail, and healthcare not far behind, according to IBM. These industries all deal with sensitive data, like financial information or personal identifiers, making them ideal targets.
Lack of Security Infrastructure
Unsurprisingly, ransomware attackers also prefer targets that lack sufficient cybersecurity measures. Small and medium-sized businesses account for half or more of ransomware attacks. These companies are less likely to have as extensive security as larger corporations, making them easier targets. There are also more businesses of that size than large corporations.
This trend may grow as ransomware-as-a-service (RaaS) expands its popularity. A growing number of ransomware groups have started franchising their tools, letting virtually anyone perform ransomware attacks for a fee. Growing RaaS use means more novice cybercriminals could engage in these attacks, and these newer attackers will likely prefer easier targets.
Companies in industries that are new to cybersecurity, like manufacturing or logistics, may fall victim to this trend. Ransomware attackers may prefer these organizations, as they’re less likely to have sufficient infrastructure to stop them.
A 2021 Twitter thread looked at the most common vulnerabilities exploited by ransomware groups – and found that vulnerabilities in 18 products were the most targeted (image below). As many of these are well-known vulnerabilities , the issue of patching remains a major concern.
Money for a Ransom
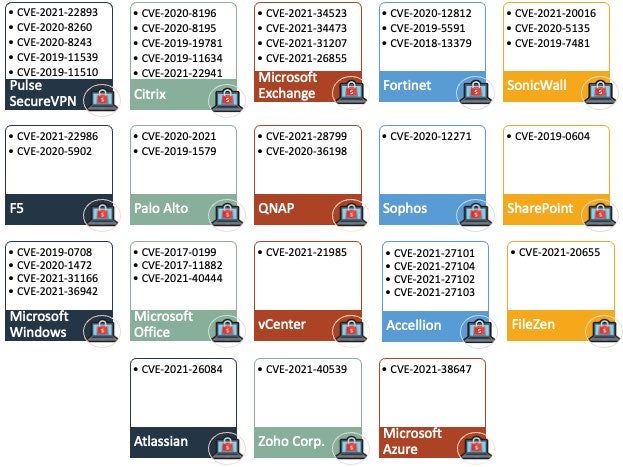
Cybercriminals also typically look for targets that can pay a larger ransom. That’s why the entertainment industry, which frequently deals in multi-million-dollar projects, experienced the second-highest number of cyberattacks in 2019, according to Verizon’s 2019 Data Breach and Investigation Report. A successful ransomware attack on wealthier companies may result in a more substantial payday for the attackers, drawing their attention.
At first, this figure may seem to counter the trend of attackers targeting small and medium businesses. However, even a medium-sized business can offer a significant amount of money to an individual or small group. It’s also important to note that while SMBs are the most common targets, that doesn’t necessarily mean new businesses are.
If your business brings in at least a few million dollars in annual revenue, you could be a target. Generally speaking, the more profitable your business is, the more enticing a target you are.
Need Some Good News About Ransomware? Learn About How One Company Survived a Ransomware Attack Without Paying the Ransom
Potential for Damage
Financial motivations are not the only driving force behind ransomware attacks. Some cybercriminals seek to cause as much destruction as possible, especially in state-sponsored cyberattacks. Whether it’s to make a statement or for a feeling of power, some ransomware attackers look for targets with the highest potential for damage.
Software supply chain companies are some of the most at-risk organizations. Take the SolarWinds attack , for example, which affected scores of customers by targeting a single system, or the Kaseya attack , which put thousands of the company’s clients at risk. If you have information belonging to multiple clients or connect to many other businesses’ software, you may be an ideal target.
Software-as-a-service (SaaS) vendors are thus in some ways ideal targets. If you offer IT services to multiple other companies, a ransomware attack on your business could cause widespread damage. That potential could attract attackers.
And critical infrastructure will remain an enticing attack for those seeking to do damage. Colonial Pipeline showed just how effective such attacks can be.
Remote Workers
Amid the COVID-19 pandemic, many businesses embraced remote work. Data shows that these same companies may be at increased risk of a ransomware attack. The software you use to collaborate with remote employees may have vulnerabilities that ransomware attackers seek to take advantage of. And remote employees tend to be less protected by ransomware essentials such as immutable data backups.
Remote desktop protocol (RDP), which remote workers may use more heavily than others, is a favorite of ransomware groups. Cybercriminals leveraged RDP vulnerabilities in 47% of all ransomware attacks in one study, more than any other category.
Virtual private networks (VPNs) are another common target. While these tools can protect you by encrypting your internet traffic, unpatched vulnerabilities or outdated versions can turn them into entry points for cybercriminals. If your business uses these or similar remote collaboration tools, you could be at risk.
