Cyber Security Essay for Students and Children
Cyber security essay.
Cybersecurity means protecting data, networks, programs and other information from unauthorized or unattended access, destruction or change. In today’s world, cybersecurity is very important because of some security threats and cyber-attacks. For data protection, many companies develop software. This software protects the data. Cybersecurity is important because not only it helps to secure information but also our system from virus attack. After the U.S.A. and China, India has the highest number of internet users.


Cyber Threats
It can be further classified into 2 types. Cybercrime – against individuals, corporates, etc.and Cyberwarfare – against a state.
Cyber Crime
Use of cyberspace, i.e. computer, internet, cellphone, other technical devices, etc., to commit a crime by an individual or organized group is called cyber-crime. Cyber attackers use numerous software and codes in cyberspace to commit cybercrime. They exploit the weaknesses in the software and hardware design through the use of malware. Hacking is a common way of piercing the defenses of protected computer systems and interfering with their functioning. Identity theft is also common.
Cybercrimes may occur directly i.e, targeting the computers directly by spreading computer viruses. Other forms include DoS attack. It is an attempt to make a machine or network resource unavailable to its intended users. It suspends services of a host connected to the internet which may be temporary or permanent.
Malware is a software used to disrupt computer operation, gather sensitive information, or gain access to private computer systems. It usually appears in the form of code, scripts, active content, and other software. ‘Malware’ refers to a variety of forms of hostile or intrusive software, for example, Trojan Horses, rootkits, worms, adware, etc.
Another way of committing cybercrime is independent of the Computer Network or Device. It includes Economic frauds. It is done to destabilize the economy of a country, attack on banking security and transaction system, extract money through fraud, acquisition of credit/debit card data, financial theft, etc.
Hinder the operations of a website or service through data alteration, data destruction. Others include using obscene content to humiliate girls and harm their reputation, Spreading pornography, threatening e-mail, assuming a fake identity, virtual impersonation. Nowadays misuse of social media in creating intolerance, instigating communal violence and inciting riots is happening a lot.
Get the huge list of more than 500 Essay Topics and Ideas
Cyber Warfare
Snowden revelations have shown that Cyberspace could become the theatre of warfare in the 21st century. Future wars will not be like traditional wars which are fought on land, water or air. when any state initiates the use of internet-based invisible force as an instrument of state policy to fight against another nation, it is called cyberwar’.
It includes hacking of vital information, important webpages, strategic controls, and intelligence. In December 2014 the cyberattack a six-month-long cyberattack on the German parliament for which the Sofacy Group is suspected. Another example 2008 cyberattack on US Military computers. Since these cyber-attacks, the issue of cyber warfare has assumed urgency in the global media.
Inexpensive Cybersecurity Measures
- The simplest thing you can do to up your security and rest easy at night knowing your data is safe is to change your passwords.
- You should use a password manager tool like LastPass, Dashlane, or Sticky Password to keep track of everything for you. These applications help you to use unique, secure passwords for every site you need while also keeping track of all of them for you.
- An easy way for an attacker to gain access to your network is to use old credentials that have fallen by the wayside. Hence delete unused accounts.
- Enabling two-factor authentication to add some extra security to your logins. An extra layer of security that makes it harder for an attacker to get into your accounts.
- Keep your Softwares up to date.
Today due to high internet penetration, cybersecurity is one of the biggest need of the world as cybersecurity threats are very dangerous to the country’s security. Not only the government but also the citizens should spread awareness among the people to always update your system and network security settings and to the use proper anti-virus so that your system and network security settings stay virus and malware-free.
Customize your course in 30 seconds
Which class are you in.

- Travelling Essay
- Picnic Essay
- Our Country Essay
- My Parents Essay
- Essay on Favourite Personality
- Essay on Memorable Day of My Life
- Essay on Knowledge is Power
- Essay on Gurpurab
- Essay on My Favourite Season
- Essay on Types of Sports
Leave a Reply Cancel reply
Your email address will not be published. Required fields are marked *
Download the App

- Skip to main content
- Skip to secondary menu
- Skip to primary sidebar
- Skip to footer
A Plus Topper
Improve your Grades
Essay on Cyber Security | Cyber Security Essay for Students and Children in English
February 14, 2024 by Prasanna
Essay on Cyber Security: Nowadays, personal and business operations depend on technologies and computers, so it is easy for attackers to steal information through the internet. Cybersecurity covers all aspects of ensuring citizens’ protection, critical infrastructures, and businesses from any threat from using the internet.
You can also find more Essay Writing articles on events, persons, sports, technology and many more.
Long and Short Essays on Cyber Security for Students and Kids in English
We provide students with essay samples on a long essay of 500 words and a short essay of 150 words on Cyber Security for reference.
Long Essay on Cyber Security 500 Words in English
Long Essay on Cyber Security is usually given to classes 7, 8, 9, and 10.
The main definition of cyber security is protecting networks, data, programs, and other information from unattended or unauthorized access, change, or destruction. Around the globe nowadays, cyber security is very vital because of some cyber-attacks and cyber-attacks. Many companies develop software for data protection.
The main task of the software developed by the companies is to protect the data in their system. Not only does cyber security helps to secure information, but it also protects it from a virus attack. India is one of the countries with the highest number of internet users, after the USA and China.
Cyber threats can be classified into two major types: Cyber crime, which happens against an individual, corporate, etc. and Cyber-warfare, which happens against a state.
Cyber-crime is the use of cyberspace such as cellphones, computers, the internet or other technical devices, etc. By using numerous codes and software in cyberspace, cyber attackers can commit cyber crime. Through the use of malware, the attackers exploit the weakness in the hardware and software design. Hacking is an ordinary way of penetrating the defences of protected computer systems and disrupting their functioning.
Cyber crimes may occur directly by targeting the computers and spreading the computer viruses or by using Denial of service attacks, which is an attempt to make a network or machine unavailable to its projected users. A software named malware is used to gain access to a private computer, gather sensitive information, or disrupt computer operation.
Snowden exposures have shown that cyberspace can become the theatre of warfare in the 21st century. The future battles will not be fought on land, air, or water but more of wars using cyber-attacks. The use of internet-based invisible force as an instrument initiated by any state to fight against another nation is known as the Cyber-warfare.
The easiest thing that an individual can do to up their security and relax knowing their data is safe is to change their passwords. Many password management tools can be used to keep track of everything for an individual as these applications help them use unique, secure passwords for every website one needs and keep track of all the passwords.
Deleting old unused accounts is a good way to secure someone’s information. In many cases, an attacker can easily access someone’s network by using their old credentials that have fallen by the curb.
To add extra security to logins, one can enable two-factor authentication as the extra layer of security makes it harder for an attacker to get into someone’s accounts. Keeping one’s software up to date is also a way to prevent cyber-attacks.
Cyber security is one of the world’s biggest needs due to today’s high internet penetration as cyber security threats are very dangerous to a country’s security. The government and the citizens should both spread awareness among the people to update their network security settings and their systems and use proper anti-virus so that their system and network settings stay malware and virus-free.
Short Essay on Cyber Security 150 Words in English
Short Essay on Cyber Security is usually given to classes 1, 2, 3, 4, 5, and 6.
Protection of networks, data, programs, and other sensitive information from unauthorized access, change, and destruction is known as cyber security. Cyber security is a major concern in this era where the use of computers has become ordinary for everyone. With the development of technology and the internet’s availability to most of the public, the pathway of cyber crimes has also increased.
Malware, spyware, ransomware, fraud, phishing, etc. are the different types of viruses used in a cyber-attack. Hackers gains access to someone’s computer systems easily if the user of that computer clicks on infected web pages, links, malicious websites, or unintentionally downloads a dangerous program. Cyber security plays an important role in preventing some difficult and heinous crimes like blackmailing, fraud transactions through another account, leakage of personal information.
It is the responsibility of every citizen to spread awareness among everyone and keep their system and network security updated to prevent cyber attacks from happening worldwide.
10 Lines on Cyber Security in English
- Cyber Security is the body of technologies, operations, and applications designed to protect programs, devices, networks, and data.
- As numerous amounts of data are collected, processed, and stored on computers by government, military, and corporate, cyber security is necessary.
- Organizations tasked with protecting information relating to national records should take steps to protect this information with cyber attacks’ growth.
- India ranks higher than its global peers as 54% of ransomware and malware attacks occur in India, whereas globally, 47% of attacks occur.
- Brutal terrorist attacks like 9/11 and 26/11 in Mumbai and America also took place due to a lack of cyber security.
- Three billion accounts were breached in 2013, as reported by Yahoo.
- The government has taken some huge steps to improve India’s cyber security and has established many cyber-crime police stations.
- Cyber security is one of the major challenges in the contemporary world due to its complexity in technology and politics.
- In December 2014, a six-month-long cyber-attack on the German parliament, and in 2008, a cyber-attack on US military computers were launched.
- Citizens and governments have to spread awareness about cyber attacks among the public; otherwise, the rate of cyber attacks will increase more and not control it.
FAQ’s on Cyber Security Essay
Question 1. What are the major types of cyber-attacks?
Answer: The main cyber-attacks are:
Question 2. Is there any difference between IT and cyber security?
Answer: IT security is applying measures and systems designed to safely protect the information using various forms of technologies, whereas cyber security is more about the protection of data in its electric form.
Question 3. Name the biggest cyber attack to date?
Answer: The Internet Giant in September 2016 announced that a cyber-attack that compromised 500 million users’ personal information took place, which is the biggest cyber attack to date.
Question 4. What are some of the main foundations of cyber security?
Answer: Some of the main foundations of cyber security consists of information security, end-user education, business continuity planning, application security, operational security.
- Picture Dictionary
- English Speech
- English Slogans
- English Letter Writing
- English Essay Writing
- English Textbook Answers
- Types of Certificates
- ICSE Solutions
- Selina ICSE Solutions
- ML Aggarwal Solutions
- HSSLive Plus One
- HSSLive Plus Two
- Kerala SSLC
- Distance Education
Student Essays

