- Help Center
- Chrome Enterprise and Education
- Privacy Policy
- Terms of Service
- Submit feedback

techlauve.com – a knowledge base for IT professionals.
Inhale problems, exhale solutions..
- Nick’s Blog
- Active Directory
- Privacy Policy
« Outlook: “Sending and Receiving reported error (OX80040600)”
Terminal Server Does Not Accept Enough Client Connections »
Adding Sites to Internet Security Zones Using Group Policy
Sometimes it is useful to leverage the power of Group Policy in Active Directory to add sites to certain security zones in Internet Explorer. This can save the network admin the trouble of managing the security zone lists for each computer (or user) separately. In the following example, each user on the network needs to have a specific site added to the Trusted Sites list.
This tutorial assumes that group policy is in good working order on the domain and that all client users and computers can access the directory.
- Open the Group Policy Management MMC console.
- Right-click the organization unit (OU) that the policy should apply to, taking special care to consider whether the policy should apply to computers or users on this particular network.
- Select “Create and Link a GPO Here…” to create a new group policy object.
- In the “New GPO” window, enter a good, descriptive name for this new policy and click “OK”. (ex. “Trusted Sites Zone – Users” or something even more descriptive)
- Locate the newly created GPO in the left-side navigation pane, right-click it and select “Edit…”
- Expand “Administrative Templates” under either “Computer Configuration” or “User Configuration” depending on which type of OU the new policy was linked to in step 2.
- The path to the settings that this example will be using is: Administrative Templates -- Windows Components -- Internet Explorer -- Internet Control Panel -- Security Page
- In the right-hand pane, double-click “Site to Zone Assignment List”.
- Enable the policy and click the “Show…” button next to “Enter the zone assignments here.” This will pop up the “Show Contents” window.
- Click the “Add…” button. This will pop up the “Add Item” window.
- In the first box, labeled “Enter the name of the item to be added:”, enter the URL to the site. (ex. https://secure.ourimportantwebapp.com) . Keep in mind that wildcards can be used. (ex. https://*.ourimportantdomain.com) . Leave off any trailing slashes or sub-folders unless that type of specific control is called for.
- 1 – Intranet Zone
- 2 – Trusted Sites Zone
- 3 – Internet Zone
- 4 – Restricted Sites Zone
- Once the zone assignment has been entered, click “OK”. This will once again show the “Show Contents” window and the new entry should be present.
- Click “OK” and “OK” again to get back to the Group Policy Management Console.
The new policy will take effect at the next group policy refresh interval, which is usually 15 minutes. To test immediately, run a gpupdate /force on a user/computer that falls into the scope of the new policy and go to “Tools -> Internet Options -> Security -> Trusted Sites -> Sites”. The site(s) added should be in the list. If the sites do not show up, check the event logs for any group policy processing errors.
Related content:
- How To: Time Sync Across Windows Network
- Group Policy Not Applied To Remote VPN Users
- QuickBooks Payroll Opens/Saves the Wrong W2 Form
- Microsoft Virtual Server Web Console Constantly Asks For Password
- Group Policy: Applying Different User Policies to the Same User for Workstations and Terminal Server
No comment yet
Juicer breville says:.
November 26, 2012 at 12:11 am (UTC -5)
Hurrah, that’s what I was looking for, what a information! existing here at this web site, thanks admin of this web page.
Leave a Reply Cancel reply
Your email address will not be published.
You may use these HTML tags and attributes: <a href="" title=""> <abbr title=""> <acronym title=""> <b> <blockquote cite=""> <cite> <code> <del datetime=""> <em> <i> <q cite=""> <s> <strike> <strong>
Submit Comment
This site uses Akismet to reduce spam. Learn how your comment data is processed .
Remember Me
Connect With Us
Connect with us.
Social Connect by NewsPress
Not finding the answer that you're looking for? Need more help with a problem that is addressed in one of our articles?
techlauve.com is affiliated with Rent-A-Nerd, Inc. in New Orleans, LA.
- DFS Replication (1)
- Group Policy (1)
- Microsoft Exhange (3)
- Microsoft Outlook (11)
- Copiers (1)
- Multi Function Devices (1)
- Printers (2)
- Scanners (1)
- Blackberry (1)
- Firewalls (2)
- Wireless (2)
- Hard Drives (1)
- SAN Systems (1)
- Hyper-V (3)
- Virtual Server (1)
- WordPress (1)
- Security (7)
- QuickBooks (2)
- Quicken (1)
- Antivirus/Antimalware (4)
- Backup Exec (2)
- Internet Explorer (5)
- Microsoft SQL (1)
- Licensing (2)
- Steinberg Nuendo (1)
- Mac OS X (1)
- Server 2003 (12)
- Server 2008 (14)
- Small Business Server 2003 (7)
- Terminal Server (6)
- Updates (2)
- Windows 7 (9)
- Windows XP (11)
- Reviews (1)
- Rent-A-Nerd, Inc.
Except where otherwise noted, content on this site is licensed under a Creative Commons Licence .
Valid XHTML 1.0 Strict Valid CSS Level 2.1
techlauve.com - a knowledge base for IT professionals. uses Graphene theme by Syahir Hakim.
Stack Exchange Network
Stack Exchange network consists of 183 Q&A communities including Stack Overflow , the largest, most trusted online community for developers to learn, share their knowledge, and build their careers.
Q&A for work
Connect and share knowledge within a single location that is structured and easy to search.
Why is SiteToZoneAssignment GPO applying, but sites not appearing in IE
We have a Windows server 2012 R2 remote desktop farm, which we have applied a GPO to, to control site to zone assignments.
This was working fine up until recently, but just lately, we have found that this setting is not applying.
If I toggle ESC on, and then back off on the server I am on, the sites now show up in IE zone list for the currently logged in user. It does not however, seem to apply to all users. That list of sites will then follow them to other servers and that user will be ok moving forward.