Zero trust is one way to secure home-based and remote workers. And enterprise firewall vendors Fortinet and Palo Alto Networks unveiled secure routers aimed at home and small office workers in 2021.
Ransomware Isn’t the Only Type of Malware You Need to Watch Out For. Read What is Malware? Definition, Purpose & Common Protections
Geographic Locations
Interestingly, recent research shows that ransomware attacks are often concentrated in specific geographic areas. In active Dark Web ransomware threads in July 2021, KELA researchers found that more than 40% of threat actors mentioned the U.S. as their desired location of victims. Canada and Australia followed, both around 37%.
This geographic concentration is likely due to the concentration of wealthier or more prominent companies. Political motivations could also play a role. Specific locations like states or cities may follow similar lines, with the largest and wealthiest areas seeing more attacks.
If your company is based in these areas, you may be at higher risk of ransomware than others. This factor is likely less influential than data value and security infrastructure, but it’s worth noting regardless.
How to Prevent Ransomware
Cybercriminals don’t act randomly. Ransomware attacks follow specific motivations, and when you understand these drivers, you can know what level of risk you face.
Regardless of how at-risk you are, protecting against ransomware is critical. However, if you fall into any of these categories, you may want to consider more extensive anti-ransomware measures.
- Data Backups: One of the best protections against ransomware is maintaining immutable backups of your data whenever possible. Decryption isn’t as consistent as it needs to be, but if you have any way to recover and restore your stolen data, you’ve removed a lot of the power ransomware attackers can have over you. However, this isn’t foolproof, as attackers might know of those backups and seek to damage them as well. Also, depending on how long it takes to deploy those backups, it might not be a feasible solution to the havoc ransomware can wreak on an organization’s day-to-day operations.
- Stop Suspicious Network Traffic: Security solutions like Intrusion Detection and Prevention (IDPS) or next-generation firewalls (NGFW) can help block potentially- malicious traffic from your network . Email gateways also have the chance of removing one of the most common vectors of ransomware infection: phishing , spoofing , and the like. EDR and SIEM systems are also core security defenses.
- Think Creatively: Deception technology could give you an early warning of ransomware or another cyberattack. Encrypting data — even in use — can take away the threat of having sensitive data leaked to the public.
- Stay Alert: Ultimately, however, these tools are only as effective as the individuals using them. As such, personal vigilance remains a key factor in preventing any malware attack. Whether it’s not opening suspicious email attachments or keeping your passwords secure, your good cybersecurity hygiene will be an effective deterrent against ransomware. This is why one of the simplest defenses against ransomware is to administer solid employee awareness training .
Need help protecting your organization from ransomware? Rapid7 offers managed detection and response (MDR) and extended detection and response (XDR) to help keep your endpoints free from ransomware. Chat with an MDR expert today.
Bottom Line
Ransomware is one of the most potent threats facing businesses today. Fortunately, knowing what ransomware hackers look for when picking their targets can help companies better prepare for an attack.
Factors such as geographic location, access to sensitive data, or lacking security infrastructure can all increase the likelihood of ransomware attacks, as well as an organization’s presence in certain industries like banking, healthcare, or manufacturing.
While there are ways to defend yourself against ransomware, none of them are foolproof, and even solid defenses are under constant threat of circumvention by enterprising hackers. Still, keeping in mind what ransomware attackers might be looking for in their targets can help you stay one step ahead of ransomware and keep your and your customers’ data safe.
Looking to Learn More About How to Defend Yourself from Ransomware? Check Out Ransomware Prevention: How to Protect Against Ransomware
NOTE: This article was originally written by Devin Partida on September 22, 2021. It was updated by Zephin Livingston on December 1, 2022.
Get the Free Cybersecurity Newsletter
Strengthen your organization’s IT security defenses by keeping up to date on the latest cybersecurity news, solutions, and best practices. Delivered every Monday, Tuesday and Thursday
Previous article
Next article