Essay On Cyber Security | Importance, Risks & Challenges
The Cyber security is the need of today’s time. The world is getting on increasingly digital. Here in point, there comes the needs for us to strengthen our cyber security to face possible risk and cyber challenges. Here is the short essay in point that discusses the meaning, importance, risks, challenges and ways to deal with cyber security in today’s world. This essay is helpful for both children and students.
Essay on Cyber Security, its Meaning & Importance
Defining Cyber Security
Cyber security can be defined as the protection of systems, networks and data within cyberspace. Defending against losses, compromises, or attacks using preventative measures is the goal of cyber security
Meaning & Importance of Cyber Security in Modern World
Cybersecurity is a complex issue that cuts across multiple domains and requires multi-dimensional, multi-layered initiatives and responses. Since it involves various ministries and departments, it has proved to be a challenge for governments. In the absence of tangible perpetrators, the threat spectrum is diffused and varied, making it difficult to formulate a suitable response.
The goal of cybersecurity is to prevent unauthorized or unattended access, destruction, and changes to data, networks, programs, and other information. Security threats and cyber-attacks have made cybersecurity a very important issue in the modern world. There are many companies that develop software for data protection.
Using this software, the data will be protected. In addition to protecting information, cybersecurity helps to protect our system from virus attacks. The U.S. and China have the most internet users, followed by India.
Classification/Types of Cyber Security
Cyber security can be classified into two broad categories;
- Cyber crime
Cyber Warfare
Cyber crime.
Criminal activities using computers or networked devices are known as cybercrime. Most cybercrimes are performed by cybercriminals for financial gain, but other cybercrimes are undertaken to damage or disable computers or devices, while others use computers or networks to spread malicious software, illegal information or images. It causes frustration, anger & Loneliness among the victims.
In addition to its financial effects, cybercrime can involve many different types of profit-driven criminal activity, such as ransomware attacks, email and internet fraud, and identity fraud, as well as attempts to steal financial account, credit card or other payment card information.
How to Boost Cyber Security & Prevent Cyber crime
Although it may not be possible to eliminate cybercrime completely and ensure complete internet security, businesses can reduce their exposure to it by implementing an effective cybersecurity strategy that employs a defense-in-depth approach to securing systems, networks, and data.
The following steps can help reduce cybercrime risks:
- Create a clear policy and procedure for the business and its employees;
- Prepare plans for managing cybersecurity incidents;
- Provide an overview of the systems and data protection measures in place;
- Install two-factor authentication (2FA) keys or use two-factor authentication apps;
- When possible, enable 2FA for every online account;
- Verify verbally the authenticity of requests to send money by talking to a financial manager;
- Set up intrusion detection systems (IDS) to flag emails with extensions similar to company emails;
- Analyze each email request for a transfer of funds to determine if it is different from the norm;
- In order to prevent security breaches, employees should be continuously trained on cybersecurity procedures;
- Maintain all software release updates and patches on websites, endpoint devices, and systems; and
- Data and information should be backed up regularly to avoid data breaches and ransomware attacks.
Cyberwarfare is the use of computers and the networks that connect them to wage war against other states. Government and military networks are usually attacked in cyberwar in order to disrupt, destroy, or deny their use. Cyberspace is made up of computers and their networks. Almost every aspect of modern society depends on cyberspace, and developing countries are becoming more reliant on it each year.
From critical infrastructure to financial institutions and commerce to national security, almost everything modern society relies on cyberspace to function. Cyber attacks do share some similarities with other criminal attacks in that they produce the same result.
The role of cybersecurity in today’s world is growing due to the high penetration of the internet. Cybersecurity is becoming an increasingly dangerous issue to the security of a country. Among the citizens as well as the government, awareness of updated network and system security settings and the use of proper anti-virus should be spread so that your networking and system settings remain virus-free and secure.
Short Essay on Cyber Security & its Importance today
Cybersecurity is an effort to keep electronic gadgets such as laptops, smartphones, and tablets away from hackers and data thieves. It is always detrimental to the end user.
Nowadays, everyone needs to have proper cybersecurity with the increasing use of electronic gadgets. It ensures the protection of our private data and official and personal documents. Cyber Security is essential to ensure the safety and privacy of our data. When Cyber Security is not implemented, anyone can steal, misuse, and abuse our data without our authorization.
Keeping our data and important documents secure when using electronic gadgets is extremely important for all people who use them regularly and frequently. Cyber security has grave impact upon the mental health of youth. It has been the leading cause of frustration, depression , anger and uncertainty. Cyber Security is provided in many ways, some of which are Antivirus, Antimalware, End-User Protection, etc.
It is important to update your system software regularly. Choose a strong password when enabling security on your gadgets. Also, avoid clicking on uncertain and suspicious links. Keeping our devices secure with the help of the tools discussed above is crucial in the current digital world.
2 thoughts on “Essay On Cyber Security | Importance, Risks & Challenges”
How to writena book in this website?
Yes! You can get your post Published with us. For more contact us at the given email at contact Us page
Leave a Comment Cancel reply
Save my name, email, and website in this browser for the next time I comment.
Home — Essay Samples — Information Science and Technology — Computers — Cyber Security
Essays on Cyber Security
Choosing a topic, types of essays, example thesis statements, example paragraphs, brief history of cyber security, cyber crimes and cyber security in modern world, made-to-order essay as fast as you need it.
Each essay is customized to cater to your unique preferences
+ experts online
Cybersecurity and Risk Management
Effects of social media on cybercrime, the importance of cybersecurity: department of justice, yahoo and jp morgan chase, the history and concept of cyber security, let us write you an essay from scratch.
- 450+ experts on 30 subjects ready to help
- Custom essay delivered in as few as 3 hours
Impact Realisation of Cyber Warfare
Fundamental steps of cyber security, statement of purpose (information technology and cyber security), data mining and machine learning methods for cyber security intrusion detection, get a personalized essay in under 3 hours.
Expert-written essays crafted with your exact needs in mind
Best Ways to Have Secure Coding at Your Company
The issue of digital security risks and its types, a survey on android malwares and their detection techniques, the notions of cyber-warriors in social media, human error, the weakest link in cybersecurity, digital crime and digital terrorism: the future of technology, general data protection regulation, cyber bullying, its effects and ways to stop, cyber crimes, cyber terrorism as a major security challenge, the most damaging hackers' attacks in history, malware classification using machine learning, national security and its need for technological advancement, international cybercrime law: past, present, future perspectives, the future of cyber security: what we can expect, research on cyberwarfare: cyberattacks, experiments, and future predictions, the role of information security, quality of life issues in relation to computers and information systems, the importance of staying safe on social media, cyber crime: the meaning, types, and ways to avoid, relevant topics.
- Digital Era
- Computer Science
- Virtual Reality
- Artificial Intelligence
- Disadvantages of Technology
- 5G Technology
By clicking “Check Writers’ Offers”, you agree to our terms of service and privacy policy . We’ll occasionally send you promo and account related email
No need to pay just yet!
We use cookies to personalyze your web-site experience. By continuing we’ll assume you board with our cookie policy .
- Instructions Followed To The Letter
- Deadlines Met At Every Stage
- Unique And Plagiarism Free
Cyber Security - List of Essay Samples And Topic Ideas
Cybersecurity, a critical concern in our digitally connected world, encompasses practices, technologies, and policies to protect networks, devices, programs, and data from attack or unauthorized access. Essays could delve into the myriad types of cyber threats like malware, phishing, and ransomware, exploring their evolution and impact on individuals and organizations. They might also discuss the measures individuals and enterprises can adopt to mitigate cyber risks, the challenges of staying ahead of cyber adversaries, and the role of governmental and international regulation in promoting cybersecurity. Discussions could extend to the implications of cybersecurity on national security, privacy, and the digital economy, and how the burgeoning field of cybersecurity is evolving to meet the complex challenges of the modern digital landscape. A substantial compilation of free essay instances related to Cyber Security you can find at Papersowl. You can use our samples for inspiration to write your own essay, research paper, or just to explore a new topic for yourself.
Cyber Security and how to Prevent Cyber Crime
Cybercrimes are interrupting normal computer functions and has brought many known companies and personal entities to their knees. Over the last decade, crime has entered into the world of information. Crime is developing gradually since the days when merchandise was transported by stagecoach, theft or extortion has changed to keep up, even to our modern-day equivalent-credit and debit cards. Stealing credit card number has become well known danger. In the present, internet has become a playing field for computer attackers. […]
Cyber Security Threats in Healthcare
Cyberattacks have been targeting the healthcare industry, among the biggest industries in the US, in the 2018 period. The implication is that it has come time to improve the protection of institutional and patient information with a more tailored approach to this threat. In comparison with other industries, many health organizations have engaged in inadequate investment in cybersecurity while spending approximately as much money as other industries. It is quite worrying when phishing cyberattacks, as well as breaches of patient […]
Impact of Technology on Privacy
The 21st Century is characterized by the heavy impact technology has on us as a society while it continues to develop new devices and modernize technology. Millions of individuals around the world are now connected digitally, in other words, people globally rely heavily on smartphones tablets, and/ or computers that store or save a majority of their personal information. Critical and extremely personal data is available and collected in these smart technology such as credit card details, fingerprint layout, and […]
We will write an essay sample crafted to your needs.
Cyber Security Threats on the State Level
This paper examines two notable events of cyber warfare and security in our current age (the Stuxnet attack on centrifuges, and the Petya ransomware affecting citizens and governmental agencies), as well as examines how these attacks shape foreign and domestic policies and procedures. By examining the extent of the damage of these two attacks, I will argue that cyber warfare events will not just affect governmental systems, but would ultimately cause destruction to the layman's infrastructure, further crippling any state […]
Essay of Cyber Security Education
The experts and professionals of matters related to cyber security should assign the participant puzzles whereby they should divide themselves into various teams as indicated in the framework of NICE, and each group should specialize in a specific area. There is a wide range of ideas on the cyber security where the riddles may come from the fields like Wireshark, protection of website application, analysis of digital systems, and social engineering. There should be a task force created to conduct […]
Constant the Rise of Technologies and Cyber Threats
There is a wide range of cyber threats that happen every day, it is important that we follow all of the necessary precaution's in order to ensure the safety of our private information including but not limited to passwords, network credentials, banking or credit card information. Malicious attacks occur more frequently than one would expect, their purpose is to damage a device. Most of us are unaware of the weaknesses we have within our smartphone's security settings. With that being […]
Cyber Security for the Average American
According to statistics, the average American spends 10 hours per day using technology. Whether it be a cellphone, tablet or laptop, that's more than 40 hours a week online. We think that we're safe, but part of living in this 21st century is understanding that our so-called private information can easily accessed by the wrong person and made public. I am sure you have heard, at some point, news pertaining to identity theft or data breaches, with the effects being […]
Cyber Security for our Generation
Some of the biggest threats to our national security often go unnoticed. These threats are generally not publicized, and no emphasis is placed on them. They represent some of the most significant challenges our generation faces. It's shocking is that these threats are often covered up or are attempted to be. For instance, one of the key issues that arose in 2018 was the Facebook data scandal. This scandal was not a cyber-attack per se, yet it highlighted that most […]
How Pervasive is the Internet in your Life?
Q.1 How pervasive is the internet in your life? How much do you think society has come to depend on the Internet? Answer: When it comes to how pervasive the internet is in current life, my answer is that the internet has almost influenced each event of our daily life every day. Of course, we can't deny that there may be some people, around our side, who never heard about the internet, for example, those elder people who has less […]
The E-Commerce and Cyber Security
The wish is the online e-commerce company that will provide the opportunity for all shoppers to find their favourite wordrobe online in all of the world. Their wardrobe could be included dresses, skirts, jeans and etc.... This company was founded in 2010 and also have the App for their over 100 million users on the iOS and android platform. The E-Commerce servers for this company is located in four cites internationally, two are in the USA, the headquarter in Alexandria […]
Advanced Cyber Security and its Methodologies
Digital Civilization has turned into a critical wellspring of data sharing and proficient exercises like business, saving money exchanges, shopping, and administrations and With the expansion in utilization of the internet, cybercriminal exercises are additionally expanding exponentially. The fundamental reasons is that with the commencement of internet, the web applications were likewise getting prevalence for information putting away and information sharing, regardless of the client. With the progression of time, web applications were getting more intricate with quick increment in […]
Defining Cybersecurity Law
INTRODUCTION In "Defining Cybersecurity Law," Jeff Kosseff, the author, appears to be more concerned with improving cybersecurity law than defining it. In this paper, I will provide a brief summary and critique of the four substantive sections of this article. I will conclude with a mention of the aspects of cybersecurity law the author missed. My main issues with this article are the author's (1) preoccupation with the prevention of cybersecurity breaches instead of balancing security against values, (2) definition […]
Why do you Want to Study Cyber Security
In today's hyper-connected era, we're more online than offline. Our digital identities intertwine with the real, making the boundary blurry. But as we gleefully navigate this digital frontier, shadows lurk in the form of cyber threats, reminding us that our brave new world isn't without its pitfalls. So, why venture into the challenging world of cybersecurity? Why choose a path that constantly grapples with these shadows? Spoiler alert: It's more than just a career choice. Real-world Superheroes In comic books […]
Health Care Cyber Security
Healthcare is an industry sector that has become unstable and crucial in this expanding digital landscape. This necessitates an organization's data security program to be properly structured, as there is no room for error, which could easily translate into a life-and-death situation. This article presents both fundamental technical and business issues that often elude the healthcare data security program. On the technical side, extensive proliferation of data and systems into the cloud, a continuous increase in connected medical devices, and […]
Substations: Smart Grid & Cyber Security Threats
Transferring from old energy network to a new technology such as smart grids. It changes the energy industry worldwide to better quality, manageability and performance. It gives us the ability to operate it by communications, monitor and control it. However, using communications in smart grid increase connectivity causing our security to be exposed and make it more challenge to protected. It can be a target for hackers, and cyber terrorism. Thus, it got governments, consumer and industry attention to increase […]
Cybersecurity: Protecting the Fragile Web of Global Connectivity
I believe everything that is created by man can also be destroyed by it. Humans have proved to be the most intelligent species in this world. We have created the technology that appears to be smarter than the human brain but if it overpowers the human intelligence it can be destroyed as well. Internet works in the same manner. It has created dependencies that have led to millions of people relying on this technology in getting every task done no […]
Cybersecurity Issues in Societal Perspective
E-governance and Cybersecurity Documents issued by a country's government provide a personal identity to an individual. Driver's licenses, social security numbers, tax identification numbers, and various other entitlement documents are used on a regular basis by people to demonstrate their identity and authorization for various opportunities. Because these documents form the basis for all subsequent documents, their integrity is of high importance to stakeholders. Therefore, these crucial documents are targets for criminals and further cyberattacks (Conklin, A., & White, G. […]
The Real Issue Behind Cyber-Security
The steady trend towards digitalization has been occurring for a long time, and as of lately, a new type of crime market has risen alongside digitalization. In recent years, companies all over the world have been affected by some form of cybersecurity issue whether that be attacks to infrastructure or momentary paralyzation of the company itself through the exploitation of security measures. Over the years the number of attacks all around the world has increased exponentially with many more cyber-attacks […]
Cybersecurity Today
Networks (internet) are not secure enough due to the lack of efficient cybersecurity. As a result, ransomware attacks are increasing, affecting most businesses and individuals today. Enacting measures to detect cyberattacks and ransomware attacks can be helpful in preventing unforeseen repercussions from the attacker in the corporate network. Cybersecurity needs to implement new policies and recommendations so that ransomware attacks can be reduced. This report will first discuss some ransomware attacks that have happened before. Next, the report will discuss […]
Cybersecurity as a Form of Digital Protection
Cybersecurity is an ever-growing form of digital protection, created and used for the sole purpose of protecting confidential information against hard drive malfunctions, power outages, and adversaries. In healthcare, it is crucial for hospitals and health providers to keep up with the security of digital health data through cybersecurity in order to comply with the Health Insurance Portability and Accountability Act (HIPAA) and avoid potentially devastating consequences. Insider threats, access control breaches, and network breaches are some of the main […]
Virtual Reality: Game Transfer Phenomena
Imagine if you were you were floating through space, watching a horror film,s or perhaps playing a video game, and it seemed like you were actually there. With the invention of virtual reality (VR), people are able to explore the illusion of this reality. Virtual reality is computer-generated technology used to create a manufactured environment. There is a range of systems that are used for this purpose such as special headsets and fiber optic gloves. The term virtual reality means […]
Cybersecurity Paper
With cybersecurity attacks on the rise, the ability of an organization to ensure uninterrupted operations is an imperative. No longer can an organization solely rely upon software applications to identify and mitigate cyber risks. It takes a skilled team led by an experienced manager to holistically address an organization's technology risks. The National Infrastructure Advisory Council's (NIAC's) definition of infrastructure resilience is "the ability to reduce the magnitude and/or duration of disruptive events. The effectiveness of a resilient infrastructure or […]
Cybercrimes: an Unprecedented Threat to the Society
What is a Cybercrime? Cybercrime, or computer-oriented crime, is the crime that involves computer and its network. The computer may have been used in the commission of a crime, or it may be the target. Cybercrimes can be defined as: "Offences that are committed against individuals or groups of individuals with a criminal motive to intentionally harm the reputation of the victim or cause physical or mental harm, or loss, to the victim directly or indirectly, using modern telecommunication networks […]
Cybersecurity for a Successful Acquisition Report
The act of conducting a policy gap analysis is crucial in determining any missing overlap or technical deficiencies when planning to join the IT architecture and network topologies of two or more companies. During the acquisition process, the policies of either party will be examined in order to confirm current software updates and patches, proper configuration of tools, and employee protocol during the transition. Once the initial merger is complete, it'll be important to compare the outcome with each company's […]
Reasons of Cyber Attacks
1. Substandard User ID and Password Every individual need to have their own password secure and stronger. For an instance strong password can be obtained by latest maintaining minimum of having15-character length with an least one special character, number, capital and small alphabet. Most importantly choosing password like own name, date of birth, phone number may become hacker to simply figure out easy to break through your personal account security. In the same way User ID should not be shared […]
Laws of Cybercrimes
Abstract This paper examines the cyber security and its challenges in current temperamental circumstance of security in present world. These day's innovation of technology persistently developing more quickly than expected. As a public that runs on latest innovation technologies, we are likewise therefore reliant on it. Where similarly as innovation of technology brings ever more noteworthy advantages, it likewise brings ever more prominent threats. We should look some significant concerns confronting that incorporate threats, information theft, identity theft, cyber war, […]
Developing and Testing Photorealistic Avatar with Body Motions and Facial Expressions for Communication in Social Virtual Reality Applications
Developing and Testing Photorealistic Avatar with Body Motions and Facial Expressions for Communication in Social Virtual Reality Applications Abstract Providing effective communication in social virtual reality (VR) applications requires a high level of avatar representation realism and body movement to convey users’ thoughts and behaviours. In this research, we investigate the influence of avatar representation and behaviour on communication in an immersive virtual environment (IVE) by comparing video-based versus model-based avatar representations. Additionally, we introduce a novel VR communication system […]
Advantages of Cybersecurity in a Digital World
Ever stopped to think about how much of your life plays out in the digital realm? Our lives are undeniably intertwined with technology, from morning alarms on our smartphones to evening Netflix binges. Yet, while we eagerly embrace the latest app or gadget, there's an unsung hero behind the scenes, ensuring our digital escapades are safe and sound: cybersecurity. It's easy to dismiss it as mere technical jargon or something only businesses need to worry about. But, truth be told, […]
Spyware Defense: Navigating the Seas of Digital Security
In the vast, uncharted ocean of the digital world, spyware represents treacherous waters that threaten to capsize the ship of your data security. Just as sailors and navigators of old employed a combination of keen awareness, advanced tools, and strategic planning to avoid perilous waters and ensure safe voyages, modern computer users must adopt comprehensive approaches to defend against the insidious threat of spyware. This essay explores effective spyware elimination techniques through the imaginative analogy of maritime navigation, emphasizing the […]
Featured Categories
Related topic, additional example essays.
- Positive Effects of Social Media
- Appropriate Age for Social Media
- Instagram and body dysmorphia
- Is Social Media Bad for Relationships Argumentative Essay
- The Negative Effects of Social Media On Mental Health
- Leadership and the Army Profession
- Why College Should Not Be Free
- Shakespeare's Hamlet Character Analysis
- A Raisin in the Sun Theme
- Why Abortion Should be Illegal
- The Devil And Tom Walker: Romanticism
- Does Arrest Reduce Domestic Violence
How To Write an Essay About Cyber Security
Understanding cyber security.
Before writing an essay about cyber security, it is essential to understand what it encompasses. Cyber security refers to the practice of protecting systems, networks, and programs from digital attacks. These cyber attacks are usually aimed at accessing, changing, or destroying sensitive information; extorting money from users; or interrupting normal business processes. Begin your essay by defining cyber security and discussing its importance in the contemporary digital world. Explore the different types of cyber threats, such as malware, phishing, ransomware, and denial-of-service attacks. It’s also crucial to understand the impact of these threats on individuals, businesses, and governments.
Developing a Thesis Statement
A strong essay on cyber security should be anchored by a clear, focused thesis statement. This statement should present a specific viewpoint or argument about cyber security. For instance, you might discuss the evolving nature of cyber threats, the challenges of cyber security in a particular sector (like finance or healthcare), or analyze the effectiveness of current cyber security measures. Your thesis will guide the direction of your essay and provide a structured approach to your analysis.
Gathering Supporting Evidence
To support your thesis, gather evidence from credible sources. This might include recent studies on cyber security, statistics about cyber attacks, examples of significant security breaches, or expert opinions. Use this evidence to support your thesis and build a persuasive argument. Remember to consider different perspectives, including technological, ethical, and legal viewpoints.
Analyzing Cyber Security Strategies and Challenges
Dedicate a section of your essay to analyzing cyber security strategies and the challenges faced in implementing them. Discuss various approaches to cyber security, such as technological solutions, policy measures, and user education. Explore the challenges in keeping up with constantly evolving cyber threats and the balance between security and privacy. For example, consider how advancements in areas like artificial intelligence and machine learning are influencing cyber security practices.
Concluding the Essay
Conclude your essay by summarizing the main points of your discussion and restating your thesis in light of the evidence provided. Your conclusion should tie together your analysis and emphasize the significance of cyber security in the digital age. You might also want to reflect on future trends in cyber security or suggest areas where further research or policy development is needed.
Reviewing and Refining Your Essay
After completing your essay, review and edit it for clarity and coherence. Ensure that your arguments are well-structured and supported by evidence. Check for grammatical accuracy and ensure that your essay flows logically from one point to the next. Consider seeking feedback from peers or experts in the field to refine your essay further. A well-written essay on cyber security will not only demonstrate your understanding of the topic but also your ability to engage with complex technological and societal issues.
1. Tell Us Your Requirements
2. Pick your perfect writer
3. Get Your Paper and Pay
Hi! I'm Amy, your personal assistant!
Don't know where to start? Give me your paper requirements and I connect you to an academic expert.
short deadlines
100% Plagiarism-Free
Certified writers
Information Security Awareness Essay
- To find inspiration for your paper and overcome writer’s block
- As a source of information (ensure proper referencing)
- As a template for you assignment
As more and more governments and private companies rely on Internet and Communications Technology (ICT), maintaining information security is becoming of utmost importance. In the pursuit of preventing cyberattacks, many entities have long been embarking on up-to-date technologies and software programs. Governments and commercial organizations have started considering human factors such as user role, knowledge, learning style, and psychological factors in implementing information awareness programs.
Until recently, businesses have relied solely on the process and technologies to address cybersecurity threats without incorporating human factors into their plan. After continuous attacks, companies realized the importance of considering employees’ integration with the processes and technologies in effectively addressing security threats (Ki-Aries & Faily, 2017). Integrating workers into security prevention is through implementing information security awareness (ISA) programs. Such programs aim to improve workers’ perception of the cyber security risk as credible and teach how to prevent risks (Bada et al., 2019). Hence, ISA aims to teach people to be aware of the potential cyber threats and respond accordingly.
Impact of User Characteristics on Security Awareness and Learning
Prior knowledge.
Another significant human factor impacting individuals’ engagement with security awareness (IS) is their general knowledge about IS. Empirical evidence shows that “higher the user’s knowledge of fundamental IS applications, the more likely they are aware of securely-related issues” (Jaeger, 2018, p. 4705). On the contrary, those who lack knowledge in IS are reluctant to engage in cybersecurity awareness training (Jaeger, 2018). Hence, users’ prior knowledge in security awareness-related issues can substantially impact their awareness level and learning.
Learning Style and Information Acquisition
Although a user’s learning style could be one of the potential determinants of individuals’ security awareness level, the existing literature does not present any evidence regarding this relationship. Nevertheless, empirical evidence proves that the availability of resources and campaigns dedicated to ISA can significantly positively influence users’ comprehension and learning of cybersecurity (Jaeger, 2018, p. 4705). Scholars have also emphasized the effectiveness of diversified and customized methods of teaching by introducing game-based, text-based, video-based methods to improve employees’ security awareness and behavior (Bauer & Bernroider, 2017). Moreover, utilizing other channels, such as sending reminders about the security risks and threats to users, is also said to impact the ISA positively (Bauer & Bernroider, 2017). Hence, employees are more likely to learn and engage with information security when provided with resources to do so.
Perception of Security
One of the significant human factors that influence ISA is the individuals’ perception of security. Bada et al. (2019) have found that employees often treated awareness programs as “tick-box exercises” without engaging in genuine concern (as cited in Ki-Aries & Faily, 2017, p. 664). Even though IS goals were identified, from a cultural perspective, individuals did not perceive security threats as credible and hence, “did not feel a need to browse internal security guidance” (Maqousi et al. 2013 as cited in Ki-Aries & Daily, 2017, p. 664). In addition, recognition and appreciation of those who engage in IS are essential since it encourages positive behavior towards IS (Dominguez et al. 2010 as cited in Ki-Aries & Daily, 2017). Meanwhile, Bauer and Bernroider (2017) emphasized that social norms, which is defined as “employee’s perception of an acceptable or permissible ISP-compliant behavior within their organization,” had a positive effect on the employee compliance with information security rules (p. 50). Hence, individuals’ perceptions of information leakage and security awareness play a significant role in the success of ISA programs.
Psychological Characteristics
Another predominant factor emphasized in the existing scholarship on security awareness is the user’s psychological and character traits. Namely, Parsons et al. (2017) has found that individuals with personality traits such as conscientiousness and agreeableness have demonstrated higher scores on the Human Aspects of Information Security Questionnaire (HAIS-Q). More agreeable individuals are concerned more about what other people think about them; hence, they are more likely to be cautious with their security behavior (Shrosphire et al., 2015, as cited in McCormac et al., 2017). On the contrary, individuals who are more impulsive, with a higher propensity to take risks, tend to score higher on ISA (McCormac et al., 2017). This finding is also supported by Hadlington (2017), who found highly impulsive individuals often with little concern for their actions, hence, violating cybersecurity rules. The author also found that users with interned addictiveness were more likely to demonstrate risky security behavior (Hadlington, 2017). Thus, although some scholars disagree on the nature of the relationship, many agree that personality traits are significant factors that might influence the ISA.
Personal Norms
The existing literature also emphasizes the importance of employees’ personal norms on the increased intention to comply with information security awareness programs. Specifically, Bauer and Bernroider (2017) have found that users often apply neutralization techniques, which are “justifications, which individuals invoke to convince themselves, and others, that their deviant behaviour is justifiable or excusable” (p. 50). This concept includes techniques such as “condemnation of the condemners,” “defense of necessity,” “denial of injury,” “denial of responsibility,” with the former two techniques being the most important ones (Bauer & Bernroider, 2017, p. 58). In other words, by applying such techniques, employees often did not comply with the proper information security behavior.
Additional Factors
While the abovementioned factors primarily relate to the human factors that might influence security awareness and learning, the existing literature explored several additional factors ranging from demographic to technological aspects. Some scholars have found that women and younger people (18-25) are more susceptible to security breaches than men (Sheng et al., 2010 as cited in McCormac et al., 2017). Bauer and Bernroider (2017) have emphasized technological factors such as reminders and security warning messages to affect ISA positively. Therefore, although human factors are the most significant factors, organizations should also consider other factors.
Bada, M., Sasse, M.A. & Nurse, J.R.C. (2019). Cyber security awareness campaigns: Why do they fail to change behaviour? International Conference on Cyber Security for Sustainable Society , 2015 .
Bauer, S., & Bernroider, E. W. N. (2017). From information security awareness to reasoned compliant action. ACM SIGMIS Database: the DATABASE for Advances in Information Systems , 48 (3), 44–68.
Hadlington, L. (2017). Human factors in cybersecurity; examining the link between internet addiction, impulsivity, attitudes towards cybersecurity, and risky cybersecurity behaviours . Heliyon , 3 (7), 2–18.
Jaeger, L. (2018). Information security awareness: Literature review and integrative framework. Proceedings of the 51st Hawaii International Conference on System Sciences , 4703–4712.
Ki-Aries, D., & Faily, S. (2017). Persona-centred information security awareness . Computers & Security , 70 , 663–674.
McCormac, A., Zwaans, T., Parsons, K., Calic, D., Butavicius, M., & Pattinson, M. (2017). Individual differences and information security awareness . Computers in Human Behavior , 69 , 151–156.
Parsons, K., Calic, D., Pattinson, M., Butavicius, M., McCormac, A., & Zwaans, T. (2017). The Human Aspects of Information Security Questionnaire (HAIS-Q): Two further validation studies. Computers & Security , 66 , 40–51.
- Global Cybersecurity in the 21st Century
- Forensic Accounting and Cyber Security
- Mining and Ocean Use in Canada
- Water Policy: The Impacts of Water Trading
- Financial Statement Fraud-Detection, Prevention, Related Regulations
- The Cybercrime Impact on People and Business
- Airport Security: Technological Requirements
- Hacking Prevention: Mobile Phone Anti-Virus
- Social Engineering Techniques for Bill’s Meat Packing Plant
- Identity Theft on Credit Card Fraud Using Qualitative Method
- Chicago (A-D)
- Chicago (N-B)
IvyPanda. (2023, July 28). Information Security Awareness. https://ivypanda.com/essays/information-security-awareness/
"Information Security Awareness." IvyPanda , 28 July 2023, ivypanda.com/essays/information-security-awareness/.
IvyPanda . (2023) 'Information Security Awareness'. 28 July.
IvyPanda . 2023. "Information Security Awareness." July 28, 2023. https://ivypanda.com/essays/information-security-awareness/.
1. IvyPanda . "Information Security Awareness." July 28, 2023. https://ivypanda.com/essays/information-security-awareness/.
Bibliography
IvyPanda . "Information Security Awareness." July 28, 2023. https://ivypanda.com/essays/information-security-awareness/.
- Active Directory Attack
- Network Attack
- Mitre Att&ck
- E-Mail Attack
CVE-2023-21554 – Hunt For MSMQ QueueJumper In The Environment
Os credential dumping- lsass memory vs windows logs, credential dumping using windows network providers – how to respond, the flow of event telemetry blocking – detection & response, uefi persistence via wpbbin – detection & response, linux event logs and its record types – detect & respond, how businesses can minimize network downtime, recovering sap data breaches caused by ransomware, how does dga malware operate and how to detect in a…, what is port forwarding and the security risks, how to optimize business it infrastructure, how businesses can identify and address cybersecurity lapses , cybersecurity management 101: balancing risk management with compliance requirements, remote desktop gateway – what is it, how to detect malware c2 with dns status codes, how brazilian students use ai, tools online casinos use to protect players, vdr — a space for efficient and secure transactions, how encryption plays a vital role in safeguarding against digital threats, push notification protocols: ensuring safety in digital communication, phishing scam alert: fraudulent emails requesting to clear email storage space…, vidar infostealer malware returns with new ttps – detection & response, new whiskerspy backdoor via watering hole attack -detection & response, redline stealer returns with new ttps – detection & response, understanding microsoft defender threat intelligence (defender ti), threat hunting playbooks for mitre tactics, masquerade attack part 2 – suspicious services and file names, masquerade attack – everything you need to know in 2022, mitre d3fend knowledge guides to design better cyber defenses, mapping mitre att&ck with window event log ids, how email encryption protects your privacy, how to check malicious phishing links, emotet malware with microsoft onenote- how to block emails based on…, how dmarc is used to reduce spoofed emails , hackers use new static expressway phishing technique on lucidchart.
- Editors Pick
Cyber Security Essay: Topics and Tips to Write a Stellar Paper

Cyber security has become exceedingly important over the last two decades. If countries are not trading accusations and counter-accusations over the violation of their online spaces, they’re strategizing how to keep attackers at bay. Countries with the best cyber defenses thrive, while unprepared ones suffer massive losses annually. But in the era where computers have literally taken over all facets of our lives, keeping safe from hackers and other crooked spies has never been more important. The subject has attracted massive attention online, with millions of articles exploring it. Therefore, it’s unsurprising that you’re looking for help with a cyber security essay. This short piece will provide all the assistance you need. It covers industry secrets, tips, and tricks from top cyber security professionals to help you write an essay on cyber security effectively. Read on to stay ahead of the pack.
Choosing Captivating Cyber Security Essay Topics
There are uncountable cyber security essay topics to choose from. Since the subject is highly contested, many issues arise daily that you can explore in your papers. However, not all topics will generate interest or add value to the debate. So, how do you go about choosing a befitting theme or subject for your essay? Here are a few tips:
- Relevance: You can write just about anything if it’s germane. You want to explore something that’s to the point and benefits your audience. Readers don’t appreciate their time wasted. Therefore, both your topic and contents must align lest they feel cheated.
- Trending: We now live in the age of #tags. Computer algorithms control what you see, when you see them, and how you see them. If you’re committed to your work, you should always consider and research current trends to maximize the impact of your paper.
- Passion: As already noted, there are numerous issues in computer security that you can write about. But not all ideas will interest you. Therefore, it’s advisable that you align with the topics you feel more passionate about. For example, it could be the nexus between data protection and cyber security, government involvement and cyber security, social engineering and cyber security, artificial intelligence and cyber security, cybersecurity laws and regulations and cyber landscape, and hacking and cyber security. Know where you lean and formulate a solid topic to explore.
From Beginner to Pro: How to Write a Stellar Essay on Cyber Security
Now that we’ve explored topic selection, let’s delve into the nitty gritty of essay writing on cyber security. Below are six critical tips to get you started:
- Background research. Solid essays benefit from thorough research work. Yours should be no exception. Remember you’re not the first person to write about the topic. There could be thousands if not millions of papers on it. So, how do you want to convince your audience to read past your introduction? Stay ahead of the curve. Read widely and determine what other authors have explored in their works. Find the gaps, the points of weakness to exploit, and the strengths to build upon. Additionally, carrying out thorough research gives you a balanced perspective. This is vital because it limits biasness. Readers are often uninterested in reading opinion pieces masquerading as research papers. Therefore, incorporate relevant and credible citations in your work, backing every claim you make.
- Solid essay structure. At this stage, you probably know the basic structure of an essay – introduction, body, and conclusion. While there are numerous variations based on an essay’s length, this fundamental formation remains the same. Ensure that your writing respects these basics, minimizing the chances of having a head or tail-heavy paper. For example, a two page essay should not have an introduction that exceeds 150 words, otherwise it becomes head-heavy. On the other hand, you can afford writing 250 words on a longer paper of 10 or more pages. Balance is critical in this case. However, if you’re unsure of what to do, you can seek help and order essay by CustomWritings which has assisted numerous students with similar challenges. Reach out to them and you’ll never regret it.
- Coherence. Having a free-flowing paper is even more critical than adhering to structural integrity. There is no benefit to having a well-structured work with a disjointed flow of ideas. As an argumentative essay, each section should usher your readers to the next seamlessly. Your paragraphs should gel and project the same messages and emotions, otherwise it becomes difficult for readers to follow the logical progression of your thoughts and may lead to confusion or disinterest. Remember that even word choice plays a significant role in the overall flow of your essay. If you do this right, you not only demonstrate clarity and organization in your writing, but also exhibit your ability to communicate effectively.
- Case studies. You can strengthen your arguments by adding some case studies and examples while also spicing it up in the process. There are so many real-world cyber security issues to work with. For example, breaches that led to huge financial losses, data theft, or system failures. The importance of creativity to essay writing cannot be over-emphasized. However, crafting an essay on cyber security is more about being factual than creative. As such, you must ground it on real stories.
- Balance. Your papers can also benefit from balanced arguments. You don’t need to convince your audience to adopt your stand by ignoring opposing voices. Instead, you should address them and provide solid counterarguments. This way, your audiences will understand why it’s better to be on your side, while at the same time respecting you as a person. You can write a short note to keep you on track by ensuring that each opposing view is countered effectively.
- Solid conclusion. Be sure to write a paragraph that recaps all your arguments. Some readers are impatient and will always skip to the conclusion to understand what an essay is about. Take that opportunity to grab their attention, and, if possible, maintain it. Your conclusion should be nothing less than a sucker punch that delivers a rush of adrenalin and awakening to them.
Cyber Security Essays Are All About Structure and Coherence!
As discussed in the article, a good essay is all about adhering to the basics. Have a solid structure and make a coherent argument. However, if you want to stand out, you must demonstrate cyber security awareness by incorporating real world examples in your work. Additionally, carry out thorough research to know what’s relevant, accurate, and valid to use. If you follow the tips above, you’ll be on your way to writing a winning paper in English.