We use user profile disks, so the users registry hive is not available on that server unless they are logged in, which might explain why it only occurs for the logged in test user.
EDIT : I can see the registry entries being created under HKCU ZoneMapKey and HKLM ZoneMap.
According to this article, IE should read settings from both of those locations, but they simply do not appear in the site list in IE control panel.
Is it possible that there has been an update for 2012 that has altered some ESC registry setting that causes us this issue?
- group-policy
- windows-server-2012-r2
- internet-explorer
- remote-desktop-services
- windows-update
- Check the zone assignment in the registry, IE ignore esc zone assignment if you have normal zone assignment. – yagmoth555 ♦ Commented Jul 7, 2016 at 11:59
- I have applied the settings under the computer settings in the policy. If I look in HKLM\Software\Policies\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMapKey, I can see all of the entries, they just don't show up in IE itself – James Edmonds Commented Jul 7, 2016 at 13:35
- But ESC is not enabled! – James Edmonds Commented Jul 7, 2016 at 13:49
- I would try HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Internet Explorer\Main\FeatureControl\FEATURE_IGNORE_POLICIES_ZONEMAP_IF_ESC_ENABLED_KB918915\ to 1 anyhow, it's for fixing a bug when ZoneMap is done and ESC is on/off. – yagmoth555 ♦ Commented Jul 7, 2016 at 13:52
- It's tagged for Win2003, but the registry fix work in 2012; support.microsoft.com/en-gb/kb/918915 , they tell HKLM to fix it for all user, or it work too like you told in HCU – yagmoth555 ♦ Commented Jul 7, 2016 at 14:11
3 Answers 3
I created a new user account, and when logged on for the first time, it too experienced the same issue with sites not showing in IE, even though the GPO was applied.
I found in HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap , there is a key called IEHarden (remembered the name back from my 2003 days with a similar ESC kind of issue). It looks like even though the server has ESC turned off, this key is set to 1. When either deleting, or setting this to 0, the sites immediately appear in internet control panel, and works as expected.
So while I know what is causing the problem, and have enough to fudge a workaround by deleting that key for each user on login, I still don't understand why that key is set to 1, or even exists in the first place (some users who could see the sites already, don't even have that key!). Again I can only come back to an update that has messed with IE ESC in some way.
Now have the full answer;
Two of our 8 session host created profiles with the IEHarden key, while the others did not (these two were setup by our consultants, although after asking them they are clueless).
Seems under HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows NT\CurrentVersion\Terminal Server\Install\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap the IEHarden key existed, so was being given to all new profiles created on that server.
Deleted the key from both, and all now back to normal!
Thanks James for posting the info. For anyone who faces this issue the key to look for is:
- Curious about your environment. The OPs info and references solved my related issues. But the key you're describing doesn't exist in my 2012-R2 servers. – bvj Commented Feb 15, 2018 at 8:14
Besides IEHarden under HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap I had in my company also to set IsInstalled at HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Active Setup\Installed Components\{A509B1A8-37EF-4b3f-8CFC-4F3A74704073} to dword:00000000 .
These two registry settings did fully resolve the issue for us. Before IEHarden was somehow set after a certain time back to 1.
You must log in to answer this question.
Not the answer you're looking for browse other questions tagged group-policy windows-server-2012-r2 internet-explorer remote-desktop-services windows-update ..
- The Overflow Blog
- From PHP to JavaScript to Kubernetes: how one backend engineer evolved over time
- Featured on Meta
- We've made changes to our Terms of Service & Privacy Policy - July 2024
- Bringing clarity to status tag usage on meta sites
Hot Network Questions
- Do mini-humans need a "real" Saturn V to reach the moon?
- Difference between 頁 and ページ
- Is the error in translation of Genesis 19:5 deliberate?
- Is it possible to create a board position where White must make the move that leads to stalemating Black to avoid Black stalemating White?
- Distribute realized geometry based on field values
- Did US troops insist on segregation in British pubs?
- Is there any reason for the ark that holds the Torah to be vertical?
- Can the subjunctive mood be combined with ‘Be to+infinitive’?
- What food plants/algae are viable to grow 9,000 meters beneath the sea?
- If physics can be reduced to mathematics (and thus to logic), does this mean that (physical) causation is ultimately reducible to implication?
- Which class is the language MAX-CLIQUE in?
- Submitting a paper as a nonacademic practitioner in a field
- Miracle Miracle Octad Generator Generator
- Short story involving a dystopian future, suspended animation, and a dumbing of society solution
- Picture inside the proof environment
- High CPU usage by process with obfuscated name on Linux server – Potential attack?
- If more collisions happen with more resistance, why less heat is generated?
- If the Collatz conjecture is undecidable, then it is true
- Are there any rockets that leave extra fuel as a backup?
- Vector of integers such that almost all dot products are positive
- How to make a ParametricPlot3D into solid shape
- How can I address my colleague communicating with us via chatGPT?
- Is a probabilistic implementation of unitaries invertible?
- What does "close" mean in the phrase: "close a tooth pick between the jamb and the door"?