Subscribe to Cybersecurity Insider
Strengthen your organization’s IT security defenses by keeping abreast of the latest cybersecurity news, solutions, and best practices.
IT Security Resources
Cookie theft: what is it & how to prevent it.

How to Use LastPass: Complete Guide for Beginners

How to Use BitDefender VPN on Any Device: 2024 Tutorial

How to Get a VPN on Any Device (+ Installation Tips)

Top Cybersecurity Companies
Get the free newsletter.
Subscribe to Cybersecurity Insider for top news, trends & analysis
Related Articles

Vulnerability Recap 8/20/24 – Microsoft Has the Spotlight This Week

Vulnerability Recap 8/13/24 – Old Vulnerabilities Unexpectedly Emerge
Website Search
Call Sign / Name Search
Register Account
- Licensing, Education & Training
- Regulatory & Advocacy
Public Service
Get involved.
- News & Features
ARRL IT Security Incident - Report to Members
Sometime in early May 2024, ARRL’s systems network was compromised by threat actors (TAs) using information they had purchased on the dark web. The TAs accessed headquarters on-site systems and most cloud-based systems. They used a wide variety of payloads affecting everything from desktops and laptops to Windows-based and Linux-based servers. Despite the wide variety of target configurations, the TAs seemed to have a payload that would host and execute encryption or deletion of network-based IT assets, as well as launch demands for a ransom payment, for every system.
This serious incident was an act of organized crime. The highly coordinated and executed attack took place during the early morning hours of May 15. That morning, as staff arrived, it was immediately apparent that ARRL had become the victim of an extensive and sophisticated ransomware attack. The FBI categorized the attack as “unique” as they had not seen this level of sophistication among the many other attacks, they have experience with. Within 3 hours a crisis management team had been constructed of ARRL management, an outside vendor with extensive resources and experience in the ransomware recovery space, attorneys experienced with managing the legal aspects of the attack including interfacing with the authorities, and our insurance carrier. The authorities were contacted immediately as was the ARRL President.
The ransom demands by the TAs, in exchange for access to their decryption tools, were exorbitant. It was clear they didn’t know, and didn’t care, that they had attacked a small 501(c)(3) organization with limited resources. Their ransom demands were dramatically weakened by the fact that they did not have access to any compromising data. It was also clear that they believed ARRL had extensive insurance coverage that would cover a multi-million-dollar ransom payment. After days of tense negotiation and brinkmanship, ARRL agreed to pay a $1 million ransom. That payment, along with the cost of restoration, has been largely covered by our insurance policy.
From the start of the incident, the ARRL board met weekly using a continuing special board meeting for full progress reports and to offer assistance. In the first few meetings there were significant details to cover, and the board was thoughtfully engaged, asked important questions, and was fully supportive of the team at HQ to keep the restoration efforts moving. Member updates were posted to a single page on the website and were posted across the internet in many forums and groups. ARRL worked closely with professionals deeply experienced in ransomware matters on every post. It is important to understand that the TAs had ARRL under a magnifying glass while we were negotiating. Based on the expert advice we were being given, we could not publicly communicate anything informative, useful, or potentially antagonistic to the TAs during this time frame.
Today, most systems have been restored or are waiting for interfaces to come back online to interconnect them. While we have been in restoration mode, we have also been working to simplify the infrastructure to the extent possible. We anticipate that it may take another month or two to complete restoration under the new infrastructure guidelines and new standards.
Most ARRL member benefits remained operational during the attack. One that wasn’t was Logbook of The World (LoTW), which is one of our most popular member benefits. LoTW data was not impacted by the attack and once the environment was ready to again permit public access to ARRL network-based servers, we returned LoTW into service. The fact that LoTW took less than 4 days to get through a backlog that at times exceeded over 60,000 logs was outstanding.
The board at the ARRL Second Board Meeting in July voted to approve a new committee, the Information Technology Advisory Committee. This will be comprised of ARRL staff, board members with demonstrated experience in IT, and additional members from the IT industry who are currently employed as subject matter experts in a few areas. They will help analyze and advise on future steps to take with ARRL IT within the financial means available to the organization.
We thank you for your patience as we navigated our way through this. The emails of moral support and offers of IT expertise were well received by the team. Although we are not entirely out of the woods yet and are still working to restore minor servers that serve internal needs (such as various email services like bulk mail and some internal reflectors), we are happy with the progress that has been made and for the incredible dedication of staff and consultants who continue to work together to bring this incident to a successful conclusion.
This information was shared with ARRL Members via email on August 21, 2024.
Photo Gallery