LEAVE A REPLY Cancel reply
Save my name, email, and website in this browser for the next time I comment.
- Privacy Policy

Home / Resources / ISACA Journal / Issues / 2022 / Volume 3 / Better Cybersecurity Awareness Through Research
Better cybersecurity awareness through research.

In the last few years, information security professionals have faced tremendous challenges. Just in 2021, there were more than two billion malware attacks and trillions of intrusion attempts. 1 Ransomware attacks alone have increased by 151 percent compared with 2020. 2 In fall of 2020, Cybersecurity Ventures estimated worldwide cybercrime costs would reach US$6 trillion annually by the end of 2021, ransomware damage costs would rise to US$20 billion, and an enterprise would fall victim to a ransomware attack every 11 seconds during the year. 3 The European Union introduced 474 separate enforcement actions for EU General Data Protection Regulations (GDPR) violations, starting from the time enforcement of the GDPR began in 2018 through December 2020, with fines totaling US$312.4 million. 4
Cybercrime is projected to worsen due to the rapid changes resulting from the COVID-19 pandemic. Thousands of organizations allowed employees to continue working from home throughout 2021, and there are indications that many will permit hybrid work indefinitely. Remote work opens a Pandora’s box of issues for organizations trying to maintain some semblance of security. Cybersecurity firm Malwarebytes reported in an August 2020 survey that remote workers caused security breaches in 20 percent of the organizations it surveyed. 5 Although the need for security awareness training for remote employees is pressing, many organizations have been finding it more difficult to implement than providing established training in a centralized workplace.
Importance of Awareness and Training
One study conducted with participation from more than 5,000 organizations around the world discovered that organizations are becoming more aware of the role of their employees play in information security incidents. Survey data collected as part of the study reported that 52 percent of organizations indicated employees were their biggest weakness in IT security, with their actions putting the business and the organizational information security strategy at risk. Forty-three percent of the organizations polled considered deployment of more sophisticated software an effective way to safeguard themselves against evolving threats ( figure 1 ). Offering staff training was the second most popular method for safeguarding organizations according to the survey, closely followed by increasing internal IT or IT security staff. 6

Similar to those findings, Verizon’s 2021 Data Breach Investigations Report states that nearly 85 percent of incidents and data breaches from 2020 were attributable to human error. 7 Additional data from the field comes from the Willis Towers Watson Cyber Claims Analysis Report , 8 which reveals that clients filed close to 1,200 data breach claims in nearly 50 countries from 2013 to December 2019. The report identifies human error such as employees clicking on links in phishing emails or replying to spoofed emails as the most common root causes of breaches (figure 2) . The costliest events were typically those where the threat actor impersonated a chief executive officer (CEO) or senior manager. The most frequently employed social engineering tactic was impersonation of a vendor or supplier. All these things could easily be prevented through employee education and training, the report concludes. 9

According to a white paper from Osterman Research, employees who received cybersecurity training demonstrated a significantly improved ability to recognize potential threats, earning the respect of their organization’s security teams. 10 By applying a model that Osterman developed to data acquired through a survey of 230 individuals in North American organizations, the researchers concluded that smaller organizations could achieve a return on investment (ROI) of nearly 70 percent and larger organizations could achieve an ROI of 500 percent, on average, by implementing security awareness training. 11
Deficiencies in Current Learning Techniques
The importance of cybersecurity awareness is underscored by reports of incidents attributed to careless human behavior and lack of training, which continue to rise at alarming rates, despite commitments from small and large organizations to increase staffing in information security support groups and expand cybersecurity technology budgets. Many organizations either underestimate the effort needed to educate a workforce or do not realize that their current cybersecurity training approaches are ineffective.
KnowBe4’s 2021 State of Privacy and Security Awareness Report notes that a large percentage of surveyed employees did not feel confident that they could identify a social engineering attack, recognize the warning signs that their computers were infected with malware or describe to their senior management the security risk associated with employees working from home. 12 Government, healthcare and education employees were the least aware of various social engineering threats.
Much of the current literature and research on improving cybersecurity awareness training is focused on how to develop an effective program or how to identify the components missing from a program. This is a great start, but it is not enough. For example, the 2021 SANS Security Awareness Report: Managing Human Cyber Risk 13 identifies which needs to prioritize while building an effective program, such as having several full-time employees focused on changing behavior, providing job titles commensurate with responsibilities, ensuring leadership support, fostering collaboration among departments and engaging people with specialized communication skills to strike the right balance by not being too technical or lengthy with organizational messaging.
Conspicuously missing from many current reports, including the ones already mentioned, are inquiries into whether both the training material content and its delivery are inherently flawed. Something is lacking in the current environment. Could it be related to the technique, or lack of it, in delivering cyberawareness material within organizations? Are some approaches more effective? Do people learn, absorb and remember better when material is presented a certain way?
For example, the SANS Security Awareness Maturity Model (figure 3) gives organizations the ability to compare and contrast the maturity level of their security awareness program and helps them focus on areas that need improvement. 14 However, the model could be made even more helpful if it included references to how organizations can apply research on how humans learn and the most effective methods of content delivery. Organizations that do this should be rated higher on the maturity scale.

Many organizations either underestimate the effort needed to educate a workforce or do not realize that their current cybersecurity training approaches are ineffective.
Models and frameworks are a great start, but developing a structured awareness program with tools for metrics monitoring only solves part of the puzzle. Organizations also need research-based information on how to create inspiring content, along with techniques for delivering it effectively.
Better Ways to Learn
Review of the literature on how humans learn and retain information reveals interesting techniques and practices that are applicable to cybersecurity awareness and training campaigns. Organizations looking to maximize return on investment when it comes to cyberawareness would do well to take a closer look at adopting some of the following into their own learning systems.
Distributed vs. Massed Practice There may be benefits to moving away from training assignments that offer a single, continuous training session. Offering an initial fact-sharing or concept-learning session followed by periodic reviews may be a better approach. Research indicates that providing the same information after the initial session in smaller chunks and at a carefully chosen frequency reinforces learning. 15 Short, spaced-out study sessions lead to meaningful learning, whereas cram sessions often lead to nothing deeper than memorization.
In a 2019 interview, a researcher at Dartmouth College, Hanover, New Hampshire, USA, said that studying information or practicing a task just once is not good enough. 16 For permanent learning, the timing of the review or practice of the information is critical. Distributed practice refers to studying the material to be learned at a specified time after the original learning event. Massed practice, on the other hand, refers to study sessions that happen right after the original learning event.
Research shows that distributed lessons improved elementary school children’s ability to generalize their learning 17 and that when faced with unique situations, college students who participated in a spaced review following the primary lecture adapted better than students who just received a massed online review. 18
Conspicuously missing from many current reports… are inquiries into whether both the training material content and its delivery are inherently flawed.
Distributed reviews of the same information make the technique effective. It is not the same as spreading different chunks of material over several sessions or days. Organizations that comprehend the advantages of distributed practice over massed practice may choose to drop the idea of holding annual or quarterly cybersecurity awareness training events—that is, cram sessions—that take all day or multiple days, usually with exercise sessions on learning objectives at the end. A better approach may be to opt for short sessions that introduce the idea of a single cybersecurity concept, say phishing, followed by defined, specific breaks of days or weeks before the same concept is revisited in the form of multiple follow-up sessions or a set of spaced-out exercises emailed to the participants. The examples in figure 4 illustrate the differences between the two approaches.

Massed practice, or the boot camp approach, may work to some extent for achieving a short-term goal such as passing an exam. However, for employees to achieve long-term retention of learned concepts—something that is of vital importance to organizations when it comes to cybersecurity—distributed practice is a superior method of learning.
Reconsolidation Tweaking a distributed practice approach to include memory reconsolidation can make training more effective. Although distributed practice involves presenting the same information, a small alteration of facts or measures reinforces the training. The key is to combine distributed practice with subtle changes in the follow-ups.
Making slight changes to the study material or task during practice sessions may help trainees master a skill much more quickly than they would without alteration. The results of a study by researchers at Johns Hopkins University, Baltimore, Maryland, USA, lends credence to the theory of reconsolidation by showing that motor skills are strengthened when existing memories are recalled and modified with new knowledge. 19 The researchers found that the gains in performance such as speedier and more accurate task completion nearly doubled in the experimental group given an altered second session, compared to a group that repeated the same task without any change. The researchers concluded that a trainee learns more and learns faster by practicing a subtly altered version of a task than by practicing the same thing multiple times in a row. However, the changes in the training must be subtle because if the modification renders the task noticeably different, trainees do not realize the desired gain.
The science behind reconsolidation is still subject to debate, but results so far offer a glimpse of the possibilities for using it to strengthen learning. Consolidation refers to how the human brain learns new material. Retrieving that material after first exposure but before the learner has had a chance to forget it reactivates the learning process. It theoretically gives the learner an opportunity to weaken or strengthen memory retention. It appears possible to disrupt or impair retention by providing conflicting or incorrect information after an initial learning event or to strengthen it by providing correct information with slight updates. The updates might help to close gaps in the initial learning experience, thereby strengthening it.
For example, when using the distributed practice approach to teach employees about phishing, it might be beneficial to use the principles of reconsolidation in the follow-up sessions by subtly changing the phishing scenarios in the exercises. Each social engineering red flag ( figure 5 ) in the set might be used to introduce a slight variation to the initial learning session to reinforce the main learning subject of phishing.

The Value of Case Studies
Nothing raises cybersecurity awareness more effectively than showing the aftermath of real breaches in targeted enterprises and highlighting how vulnerable all organizations are to cyberthreats. One well-known and effective training technique is the use of case studies in problem-based learning (PBL) scenarios. The results of multiple studies indicate that PBL has a significant positive effect on students’ skill development and knowledge retention. 20 The US National Center for Case Study Teaching in Science polled more than a hundred university faculty members who had been trained to use case studies and found that more than 90 percent reported that students who were taught using sample cases learned new ways to think about issues and took an active part in the learning process. 21
Key characteristics of a good discussion case include being concise; being somewhat controversial to grab attention, but maintaining balance and not getting carried away; having memorable characters act out the case study with dialogue; ensuring that the subject material is relevant to the learners; presenting a dilemma to be solved; being contemporary rather than purely historical; using real rather than fabricated scenarios and having clear learning objectives.
Additional research expands on the qualities that make a good case study, 22 including being pertinent to the class and learning objectives, 23 being connected to theory and practice 24 , 25 , 26 and telling a story containing some form of ambiguity. 27
Information security officers struggling to sell internal leadership and stakeholders on abstract concepts such as segregation of duties (SoD), change management and other internal IT controls might find that case studies based on events in the news are effective tools to get their message across.
For example, a complete case study on the Bernard Madoff financial scam—complete with short news video clips and government press releases on IT personnel being charged with crimes—helped illustrate complex topics in an easy-to-understand format for the leadership at a not-for-profit and get its buy-in for implementing organizationwide checks and balances ( figure 6 ).
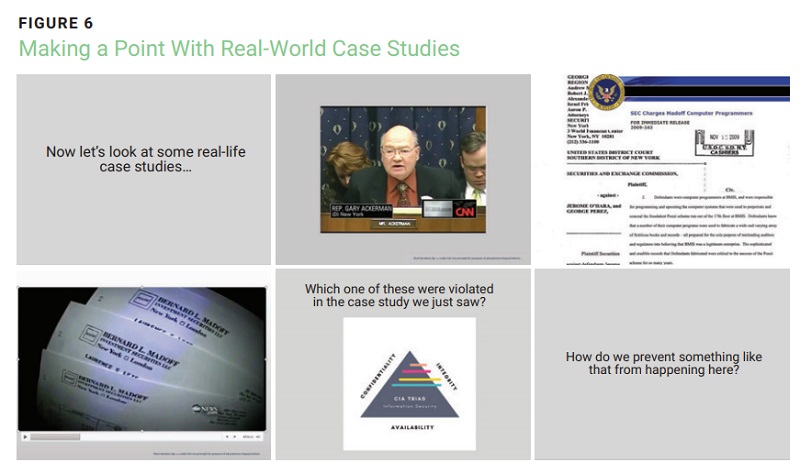
Learning From Incidents and Accidents Industrial accidents have been studied and analyzed over many decades, and learning from these incidents that inevitably occur in large systems—especially ones that pose a danger to human safety, such as those that occur with chemicals and other hazardous materials—has always been a top priority. By establishing a framework for learning from incidents, an organization can reduce risk and minimize loss and, thus, become a more reliable organization over time. Learning from incidents and accidents fosters a culture of continuous organizational improvement that will reduce incident severity and risk of disaster. Organizations that do not learn from past errors are doomed to repeat them, for example:
- The US National Aeronautics and Space Administration (NASA) lost two space shuttles, the Challenger in 1986 and the Columbia in 2003. The Columbia Accident Investigation Board noted that “[T]he causes of the institutional failure responsible for Challenger have not been fixed. Second, the Board strongly believes that if these persistent, systemic flaws are not resolved, the scene is set for another accident.” 28
- Failure to learn was among the causes for the Deep Water Horizon disaster. British Petroleum had experienced several major incidents before— specifically the Grangemouth refinery incident in Scotland, the Texas City refinery explosion in the US state of Texas, and the Prudhoe Bay leaks in the US state of Alaska. 29
Incidents, however, do not always have to end in disaster. 30 A system can be put in place to control their severity. It is important to recognize that, in most cases, a disaster results from a chain of events going undetected rather than from a standalone, spontaneous event. If an effective learning system could detect the incident, the chain of events could be broken and a disaster could be prevented.
By establishing a framework for learning from incidents, an organization can reduce risk and minimize loss and, thus, become a more reliable organization over time.
In addition to implementing systems that enable learning from incidents, technology organizations should investigate the use of mitigating systems, including a sort of kill switch that could potentially prevent an incident from becoming a disaster. One IT organization that suffered a series of ransomware events used data security software to study the data from the incidents and determined that all the attacks originated from end-user workstations and spread to network shares before showing up on assets of higher value. 31 A mitigating system using the data security platform was soon put in place so that ransomware activity detected at the end-user’s virtual local area network (VLAN) would automatically disable the user account the questionable activity was operating under and close ports to other parts of the network. Other examples of mitigating systems are automatic blocking of remote Internet Protocol (IP) addresses based on scanning activity detected by a security information and event management (SIEM) tool and automatic disabling of user accounts flagged as exhibiting unusual activity by other security tools.
In IT, especially cybersecurity, distilling the data collected from past incidents and accidents into actionable, effective training remains a challenge.
Organizations other than typical industrial factories have already adopted techniques to prevent incidents from descending into chaos and disaster. In the mid-1980s, researchers at the University of California, Berkeley, USA, began taking a closer look at why some organizations, despite their complex and risk-prone environments, continued to succeed in avoiding major safety incidents. 32 The term high reliability organizations (HRO) soon evolved to refer to this category of organizations. Researchers discovered that HROs use several tools and initiatives to learn from safety incidents, some of which could be adapted for use in healthcare, for example. 33 The researchers conducted a systematic review to identify effective learning tools that multidisciplinary teams in healthcare could adapt and use following a patient safety incident. IT-reliant organizations are on the cusp of facing major disasters; the attempted poisoning of city water in Oldsmar, Florida, USA, 34 and the Colonial Gas pipeline ransomware event are early warning signs. 35 If IT does not invest in learning systems championed by industries other than IT over the years, catastrophes will become inevitable.
Sometimes lessons are not learned. This can happen for various reasons, including the handling of information within and between organizations in a way that discourages dissemination of lessons learned from emergencies, training and educational programs, placing an unhealthy emphasis on what to learn rather than how to learn and ingrained organizational cultures preventing learning. 36
Recommendations for avoiding these traps include creating an official policy for identifying and learning lessons, developing techniques to identify and learn lessons from mock exercises and major emergencies, and engaging in an ongoing process of cross-training so that diverse teams can fully develop a broad understanding of how other teams think and operate under pressure. Data from the incident learning system can be applied in future training sessions. 37
Safety-conscious industrial organizations, often under the watchful eye of regulators, have long prioritized collecting data about accidents and feeding them into learning systems that are then converted to simulations used in training. Although the typical IT organization may not have as many situations that could affect human safety as other industry sectors, IT in general is known for having a culture of investigating failures and conducting root-cause analyses. However, in IT, especially cybersecurity, distilling the data collected from past incidents and accidents into actionable, effective training remains a challenge.
For example, one organization responded to the challenge by converting root-cause analysis of its actual cybersecurity incidents into animated training simulations that were then emailed out as quarterly or annual retrospectives (figure 7) . IT personnel received a more detailed tear-down of the incidents using the same animation medium.

Despite investing in training, technology and technical know-how and expanding their budgets to support ever-increasing information security operational costs, organizations are still falling victim to cyberattacks every day. These attacks show no sign of slowing down. Checkpoint research reported 900 weekly attacks per organization in 2021, a 50 percent jump compared with 2020. 38
Organization leaders need to realize that cybersecurity awareness is not just about training nontechnical employees about phishing and online scams and then arming them with better security practices. Cybersecurity awareness also plays a vital role in changing an organization’s culture for the better by changing certain behaviors (e.g., leaky change management practices; arming people with the data to make better decisions; providing the confidence and means to challenge unethical behavior, such as a senior manager falsifying disaster-recovery test results). The server left unpatched, the files left unprotected and the critical security feature, which took nine months to roll out, reflect organizational cultures that are in dire need of reform.
To create lasting change, organizations must not only build the components of an effective cyberawareness program, but also improve the quality of their content and the mechanisms for its delivery. Informed by research concerning how humans learn, organizations can adopt the most effective techniques to aid the developers of their training systems. With the right tools, developers can tailor content that improves employees’ learning speed and information retention and help employees adapt quickly to changing environments and situations, even during times of heavy workload and high pressure.
Author’s Note
The information and views expressed in this article are those of the author and do not constitute any official position, policy or pronouncement of his employer.
1 SonicWall, 2021 SonicWall Cyber Threat Report , USA, 2021, https://www.sonicwall.com/resources/white-papers/2021-sonicwall-cyber-threat-report/ 2 Ibid. 3 Morgan, S.; “Cybercrime to Cost the World $10.5 Trillion Annually by 2025,” Cybercrime Magazine , 13 November 2020, https://cybersecurityventures.com/hackerpocalypse-original-cybercrime-report-2016/ 4 KnowBe4 , 2021 State of Privacy and Security Awareness Report , USA, 2021, https://www.knowbe4.com/hubfs/2021-State-of-Privacy-Security-Awareness-Report-Research_EN-US.pdf 5 Malwarebytes, Enduring From Home: COVID-19’s Impact on Business Security , USA, 2020, https://www.malwarebytes.com/resources/files/2020/08/malwarebytes_enduringfromhome_report_final.pdf 6 Kaspersky, “The Human Factor in IT Security: How Employees Are Making Businesses Vulnerable From Within,” Kaspersky Daily, https://www.kaspersky.com/blog/the-human-factor-in-it-security/ 7 Verizon, 2021 Data Breach Investigations Report , USA, 2021, https://enterprise.verizon.com/content/verizon-enterprise/us/en/index/resources/reports/2021-data-breach-investigations-report.pdf 8 Willis Towers Watson, Cyber Claims Analysis Report , United Kingdom, 2020, https://www.wtwco.com/en-NZ/Insights/2020/07/cyber-claims-analysis-report 9 Ibid. 10 Osterman Research, Inc., The ROI of Security Awareness Training , USA, August 2019, https://www.mimecast.com/resources/analyst-reports/osterman-research---the-roi-of-security-awareness-training/ 11 Ibid. 12 Op cit KnowBe4 13 DeBeaubien, ; L. Spitzner; H. Xu; N. Zhang; 2021 SANS Security Awareness Report: Managing Human Cyber Risk , USA, 2021, https://www.sans.org/security-awareness-training/resources/reports/sareport-2021/ 14 SANS, “Measuring Program Maturity,” https://www.sans.org/security-awareness-training/resources/maturity-model/ 15 Carpenter, K.; N. J. Cepeda; D. Rohrer;H. K. Kang; H. Pashler; “Using Spacing to Enhance Diverse Forms of Learning: Review of Recent Research and Implications for Instruction,” Educational Psychology Review , vol. 24, iss. 3, http://www.jstor.org/stable/43546797 16 Francisco, A.; “Ask the Cognitive Scientist: Distributed Practice,” Digital Promise, 8 May 2019, https://digitalpromise.org/2019/05/08/ask-the-cognitive-scientist-distributed-practice/ 17 Vlach, H.; C. Sandhofer; “Distributing Learning Over Time: The Spacing Effect in Children’s Acquisition and Generalization of Science Concepts,” Child Development , 22 May 2012, https://ncbi.nlm.nih.gov/pmc/articles/PMC3399982/ncbi.nlm.nih.gov/pmc/articles/PMC3399982/ 18 Kapler, ; T. Weston; M. Wiseheart; “Spacing in a Simulated Undergraduate Classroom: Long-Term Benefits for Factual and Higher-Level Learning,” Learning and Instruction , April 2015, https://www.sciencedirect.com/science/article/abs/pii/S0959475214001042?via%3Dihub 19 Wymbs, N.; A. Bastian; P. Celnik; “Motor Skills Are Strengthened Through Reconsolidation,” Current Biology , 8 February 2016, https://www.sciencedirect.com/science/article/pii/S0960982215015146 20 Herreid, ; “Using Case Studies to Teach Science,” American Institute of Biological Sciences, 2005, https://files.eric.ed.gov/fulltext/ED501359.pdf 21 Herreid, ; “Case Studies in Science–A Novel Method of Science Education,” Journal of College Science Teaching , February 1994, https://eric.ed.gov/?id=EJ487069 22 Anderson, ; “Teaching Developmental Theory With Interrupted Video Case Studies,” Journal of the Scholarship of Teaching and Learning , December 2019, https://scholarworks.iu.edu/journals/index.php/josotl/article/view/25385/3711 23 McFarlane, D.; “Guidelines for Using Case Studies in the Teaching-Learning Process,” College Quarterly , Winter 2015, https://files.eric.ed.gov/fulltext/EJ1070008.pdf 24 Anderson, B.; S. Bradshaw; J. Banning; Using Interrupted Video Case Studies to Teach Developmental Theory: A Pilot Study , Gauisus, 2016, https://sotl.illinoisstate.edu/downloads/gauisus/AndersonVolume4.pdf 25 Penn, ; C. Currie; K. Hoad; F. O’Brien; “The Use of Case Studies in OR Teaching,” Higher Education Pedagogies, 8 March 2016, www.tandfonline.com/doi/full/10.1080/23752696.2015.1134201 26 Prud’homme-Généreux, A.; “Case Study: Formulating Questions That Address Student Misconceptions in a Case Study,” Journal of College Science Teaching , March 2017, https://eric.ed.gov/?id=EJ1136640 27 Boston University Center for Teaching and Learning, Massachusetts, USA, “Using Case Studies to Teach,” https://www.bu.edu/ctl/teaching-resources/using-case-studies-to-teach/ 28 Columbia Accident Investigation Board, Report Volume I, USA, August 2003, http://s3.amazonaws.com/akamai.netstorage/nasa-global/CAIB/CAIB_lowres_full.pdf 29 Dechy, N.; J. Rousseau; F. Jeffroy; “Learning Lessons From Accidents With a Human and Organisational Factors Perspective: Deficiencies and Failures of Operating Experience Feedback Systems,” EUROSAFE Forum 2011, researchgate.net/publication/233997934 30 Cooke, ; T. Rohleder; “Learning From Incidents: From Normal Accidents to High Reliability,” System Dynamics Review , September 2006, https://onlinelibrary.wiley.com/doi/10.1002/sdr.338 31 Varonis, Varonis Case Study: City of San Diego, USA, https://info.varonis.com/hubfs/docs/case_studies/en/Varonis_Case_Study_San_Diego.pdf 32 Roberts, K. H.; “HRO Has Prominent History,” Anesthesia Patient Safety Foundation Newslette r, 18, iss. 1, Spring 2003, https://www.apsf.org/article/hro-has-prominent-history/ 33 Serou, ; L. Sahota; A. Husband; S. Forrest; Slight; S. Slight; “Learning From Safety Incidents in High-Reliability Organizations: A Systematic Review of Learning Tools That Could Be Adapted and Used in Healthcare,” International Journal for Quality in Health Care , 17 March 2021, https://academic.oup.com/intqhc/article/33/1/mzab046/6174559 34 Staff, “‘A Matter of National Security: FBI, Secret Service Investigate After Hacker Tried to Poison a Florida City’s Water With Lye,” USA Today , 9 February 2021, https://www.usatoday.com/story/news/nation/2021/02/09/oldsmar-florida- water-hacker-lye-sodium-hydroxide/4444387001/ 35 Turton, W.; K. Mehrotra; “Hackers Breached Colonial Pipeline Using Compromised Password,” Bloomberg, 4 June 2021, https://www.bloomberg.com/news/articles/2021-06-04/hackers-breached-colonial- pipeline-using-compromised-password 36 Coles, E; “Learning the Lessons From Major Incidents: A Short Review of the Literature,” Emergency Planning College , June 2014 37 Ibid . 38 Check Point Research, “Check Point Research: Cyber Attacks Increased 50 Percent Year Over Year,” 2022, https://blog.checkpoint.com/2022/01/10/check-point-research-cyber- attacks-increased-50-year-over-year/
Ranjit Bhaskar, CISA, CISM, CISSP
Is a senior security architect at Texas Windstorm Insurance Association (TWIA). Bhaskar has 25 years of experience in enterprise architecture and is the author of the op-ed, “A Cybersecurity Culture Score.” He can be reached via LinkedIn at https://www.linkedin.com/in/ranjit-bhaskar-467877218 .
| You might be using an unsupported or outdated browser. To get the best possible experience please use the latest version of Chrome, Firefox, Safari, or Microsoft Edge to view this website. |
Cybersecurity Awareness: What It Is And How To Start