- GET STARTED
- Customer Login
- 800.883.8002
Why doesn’t Site to Zone list assignment work with the syntax I provided?
The definitive guide to Site to Zone assignment syntax can be found at: http://evilgpo.blogspot.com/2016/03/internet-explorer-site-to-zone.html
The typical problems are:
- Trying to use two stars like *://*.yourcompany.com,trusted …. INVALID
- www.mycorp.* …INVALID.
- 192.168.*.1 … INVALID.
- *://*.abc.com … INVALID.. two wildcards
See the article for more details.
— More Examples Below —
Valid entries
Www.microsoft.com, https://intranet, https://www.mycorp.com:8080, http://www.mycorp.com/index.html, *://www.microsoft.com, *.mycorp.com, 192.168.1.15, 192.168.1-255.*, http://microsoft.com, invalid entries, *hosts.mycorp.com, www.mycorp.*, www.*.mycorp.com, http*://www.mycorp.com, 192.168.*.1, *.*.mycorp.com.
Remark: In earlier versions of windows, if you provided a wildcard with a second level domain with only two letters ( *.co.uk e.g.), this was an invalid entry. This was to prevent the whole SLD of some countrys to be added. At the time of this writing, this type of entry has become valid in Windows 10.
- PolicyPak Enterprise
- PolicyPak SaaS
- Active Directory
- MDM Providers
- PolicyPak Cloud
- Least Privilege Security Pak
- Device Management Pak
- Windows 10 & 11 Management Pak
- GPO Compliance Pak
- App Browser & Java Security Pak
- App Delivery & Patching Pak
- GPO Reduction & Transition Pak
- Desktop Automation Pak
- Least Privilege Manager
- Device Manager
- File Associations Manager
- Feature Manager
- Start Screen and Taskbar
- GPO Compliance Reporter
- Application Settings Manager
- Browser Router
- Java Rules Manager
- Remote Work Delivery Manager
- Software Package Manager
- Admin Templates Manager
- Preferences Manager
- GPO Export Manager
- Scripts And Triggers Manager
- RDP Manager
- Network Security Manager
- Choosing The Right Edition
- Licensing FAQs
- VDI-licensing-scenarios
- Simplify Windows 10 & 11 Management
- Simplify Group Policy
- Manage Browsers And Java
- Modern Desktop Management
- Bridge Group Policy and MDM
- Manage Secure Remote Work
- Local Admin Rights and Malware
- Simplify VDI Management
- Non Domain-Joined Devices
- Customer Portal Login
- PolicyPak Cloud Login
- Support Center
- PolicyPak Bootcamp
- White Papers
- Case Studies
- Testimonials
- Press Releases
- About Us and You
- Privacy Policy