Back to Top
Having Trouble?
News & Features >> News
- ARRL Audio News
- ARRL Periodicals Archive Search
- On the Air Magazine
- ARRL Letter
- So Now What?
- ARRL Magazines
EXPLORE ARRL
DXCC Program , W100AW & W1AW QSLs via Bureau , Centennial QSO Party , Operating Specialties , International Grid Chase 2018 , Hiram Percy Maxim 150th Birthday Celebration , Cycle 25 , Transatlantic , Special Event Stations , Operating Resources , Volunteers On the Air , QSL Service , NPOTA , Contests , Awards , Logbook of The World , Amateur Code , Amateur Radio Direction Finding , W1AW
Licensing, Education & Training
Courses & Training , What is Ham Radio , FCC License Info and Forms , License Certificates , Youth Licensing Grant Program , Volunteer Examiners , Edu Dept Home , Learning Center Help , Getting Licensed , Newly licensed? Learn More , Volunteer Instructors/Mentors , Amateur Radio in the Classroom , Learning Programs , Gordon West
Member Directory , myARRL , Blind Membership , Join ARRL/Renew Membership , member feedback , Dues Increase FAQ , Techquestion , Please Confirm Your Information , Member Discounts , Member Bulletin , QST Reissue , Membership Certificate , Member Support , Connecticut Member Social , Silent Key Submission Guidelines , Login Instructions , Dues Survey , Gift Membership , New Join , 3-Year Special Offer , 2024 Dues Rates , ARRL Groups , Student
Regulatory & Advocacy
State and Local , Volunteer Consulting Engineer Program , Volunteer Counsel Program , CCR Study Information , International , Technical Relations Office , Federal , Volunteer Monitor Resources , Federal RFI Preemption , Antenna Regulation and Zoning , Volunteer Monitor Program
NTS Manual , Public Service Resources , Volunteer Form for Deployment Consideration , 2018 Hurricanes , Hurricane Maria - 2017 , Hurricane Irma - 2017 , Hurricane Harvey Response , Ham Aid , Public Service Honor Roll , 2019 Hurricanes , 2020 Hurricanes , 2021 Hurricanes , Puerto Rico - Caribbean Recovery 2017 , Kentucky ARES Summit and Survey , Hurricanes , Served Agencies and Partners , SKYWARN Recognition Day , NTS , 2024 Hurricanes , ARES
ARRL References , ARRL Lab , Tech Portal , Radio Technology Topics , Technical Information Service , ARRL Clean Signal Initiative , Radio Frequency Interference (RFI)
Clubs , Volunteer Opportunities , Youth , Recruiting & Outreach , The ARRL Foundation , Donate to ARRL , Collegiate Amateur Radio , Hamfests and Conventions Calendar
Publications & Online Store
ARRL Publication Dealers , ARRL Store , List all Products , Return Policy , Shipping and Tax , Customer Service/Support , Handbook , Product Notes
Site Index , Centennial , ARRL Strategic Plan , Advertising and Other Business Opportunities , ARRL on the Purpose of Amateur Radio , Library , Ideas , Copyright , Media and Public Relations , Visit Us , Organization Structure , Privacy Policy , General Information , ARRL Social Media , Contact ARRL , Employment Opportunities

ARRL The National Association for Amateur Radio ® 225 Main Street Newington, CT, 06111-1400 USA Tel: 1-860-594-0200 | Fax: 1-860-594-0259 Toll-free: 1-888-277-5289 hq@arrl.org
- Join / Renew Your Membership
- Advertise With Us
- Contact ARRL
- Terms of Use / Privacy Policy
- E-mail to a Friend
- Sign Up for Our Newsletter