Updated: Mar 16, 2022, 12:46pm

Every October, cybersecurity professionals and enthusiasts alike observe Cybersecurity Awareness Month. Backed by the Cybersecurity & Infrastructure Security Agency (CISA) and National Cyber Security Alliance , Cybersecurity Awareness Month encourages individuals and organizations to own their role in protecting their part of cyberspace.
For many organizations, it’s the perfect time to celebrate cybersecurity awareness and jump-start a training program with the countless resources available. But before we dive into how to use this Cybersecurity Awareness Month to your advantage, we first must understand the role of cybersecurity awareness in keeping your employees and organization safe.
What is Cybersecurity Awareness?
Cybersecurity awareness involves being mindful of cybersecurity in day-to-day situations. Being aware of the dangers of browsing the web, checking email and interacting online are all components of cybersecurity awareness. As business leaders, it’s our responsibility to make sure everyone considers cybersecurity an essential part of their role.
Not everyone in an organization needs to understand concepts like SPF records and DNS cache poisoning, but empowering every employee with information relevant to their role helps them stay safe online—both at work and home. Role-based training for technical and non-technical staff is the best way to prepare the right people for the right cybersecurity threats.
Cybersecurity awareness could mean something a bit different to your general workforce than it means to technical teams. Management of data, permissions and regulations are topics that your IT team needs to know but aren’t necessarily relevant to the rest of your organization. Delivering the appropriate training to each team is vital to building a cybersecurity awareness program that motivates lasting behavior change.
Why is Cybersecurity Awareness Important?
Similar to safety incidents, cybersecurity incidents can come with a hefty price tag. If you’re struggling to allocate budget to cybersecurity training, tools or talent, you should think about it through the lens of risk management. With an ever-rising number of cyberattacks each year, the risk of not educating your employees on cybersecurity awareness only continues to grow.
Cybercriminals are constantly finding new ways to circumvent the latest defensive tools and technologies, landing themselves in the inboxes and browsers of your employees. In 2021 alone, 85% of data breaches involved the human element, with 94% of malware delivered via email.
These email attacks almost always involve some sort of phishing. Phishing is the fraudulent practice of sending emails posing as a legitimate source to compel victims to reveal sensitive information, such as passwords and credit card numbers. You may have seen phishing emails before, offering you a free TV or asking you to change your password. While an email spam filter will catch many of these, some will still occasionally make it through to your inbox.
Not only is phishing a simple attack to perform, but it’s a Google search away. Anyone who can access the dark web can purchase a phishing kit the way you’d buy a book from Amazon. Your employees will eventually come face-to-face with a cyber incident, and you’ll want them to be prepared to respond accordingly by reporting threats to your IT or security team. Luckily, cybersecurity awareness training can be an effective defense against phishing attacks.
Defending against phishing and social engineering attacks ultimately comes down to knowing what you’re up against. These can come in several forms, but the most common cyber attacks are phishing emails that ask you for usernames, passwords and personally identifiable information (PII). A good rule of thumb is to have healthy skepticism whenever an email asks for personal information—especially emails from an unexpected sender.
This can sound like quite the daunting task for any company, let alone a small business. The reality is that the opportunity cost of not training your employees is too high to ignore. According to IBM , the average cost of a data breach last year was $4.24 million. Thirty-eight percent of companies lost business as a result of a breach, which accounted for over half of the total financial losses.
By training your workforce to identify these attacks, you can significantly reduce the risk of a security incident or breach. This can be the difference between an expensive ransomware infection and a message to your IT department that reads, “This email looks suspicious, so I didn’t open it.”
From Awareness to Culture
While cybersecurity awareness is the first step, employees must willingly embrace and proactively use cyber-secure practices both professionally and personally for it to truly be effective. This is known as a culture of security or security culture. Security culture is defined as an organization’s collective awareness, attitudes and behaviors toward security. ISACA and CMMI Institute studies have shown that organizations with strong cybersecurity cultures experience increased visibility into potential threats, reduced cyber incidents and greater post-attack resilience, among other measurable benefits.
We can all learn from organizations that have heavily invested in building cultures of safety to drive down workplace incident rates. When organizations saw that safety incidents, similar to security incidents, were costly and dangerous, they invested in preventing them with employee education. For this to be effective, they had to go beyond awareness to ensure employees were embracing safety protocols as part of their workplace culture. Just like you wouldn’t enter a construction site without a hard hat today thanks to OSHA training, building a security culture will make common mistakes like reusing passwords or opening malicious files a thing of the past.
For security culture to be most effective, it’s important to make security training not only engaging but also relevant to employees so they understand how cybersecurity impacts them in and outside of work. Like learning how to bend with your knees, security education can help them at home as well. With today’s hybrid workforce, this mindset is more important than ever. As leaders, it is our role to connect the dots and help employees understand how security education benefits them. When you get there, you can create lasting behavior change and a culture of security.
What Can You Do to Get Started?
The best part about cybersecurity training is that it can be customized to your organization’s needs. From a formal security awareness training program to a monthly email with cybersecurity tips and tricks, any cybersecurity awareness and training can significantly impact employee behavior, and can even spur a cultural change in the way your employees view cybersecurity. The real change begins once the individuals buy into the idea that cybersecurity is one of their own job responsibilities.
When it comes to the bottom line, even a small investment into cybersecurity awareness training drives a positive ROI . The most effective programs take a people-first approach to security education. That means aligning training to specific roles, departments and cultures to boost engagement, training relevancy and, ultimately, lasting behavior change.
Many low-cost and free resources are available to help organizations get started with cybersecurity awareness training, especially during Cybersecurity Awareness Month. Every year, organizations like CISA and Infosec create free training kits that serve this exact purpose: to give you a place to start. These tools allow organizations to deliver training modules, assessments and newsletters to keep employees engaged all month long.
Once you get the ball rolling, consistency is key to keeping security top of mind for your organization all year long. Even a simple training module or a monthly newsletter goes a long way to preventing a cyber incident.
Moving forward, you can continue to find great resources on the Infosec resource center and the CISA website .
- Best Antivirus Software
- Best iPhone Antivirus Software
- Best Android Antivirus Software
- Best Mac Antivirus Software
- Best Free Antivirus Software
- Most Common Cyberthreats
- McAfee Antivirus Review
- Malwarebytes Premium Review
- Bitdefender Antivirus Review
- Norton Antivirus Review
- Avast Antivirus Review
- AVG Internet Security Review
- Kaspersky vs. Avast vs. Bitdefender
- Webroot vs. Bitdefender
- McAfee vs. Norton
- Malwarebytes vs. Avast
- Malwarebytes vs. Windows Defender
- Bitdefender vs. McAfee
Next Up In Business
- Best Phishing Simulators To Prepare Employees And Defend Your Network
- Top 5 Cybersecurity Questions For Small Businesses Answered
- What Is Zero-Trust Security, And Should Your Business Adopt It?

What Is SNMP? Simple Network Management Protocol Explained
What Is A Single-Member LLC? Definition, Pros And Cons
What Is Penetration Testing? Definition & Best Practices
What Is Network Access Control (NAC)?
What Is Network Segmentation?

How To Start A Business In Louisiana (2024 Guide)
Jack Koziol is president and founder of Infosec, a leading security awareness and anti-phishing training provider. With years of private vulnerability and exploitation development experience, he has trained members of the U.S. intelligence community, military and federal law agencies. His extensive experience also includes delivering security awareness and training for Fortune 500 companies including Microsoft, HP and Citibank. Jack is the lead author of The Shellcoder's Handbook: Discovering and Exploiting Security Holes. He also wrote Intrusion Detection with Snort, a best-selling security resource with top reviews from Linux Journal, Slashdot and Information Security Magazine. Jack has appeared in USA Today, CNN, MSNBC, Wall Street Journal and other media outlets for his expert opinions on information security.
Cassie is a deputy editor collaborating with teams around the world while living in the beautiful hills of Kentucky. Focusing on bringing growth to small businesses, she is passionate about economic development and has held positions on the boards of directors of two non-profit organizations seeking to revitalize her former railroad town. Prior to joining the team at Forbes Advisor, Cassie was a content operations manager and copywriting manager.

Schedule a demo
Schedule a cab demo, download the the state of security awareness training, download the phishing simulation playbook.

14 Cybersecurity Awareness Topics You Need to Cover
You might be surprised to discover that merely running cybersecurity awareness training programs for your staff is insufficient to foster a robust culture of awareness in your organization. Paying attention to the details of how the training works and the precise topics covered is what sets apart the most security-aware businesses.
With the cyber threat landscape evolving swiftly, training programs that stay the same over time become outdated quickly. Who had even heard of a double supply chain attack before 2023? The math is simple: a recent survey reported that over 80% of leaders say their company has a security awareness and training program, but over 50% believe their employees lack cyber awareness. Clearly, there are issues and shortfalls in the subjects covered by these programs.
Here are fourteen pertinent cybersecurity awareness topics your training program must cover to be effective.
Why Cybersecurity Awareness Training is Critical Today
In addition to the growing number and sophistication of cyber threats, many attacks target users directly, and many cyber mishaps stem from a lack of security awareness. The right cybersecurity awareness training is vital because a comprehensive, up-to-date program helps change employees from being a weak link to a human firewall that can identify and avoid many cyber attacks and breaches.
Most corporate leaders believe greater employee cybersecurity awareness would help reduce cyber attacks. Security awareness training offers an organization invaluable benefits, including:
- Educating your employees about an evolving threat landscape
- Helping them recognize the value of the data they handle and applying the best practices to protect it
- Mitigating financial losses
- Ensuring your employees understand their roles and responsibilities in compliance with regulations such as GDPR, HIPAA, and the Digital Operational Resilience Act (DORA)
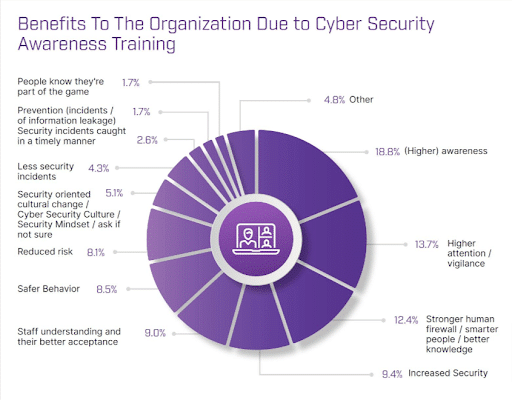
14 Cybersecurity Awareness Topics to Cover in Training
When choosing a training program, be sure that the following cybersecurity awareness topics are covered:
1. Phishing Awareness
Your employees need to know how to identify phishing attempts so they don’t get tricked by email scams that involve outsiders masquerading as trustworthy people or companies.
Points to teach in training modules include:
- Examine sender email addresses closely to check for any misspellings or slight deviations from the usual address.
- Scrutinizing URLs within emails before clicking on them.
- Look for phishing language signs, such as urgency, generic greetings, or poor spelling/grammar.
This topic should also cover fraudulent text messages ( smishing ) or phone calls (vishing) as other delivery methods for these scams. Include information about common phishing tactics, like fake job offers or mimicking legitimate organizations that recipients trust.
Pay attention to the growing problem of targeted spear phishing attacks focusing on specific individuals or roles within your company, such as impersonating a high-level executive or targeting finance teams.
The best way to train phishing awareness is through phishing simulations. CybeReady’s platform uses data-driven campaigns and adaptive training to help deliver phishing simulations that markedly improve the ability to identify and avoid phishing scams.
2. Password and Authentication Security
Convey to learners how solid and unique passwords combined with multi-factor authentication (MFA) significantly reduce the risk of unauthorized access to their accounts.
Even with billions of stolen credentials circulating on the dark web, hackers will struggle to get into an account protected by MFA because they’ll need to provide a second, distinct category of evidence beyond a password that proves their identity, such as biometrics or a one-time code sent to your employee’s phones.

Also, cover best practices for Single Sign-on (SSO) security to avoid account takeover (ATO) attacks targeting employees and customers.
3. Social Engineering Defense
Threat actors don’t limit themselves to traditional phishing scams when trying to dupe or manipulate people into revealing sensitive info, downloading malicious attachments, or clicking suspicious links. Practical training should run through the whole gamut of social engineering techniques that hackers could use, including pretexting, baiting, and tailgating.
Beyond understanding the many types of social engineering, teach employees how to verify identities and requests, especially in cases where those requests involve access to sensitive data or financial transactions.
4. Safe Internet Practices
Many cyber breaches stem from unsafe Internet practices. Ensure cybersecurity awareness training addresses best practices like trusting websites with secure HTTPS connections, not downloading files or software from untrusted sources, and being mindful of what information employees share on social media or networking platforms like LinkedIn.
Remind employees that many public Wi-Fi connections lack any security features, so encrypting the connection with a VPN is imperative if they must connect to those networks.
5. Email Security
Good email security awareness includes being cautious of attachments and links from unknown sources, using spam filters, and reporting suspicious emails. Also, teach employees about the risk of sharing sensitive information by email and the need for an encrypted connection.
6. Mobile Device Security
With the boundaries between personal and work life blurring, employees must understand how to securely use personal and company-provided mobile devices when accessing work-related information. This includes using the device’s basic security features, like setting a screen lock and promptly applying operating system security updates when notified.
Employees also need to Understand the risk of installing apps from unverified sources outside the usual app stores on these devices.
7. Data Protection and Privacy
Employees play a frontline role in safeguarding your company’s sensitive information. Awareness training should convey the importance of this function and help employees understand how to ensure data confidentiality, integrity, and availability.
Distinguish between different types of data to protect, such as Personal Identifiable Information (PII), Protected Health Information (PHI), and Intellectual Property (IP). Also, outline the legal consequences of data breaches. Round this training with secure practices like data minimization, encryption, and access control .
8. Malware and Ransomware
Awareness of malware and ransomware means knowing how malicious software can infect systems. The two most common ways are email attachments, and malicious or spoofed websites . Include other relevant topics like the danger of enabling Macros in Microsoft Excel or running executable files from unknown sources. Employees must also know what to do if they inadvertently install malware on their system.
9. Remote Working Security
With hybrid work now a mainstay option in many job roles, remote work security is more important than ever. A comprehensive approach includes tips on bolstering home Internet security by changing default router settings and updating firmware when available. Beyond the home Internet network, employees should know how to secure devices from theft or unauthorized access. Strong familiarity with your company’s remote work policy is also paramount.
10. Cloud Security
The average business now uses 371 SaaS apps, and the cloud revolution extends to cloud infrastructure and data storage. Employees who use any cloud service need to know about specific cloud security practices, such as:
- Only using vetted and approved apps.
- Sharing data securely.
- Using configuration management tools to avoid misconfigurations.
- Encrypting data before uploading it to cloud services.

11. Artificial Intelligence
The rapid proliferation of AI tools into many different roles creates opportunities, but it also comes with security concerns. Over 60% of knowledge workers use generative AI tools like ChatGPT in daily tasks.
AI cybersecurity awareness topics to teach employees include the danger of feeding confidential or sensitive data into these tools, and the use of generative AI by threat actors to create convincing phishing emails or other scams.
12. Physical Security
Somewhat surprisingly, physical security and cybersecurity are closely linked. Physical security lapses like letting strangers into the office, not disposing of printed sensitive info securely, or leaving workstations unlocked all pose cyber risks worth preventing.
Don’t forget that the boundaries between physical and digital security are blurring. IoT devices collect data from the physical world, and OT systems control physical processes. A security breach can have real-world consequences, so consider the best security practices for each if they apply to your business.
13. Incident Reporting Procedures
Any incident response plan should include procedures and steps to report security incidents. However, for this plan to be effective, your employees must know the exact steps they should take if they suspect a security incident. Your security awareness training needs to familiarize employees with whom to contact and what information to include if they need to report something suspicious.
14. Security Policies and Procedures
Lastly, include awareness training about your company’s specific security policies and procedures. These include regulatory requirements for the industry you operate in, acceptable use policies, how to classify and handle different types of data, and any policies about the use of personal devices for work reasons.
CybeReady: Proven Training with Up-to-Date Cybersecurity Awareness Topics
Ensuring that your team receives cybersecurity awareness training that covers a broad range of topics with the latest updates is essential to it being effective. But equally important is making sure that critical information is retained—and that comes down to how it’s taught.
CybeReady’s fully managed training solution leverages data to optimize the learning experience for every one of your employees. It takes a proven training approach to security awareness, with a continuous learning paradigm involving hands-on experience, a variety of training simulations, positive and short content, and immediate feedback—all designed for maximum engagement, retainment, and effectiveness.
Discover how CybeReady teaches the cybersecurity awareness topics you need by scheduling a free demo today.

Your Employees are Already Using GenAI. How Will You Communicate the Security Risks?
August 15,2024

Let the Games Begin! A Security Awareness Training (and a personal story) Inspired by the Olympic Spirit
May 19,2024

Jiu-Jitsu Principles in Security Awareness Training: A DevOps Engineer's Perspective
April 17,2024
Get the latest & greatest cybersecurity insights straight to your inbox:

Get the latest & greatest cybersecurity insights straight to your inbox:

- Take a Virtual Tour
- Security Awareness Bites
- Phishing Simulations
- Compliance Tool
- Elastic Security Program
- Banking Industry
- Education Industry
- Manufacturing Industry
- Pharmaceutical Industry
- Why CybeReady
- Partner Program
- CISO Toolkit
- HI-5 With A CISO
- Phishing Playbook
- Interactive Learning Kits
Copyright © 2024 – CybeReady
We will reach out to you shortly. In the meantime, please check out our complimentary CISO Tool Kit
We will reach out to you shortly. In the meantime, please check out our complimentary CISO Tool Kit , or visit Our Blog

An official website of the United States government
Here’s how you know
Official websites use .gov A .gov website belongs to an official government organization in the United States.
Secure .gov websites use HTTPS A lock ( Lock A locked padlock ) or https:// means you’ve safely connected to the .gov website. Share sensitive information only on official, secure websites.
Free Cyber Services #protect2024 Secure Our World Shields Up Report A Cyber Issue
CISA Cybersecurity Awareness Program
The CISA Cybersecurity Awareness Program is a national public awareness effort aimed at increasing the understanding of cyber threats and empowering the American public to be safer and more secure online. Cybersecurity is a shared responsibility and we each have a part to play. When we all take simple steps to be safer online – at home, in the workplace, and in our communities – it makes using the Internet a more secure experience for everyone.
This Program is part of an unprecedented effort among federal and state governments, industry, and non-profit organizations to promote safe online behavior and practices. It is a unique public-private partnership, implemented in coordination with the National Cyber Security Alliance.
More and more, Americans are using new technologies and spending more time online. Our growing dependence on technology, coupled with the increasing threat of cyberattacks, demands greater security in our online world. This presents the need for simple, easy-to-understand resources and tips to help ensure their safety and security.
The CISA Cybersecurity Awareness Program provides Americans access to the resources and tools they need to make more informed decisions when using the Internet.
Since 2004, the President of the United States and Congress have declared October to be Cybersecurity Awareness Month , helping individuals protect themselves online as threats to technology and confidential data become more commonplace. The Cybersecurity and Infrastructure Security Agency (CISA) and the National Cybersecurity Alliance (NCA) lead a collaborative effort between government and industry to raise cybersecurity awareness nationally and internationally.
Cybersecurity Awareness Month
Subscribe to the cisa community bulletin.
Sign up for the CISA Community Bulletin to learn how you can spread cybersecurity awareness across the country to people of all ages. Organizations and individuals will learn about CISA services, programs, and products and how they can use them to advocate and promote cybersecurity within their organizations and to their stakeholders.
Homeland Security Information Network - Critical Infrastructure
The Homeland Security Information Network (HSIN) is the trusted network for homeland security mission operations to share Sensitive But Unclassified (SBU) information . The Critical Infrastructure community on HSIN (HSIN-CI) is the primary system through which private sector owners and operators, DHS, and other federal, state, and local government agencies collaborate to protect the nation’s critical infrastructure. HSIN-CI provides real-time collaboration tools including a virtual meeting space, document sharing, alerts, and instant messaging at no charge.
CISA Cybersecurity Awareness Program Young Professional Resources
Cisa cybersecurity awareness program older american resources, cisa cybersecurity awareness program government resources, cisa cybersecurity awareness program small business resources, cisa cybersecurity awareness program law enforcement resources, cisa cybersecurity awareness program toolkit.