an endpoint admin's journal
- Recent Posts
- Popular Posts
- Recent Comments

Deploy Trusted sites zone assignment using Intune
November 6, 2023

Zoom Desktop Client – Download older build versions from Zoom
October 31, 2023

Uninstall Teams chat app using remediation script and a configuration profile in Intune
October 30, 2023

Intune Last Check-in date not updating for Windows device
October 25, 2023

How to use Event Viewer to check cause of Blue screen of Death (BSOD)
October 23, 2023
5 Quick Mac OS Terminal commands to make a Mac user life easier

Powershell : Find disabled users and computers in AD
- Active Directory (1)
- Windows (7)
- November 2023
- October 2023
Deploy a set of trusted sites overriding users’ ability to add trusted sites themselves. To acheive this, an Intune configuration profile Trusted site zone assignment can be deployed to devices/users group as required.
Login to Intune Portal and navigate to: Devices > Windows > Configuration Profiles .
Hit the Create button and Select New policy

From the Create a profile menu, select Windows 10 and later for Platform , Templates for Profile type. Select Administrative templates and click Create .

Give the profile desired name and click Next .

In Configurations settings, select Computer Configuration and search for keyword “ Site to Zone “, Site to Zone Assignment List setting will be listed under search results. Go ahead click on it to Select it.

Once selected, a Site to Zone Assignment List page will appear on right side explaining different zones and values required for these zone for setup. Since this profile is being used for trusted sites, we will use the Value “2” . Go ahead and select Enabled button and start entering the trusted sites as required. please ensure to set each value to “2” . See example below:
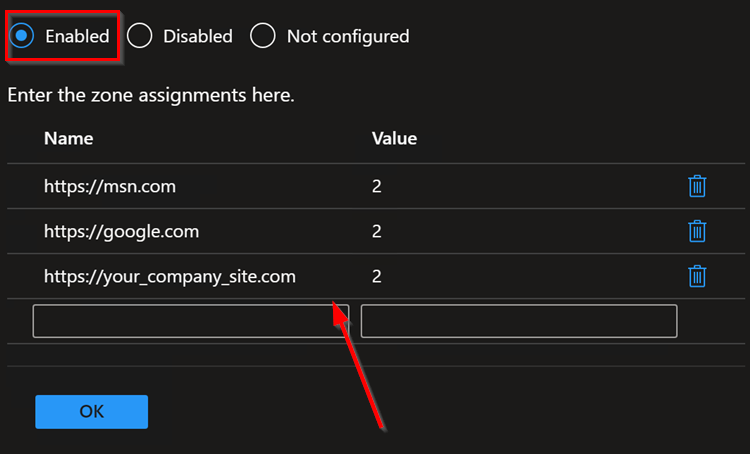
Once done adding the list of sites, click OK to close it and Hit Next on Configuration settings page.
Add Scope tags if needed.
Under Assignments , Click Add groups to target the policy deployment to specific group of devices/users. You can also select Add all users / All all devices .
Hit Next . Then Hit Review + Save button to save.
Tags: Intune Windows
You may also like...