CISA Cybersecurity Awareness Program Student Resources

Cybersecurity Awareness Program Parent and Educator Resources
To learn more or get involved in the CISA Cybersecurity Awareness Program, please contact us at [email protected] .
- Engineering Mathematics
- Discrete Mathematics
- Operating System
- Computer Networks
- Digital Logic and Design
- C Programming
- Data Structures
- Theory of Computation
- Compiler Design
- Computer Org and Architecture
What is Cyber Security Awareness?
Cyber Security Awareness is a method to read the types of threats and implement the protection against such threats from the internet to protect our privacy and secure our data. Internet is used by us on regular basis and we all are aware of the security threats on the internet. We need to protect our privacy from such cyber attacks.
As the world of cyber is getting huge, the threats to us also increases on the regular basis and we need to be protective against such attacks. The internet and connectivity devices are making our life easier, but they also bring danger online.
A cyber security awareness is an important to protect our data from the cyber attacks, and unknown login. We need to get aware from the online threats like phishing and malware that cybercriminals use to steal our data. We need to identify and avoid frauds that are conducted online, via email, or on social media.
Importance of Cybersecurity Awareness
At earlier times, only the computer viruses were a problem but now we have antivirus software to protect us from them. But now the cyber threats have grown large and advanced that is becoming dangerous to all of us. Malware, phishing, DDoS attacks , data breaches and fraud email some common example where we trap ourselves and become a victim. Following are some points to know the importance of cybersecurity awareness :
- As the world of digital era is increasing, the cyber-attacks and threats are also increasing day to day and we need to be aware from such cyber threats and protect our data.
- Multiple malware, phishing, DDoS attacks, data breaches and fraud email are sent to user through the internet to access and breach their personal and professional data on daily basis.
- It is important to protect yourself from the various cyber threats such as phishing scams, malware attacks, and data breaches and protect our personal and professional data.
- We need our professional data to be Private and Confidential because the personal loss can be compromised at a stance, but professional data breach cannot only harm our self but can also damage the entire company by the cyber threats.
- Their is a huge risks of identity theft on the internet so it is important to keep our personal information safe and prevent identity fraud.
- It is seen that a lot of victims are made by making financial scams, fraud transactions and ransom attacks which causes a huge financial loss to the victim.
- We also need to Secure our digital assets and cybersecurity awareness helps us to do so by protecting our digital assets which includes email accounts, our social media profiles, and the online banking accounts from the cybercriminals.
Cybersecurity Threats
- There are a lot of cyber threats that an individual needs to know about to ignore the cyber threats. Cybercriminals could any one of them to trap a victim. We carefully need to know about such threats that are commonly known as malware, phishing, and email spamming.
- Malwares are the hidden and very dangerous malicious software that can cause severe damage to our system and could help criminals gain unauthorized access to our computer.
- Phishing is a huge cyber-attack in which our sensitive information such as passwords, credit card numbers, or personal data saved into our system is taken by the cyber criminals.
- Whereas in email spamming, a large amount of Spam emails that are of no use to us are often sent which contain misleading information and are sent to trap the user and steal their data.
- Cybercriminals is always looking for poor victims who they can trap easily. They always try to find new ways to break into an individual system and if they find a problem with software or the server, or old systems with known issues, they easily break into the system and steal the information. They look for weak passwords, Un updated apps, or old operating systems which help them to hack the system easily. People are tricked too because people aren’t careful while checking their system.
- The cyber-attacks can be very dangerous if they steal our identity or we lose our money through fraud calls or if leaks our private information. It can cause huge problems like it can ruin our reputation or give us economic struggle or we get into serious legal trouble.
Impact of Cyber Threats
- A large amount of financial fraud has been seen in the growing past years that has been made through hacking, identity theft and money scams. These financial losses haven’t only affected the lives of million of people but also had given a very bad impact on the country’s economy.
- The most cyber threats are made to people to interrupt their privacy and steal their personal and professional data. This is a serious matter of concern because it has made people chose the wrong track for their future. The breach in privacy left them no choice than choosing the wrong path and they are asked to do illegal jobs in return.
- Due to increase in cyber-attacks and threats to people, the government need to spend more on cybersecurity measures day by day which is creating a new problem to government.
- The increase in cyber threats have also made the loss of trust between people, whether it is between a boss or employee to the consumer and shareholder of the company which causes a huge reputation damage and reduce the market value of both the companies and governments.
- Their is a regular pressure on the government about the cyber threats due to which strict data protection laws are implemented for the better cybersecurity practices of the people and the companies. This increases the costs of making new organizations and pay the government for them.
Protection from Cyber Threats
- We need to get very conscious about the malware, phishing, DDoS attacks , data breaches and fraud email because they are the first weapon used by cyber criminals to attack into our system. We always need to check the sources of links sent to us and the mail we are receiving, if it’s suspicious we need to spam the mail. We need to be also careful about malware application because they can steal hefty of our data from the system.
- We should always Use strong and complex passwords for our login accounts that are made with several combinations so that they cannot be broken easily by the cyber criminals and we can stay safe from them.
- We should enable Two-Factor Authentication (2FA) wherever possible because it gives us an extra protection from the hackers and secure our data. It can also inform us about an unidentified login to any of our accounts which can help us to block them.
- It is mandatory to keep the software updated of the application we are using to access our login because the updated version always help us to protect us from such cyber activity.
- We should try to use the secure networks rather than the public network or open network that can help the cyber criminals to access and attack on our system and steal our data.
- We need to secure our devices by Installing regular security updates software on all our devices and we need to protect our data by using firewalls and encryption.
- It is important to Stay Informed about the latest cybersecurity news and trends by following reputable sources for information and know about the necessary security measures from them.
- We need regular backups of our important files and data to protect them against data loss in case of our system failure or any cyber-attack on us.
- It is recommended to only visit the official websites and be aware and informed while downloading files or clicking on the ads shown online. We should avoid visiting suspicious or potentially malicious websites which can cause virus and steal our data.
Frequently Asked Questions on Cyber Security Awareness – FAQs
How can we get protected from the cyber-attacks.
We need to get very conscious about the malware, phishing, DDoS attacks, data breaches and fraud email because they are the first weapon used by cyber criminals to attack into our system. We always need to check the sources of links sent to us.
What are the 6 tips of cyber security awareness?
We can be aware by using Two-Factor Authentication (2FA), use the secure networks, Stay Informed about the latest cybersecurity news, Use strong and complex passwords etc.
Please Login to comment...
Similar reads.
- Cyber-security
Improve your Coding Skills with Practice
What kind of Experience do you want to share?
- Search Menu
- Sign in through your institution
- Editor's Choice
- Author Guidelines
- Submission Site
- Open Access
- About Journal of Cybersecurity
- Editorial Board
- Advertising and Corporate Services
- Journals Career Network
- Self-Archiving Policy
- Journals on Oxford Academic
- Books on Oxford Academic

Article Contents
Introduction, related works, research methodology, data collection and analysis, factors evaluated, metrics development, conclusions, acknowledgements, developing metrics to assess the effectiveness of cybersecurity awareness program.
sunil.chaudhary, vasileios.gkioulos, [email protected]
- Article contents
- Figures & tables
- Supplementary Data
Sunil Chaudhary, Vasileios Gkioulos, Sokratis Katsikas, Developing metrics to assess the effectiveness of cybersecurity awareness program, Journal of Cybersecurity , Volume 8, Issue 1, 2022, tyac006, https://doi.org/10.1093/cybsec/tyac006
- Permissions Icon Permissions
Cybersecurity awareness (CSA) is not just about knowing, but also transforming things learned into practice. It is a continuous process that needs to be adjusted in subsequent iterations to improve its usability as well as sustainability. This is possible only if a CSA program is reviewed and evaluated timely. Review and evaluation of an awareness program offer an insight into the program's effectiveness on the audience and organization, an invaluable piece of information for the continuous improvement of the program. Further, it provides the information required by the management and sponsor to decide on whether to invest in the program or not. Despite these advantages, there does not exist a common understanding of what factors to measure and how to measure them during the evaluation process. As a result, we have proposed evaluation metrics for the purpose. In order to do so, we performed a literature review of 32 papers mainly to extract the following data: (i) what factors did the paper measure, and (ii) how did it measure the factors? Next, we adapted the European Literacy Policy Network's four indicators (i.e. impact, sustainability, accessibility, and monitoring) for awareness evaluation to make it appropriate for evaluating a CSA program. We believe that measuring all four indicators will contribute to making the evaluation process systematic, complete, and replicable. More importantly, it will help to produce more inclusive, accurate, and usable results for the future enhancement of the program.
Cybersecurity is not just about technology, but it also includes the people who interact with technology and are responsible for properly implementing and operating it. Many past studies [ 1–3 ] have identified people's behaviors and actions to be responsible for most cybersecurity incidents. This could be a reason why ‘ people ’ is considered the weakest link among the people-process-technology triad of cybersecurity. As the first step in handling human factors, raising the cybersecurity awareness (CSA) of people is of paramount importance.
CSA combines both gains in knowledge and positive changes in attitudes and behaviors (KAB) [ 4–7 ] that protect systems, data, and information from cyber threats. The learning achieved from CSA activities is not detailed or in-depth knowledge but only enough information to direct the attention of individuals to security issues, perceive their potential implications, and act responsibly (or make informed decisions) [ 6 , 8, 9 ]. This is done by communicating the needed security information to the participants in a way so that they develop a healthy level of skepticism and motivation to act when encountering unusual situations [ 10 ]. Practically, this encompasses different dimensions, such as
Make people realize that there are cyber risks and threats to which they are vulnerable.
Alert people about the harmful implications of cyber threats.
Draw people's attention to potential threat actors, ways they might or do target their victims, and critical assets they are interested in.
Impart information about signs and mechanisms to identify cyber threats.
Inform people about the existing security measures (tools, policies, procedures, guidelines, standards, regulations, laws, strategies, and practices) that can counteract the relevant cyber threats.
Motivate people to timely use security measures to mitigate cyber threats.
Make people understand the importance of cybersecurity and their obligations toward it.
CSA is a continuous process, and it is most effective when performed iteratively and focused on continuous improvement [ 4 , 11 ]. It must comprehend factors like the evolving cyber threat landscape, advancements in technology, and shifts in an organization's missions and priorities to stay relevant to the target audience and optimized for the organization. But this is possible only if CSA programs are reviewed and evaluated for their effectiveness. Review and evaluation aim at evaluating the effectiveness of the undertaken iteration according to a set of pre-defined metrics, demonstrating in this way the achieved return on investment (ROI). Further, they facilitate the assessment of the program's suitability and the necessary enhancements for future iterations (e.g. weaknesses in content quality, delivery channels, and others). In other words, the results and measurements of a review and evaluation can act as critical indicators for future planning, updates, and improvement of a CSA program.
Over the last few years, several assessments, broadly categorized as output and outcome of the program [ 12 ], have emerged that can be used as indicators of the effectiveness of CSA programs. Many past studies depend on measuring and assessing one or more of the following factors to evaluate the effectiveness of a CSA program: (i) the audience interest in CSA programs generally quantified in terms of the number of participants, (ii) the reduction in the cybersecurity incidents occurred after the program, and (iii) the change in the audience's perception, knowledge, attitude, and behavior [ 13 ]. Although the first parameter is simple and demonstrates the audience's satisfaction or dissatisfaction with a CSA program, it does not convey whether the awareness program made any real difference in practice. Similarly, the second parameter cannot confirm whether the improvement in cybersecurity incidents results from a CSA program or has occurred simply because of a decrease in cyberattacks impacting the audience after implementing a better firewall and network protection. The third parameter is complex, but is the most relevant. It measures and assesses the changes in the security knowledge, attitude, and behavior of the audience.
Evaluations of security knowledge, attitude, and behavior use both subjective (e.g. ask the audiences about their experience), and objective (e.g. ask the audiences to do something) methods [ 14 ]. Measuring the knowledge and comprehension of security is conducted through, e.g. online quizzes that can reveal whether people know and understand the risk [ 8 ]. Similarly, measuring attitude is conducted through, e.g. anonymous surveys on why people take risky actions. But measuring the behavioral change is not simple and is performed mostly using indirect measurement, e.g. self-reporting and surveys. A few studies used simulated attacks (i.e. attack simulation based on the threat profile of the target audience) and system data (e.g. analysis of audit logs) to understand the audience's security knowledge, attitude, and behavior from their responses. Other ways include investigating the three key elements of the Fogg Behavior Model, i.e. motivation, ability, and trigger [ 15 ] that have to occur simultaneously for behavior change.
Although the aforementioned parameters and their evaluation techniques are relevant, there do not exist commonly agreed and understood standards on what constitutes an effective and successful CSA program [ 16 ] and measurements to evaluate its effectiveness [ 11 ], thus hindering the evaluation process. This may have happened because of the logic that different audiences have varying needs and situations for a CSA program, thus their intention for evaluation cannot be captured by metrics valid for all [ 17 ]. Ironically, this lack of metrics has become a major reason for organizations' struggle to determine and measure the effectiveness of their CSA program. Many organizations either do not make any provision to measure the effectiveness of their program or their evaluation is merely based on the program's outreach [ 17 ]. Without a proper evaluation, a mature CSA program is presumably unachievable [ 18 ] and above all, it has a high chance of failure. Incidentally, the SANS security awareness maturity model [ 19 ] has the final (highest) level “ metrics framework ” that also reinforces a robust metrics framework to track progress and measure impact as the main requirement for a mature awareness program. The model's main argument is that an awareness program can be called mature only if it has developed the capability to demonstrate its continuous improvement, ROI, and value to the organization. This capability is possible only if an awareness program has standard measurements or metrics in place. The need for suitable metrics to measure the effectiveness has become even more crucial considering the fact that most existing efforts to improve people's security behavior are failing to produce the desired impact [ 7 ].
Therefore, the main objective of this paper is to define the right metrics for the evaluation of a CSA program and the corresponding methods that provide information on how well the metrics have been met. Defining such metrics will help to reduce the ambiguity in the evaluation of a CSA program by indicating the priorities that need to be focused on. Moreover, they will help to assess the aspects of the program and identify what has been successful and what has not, as well as what has been a required improvement. In order to define the metrics, we used a systematic literature review and the European Literacy Policy Network's (ELINET) four indicators for awareness evaluation.
Through this proposition, we intend to make the evaluation process of a CSA program as inclusive, complete, and unbiased as possible and, more importantly, make it replicable so that everyone should be able to conduct the same evaluation and get similar results. We believe that this will help CSA professionals assess their implementation to get more accurate and usable findings for the future iterations of their awareness program and attain a successful CSA program.
There are some major works that proposed methods for the evaluation of a CSA program. A survey report by the European Union Agency for Cybersecurity (ENISA) [ 5 , 11 ] found that in general there are four main approaches, each with different performance indicators, used by organizations for the measurement and assessment of the effectiveness of CSA activities. We present details of these four approaches in Table 1 . Most organizations use a blend of these approaches for assessment and make their decisions based on the overall picture rather than on a single measure. Along with that, the latter work [ 5 ] also mentioned that as the needs and situations of target groups differ greatly so should their evaluation metrics. Thus, it provided 71 key performance indicators (KPIs) and suggested considering different layers (i.e. business layer, service layer, and operational layer) and dimensions (i.e. planning, managing, and evaluating), while identifying the evaluation metrics and KPIs for the evaluation of the CSA of an organization. Further, it recommended making use of industry-standard performance management models, such as the Balanced Scorecard or Six Sigma, to define performance targets and measurements. As a part of the overall evaluation of CSA, these reports suggested both formative and summative evaluations [ 20 ]. However, a major difficulty in using the metrics would be deciding what to measure and for whom it is measured (intended users of the outcomes) among the number of KPIs they recommend measuring, which has been left up to the evaluator to decide.
CSA evaluation metrics [ 11 ]
| Approach . | Description . | Performance indicator . |
|---|---|---|
| Measures the effort invested to conduct a program(e.g. development, dissemination, and deployment)and has no link to the end result, i.e. whethersecurity has improved or not. | ||
| Measures how resistant the staff is to a potentialattack. | ||
| Measures the experience of security incidents withinthe organization. | ||
| Measures secure behavior results because ofawareness. |
| Approach . | Description . | Performance indicator . |
|---|---|---|
| Measures the effort invested to conduct a program(e.g. development, dissemination, and deployment)and has no link to the end result, i.e. whethersecurity has improved or not. | ||
| Measures how resistant the staff is to a potentialattack. | ||
| Measures the experience of security incidents withinthe organization. | ||
| Measures secure behavior results because ofawareness. |
Another similar study by Manifavas et al. [ 21 ] suggested 12 quantitative metrics for the evaluation of the CSA of an organization, shown in Table 2 . It showed a method to assign a weight to metrics. In addition, it proposed the cost of implementing and running the CSA program (i.e. cost-benefit analysis) as a part of the evaluation process. The effectiveness of an awareness program is determined by the weighted summation of the value of its underlying metrics and the summation of their (i.e. metrics) costs. But a major limitation of this study is that it does not provide a complete evaluation of any dissemination methods. For example, email views or poster downloads can convey only the reachability of an awareness program. With this information on hand, it will not infer, e.g. if the awareness message has been read and understood properly as well as practiced in everyday life by the audience. Not to mention, it is widely recommended to use multiple dissemination channels to fulfill the needs and preferences of diversified end-users [ 22, 23 ] and to retain the information richness of the awareness content as much as possible [ 24 ]. This also implies that evaluation has to be performed for each dissemination channel used.
Evaluation metrics and measuring parameters [ 21 ]
| Approach . | Description . | Performance indicator . |
|---|---|---|
| Surveys | Questionnaire-based survey on technical andsecurity policy issues. | Statistical analysis of monthly survey (conducted inthe different divisions of the organization) andannual survey (conducted in the wholeorganization). |
| Awareness/security day | Direct communication with employees to get theirfeedback. | Statistical analysis of security day attendance. |
| Independent observation | Silent observation of employees' security behaviors. | Statistical analysis of unsuccessful mock phishingattacks, and new threats bulletins' readership. |
| Audit departmentreports | Security awareness related incidents identified byaudits should decline. | Count of security incidents caused due to employeebehavior identified by the audit department. |
| Risk department reports | Risk identified during the previous assessmentshould reduce throughout time. | Count of security issues occurred due to employeebehavior identified by the risk department. |
| Security incidents | The volume of security incidents that occurred. | Number of employees who have caused at least onesecurity incident |
| Awareness sessions(workshops) | Post-session feedback from employee. | Statistical analysis of session attendance andeffectiveness. |
| Information securitywebsite | Employee interest in the awareness program. | Statistical analysis of information security websitevisit. |
| e-Learning | Reachability of the awareness program and theemployees' interest in it. | Statistical analysis of e-learning program visits,registrations, and completion. |
| Emails | Employees' interest in the awareness program (linkcan be provided for follow up information). | Statistical analysis of email views. |
| iNotices | Employees' interest in the awareness program (linkcan be provided for follow up information). | Statistical analysis of iNotice reading. |
| Posters | Independent observations, combined with electronicmeans, e.g. Quick Response (QR) code to additionalresources, or Uniform Resource Locator (URL) fromwhere the poster can be downloaded. | Statistical analysis of poster downloads. |
| Approach . | Description . | Performance indicator . |
|---|---|---|
| Surveys | Questionnaire-based survey on technical andsecurity policy issues. | Statistical analysis of monthly survey (conducted inthe different divisions of the organization) andannual survey (conducted in the wholeorganization). |
| Awareness/security day | Direct communication with employees to get theirfeedback. | Statistical analysis of security day attendance. |
| Independent observation | Silent observation of employees' security behaviors. | Statistical analysis of unsuccessful mock phishingattacks, and new threats bulletins' readership. |
| Audit departmentreports | Security awareness related incidents identified byaudits should decline. | Count of security incidents caused due to employeebehavior identified by the audit department. |
| Risk department reports | Risk identified during the previous assessmentshould reduce throughout time. | Count of security issues occurred due to employeebehavior identified by the risk department. |
| Security incidents | The volume of security incidents that occurred. | Number of employees who have caused at least onesecurity incident |
| Awareness sessions(workshops) | Post-session feedback from employee. | Statistical analysis of session attendance andeffectiveness. |
| Information securitywebsite | Employee interest in the awareness program. | Statistical analysis of information security websitevisit. |
| e-Learning | Reachability of the awareness program and theemployees' interest in it. | Statistical analysis of e-learning program visits,registrations, and completion. |
| Emails | Employees' interest in the awareness program (linkcan be provided for follow up information). | Statistical analysis of email views. |
| iNotices | Employees' interest in the awareness program (linkcan be provided for follow up information). | Statistical analysis of iNotice reading. |
| Posters | Independent observations, combined with electronicmeans, e.g. Quick Response (QR) code to additionalresources, or Uniform Resource Locator (URL) fromwhere the poster can be downloaded. | Statistical analysis of poster downloads. |
Next, the study by Bitton et al. [ 25 ] proposed a framework for assessing the Information Security Awareness (ISA) of smartphone users. The framework focused on measuring the behavior of smartphone users by collecting and analyzing data from three sources, which are
a mobile device agent installed on the subject's device,
a network traffic monitor (network traffic sent to/from the subject's devices), and
survey data (using a security questionnaire).
The main issue in this study is the data collection methods it suggested. Data collection methods like a mobile device agent and a network traffic monitor can be controversial to use and may be considered equivalent to spying on the audiences.
Last but not least, Fertig et al. [ 18 ] performed a systematic literature review to identify metrics that are regarded for ISA and performance measurement systems (PMS) used for the assessment of ISA. They mainly found two types of metrics, which are
Knowledge-based metrics: impacts of knowledge in attitude and behavior (KAB based [ 26 ]), evaluation of ISAs training (based on various KPIs), dissemination of knowledge (ease of sharing and using knowledge), and impacts of knowledge on individuals (improvement in the sense of responsibility for security).
Behavior-based metrics: improvements in security behavior (for various security threats, and security practices).
In the same study, the authors also identified requirements for metrics in theory (used literature review) and practice (used interviews with experts). Further, they analyzed whether the existing metrics and PMS meet the identified requirements. Their analysis revealed that most existing metrics and PMS do not meet primarily two requirements, which are automation (computed automatically) and visualization (visualizing the results properly). However, the study does not discuss how metrics can be measured (measurement methods).
All the aforementioned works do not dismiss the value of qualitative methods in the evaluation process; however, they all emphasize the use of quantitative methods. This is mainly because it is relatively easier to express and convey the message on the benefit of CSA to the senior management using quantitative values, i.e. in a language and format they understand and are used to. Moreover, all of them primarily focus on the evaluation of CSA in organizations.
Indeed, the aforementioned works are useful; however, we believe that they disregard certain important aspects to measure that we have included and compared with our proposition in Section Metrics Development.
The main objective of this research is to come up with appropriate metrics for evaluating a CSA program. To begin with, we have conducted a systematic literature review with an intent of determining and analyzing the “ factors to be measured ” and their “ measuring methods ” commonly used to evaluate the performance of a CSA program. And, to conduct the literature review, we followed the structure of a systematic literature review as suggested by Webster and Watson [ 27 ], as shown in Fig. 1 . Following that, ELINET's four indicators for awareness evaluation (metrics in practice but for purposes other than cybersecurity) have been adapted for CSA purposes. For each indicator, we have provided appropriate “ factors to be measured ” and their “ measuring methods ” that should be used while evaluating the performance of a CSA program.
![essay on cyber security awareness Structure of a literature review [27]](https://oup.silverchair-cdn.com/oup/backfile/Content_public/Journal/cybersecurity/8/1/10.1093_cybsec_tyac006/3/m_tyac006fig1.jpeg?Expires=1726682260&Signature=zfMkknD6KkODz3LWCbvz0Z4z6N03ej65ZVVD8mFP~ML5TaBp0NO9yCAsWOHLtdElhDboHJ7lIR3qT3zvdk3xiE8nsHfvAIF1KaPiwBYUJW1N73CLyBzwjLv1gTdxwkUmOJL-LC1Nn2ZArjAlStfR8O9wEfccmEbovZ2xni7LqtMe6a1Kfk6aAlzUlGLns2ejNzbEDBdAAlMfmIa1U5EfTnMC7Vq0Lz1tTs9VElXTno6j6pFOTonlwQjcEPyuWOIKRpNKDZqlPaii4EVIkhu6THWVL7KKJv8tqb53~pGoSQTJj-6a5O7CtOT5Wdy6SiedPtuEbZpmOzJ1QW1w-ZQ0dg__&Key-Pair-Id=APKAIE5G5CRDK6RD3PGA)
Structure of a literature review [ 27 ]
In order to identify relevant literature on the topic, we used search services on Google Scholar Citations and Microsoft Academic. Both are freely accessible web search engines indexing the full text or metadata of an array of scholarly materials including peer-reviewed academic journals and conference papers, books, theses and dissertations, technical reports, and other scholarly literature published in different digital libraries and databases. There are several features of these search engines that helped to accomplish the search goal more efficiently. These search engines perform search operations on the full text of documents and rank them according to their weight calculated using different important criteria [ 28, 29 ]. This feature saved lots of our time and effort that would have been required for screening relevant literature if used a search engine that indexes only the title, abstract, and keywords of a document. Further, it is a very challenging task to decide which digital libraries and databases to include in the study and know if they will result in relevant literature or not. Not to mention, many academic databases do not contain gray literature like white papers, technical reports, theses, and dissertations, which are equally useful for a systematic literature review [ 30 , 31 ]. Some potential benefits of including gray literature in a review can be, e.g. this helps to reduce the possibility of publication bias, improves the comprehensiveness and timeliness of the reviews, fosters a more balanced understanding of the available evidence, and ultimately enriches the review's findings [ 31 ]. Moreover, this study does not intend to limit only to academic findings but also include industry findings, i.e. to provide a more balanced picture based on both theory and practice [ 18 ], which would be possible only by including gray literature. More importantly, performing search and screening operations in various digital libraries, university academic repositories, and others to collect a large number of relevant literature studies (including gray literature) would be exhausting. This became relatively easier and more convenient merely by searching these two search engines, as it would otherwise have required performing search operations on different databases independently.
This paper is a revised and extended version of the CyberSec4Europe project report [ 32 ]. So, we performed the first round of search operations in October 2020. With an intent to extend the report, we performed the second round of search operations in July 2021. We used “security + awareness + effectiveness,” “security + awareness + success ,” and “security + awareness + value,” as the search keyword strings, where ‘+’ is an “AND' operator. Before selecting this keyword string, we performed a trial with other keyword strings like “cybersecurity + awareness + effectiveness,” “cyber-security + awareness + effectiveness,” “cyber security + awareness + effectiveness,” “information security + awareness + effectiveness,” and “Internet security + awareness + effectiveness.” But by using these keywords, we did not find relevant literature showing up on the top result pages. In the case of search results common to both of the search engines, a download was just made from one of them.
After a manual screening of 350 results in Google Scholar Citation and 400 results in Microsoft Academic based on their abstract and keywords, we downloaded 78 papers. The downloaded papers were thoroughly read in the second round of screening to determine how relevant the papers were to the research topic and to provide answers to the two questions “ what to measure ” and “ how to measure ” to evaluate the effectiveness of a CSA program. After the second round of screening, we selected 32 papers for the literature review comprising 19 journal papers, 12 conference and workshop papers, and a NIST Technical Series publication.
For the selection of literature, we defined inclusion and exclusion criteria as follows:
Literature in languages other than English is excluded, since the working language for this study is English.
No exclusion criterion was defined for the year of publication. The oldest and the most recent papers considered for the review are 2003 and 2020, respectively. Many traditional methods used for raising awareness are still relevant and in practice with necessary modifications; e.g. different organizations still use posters and leaflets [ 33 ] to raise CSA. So, restricting by the year of publication in the literature selection will lead to missing many important papers with information even now relevant and useful.
Along with academic literature, gray literature as recommended by Kitchenham [ 30 ] and Paez [ 31 ] was also included in the review. However, only technical reports from reputable organizations also cited by many other works have been considered for the review to maintain academic integrity in the work.
Finally, for high-quality literature as recommended by Webster and Watson [ 27 ], information like published venue (peer-reviewed journals, conferences, and workshops) and citations were used for the literature selection.
In order to structure the review, we were highly reliant on a tabular presentation style, since it is easier to present a large amount of data in an understandable form.
The theory development is based on ELINET ’s four indicators for awareness evaluation, a well-established model designed for awareness evaluation. We have adapted it to make it applicable to CSA. While doing so, we have considered the findings of the literature review, and some criteria for good metrics.
A review of the 32 selected papers [ 4 , 21 , 26 , 34–62 ] was performed mainly to gather “ what factors are measured or suggested to be measured ” in order to determine the effectiveness of a CSA program and “ how those factors are measured or suggested to be measured .” The collected factors and their measuring methods have been listed in Tables 3 and 4 , respectively.
Factors measured by the reviewed papers to evaluate the effectiveness of a CSA program
| Measured factor . | Paper . |
|---|---|
| Improvement in cybersecurity resulted from participating in an awareness program. This has beenexpressed as follows: | References [ , , ] |
| Positive changes in the cybersecurity of the audience resulted from participating in a CSA program.This has been expressed as follows: | References [ , , , , , , ] |
| Cybersecurity gained by participating in a CSA program. This has beenexpressed as follows: | References [ , , , , , , , ] |
| The audience, organizer, and management/sponsor's in a CSA program. This has been expressed asfollows: | References [ , , , , ] |
| of an awareness program, i.e. information has reached the right audience. This has beenexpressed as follows: | References [ , , , ] |
| of an awareness program, i.e. information is perceived positively by the right audience. Thishas been expressed as follows: | References [ , ] |
| by an awareness program, i.e. economic, or other benefits. This has been expressed asfollows: | References [ , , ] |
| of topics covered, learning methods used, and awareness program organized. This has beenexpressed as follows: | References [ , , , , ] |
| on an awareness program. This has been expressed as follows: | References [ , , , ] |
| Measured factor . | Paper . |
|---|---|
| Improvement in cybersecurity resulted from participating in an awareness program. This has beenexpressed as follows: | References [ , , ] |
| Positive changes in the cybersecurity of the audience resulted from participating in a CSA program.This has been expressed as follows: | References [ , , , , , , ] |
| Cybersecurity gained by participating in a CSA program. This has beenexpressed as follows: | References [ , , , , , , , ] |
| The audience, organizer, and management/sponsor's in a CSA program. This has been expressed asfollows: | References [ , , , , ] |
| of an awareness program, i.e. information has reached the right audience. This has beenexpressed as follows: | References [ , , , ] |
| of an awareness program, i.e. information is perceived positively by the right audience. Thishas been expressed as follows: | References [ , ] |
| by an awareness program, i.e. economic, or other benefits. This has been expressed asfollows: | References [ , , ] |
| of topics covered, learning methods used, and awareness program organized. This has beenexpressed as follows: | References [ , , , , ] |
| on an awareness program. This has been expressed as follows: | References [ , , , ] |
Factors measured and their respective measurement methods
| Measured factor . | Measurement method . |
|---|---|
| Accessibility of awareness materials. | |
| Self-motivated actions. | |
| Measured factor . | Measurement method . |
|---|---|
| Accessibility of awareness materials. | |
| Self-motivated actions. | |
With a motive to evaluate the effectiveness of a CSA program, the reviewed papers measured the following factors given in Table 3 , and the count of papers measuring them are shown in Fig. 2 .