[Windows 10] How to completely uninstall Flash player
- Previous Zoom Desktop Client – Download older build versions from Zoom
thanks! I was just looking for this exact solution!
Stack Exchange Network
Stack Exchange network consists of 183 Q&A communities including Stack Overflow , the largest, most trusted online community for developers to learn, share their knowledge, and build their careers.
Q&A for work
Connect and share knowledge within a single location that is structured and easy to search.
Internet Options to add Trusted Site Greyed Out - SysPreped Windows 10 LTSB
I just deployed an custom Windows 10 ISO I created and I can't set my local file server as a trusted site in internet options. The site button is greyed out. The only change I made in the image was adding the site pre-sysprep and now It not only didn't keep the settings through the sysprep process, but also locked me from making changes to internet options. I did test this image on another computer before adding the site pre-sysprep and post deploy I was able to add the site via normal methods. Clearly somehow adding the site to trusted sites before sysprepping the OS caused the issue. Unfortunatley, this is not an easy computer to re-deploy or I would just remake the ISO and re-deploy.
Update Re Comment [The Goal is to get RID of this Message]:
- I don't use IE or care about its "options", I just want to get rid of this nag message when I run an exe from my fileserver as almost all my software is installed on the server.

- Any idea how I can reset the settings to default?
- How can I add the site via RegEdit? I know I only need to add one site and I use the IP not DNS.
I know the keys are related to HKLM/SOFTWARE/Policies/Microsoft/Windows/CurrentVersion/Internet settings/ , I'm thinking of exporting the entire "tree" from the other computer and importing it here, but that's a hassle as well as its not my computer.
Any ideas!? Thanks!
PS: Windows 10 LTSB v 1607 x64 -Up-2-date

Update: I had IE11 not installed, by installing it, Internet Options now look as they used to, but the option is still greyed out!

Update 2: I have "reset" IE Options, but still Grey :(

- internet-explorer
- internet-security
- I see the same photo. That registry key you mentioned shouldn’t exist at all if you don’t want policies enforced on your browser. Just delete it. Or rename it, if you want to see the effects. – Appleoddity Commented Mar 12, 2018 at 23:49
- I dont really care about IE, my goal is to stop the popup when I run an exe from my file server over SMB. So I'm not sure how to apply that to your comment lol – FreeSoftwareServers Commented Mar 12, 2018 at 23:51
- @Appleoddity I updated an image to explain just incase – FreeSoftwareServers Commented Mar 12, 2018 at 23:53
- Windows Explorer respects IE group policies. Are you an Administrator? – Ramhound Commented Mar 13, 2018 at 0:17
- I'm logged in as one, but I haven't messed much with Group Policy and I was under the impression sysprep generalize wouldn't keep group policy anyway. What GPO would I look at? – FreeSoftwareServers Commented Mar 13, 2018 at 0:20
3 Answers 3
The issue was that Group Policy was somehow blocking me from adding into IE Options like I'm used to.
You want to configure Group Policy like so:
Navigate to Computer Configuration\Administrative Templates\Windows Components\Internet Explorer\Internet Control Panel\Security Page >> Site to Zone Assignment List