Factors measured by the reviewed papers
Knowledge, attitude, and behavior
Among the measured factors, knowledge, attitude, and behavior are found to be the most popular. Knowledge refers to a familiarity, awareness, or understanding of security policies, procedures, standards, guidelines, laws/directives/regulations, strategies, technologies/systems, and good practices. Similarly, an attitude refers to beliefs, opinions, thinking, or feelings toward security. An attitude can be positive (e.g. I am aware of my role in protecting the organization against potential cyber threats) or negative (e.g. I think cybercrime reporting is a waste of time). Finally, behavior is the way in which a person acts or conducts toward security issues, i.e. either avoiding or bringing into practice security knowledge s/he has learned. The popularity of these factors may have happened due to the influence of the KAB model (also known as the knowledge-attitude-practice-KAP model), which is widely popular in health education but now has also been increasingly adopted for CSA purposes.
The KAB model divides the changes in behavior into three successive processes that initiate with the acquisition of knowledge, followed by the generation of attitude, and finally, result in the formation of behavior or actions. The model implies that just because someone possesses security knowledge does not mean they will utilize it to good use and act appropriately. If someone has a negative attitude, their actions (behavior) will be in direct opposition to their understanding. Behavioral change comes with knowledge through attitude. However, every knowledge and attitude may not translate into action (i.e. intention–behavior gap). Many unfavorable factors, for instance, lack of suitable knowledge, adequate time and resources, and others, may inhibit translating intention into behavior.
The primary objective of a CSA program is to motivate or influence the participants in the adoption of secure online behavior [ 7 ]. This may be a reason why several studies have utilized different psychological, social, and behavioral modeling theories to study the impact of knowledge and attitude on security behaviors with a motive to improve the effectiveness of CSA [ 63 ]. Moreover, in the various classifications of CSA levels [ 64, 65 ], the highest or ultimate awareness level is also about behavioral changes, i.e. security activities and behaviors occur automatically in an individual when performing personal and professional activities. Therefore, there is no way to evaluate a CSA program's success just based on knowledge measurement but requires also including the measurements of attitude and behavior.
A major issue with the studies evaluating security knowledge, attitude, and behavior is that they develop their own measurement, which is often non-standardized (do not follow a standard process to design questionnaire and scale as well as analyze the data). They often examine only one or a few selected components of cybersecurity for the assessment. Therefore, it is recommended to use a standardized questionnaire and scale to measure knowledge, competence, attitude, and behavior [ 46 ]. Several studies have produced well-validated and standardized scales or questionnaires intended to measure security knowledge, attitude, and behaviors. Some of their examples are
Human Aspects of Information Security Questionnaire (HAIS-Q) [ 66 ] is used to assess the vulnerability of organizational critical assets caused by the risky or risk-taking behavior of employees.
Security Behavior Intentions Scale (SeBIS) [ 67 ] is used to measure users' self-reported adherence to computer security advice.
SA-6 scale [ 68 ] is used to assess and compare users' security attitudes.
Rajivan et al.’s [ 69 ] questionnaire containing a combination of skills and knowledge-based questions is used to measure security expertise in end-users.
Hadlington's [ 70 ] combination of four scales, which are the Abbreviated impulsiveness scale (ABIS) [ 71 ], Online cognition scale (OCS) [ 72 ], Risky cybersecurity behaviors scale (RScB), and Attitudes toward cybersecurity and cybercrime in business (ATC-IB), are used to measure the human factors in cybersecurity.
Ög˘ütçü et al.’s [ 73 ] four independent scales; namely Risky Behavior Scale (RBS), Conservative Behavior Scale (CBS), Exposure to Offence Scale (EOS), and Risk Perception Scale (RPS), are used for the assessment of security-related behaviors and security awareness levels of information system (IS) users.
Smartphone Security Behavior Scale (SSBS) [ 74 ] is used to measure the influence of mental health issues on smartphone security behavior intentions.
Users' ISA Questionnaire (UISAQ) [ 75 ] is used to measure users' security awareness (security knowledge, belief, and behavior).
We believe that using these standard scales and questionnaires for evaluation purposes can help to get more reliable and scientifically valid results. Finally, touchability (i.e. awareness information is perceived positively) is also mainly associated with knowledge, attitude, and behavior.
Usability is the next popular factor measured to evaluate the effectiveness of a CSA program. This is measured in terms of the relevancy of topics covered, the quality of the content, and the suitability of the dissemination channels used. Reachability (i.e. the ability to reach the right audience) is also a quality of dissemination channels.
In an organization, CSA can be undertaken at different levels, e.g. individual, departmental (or business unit), and organizational [ 76 ] aligning with the individual needs, departmental (or business unit) objectives, and organizational strategic plans and goals, respectively. Organizations depending on CSA designed based on the “ one-size-fits-all ” approach completely underestimate its purpose. By doing so, the problem of cybersecurity cannot be addressed, rather it only contributes to the organization's overhead.
It is not by any means beneficial for organizations to ask their employees to mandatorily attend a CSA program on topics irrelevant to them. Essentially, CSA topics suitable for managers and executives to carry out their managerial roles and responsibilities [ 77 ], cannot be of use and interest to other general employees. Likewise, awareness topics appropriate for employees with specialized roles and responsibilities, e.g. accounting, may not be of use and interest to employees in the IT department. Even within the same department, some employees may have different CSA needs than their departmental colleagues, whereas employees from different departments may have the same CSA needs. So, the evaluation must check whether the awareness topic was of use and interest to the audience and also identify the topics they really want to learn about.
The quality of CSA contents is not just about what has been expressed but also how they have been presented [ 78 ]. The same message can be framed and conveyed in a multitude of ways without changing its meaning and facts. And the way it has been conveyed largely determines whether the message will persuade the recipients or drive them away. The concern on a CSA content's presentation, therefore, should not limit just to what formats of media be used, but much more than that. Unfortunately, there is no consensus on how the quality of awareness content should be evaluated. Existing evaluations are largely based on asking the audience how informative and useful the content is, or how satisfied the audience is with the content. Such evaluations may not provide results that can disclose the aspects requiring improvement or update in the content. Therefore, we suggest a more comprehensive evaluation, where questions ask about attributes like
Accurate, consistent, up-to-date, and complete information.
Clear and concise presentation.
Effective message framing.
Convenient and doable suggestions.
Innovative, engaging, localized, and useful message.
Finally, a CSA message is disseminated through a variety of channels, e.g. workshops, newsletters, posters, screensaver, emails, games, videos, audio, simulation, and so on. Different audience groups can have varying preferences regarding dissemination channels [ 79 ], e.g. young people may prefer dynamic channels (like games and simulations) over static ones (like posters and newsletters). Therefore, it is necessary to know how well-fit the dissemination channel was to the audience. Once again, there is not a common understanding or standard for the evaluation of dissemination channels. Certainly, there are some studies [ 5 , 24 , 80–82 ] that have compared various dissemination channels to gauge their advantages and limitations. Some parameters drawn from those studies, which we believe can be useful for designing evaluation questions, are
Cost and technology (did it require any additional cost and technology to operate?).
Operation (how easy was it to operate?).
Work culture (did it support the users' work culture?).
Flexibility (did it support self-paced learning?).
Interesting and engaging (was it interesting to use and offered high engagement of users?).
Content type (did it support preferred content types?).
Reachability (did the information reach the right audience?).
The individual interest of the organizer, sponsor, senior management, or audience toward a CSA program is another factor widely measured to evaluate its effectiveness. In psychology, focused attention characterizes interest, increased cognitive and affective functioning, and persistent effort [ 83 ]. It has also been found to be strongly related to motivation, behavior, and outcome [ 84 ]. The organizers, sponsors and senior management interest is necessary for the sustainability of the program. Similarly, the audience's interest is essential to motivate them to participate, learn, and benefit from a CSA program. Therefore, this can be an essential factor to be measured to know the effectiveness of a CSA program.
A simple and direct way to measure interest is to ask an individual if the program interested him/her (self-reporting). But a more reliable result can be obtained by watching other indirect indicators. Indicators like voluntary participation (e.g. attendance or visits to awareness resources available online), seriousness for learning (e.g. further inquiry with a desire to learn more, or visits to additional materials), activities during physical participation, and affect or performance after participation in a CSA program (e.g. test results and changes in behavior) can be utilized to measure the interest of the audience. Next, the organizer's and sponsor's interests can be realized from the continuity of the program. Finally, in an organization, the senior management's interest can be realized from their commitment and moral support for the program, their participation in the program, and the funds allocated for the program.
Value added
Value-added, means economic (time- and cost-saving that could have suffered due to a cyberattack or repairing and reinstating normal business operations after suffering an attack) and non-economic benefits (market competitiveness, or improved customer confidence) benefits gained due to a CSA initiative. It is, once again, important for the sustainability and continuity of a CSA program. An organization performing a cost-benefit analysis of a CSA program [ 5 ] can provide more formal results valuable to the management. Some other indicators are lowered cyber incidents, awards received, a reputation built due to improved cybersecurity, and CSA's lessons learnings integrated into the work culture of an organization. However, such specific indicators may not be available in the case of a CSA program for civilians. In that case, a self-reporting method can be used to gather the different benefits they gained by participating in a CSA program.
Methods used for evaluation
The methods that have been utilized to evaluate each factor are presented in Table 4 . Basically, these methods (shown in Fig. 3 ) can be classified into two types: intrusive evaluation, and non-intrusive [ 85 ].