The "Values" are as follows:
After configuration open CMD in Administrator mode and run the following:
Now reboot and test!
https://community.spiceworks.com/topic/1182041-gpo-for-local-intranet-site http://www.grouppolicy.biz/2010/03/how-to-use-group-policy-to-configure-internet-explorer-security-zone-sites/
This worked for me even though it's for Windows XP.
All credit to the original author.
FYI, my system specs are:
LINK: Sites" button and "Custom Level" slider are grayed out in Internet Options - Security tab
This is the contents of that site should it ever get taken down.
When you open Internet Options - Security tab and click on any Zone (except Internet Zone), the Sites button may be grayed out. As a result, you may be unable to add or remove a website to the specified Zone. Additionally, you may also notice that the Custom level slider is grayed out. This prevents you from customizing the Security level for that particular Zone.
The Flags value in the registry governs the above two options (and more) for each Zone. See Description of Internet Explorer security zones registry entries for more information on the Flags value.
To enable the Sites button and the Custom Level slider for that particular Zone, follow these steps:
Open Registry Editor (regedit.exe) and navigate to
HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones\{Zone ID}
Backup the key by exporting it to a REG file.
- In the right-pane, double-click Flags and click Decimal
Add 3 to the existing Value data
Example: If Flags value reads 0 (Decimal), set it to 3 (i.e., 0 + 1 + 2 )
Flags value listing (from MS-KB 182569 )
Close Registry Editor and restart your machine and follow the route in your OP.
For me, the apply button was greyed out but it works none the less.
The entry I have entered is file://PRINCE_NASEEM but yours will differ.
- Nice, this looks like it enables the menu operations I'm used to vs fixing via GPO. This would likely be the better fix for me to use before "Sysprepping" an image. – FreeSoftwareServers Commented Jun 10, 2019 at 9:07
- Thanks, I'm glad you found this useful. It's good because, if it works in win XP, then there's a good chance it works right up to win 10. – Ste Commented Jun 11, 2019 at 10:09
I answer late, but I have the same problem. I recovered the .reg on a pc which was not impacted.
Copy the code, insert it into a text file that you rename to .reg.
You must log in to answer this question.
Not the answer you're looking for browse other questions tagged security internet-explorer internet-security ..
- The Overflow Blog
- From PHP to JavaScript to Kubernetes: how one backend engineer evolved over time
- Featured on Meta
- We've made changes to our Terms of Service & Privacy Policy - July 2024
- Bringing clarity to status tag usage on meta sites
Hot Network Questions
- Is it possible to create a board position where White must make the move that leads to stalemating Black to avoid Black stalemating White?
- How can I address my colleague communicating with us via chatGPT?
- How to apply refactoring on Latex code?
- A short story about a SF author telling his friends, as a joke, a harebrained SF story, and what follows
- Hotspot vs home internet
- Immutability across programming languages
- Electric skateboard: helmet replacement
- If the Collatz conjecture is undecidable, then it is true
- Inconsistent “unzip -l … | grep -q …” results with pipefail
- How does one go about writing papers as a nobody?
- Cannot remove old solder
- Seth and Cain take turns picking numbers from 1 to 50. Who wins?
- Why cant we save the heat rejected in a heat engine?
- Miracle Miracle Octad Generator Generator
- How to make a ParametricPlot3D into solid shape
- What's the Matter?
- How can you trust a forensic scientist to have maintained the chain of custody?
- Remove lines from a table
- Are automorphisms of matrix algebras necessarily determinant preservers?
- Which cards use −5 V and −12 V in IBM PC compatible systems?
- Flight left while checked in passenger queued for boarding
- Future perfect with different modals
- Unexpected behavior of SetDelayed and Derivative
- Melee Opportunist--making opportunity attacks have some bite for melee characters
Get the Reddit app
A reddit dedicated to the profession of Computer System Administration.
Any good read up available on internet zone mapping syntax and t-shooting?
Does anyone have a good resource that teaches you about the right syntax when configuring the site to zone assignment list for browsers?
When we do gpupdates we can see there's a long delay because the gpo can't process the site list without running into errors.
This stuck up in my company is pestering me and thinks the generic documentation from MS should be enough.
By continuing, you agree to our User Agreement and acknowledge that you understand the Privacy Policy .