Methods used for the evaluation CSA
In intrusive evaluation, the participant's normal behavior is consciously disrupted by the evaluation processes. This also means that the participants are aware of the things happening to and around them, which could lead them to be alert or possess a high cognitive load. Such participants (alert or with a high cognitive load) may not think and act in the ways they would do in a natural environment. This could negatively affect the accuracy of the outcomes. The evaluation is generally conducted in a laboratory environment using well-established evaluation techniques, such as questionnaires, interviews, tests, observations in a laboratory setting, and focus group discussions. Its main advantage is a short evaluation duration (a session may last from a few hours to a day) within which different aspects of cybersecurity can be covered. An intrusive evaluation could be suitable for assessing/measuring security knowledge and attitude, where the familiarity with facts and information, and individual viewpoints are measured, respectively.
Whereas in non-intrusive evaluation, the participant's normal behavior is not consciously disrupted by the evaluation processes. The evaluation processes are performed in a natural environment with a lower cognitive load in the participants, which may result in more accurate outcomes. However, the main disadvantages of this evaluation are a longer evaluation period (can continue for a few days depending on the number of participants and the aspects to be assessed), only a few existing evaluation techniques are applicable (e.g. analysis of system and log data, disguised observations, simulated and other attacks), and the likelihood of bias introduction is high that may skew the outcomes (e.g. in observation the evaluator has to interpret the participant's activities). A non-intrusive evaluation could be more appropriate to assess security behavior. Moreover, it should be preferred to assess/measure other factors wherever possible in organizations since it will save the participant's (or employee's) effort and time. However, sometimes getting an in-depth understanding of why the participants behaved in a certain way may require using a follow-up intrusive method.
The widely used methods for evaluation purposes are categorized broadly in Fig. 3 and explained next. Although some of the categories overlap with each other based on their true definitions, we have distinguished them in the description to improve their clarity and understanding.
A questionnaire survey has been found to be the most popular method used. It has been implemented mainly to determine the impact of a CSA program on the security knowledge, attitude, and behavior of the participants. In order to do so, pre- (before the awareness program) and post- (after the awareness program) surveys have been utilized. In addition to these factors, post-survey has also been carried out for many other purposes, such as
To determine the suitability and usefulness of the covered topics.
To realize the importance of the knowledge gained in practice.
To understand the interest and willingness to participation.
To realize the confidence, satisfaction, and preference of the audience.
To determine preference for learning methods.
To get overall feedback (or suggestion, opinion).
This popularity of a questionnaire survey could be because (i) it allows a large population to be assessed with relative ease, (ii) it is easy to integrate different aspects of cybersecurity for evaluation in a survey, and (iii) it is possible to reduce time, effort, and cost for conducting a survey by using techniques like an online survey (it is economical to disseminate questionnaires, and data gathering is automated), survey sampling (it reduces sample size when the target size is large), and quantitative questions (it is relatively easy, and fast to analyze quantitative questions).
A survey can use closed-ended questions, open-ended questions, or a mixture of both question types. When close-ended questions are used, the results can be quantified; however, open-ended questions are presumably more suitable to get deeper insights into attitudes and behavior changes [ 45 ] if the respondents are adequately literate and interested to answer. On the flip side, responses to open-ended questions may be difficult to interpret and analyze, limiting their usefulness.
Finally, a survey captures active data from willing participants, who may not remember correctly all the things they do. Such memory lapse can introduce incorrect data that ultimately could restrict the ability to use the information for actionable results. This can be mitigated to an extent by using closed-ended questions whenever possible, where all possible options are provided, making it easier for the participants to remember and recall their preferences. Moreover, making the survey anonymous can encourage the participants to provide real and honest feedback. These all are important since the survey result is of value as long as the participants do not lie.
Passive data
Analyzing passive data (also referred to as indirect observation) has been found to be the next popular method used mainly to evaluate the behaviors of the participants and their interest in CSA. When gathering data through direct observation becomes very expensive and time-consuming, then indirect observation becomes more relevant. The reviewed studies have collected passive data from multiple sources, such as the audit department, the risk department, other external and internal auditors, and the helpdesk in a natural environment (i.e. participants remain unaware of the data collection for a research purpose). This data is not subjective (i.e. human independence, so a separate time of the audience for the data collection is not required), and easy as well as economical to obtain. These may be some reasons why many studies utilized them to evaluate cybersecurity behaviors (both risky behaviors and best security or compliance behaviors). Some types of passive data used to measure cybersecurity behavior are
Anti-virus and firewall logs.
Visits or requests to visit unauthorized services and websites.
Number of security incidents or violations reported.
Use of weak passwords.
Sending of sensitive information via email.
Count of calls to the helpdesk.
Visits or traffic to the location where awareness information is available (e.g. security intranet page, or location where awareness information is uploaded).
Click through rate of malicious links.
Count of information security intranet page access, or visits to a webpage where awareness information has been uploaded.
Installation/non-installation of security protection.
Coverage and identified needs of CSA are shrinking.
Frequency of awareness programs needed in the organization.
Increase in reporting of potential cyber incidents by cyber aware people.
Similarly, passive data that has been utilized to know whether the CSA information reached the target audience or not are
Count of people that received a leaflet.
Number of attendees visiting the e-learning program.
Count of email recipients.
Count of people logged into iNotice.
Visits the website (but there is a risk that a small group of people may repeatedly visit the website).
Percentage of people who attended an awareness session.
The audience's interest in a CSA program (or whether cybersecurity information touched the audience or not) is also determined by utilizing the following passive data:
Number of attendees registering, and completing the e-learning program.
Hit counts to the link for more information in the email/iNotice.
Poster downloaded from the link.
Activities like attendees temporarily leaving the room, constantly chatting with colleagues, or sketching on their notes are not encouraging reactions.
As a matter of fact, utilizing such data for evaluation purposes in cybersecurity provides a more realistic outlook for the situation. This data is a part of everyday activities, so participants do not need a separate notification that could make them aware and alert, thus influencing their activities and data.
However, analyzing this data could answer only what has happened and not why has it happened, since the evaluator gathers information without the direct involvement of the people studied. For example, it will answer if the participants continue to use a weak password even after participating in a related awareness program, but not provide an answer to why they continue doing so. Indeed, it is important to know whether an awareness program has brought positive changes in the participant's behavior or not, but at the same time, it is equally necessary to know why certain behaviors have not changed. This information will help to improve the awareness program in a future iteration. In addition, access to someone's digital footprints will require a precautionary approach, e.g. implementing privacy-enhancing technologies, incorporating regulatory controls, and receiving permission from the authority.
Tests in two forms have been utilized for evaluation purposes, which are (i) a question-based test, and (ii) an attack-based test. Such tests are performed before and after a CSA program and their results are compared to know the effectiveness of the CSA program. These tests are conducted mainly to evaluate cybersecurity knowledge, and in the case of a simulated attack, are also used to evaluate behavior.
In a question-based test (e.g. quiz, or game) using standardized questions [ 46 ] comprising vocabulary and scenario type questions [ 36 ] can help to ask the right and relevant questions. Then, in an attack-based test, using a secret simulated attack, e.g. sending a phishing email to the audience and observing their responses like a count of people who revealed sensitive information, who downloaded or opened the attachment, who identified and reported the phishing attempt to the concerned authority, and who reported about fallen for a phishing attack after realizing it, can provide more realistic results. Similarly, other attack types, such as checking password strength using tools and techniques after an awareness program on creating strong passwords, can also be a test to evaluate the effectiveness of the awareness program.
As with the passive data approach described above, this simulated attack also provides a more realistic view of the situation. But it involves more work (like developing attacks in as natural form as possible, taking care of legal and ethical aspects, and others) and can be expensive to conduct. Further, for various aspects of cybersecurity, other forms of evaluation could be more appropriate than using simulated attacks, e.g. the observation method would be suitable to determine whether an individual leaves his/her digital devices unattended, or passive data would be suitable to know whether an individual routinely updates the anti-virus software in his/her digital devices. More importantly, exposing people to simulated attacks can have several unintended consequences (negatively impact the staff trust, and security and error culture of an organization) and could also violate various national or data protection laws, or local agreements [ 86 ]. For example, a phishing attack attempts to persuade victims to reveal sensitive information, download and open a malicious attachment, circumvent security in digital devices, transfer money, and so will be a simulated phishing attack that may not be compatible with different laws and agreements. Therefore, while conducting such attacks, it is mandatory to ensure that no laws and ethics are contravened.
Face-to-face interaction
Face-to-face interaction using techniques like semi-structured interviews, informal break room conversations, and focus group discussions to get audience and management feedback on a CSA program has been found to be the next popular method. It can be either targeted or generalized (e.g. suggestions, opinions, wishes, concerns, problems, and values). Such face-to-face interaction conducted in a laboratory setting can also be utilized to an extent to realize the audience's cybersecurity knowledge, attitude, and behavior.
One of the main advantages of face-to-face interaction is that it captures both verbal and non-verbal (e.g. nuances of the voice, facial expressions) cues. In addition, it supports immediate feedback and without any delay clears up confusion and misunderstanding in the message conveyed if any exists. However, in a face-to-face interview, the cost can be a major disadvantage since it requires an interviewer (i.e. personnel cost) and is very time-consuming to conduct. Its cost can be reduced by using informal break room conversations and focus group discussions, although they may not provide a comprehensive understanding of the problem. Also, face-to-face interaction does not provide anonymity, which can be a concern for some respondents.
Observation
Both disguised (i.e. evaluator's presence is concealed from participants) and non-disguised (i.e. evaluator's presence is known to participants) observations have been found to be utilized mainly to evaluate cybersecurity behavior. Observation can be both direct (involves looking at the actual behaviors) and indirect (involves looking at a result of behaviors). This subsection, by observation, refers only to the direct one. The indirect observation has been included as passive data in subsection Passive data.
Although the non-disguised method alleviates ethical concerns that may arise due to watching someone covertly, it suffers the Hawthorne effect [ 87 ], i.e. participants act differently when they are being watched, and could not provide the actual behavioral changes resulted due to an awareness program. In addition, there is always a risk of distracting and disturbing the participants from their normal activities. At the same time, the non-disguised method can be replaced with a survey that can be equally effective. In that case, the disguised method conducted in the natural environment is a more preferable method for assessing the behaviors of the participants. But this also has a downside, which is due to the absence of interaction between evaluator and participants, there is a high chance that the evaluator may introduce errors and bias in the analysis of behavioral events. Moreover, in the case of an organization where the participants are within a specified perimeter, conducting a disguised observation could be easy, but doing the same may not be feasible for an awareness program that targets the general public.
There often exists a disconnect between what people self-report they do and what they actually do. So, to study a change in the participant's behaviors after participating in a CSA program, observation can be a very effective method. A more focused or structured observational study (where the evaluator uses checklists or targets specific behaviors) can be a more dependable method. This requires the evaluator to know what to observe ( event sampling ), when to conduct the observation ( time sampling ), and how to document the observations. The evaluator is often suggested to record the events for discussion and analysis at a later stage.
But a major limitation of observation is that it is generally conducted in-depth over a prolonged period, with data that are often subjective and difficult to quantify, thus the sample size is usually kept at a minimum. Moreover, it requires skilled observers and analysts, otherwise they may introduce errors and biases in their analysis. Not to mention, it does not provide anonymity to the participants.
But prior to metrics development, it is important to realize what constitutes good metrics. Some criteria of good metrics, which we believe are relevant for our proposed metrics [ 13 ] are shown in Fig. 4 .
![essay on cyber security awareness Criteria for good metrics [13]](https://oup.silverchair-cdn.com/oup/backfile/Content_public/Journal/cybersecurity/8/1/10.1093_cybsec_tyac006/3/m_tyac006fig4.jpeg?Expires=1726682260&Signature=U8UKhQL3BB11cZzhXmTMN08ke0znGM~O3GbFqLYe9kByNtYSKnbfCmwl9zbka-eorGaBksOp6cURXSI3Fcd80upXC8aWNIfnc1hPkTfLs7MP5YlotBb9wWQ5JJKtCmb8hR0P996Ih02QbeFGrtCTZysQZa2uljg1TLF7A2~shh-oDw0JhxgRTc4zgVlgWpkTa4CDrptxr-YgjoaYldE0YN65iKm87iSPhTY-MYt4XLTOhl-N2z4hFFLFo6Lk8yP7kWfC5ZFZok~Ofaypzt-V52N0OKwwKFUobmJGcoJpqjqCNI~Y0GZvyJBctRfmC8FdTYyeCCyp9YpIX6bCFmUj-w__&Key-Pair-Id=APKAIE5G5CRDK6RD3PGA)
Criteria for good metrics [ 13 ]
Evaluation can be diagnostic (i.e. a pre-assessment conducted to know an audience's existing awareness level on the topic), formative (i.e. an assessment conducted during the program development and implementation to realize the needs and processes required to achieve the goal), and summative (i.e. a post-assessment conducted to assess the outcome of the program and determine broader and long-term changes occurred due as a result of the program). The diagnostic assessment followed by the summative assessment is mainly related to the outcome and impact of the program or the declaration of the success or failure of the program, but the formative assessment helps learn where to best put the limited resources available for CSA. For a complete evaluation of a CSA program, all three assessments are equally necessary.
For the evaluation purpose, it is imperative to have a clear goal [ 5 ] and measurable objectives [ 88 ] from a CSA program. More essentially, both the goal and objectives must be realistic or achievable. The goal and objective should serve to uphold the reason for creating an awareness program, i.e. what the program wants to achieve. They can be unique to each target group. The measurable objective can be tracked with the help of numbers and units, which is crucial for continuously monitoring and analyzing the success. Against this objective, the effectiveness of the program is evaluated, and accordingly, the program is revised and updated.
In general, a CSA program is expected to communicate cybersecurity knowledge (i.e. recommended guidelines and security best practices) to the target audience, broaden the cybersecurity knowledge of the target audience (i.e. familiarity with guidelines and security best practices), bring positive changes in attitude (i.e. motivate to adopt recommended guidelines and practices) and behavior (i.e. create a strong culture of security) in the target audience, gain and keep the audience and management/sponsor trust and satisfaction; and ultimately minimize the number and extent of security breaches [ 5 ]. But these expectations are difficult to quantify. Some examples of clear goals and their respective measurable objectives are as follows:
Goal : achieve compliance with required regulations and directives; objective : compliance with GDPR, e-Privacy Regulation, NIS Directive, and so on.
Goal : identify and manage human risks to an acceptable level; objectives : reduce accidental data loss incidents by 70%.
Goal : raise awareness of security best practices; objectives : use of password security, practice social media safety, practice malware protection, practice mobile security, awareness of phishing, and so on.
In addition, the evaluation process must be cost-effective (or inexpensive) to conduct and its results are useful for decision-making. Cost can be reduced by limiting to only variables that need to be measured and doing this in a more planned and structured way in terms of schedule and clarity in questions intended to be answered. Then, usefulness can be improved by understanding and taking into account the priorities and concerns of different stakeholders who will use the evaluation findings for decision-making.
The ELINET [ 89 ] recommends four indicators and their measurement methods that are important for the evaluation of awareness activities. Based on this recommendation, the aforementioned criteria for good metrics, and evaluation methods utilized by the reviewed studies, we propose the metrics as shown in Fig. 5 and explained in Table 5 for the evaluation of a CSA program. We believe that all these four indicators are important to be evaluated in order to know the effectiveness and success of a CSA program. It is possible that an organization may not be in a situation to afford the measurement of every factor. In a situation like this, it is suggested that the organization measure selective factors most relevant to it from each indicator rather than measuring all factors from a certain indicator while abandoning other indicators. The target audience will impact how each indicator can be measured. For example, it may be easy and economical to obtain system and log data if the target audience is the organizational staff (they are in a controlled environment), but such data may not always exist if the target audience is customers (they are in an uncontrolled environment). Moreover, while suggesting measurement/assessment methods, we have tried to ensure that they adhere to the criteria for good metrics. For example, we have emphasized a quantitative method, i.e. non-subjective as well as quantifiable, and so makes sense to the sponsor/management. Besides, we have provided multiple alternatives to measure each indicator type so that the cost-effective option can be selected.

Metrics for the evaluation of a CSA program
Metrics for the evaluation of CSA
| Indicator . | Measured factor . | Measurement/assessment method . |
|---|---|---|
| Measure and assess the learning (i.e.knowledge and skills gained by theaudience as a result of the awareness), andthe impact on the audience's performanceand attitude toward cybersecurity. | Impact of awareness on: It also comprises touchability. | ○ Data from audits and riskdepartments. ○ Count and severity of securityincidents occurred due to staffbehaviors. ○ Other best behavior data that canbe automatically collected (e.g.anti-virus and firewall log data,and helpdesk data). |
| Measure the direct and indirect valuesadded to the organizations as a result ofimplementing CSA. These indicators arecritical for the management or sponsors intheir decision-making on whether to investin the program or not, and this is necessaryfor the continuity of the program. | Impact of awareness in the change of: Change in top management and sponsorsupport and commitment for theawareness program | ○ Recognition of securitycontributions, e.g. count andreputation of awards and contestswon due to the awarenessprogram. ○ Percentage of awarenessprocesses incorporated in theorganization's policies, processes,and arrangement |
| Measure the quality of resources anddelivery channels used in the awarenessprogram. | Quality of awareness resources. Effectiveness of awareness resources.For example, whether the content wasrelevant and easy to follow or not, what werethe strengths and weaknesses of the program,and whether the delivery methods were ableto accommodate the audience's pace andlearning style or not. It comprises of usabilityand reachability. | • Survey to evaluate (using closedquestions/quantitative, such as Likertscale).○ Relevancy of topics.○ Content quality.○ Delivery assessment.• Percentage of security topics coveredwith respect to expected topics to becovered to know if all relevant ordemanded topics are covered or not. |
| • System and log data analysis (e.g.,attendance, website visit, emailrecipient, etc.) to determine if the targetgroup has access to the awarenessresources or not. | ||
| Measure how the audiences, sponsor, andsenior management have perceived orreacted to the awareness program. | Interest, support, commitment, andparticipation of different stakeholdersin the program. | Interest and active participation evaluatedusing: |
| Indicator . | Measured factor . | Measurement/assessment method . |
|---|---|---|
| Measure and assess the learning (i.e.knowledge and skills gained by theaudience as a result of the awareness), andthe impact on the audience's performanceand attitude toward cybersecurity. | Impact of awareness on: It also comprises touchability. | ○ Data from audits and riskdepartments. ○ Count and severity of securityincidents occurred due to staffbehaviors. ○ Other best behavior data that canbe automatically collected (e.g.anti-virus and firewall log data,and helpdesk data). |
| Measure the direct and indirect valuesadded to the organizations as a result ofimplementing CSA. These indicators arecritical for the management or sponsors intheir decision-making on whether to investin the program or not, and this is necessaryfor the continuity of the program. | Impact of awareness in the change of: Change in top management and sponsorsupport and commitment for theawareness program | ○ Recognition of securitycontributions, e.g. count andreputation of awards and contestswon due to the awarenessprogram. ○ Percentage of awarenessprocesses incorporated in theorganization's policies, processes,and arrangement |
| Measure the quality of resources anddelivery channels used in the awarenessprogram. | Quality of awareness resources. Effectiveness of awareness resources.For example, whether the content wasrelevant and easy to follow or not, what werethe strengths and weaknesses of the program,and whether the delivery methods were ableto accommodate the audience's pace andlearning style or not. It comprises of usabilityand reachability. | • Survey to evaluate (using closedquestions/quantitative, such as Likertscale).○ Relevancy of topics.○ Content quality.○ Delivery assessment.• Percentage of security topics coveredwith respect to expected topics to becovered to know if all relevant ordemanded topics are covered or not. |
| • System and log data analysis (e.g.,attendance, website visit, emailrecipient, etc.) to determine if the targetgroup has access to the awarenessresources or not. | ||
| Measure how the audiences, sponsor, andsenior management have perceived orreacted to the awareness program. | Interest, support, commitment, andparticipation of different stakeholdersin the program. | Interest and active participation evaluatedusing: |
Furthermore, an evaluation should not be limited to what factors to measure and how to measure them, but should also cover whom they have been measured for. This will help in the complete evaluation (i.e. from the perspective of all important stakeholders like CSA professionals, management/sponsors, and an audience group) and at the same time provide an idea of who will participate in the evaluation process. Outcomes from the evaluation of impact factors and accessibility factors are more connected to the CSA professionals, who are responsible for updating and adjusting the CSA program for future iterations. Whereas evaluation results of sustainability indicators and monitoring indicators are helpful for the management or sponsor in deciding whether to continue investing in the existing awareness program or have to look for an alternative.
Other important aspects are a proper visualization of the evaluation results and automation of the measurement processes [ 18 ]. For the visualization of evaluation results, a scorecard can be a potential option [ 5 , 18 ]. Likewise, several tools are available that can be used to automate data collection processes using surveys, tests, and passive data; however, to use them could demand a certain set of technical skills.
Different from the works discussed in the section Related Works, our proposed metrics have given equal importance to the evaluation of the sustainability indicators. Sustainability can be expressed in terms of the program outcome's ability to exist constantly by influencing organizational policies, arrangements, and regulatory framework. It can also be expressed in terms of the program's ability to exist constantly in the organization by becoming a part of the organizational policies and receiving abundant funds. CSA is a continuous process, and the evaluation process is similarly iterative. Without the evaluation of the sustainability indicator, the continuity of the process itself can become questionable. More importantly, the evaluation should seek input from all of those involved and affected by a CSA program. This is possible only by ensuring that diverse viewpoints from different stakeholders are considered so that the results are as complete and unbiased as possible. Ironically, none of the work discussed in the section Related Works has clearly considered this aspect and has based its evaluation completely on the audience's viewpoint. Indeed, the audience assessment and feedback are important, but to yield a more balanced and holistic picture of the awareness program, it is necessary to measure how well the expectations of each stakeholder are met. This can provide critical insight and guidance to adjust the awareness program for future iterations.
The proposed metrics can guide the evaluation process of a CSA program; however, they do not answer what score is an acceptable level of awareness [ 21 , 26 ]. This is an important question, but is contextual and will vary depending on the target topic and audience type. For example, if the target audience is healthcare or banking staff, the only acceptable score will presumably be the maximum. Therefore, it is necessary to set a benchmark expectation from the CSA program [ 4, 5 ]. Further, for any evaluation, there needs to be clarity about what will be considered a quality and ethical evaluation [ 90 ]. This could vary depending on organizational policies, laws, and regulations. Some organizations could have in place particular evaluation standards and/or ethical guidelines to guide the evaluation. The most important thing is to approach it methodically and attentively to avoid any unforeseen repercussions, unnecessary interruptions, or meaningless outcomes.
The evaluation of a CSA program is an important activity in the post-implementation phase. Evaluation is necessary to know how effective and successful the program was. Moreover, it provides information on which aspects of the program require improvement and also information used by senior management/sponsor in deciding whether to invest further in the program.
In spite of all the benefits of evaluation, there does not exist a consensus on what to measure and how to measure while evaluating a CSA program. This may be because different target groups have varying needs and environments determining the content of their CSA programs; so generalized evaluation metrics cannot capture the rationale behind an evaluation strategy. Ironically, this lack of evaluation metrics for CSA has caused more harm than good: e.g. many organizations and individuals either abandon the evaluation process or limit their evaluation to some weak or irrelevant factors and indicators. Therefore, in this paper, we have designed and proposed evaluation metrics for CSA that we believe are widely applicable.
In order to do so, we performed a systematic literature review of 32 past studies that have evaluated or proposed methods to evaluate a CSA program. We gathered the relevant papers after multiple rounds of screening. A review of the gathered papers followed this, mainly to extract information on what factors past studies measured and how they measured them to evaluate or assess the effectiveness and success of a CSA program. Analysis of the collected data revealed that factors measured by the past studies can be classified into behavior, attitude, knowledge, interest, reachability, touchability, value-added, usability, and overall feedback. Among all the factors measured, behavior, attitude, and knowledge are the most popular factors. Similarly, methods used to measure these factors can be categorized into a survey, test, passive data, face-to face-interaction, and observation, where survey and passive data are found to be the most popular.
Using the obtained findings, criteria for good metrics, and the ELINET's four indicators (i.e. impact, sustainability, accessibility, and monitoring), we have designed and proposed new metrics for the evaluation of a CSA program. Our proposition provides factors to be measured and their respective measurement methods in order to realize each of the indicators.
The impact indicator is realized by measuring positive changes in cybersecurity knowledge, attitude, and behavior due to the CSA program using methods like online surveys, tests (web-based, tool-based, and simulated), and statistical analysis of relevant passive data.
Similarly, the sustainability indicator is realized by measuring the changes in organizational policies, regulatory framework, and organizational arrangement due to CSA. Moreover, it is also realized by measuring the change in senior management and sponsor support, and commitment to CSA. The sustainability indicator is measured using statistical analysis of relevant passive data like the percentage of awareness outcomes integrated into the organizational process, policy, and arrangements; cost-benefit analysis; and changes in funds and resources allocated for the program.
Next, the accessibility indicator is realized by measuring the relevancy of topics, quality of materials, and appropriateness of delivery channels using methods like surveys, the percentage of relevant topics covered, and statistical analysis of relevant passive data like audience interest in the awareness program.
Finally, the monitoring indicator is realized by measuring stakeholders' interest and participation in the awareness program using passive data analysis and post-program surveys.
We believe our proposition is inclusive of all directly affected stakeholders, i.e. management, CSA professionals, and target audiences. More importantly, the proposed metrics have considered various important aspects, such as criteria for good metrics, different stakeholder needs, and the sustainability of the program in order to make the evaluation process inclusive, complete, and unbiased as far as possible.
The authors would like to thank David Goodman (Trust in Digital Life, Belgium) and Pasquale Annicchino (Archimede Solutions SARL, Switzerland) for reviewing the deliverable report submitted to the CyberSec4Europe.
This work has financially been supported by the CyberSec4Europe project (grant agreement no. 830929). This paper is an extended and revised version of the deliverable report [ 32 ] that was submitted to CyberSec4Europe WP9: dissemination, outreach, spreading of competence, and raising awareness.
Williams S . More than half of personal data breaches caused by human error . IT Brief . 2019 .
Google Scholar
IBM Global Technology Services , IBM Security Services 2014 Cyber Security Intelligence Index Analysis of cyber attack and incident data from IBM's worldwide security operations . Somers : IBM Corporation . 2014 .
Kaspersky . The human factor in IT security: How employees are making businesses vulnerable from within . Kaspersky Daily . 2018 .
Wilson M , Hash J . Building an information technology security awareness and training program . https://nvlpubs.nist.gov/nistpubs/Legacy/SP/nistspecialpublication800-50.pdf . (20 September 2020, date last accessed ).
ENISA . The new users' guide: How to raise information security awareness . https://www.enisa.europa.eu/publications/archive/copy_of_new-users-guide/at_download/fullReport . 2010 . (20 September 2020, date last accessed ).
Hänsch N , Benenson Z . Specifying IT security awareness . In: Proceedings of the Twenty-fifth International Workshop on Database and Expert Systems Applications , Munich , 2014 .
Google Preview
Bada M , Sasse AM , Nurse JR . Cyber security awareness campaigns: why do they fail to change behaviour? . In: Proceedings of the International Conference on Cyber Security for Sustainable Society , Coventry , 2015 .
Katsikas S . Health care management and information system security: awareness, training or education? . Int J Med Inf . 2000 ; 60 : 129 – 35 .
McCrohan KF , Engel K , Harvey JW . Influence of awareness and training on cyber security . J Internet Commer . 2010 ; 9 : 23 – 41 .
Furnell S , Vasileiou I . Security education and awareness: just let them burn? . Netw Secur . 2017 ; 2017 : 5 – 9 .
ENISA . Information security awareness initiatives: current practice and the measurement of success . https://ifap.ru/library/book206.pdf . (20 September 2020, date last accessed ).
Rohlich N , Haas P , Edwards F . Exploring the effectiveness of transit security awareness campaigns in the San Francisco Bay area . https://transweb.sjsu.edu/research/Exploring-Effectiveness-Transit-Security-Awareness-Campaigns-San-Francisco-Bay-Area . (20 September 2020, date last accessed ).
Spitzner L . Security awareness metrics . https://www.sans.org/security-awareness-training/blog/security-awareness-metrics . (20 September 2020, date last accessed ).
Timmermans B , Cleeremans A . How can we measure awareness? An overview of current methods . In: Overgaard M (ed.), Behavioural Methods in Consciousness Research , Oxford : Oxford University Press , 2015 , 21 – 46 .
Fogg B . A behavior model for persuasive design . In: Proceedings of the Fourth International Conference on Persuasive Technology , Claremont, CA , p. 26 – 9 .. 2009 .
Richardson R . CSI computer crime & security survey . http://www.sis.pitt.edu/jjoshi/courses/IS2150/Fall11/CSIsurvey2008.pdf . (20 September 2020, date last accessed ).
Monaha D . Security Awareness Training: It's Not Just For Compliance . Boulder : Enterprise Management Associates (EMA) , 2014 .
Fertig T , Schütz AE , Weber K . Current issues of metrics for information security awareness . In: Proceedings of the Twenty-Eighth European Conference on Information Systems , Virtual conference , Marrakech , p. 15 – 7 .. 2020 .
Spitzner L , deBeaubien D , Ideboen A . Security awareness report . Bethesda, MD : SANS Institute , 2019 .
Dixson DD , Worrell FC . Formatibe and summative assessment in the classroom . Theory Into Practice . 2016 ; 55 : 153 – 9 .
Manifavas C , Fysarakis K , Rantos K et al. DSAPE: dynamic security awareness program evaluation . In: Proceedings of the Sixteenth International Conference on Human-Computer Interaction , Crete , p. 258 – 69 .. 2014 .
Bada M , Nurse JRC . Developing cybersecurity education and awareness programmers for small and medium-sized enterprises (SMEs) . Inf Comput Secur . 2019 ; 27 : 393 – 410 .
Gattiker UE . Can an early warning system for home users and SMEs make a difference? A field study . In: Proceedings of the International Workshop on Critical Information Infrastructures Security , Samos Island , 2006 .
Shaw R , Chen CC , Harris AL et al. The impact of information richness on information security awareness training effectiveness . Comput Edu . 2009 ; 52 : 92 – 100 .
Bitton R , Boymgold K , Puzis R et al. Evaluating the information security awareness of smartphone users . In: Proceedings of the 2020 CHI Conference on Human Factors in Computing Systems (CHI'20) , Honolulu, HI , p. 25 – 30 .. 2020 .
Kruger H , Kearney W . A prototype for assessing information security awareness . Comput Secur . 2006 ; 25 : 289 – 96 .
Webster J , Watson RT . Analyzing the past to prepare for the future: writing a literature review . MIS Quart . 2002 ; 26 : xiii – xxiii .
Google Scholar . https://scholar.google.com/intl/en/scholar/about.html . (7 July 2021, date last accessed ).
Microsoft Academic . https://academic.microsoft.com/faq . (7 July 2021, date last accessed ).
Kitchenham B Procedures for Performing Systematic Reviews . Keele : Software Engineering Group, Department of Computer Science, Keele University , 2004 .
Paez A . Gray literature: an important resource in systematic reviews . J Evid Based Med . 2017 ; 10 : 233 – 40 .
Chaudhary S , Gkioulos V . D9.13 Awareness effectiveness study . 2021 . ( 16 February 2021, date last accessed ).
Chaudhary S , Gkioulos V , Goodman D . D9.11: SME cybersecurity awareness program 2 . https://cybersec4europe.eu/wp-content/uploads/2021/05/D9.11-SME-cybersecurity-awareness-program-2-FINAL-submitted-1.pdf . (14 July 2021, date last accessed ).
Dodge RC , Ferguson AJ . Using phishing for user email security awareness . In: Security and Privacy in Dynamic Environments . Proceedings of the IFIP TC-11 Twenty-First International Information Security Conference (SEC 2006) , Karlstad , p. 22 – 4 .. 2006 .
Kruger HA , Drevin L , Steyn T . A framework for evaluating ICT security awareness . In: Proceedings of the ISSA 2006 from Insight to Foresight Conference, July 5-7 . Sandton . 2006 .
Kruger H , Drevin L , Steyn T . A vocabulary test to assess information security awareness . Inf Manag Comput Secur . 2010 ; 18 : 316 – 27 .
Albrechtsen E , Hovden J . Improving information security awareness and behavior through dialogue, participation, and collective reflection: an intervention study . Comput Secur . 2010 ; 29 : 432 – 45 .
Khan B , Alghathbar KS , Nabi SI et al. Effectiveness of information security awareness methods based on psychological theories . Afr J Bus Manag . 2011 ; 5 : 10862 – 8 .
Wolf M , Haworth DA , Pietron L . Measuring an information security awareness program . Rev Bus Inf Syst . 2011 ; 15 : 9 – 22 .
Ahlan AR , Lubis M . Information security awareness in university: maintaining learnability, performance, and adaptability through roles of responsibility . In: Proceedings of the Seventh International Conference on Information Assurance and Security (IAS) , Melaka , p. 5 – 8 ., 2011 .
Tsohou A , Karyda M , Kokolakis S et al. Analyzing trajectories of information security awareness . Inf Technol People . 2012 ; 25 : 327 – 52 .
Bauer S , Bernroider EW , Chudzikowski K . End user information security awareness programs for improving information security in banking organizations: preliminary results from an exploratory study . In: Proceedings of the AIS SIGSEC Workshop on Information Security & Privacy (WISP2013) , Milano . 2013 .
Gundu T , Flowerday S . Ignorance to awareness: towards an information security awareness process . South Afr Inst Elect Eng . 2013 ; 104 : 69 – 79 .
Velki T , Solic K , Ocevcic H . Development of user's information security awareness questionnaire (UISAQ) . In: Proceedings of the International Convention MIPRO , Opatija , p. 26 – 30 .. 2014 .
Prah ANW , Otchere AA , Opan KE . The perceived effectiveness of information security awareness . Inf Knowl Manag . 2016 ; 6 : 62 – 73 .
Scholl MC , Leiner B , Fuhrmann F . Blind spot: do you know the effectiveness of your information security awareness raising program? . Syst Cybernet Inf . 2017 ; 15 : 58 – 62 .
Carella A , Kotsoev M , Truta TM . Impact of security awareness training on phishing click-through rates . In: Proceedings of the IEEE International Conference on Big Data , Boston, MA , p. 11 – 4 .. 2017 .
Wahyudiwan DDH , Sucahyo YG , Gandhi A . Information security awareness level measurement for employee: case study at Ministry of Research, Technology, and Higher Education . In: Proceedings of the Third International Conference on Science in Information Technology , Bandung , p. 25 – 6 .. 2017 .
Shamsi AAA . Effectiveness of cyber security awareness program for young children: a case study in UAE . Int J Inf Technol Lang Stud . 2019 ; 3 : 8 – 29 .
Gundu T , Flowerday S , Renaud K . Deliver security awareness training, then repeat: {Deliver, Measure Efficacy} . In: Prroceedings of the Conference on Information Communications Technology and Society (ICTAS) , Durban , March 6-8 , 2019 .
Ikhalia E , Serrano A , Bell D et al. Online social network security awareness: mass interpersonal persuasion using a Facebook app . Inf Technol People . 2019 ; 32 : 1276 – 300 .
Tschakert KF , Ngamsuriyaroj S . Effectiveness of and user preferences for security awareness training methodologies . Heliyon . 2019 ; 5 : e02010 .
Haney J , Lutters W . Security awareness training for the workforce: moving beyond “check-the-box” compliance . Computer . 2020 ; 53 : 91 – 5 .
Parsons K , McCormac A , Pattinson M et al. A study of information security awareness in Australian government organisations . Inf Manag Comput Secur . 2014 ; 22 : 334 – 45 .
Kaur J , Mustafa N . Examining the effects of knowledge, attitude and behaviour on information security awareness: A case on SME . In: Proceedings of the International Conference on Research and Innovation in Information Systems (ICRIIS) , Kuala Lumpur , 2013 .
Labuschagne W , Eloff M . The effectiveness of online gaming as part of a security awareness program . In: Proceedings of the Thirteenth European Conference on Cyber Warfare and Security , Piraeus , July 3–4 , 2014 .
Koyuncu M , Pusatli T . Security awareness level of smartphone users: an exploratory case study . Mob Inf Syst . 2019 ; 2019 : 1 – 11 .
Ahlan AR , Lubis M , Lubis AR . Information security awareness at the knowledge-based institution: its antecedents and measures . Proc Comput Sci . 2015 ; 72 : 361 – 73 .
Chen CC , Medlin BD , Shaw R . A cross-cultural investigation of situational information security awareness programs . Inf Manag Comput Secur . 2008 ; 16 : 360 – 76 .
Eminağaoğlu M , Uçar E , Eren Ş . The positive outcomes of information security awareness training in companies: a case study . Inf Secur Tech Rep . 2009 ; 14 : 223 – 9 .
Rantos K , Fysarakis K , Manifavas C . How effective is your security awareness program? An evaluation methodology . Inf Secur J Glob Perspect . 2012 ; 21 : 328 – 45 .
Talib S , Clarke NL , Furnell SM . An analysis of information security awareness within home and work environments . In: Proceedings of the International Conference on Availability, Reliability and Security , Krakow , 2010 .
Bulgurcu B , Cavusoglu H , Benbasat I . Information security policy compliance: an empirical study of rationality-based beliefs and information security awareness . MIS Quart . 2010 ; 34 : 523 – 48 .
Kruse S , Pankey B . Assessing the effectiveness of security awareness training . http://www.securitymetrics.org/attachments/Metricon-6.5-Kruse.pdf . (20 September 2020, date last accessed ).
Beyer M , Ahmed S , Doerlemann K et al. Awareness is only the first step: a framework for progressive engagement of staff in cyber security . https://www.riscs.org.uk/wp-content/uploads/2015/12/Awareness-is-Only-the-First-Step.pdf . (20 September 2020, date last accessed ).
Parsons K , McCormac A , Butavicius M et al. Determining employee awareness using the Human Aspects of Information Security Questionnaire (HAIS-Q) . Comput Secur . 2014 ; 42 : 165 – 76 .
Egelman S , Peer E . Scaling the security wall: developing a security behaviour intention scale (SeBIS) . In: Proceedings of the Thirty-Third Annual ACM Conference on Human Factors in Computing Systems , Seoul , April 18-23 . 2015 .
Faklaris C , Dabbish L , Hong JI . A self-report measure of end-user security attitudes (SA-6) . In: Proceedings of the USENIX Symposium on Usable Privacy and Security (SOUPS) , Santa Clara, CA , August 11–13 . 2019 .
Rajivan P , Moriano P , Kelley T et al. Factors in an end user security expertise instrument . Inf Comput Secur . 2017 ; 25 : 190 – 205 .
Hadlington L . Human factors in cybersecurity, examining the link between Internet addiction, impulsivity, attitudes towards cybersecurity, and risky cybersecurity behaviours . Heliyon . 2017 ; 3 : e00346 .
Coutlee CG , Politzer CS , Hoyle RH et al. An abbreviated impulsiveness scale (ABIS) constructed through confirmatory factor analysis of the BIS-11 . Arch Sci Psychol . 2014 ; 2 : 1 – 12 .
Davis RA , Flett GL , Besser A . Validation of a new scale for measuring problematic internet use: implications for pre-employment screening . Cyberpsychol Behav . 2002 ; 5 : 331 – 45 .
Ög˘ütçü G , Testik ÖM , Chouseinoglou O . Analysis of personal information security behavior and awareness . Comput Secur . 2016 ; 56 : 83 – 93 .
Huang HY , Demetriou S , Banerjee R et al. Smartphone security behavioral scale: a new psychometric measurement for smartphone security . https://arxiv.org/abs/2007.01721 . (26 August 2020, date last accessed ).
Velki T , Solic K , Ocevcic H . Development of Users' Information Security Awareness Questionnaire (UISAQ)—ongoing work . In: Proceedings of the Thirty-Seventh International Convention on Information and Communication Technology, Electronics and Microelectronics (MIPRO) , Opatija , May 26–30 . 2014 .
Caballero A . Security education, training, and awareness . In: Computer and Information Security Handbook , Burlington : Morgan Kaufmann Publishers , 2017 , 497 – 505 .
Spitzner L . Security awareness for senior management . ( 29 July 2021, date last accessed ).
Peltier TR . Implementing an information security awareness program . Inf Syst Secur . 2005 ; 14 : 37 – 49 .
Abawajy J . User preference of cyber security awareness delivery methods . Behav Inf Technol . 2014 ; 33 : 237 – 48 .
Nachin N , Tangmanee C , Piromsopa K . How to increase cybersecurity awareness . ISACA J . 2019 ; 2 : 45 – 50 .
González CSG , Toledo P , Izquierdo FB . Integrating the principles of DGBL, CSCL and playability in the design of social videogames: a case of study . In: Student Usability in Educational Software and Games: Improving Experiences , Hershey , IGI Global , 2012 , 293 – 304 .
Mabitle K , Kritzinger E . Schoolteacher preference of cyber-safety awareness delivery methods: a South African study . In: Silhavy R. (eds), Artificial Intelligence and Bioinspired Computational Methods. CSOC 2020. Advances in Intelligent Systems and Computing , Cham : Springer , 2020 .
Ainley M , Hidi S , Berndroff D . Interest, learning, and the psychological processes that mediate their relationship . J Educ Psychol . 2002 ; 94 : 545 – 61 .
Rounds J , Su R . The nature and power of interests . Curr Dir Psychol Sci . 2014 ; 23 : 98 – 103 .
Shen X , Eades P , Hong S et al. Intrusive and non-intrusive evaluation of ambient displays . In: Proceedings of the First International Workshop on Ambient Information Systems, Collocated at Pervasive , Toronto , 2007 .
Volkamer M , Sasse MA , Boehm F . Analysing simulated phishing campaigns for staff . In: Proceedings of the ESORICS Second Workshop on Security, Privacy, Organizations, and Systems , Guildford , 2020 .
Dupuis MJ , Smith S . Clickthrough testing for real-world phishing simulations . In: Proceedings of the Twenty-First Annual Conference on Information Technology Education , Online event , 2020 .
Mustaca S Define S.M.A.R.T IT Security Goals. (ISC)2 . https://blog.isc2.org/isc2_blog/2013/02/define-smart-it-security-goals.html . (23 March 2021, date last accessed ), 2013 .
Ceneric I , Looney J , Greef Md . Indicators for Evaluation of Awareness and Fundraising for Low Literacy in Europe . Brussels : ELINET- European Literacy Policy Network , 2014 .
BetterEvaluation . Define ethical and quality evaluation standards . https://www.betterevaluation.org/en/rainbow_framework/manage/define_ethical_and_quality_evaluation_standards . (23 July 2012, date last accessed ).
Author notes
| Month: | Total Views: |
|---|---|
| May 2022 | 329 |
| June 2022 | 756 |
| July 2022 | 653 |
| August 2022 | 641 |
| September 2022 | 787 |
| October 2022 | 1,272 |
| November 2022 | 864 |
| December 2022 | 694 |
| January 2023 | 732 |
| February 2023 | 716 |
| March 2023 | 719 |
| April 2023 | 646 |
| May 2023 | 570 |
| June 2023 | 516 |
| July 2023 | 627 |
| August 2023 | 556 |
| September 2023 | 822 |
| October 2023 | 885 |
| November 2023 | 1,026 |
| December 2023 | 802 |
| January 2024 | 943 |
| February 2024 | 1,137 |
| March 2024 | 1,598 |
| April 2024 | 1,424 |
| May 2024 | 1,324 |
| June 2024 | 1,161 |
| July 2024 | 919 |
| August 2024 | 711 |
Email alerts
Citing articles via, affiliations.
- Online ISSN 2057-2093
- Print ISSN 2057-2085
- Copyright © 2024 Oxford University Press
- About Oxford Academic
- Publish journals with us
- University press partners
- What we publish
- New features
- Open access
- Institutional account management
- Rights and permissions
- Get help with access
- Accessibility
- Advertising
- Media enquiries
- Oxford University Press
- Oxford Languages
- University of Oxford
Oxford University Press is a department of the University of Oxford. It furthers the University's objective of excellence in research, scholarship, and education by publishing worldwide
- Copyright © 2024 Oxford University Press
- Cookie settings
- Cookie policy
- Privacy policy
- Legal notice
This Feature Is Available To Subscribers Only
Sign In or Create an Account
This PDF is available to Subscribers Only
For full access to this pdf, sign in to an existing account, or purchase an annual subscription.
Security Awareness Essays
Key metrics for measuring the success of the security awareness training program, popular essay topics.
- American Dream
- Artificial Intelligence
- Black Lives Matter
- Bullying Essay
- Career Goals Essay
- Causes of the Civil War
- Child Abusing
- Civil Rights Movement
- Community Service
- Cultural Identity
- Cyber Bullying
- Death Penalty
- Depression Essay
- Domestic Violence
- Freedom of Speech
- Global Warming
- Gun Control
- Human Trafficking
- I Believe Essay
- Immigration
- Importance of Education
- Israel and Palestine Conflict
- Leadership Essay
- Legalizing Marijuanas
- Mental Health
- National Honor Society
- Police Brutality
- Pollution Essay
- Racism Essay
- Romeo and Juliet
- Same Sex Marriages
- Social Media
- The Great Gatsby
- The Yellow Wallpaper
- Time Management
- To Kill a Mockingbird
- Violent Video Games
- What Makes You Unique
- Why I Want to Be a Nurse
- Send us an e-mail

IMAGES
COMMENTS
Cyber Security Essay. Cybersecurity means protecting data, networks, programs and other information from unauthorized or unattended access, destruction or change. In today's world, cybersecurity is very important because of some security threats and cyber-attacks. For data protection, many companies develop software.
200 Words Essay On Cyber Security. School students are the future of our society, and it's important to teach them the importance of cyber security from an early age. Cyber security is an ever-increasing problem in our digital world, and it's up to us to ensure that our students are aware of the risks and dangers that come with the internet.
Cryptographic Algorithms: The Use in Cyber Security. Cryptographic protection of a system depends on two factors, 1) the strength of the keys and effectiveness of associated protocols, and 2) protection of said keys via key management. Facebook Compatibility with Padgett-Beale Cybersecurity Philosophy.
Long Essay on Cyber Security is usually given to classes 7, 8, 9, and 10. The main definition of cyber security is protecting networks, data, programs, and other information from unattended or unauthorized access, change, or destruction. Around the globe nowadays, cyber security is very vital because of some cyber-attacks and cyber-attacks.
The Cyber security is the need of today's time. The world is getting on increasingly digital. Here in point, there comes the needs for us to strengthen our cyber security to face possible risk and cyber challenges. ... Essay on Cyber Security, its Meaning & Importance ... awareness of updated network and system security settings and the use ...
Cyber Security Conceptual or Substantive Assumptions Cybersecurity is fast approaching a place where it is becoming a form of currency with consumers and clients. It is only in the past decade that digital environments became a normal and typical way to transact business. Consumers and clients quite rapidly adapted to the convenience of conducting business and managing their finances in online ...
Cybersecurity Fast Facts. 20% of Gen Zers and 18% of Millennials have had their identity stolen at least once. 2.76 million cybercrime complaints reported to the FBI from 2017-2021. $18 billion in total losses due to cybercrime from 2017-2021. 6.95 million new phishing and scam pages created in 2021.
Cyber Security is a crucial topic in today's digital world. Writing an essay about Cyber Security can help raise awareness and understanding of the importance of protecting our online information and systems. It is essential to educate people about the potential risks and the measures they can take to stay safe in the digital world. Choosing a ...
15 Cyber Security Essay Topics In the following section, you will find unique ideas for your essay on cyber security. Choose the most appropriate one and create your outstanding paper. Don't forget to compose a catchy introduction, a clear thesis statement, and a dynamic conclusion. You can get more ideas by using our topic generator. Or come ...
29 essay samples found. Cybersecurity, a critical concern in our digitally connected world, encompasses practices, technologies, and policies to protect networks, devices, programs, and data from attack or unauthorized access. Essays could delve into the myriad types of cyber threats like malware, phishing, and ransomware, exploring their ...
Integrating workers into security prevention is through implementing information security awareness (ISA) programs. Such programs aim to improve workers' perception of the cyber security risk as credible and teach how to prevent risks (Bada et al., 2019). Hence, ISA aims to teach people to be aware of the potential cyber threats and respond ...
Cyber Security Essays Are All About Structure and Coherence! As discussed in the article, a good essay is all about adhering to the basics. Have a solid structure and make a coherent argument. However, if you want to stand out, you must demonstrate cyber security awareness by incorporating real world examples in your work. Additionally, carry ...
Better Cybersecurity Awareness Through Research. In the last few years, information security professionals have faced tremendous challenges. Just in 2021, there were more than two billion malware attacks and trillions of intrusion attempts. 1 Ransomware attacks alone have increased by 151 percent compared with 2020. 2 In fall of 2020 ...
While cybersecurity awareness is the first step, employees must willingly embrace and proactively use cyber-secure practices both professionally and personally for it to truly be effective. This ...
Cyber security may also be referred to as information technology security." (Lord, 2019). Which is an important part of networking and business security that is required to ensure our security in all aspects of our daily lives. Cybersecurity is important due to the amount of sensitive information that is stored on many different computer ...
Cybersecurity awareness includes being aware of the latest security threats, cybersecurity best practices, the dangers of clicking on a malicious link or downloading an infected attachment, interacting online, disclosing sensitive information and so on. Security awareness training programs help to enhance your organization's security posture ...
Cetin & Hamdullah Nejat Basim (2020): Cyber Security Awareness, Knowledge and Behavior: A Comparative Study, Journal of Computer Information Systems, DOI: 10.1080/08874417.2020.1712269
Cyber Security Awareness Essay. 1623 Words7 Pages. 1. What is Cyber security Awareness? Let's start by a brief description of what Cyber is, then cyber-crime, and then elaborate on Cyber security. We will have to educate our citizens on how to protect themselves from cyber -crime, cyber. Cyber is the prefix used in computers, systems ...
AI cybersecurity awareness topics to teach employees include the danger of feeding confidential or sensitive data into these tools, and the use of generative AI by threat actors to create convincing phishing emails or other scams. 12. Physical Security. Somewhat surprisingly, physical security and cybersecurity are closely linked.
Cybersecurity Best Practices, Partnerships and Collaboration. The CISA Cybersecurity Awareness Program is a national public awareness effort aimed at increasing the understanding of cyber threats and empowering the American public to be safer and more secure online. Cybersecurity is a shared responsibility and we each have a part to play.
A cyber security awareness is an important to protect our data from the cyber attacks, and unknown login. We need to get aware from the online threats like phishing and malware that cybercriminals use to steal our data. We need to identify and avoid frauds that are conducted online, via email, or on social media. Importance of Cybersecurity ...
Goal: raise awareness of security best practices; objectives: use of password security, practice social media safety, practice malware protection, practice mobile security, awareness of phishing, and so on. In addition, the evaluation process must be cost-effective (or inexpensive) to conduct and its results are useful for decision-making.
This is why most security awareness programs fail. The increasing number of data breaches and other cyber-attacks clearly demonstrate that these tips are not enough to raise public security awareness to a level required to create a secure cyber culture. A security awareness program is difficult to implement (Manke & Winkler, 2013).
Key Metrics for Measuring the Success of the Security Awareness Training Program. One way to measure the success of a security awareness program is to note the behaviors a firm desires to tackle and use the data collected to develop a clear, actionable method. Nevertheless, most cyber security leaders need a suitable framework to measure the ...