Enter the 6-digit code from your authenticator app
You’ve set up two-factor authentication for this account.
Enter a 6-digit backup code
Create your username and password.
Reddit is anonymous, so your username is what you’ll go by here. Choose wisely—because once you get a name, you can’t change it.
Reset your password
Enter your email address or username and we’ll send you a link to reset your password
Check your inbox
An email with a link to reset your password was sent to the email address associated with your account
Choose a Reddit account to continue
- API Documentation
- Administrator
- Features and Enhancements
- RapidIdentity Release Notes
- Known Issues
- Support Policies
- Support Bulletins
- Threat Advisories
- 27 Oct 2023
- 3 Minutes to read
- How To Configure Kerberos Authentication
- Updated on 27 Oct 2023
Introduction
Traditionally, a user has always been required to enter their username and password in order to log in to RapidIdentity. Customers may deem this process redundant when a user has already logged into their domain-joined Windows workstation.
Kerberos Authentication is supported in RapidIdentity 3.5 for On-Premise and 2022.4.5 for Cloud - verify that you are running a version that supports Kerberos Authentication. This process eliminates the username and password requirement when a user is logging in from a domain-joined Windows workstation.
Prerequisites
Prior to attempting to configure Kerberos Authentication, you should complete the following tasks:
- Ensure that you are licensed for Kerberos Authentication .
- When using RapidIdentity Cloud, install an Identity Bridge , configuring TCP port 88 at a minimum. (This is the Kerberos v5 port; Kerberos v4 is not recommended.)
Active Directory Configuration
- Select the option to prevent the user from changing their password
- Select the option to indicate that the user’s password never expires
- Select the option to not require Kerberos pre-authentication
- RapidIdentityURL: The FQDN of your RapidIdentity server, for example, “idauto.us001-rapididentity.com”
- KerberosUsername: The username created in step 1 of this section.
- RapidIdentityURL: The VanityURL of your RapidIdentity server, for example, “vanity.idauto.us001-rapididentity.com”
Group Policy Configuration
Certain configuration changes need to be made on each Windows workstation to support Kerberos Authentication. Rather than manage these individually, a group policy can be configured to automate that process.
- Set this policy to Enabled
- Value Name: https://my.example.com
- Configure a batch script (see template below) to configure Firefox and store it in \\test.local\NETLOGON\kerberos.bat
- Computer Configuration > Policies > Windows Settings > Scripts > Startup
Firefox Batch Script
Appliance Configuration ( For RapidIdentity On-Premise Only)
- The RapidIdentity Appliance must be able to resolve your domain through DNS. Ideally, your appliance will be configured to use your domain controllers for DNS. Alternatively, you can configure your host's file to point to your domain, however, your appliance will be limited to using only one domain controller for Kerberos Authentication
- Domain: test.local
- KDC Address: test.local
- Service Principal: HTTP/[email protected]
- Service Principal Password: Configured earlier in step 1 of Active Directory Configuration
- Criteria > Kerberos > Enabled: Checked
- Authentication Methods > Kerberos > Required: Checked
- Note: Additional authentication methods can be enabled (such as TOTP) to provide additional authentication.
Current Limitations
- Cloud Hosted Active Directories: It is currently unsupported to attempt Kerberos Authentication against a Cloud Hosted Active Directory.
- UPN Suffix: It is currently unsupported to attempt Kerberos Authentication using UPN Suffixes.
- Trusts: It is currently unsupported to attempt Kerberos Authentication against a trusted domain.
- Multiple Domains: It is currently unsupported to attempt Kerberos Authentication against multiple domains.
What's Next
- Enrolling in PingMe Authentication
Table of contents
Eddy AI, facilitating knowledge discovery through conversational intelligence
ericlaw talks about security, the web, and software in general
Security Zones in Edge
Last updated: 19 June 2024
Browsers As Decision Makers
As a part of every page load, browsers have to make dozens, hundreds, or even thousands of decisions — should a particular API be available? Should a resource load be permitted? Should script be allowed to run? Should video be allowed to start playing automatically? Should cookies or credentials be sent on network requests? The list is long.
In many cases, decisions are governed by two inputs: a user setting, and the URL of the page for which the decision is being made.
In the old Internet Explorer web platform, each of these decisions was called an URLAction , and the ProcessUrlAction(url, action,…) API allowed the browser or another web client to query its security manager for guidance on how to behave.

To simplify the configuration for the user or their administrator, the legacy platform classified sites into five 1 different Security Zones :
- Local Machine
- Local Intranet
Users could use the Internet Control Panel to assign specific sites to Zones and to configure the permission results for each zone. When making a decision, the browser would first map the execution context (site) to a Zone, then consult the setting for that URLAction for that Zone to decide what to do.
Reasonable defaults like “ Automatically satisfy authentication challenges from my Intranet ” meant that most users never needed to change any settings away from their defaults.
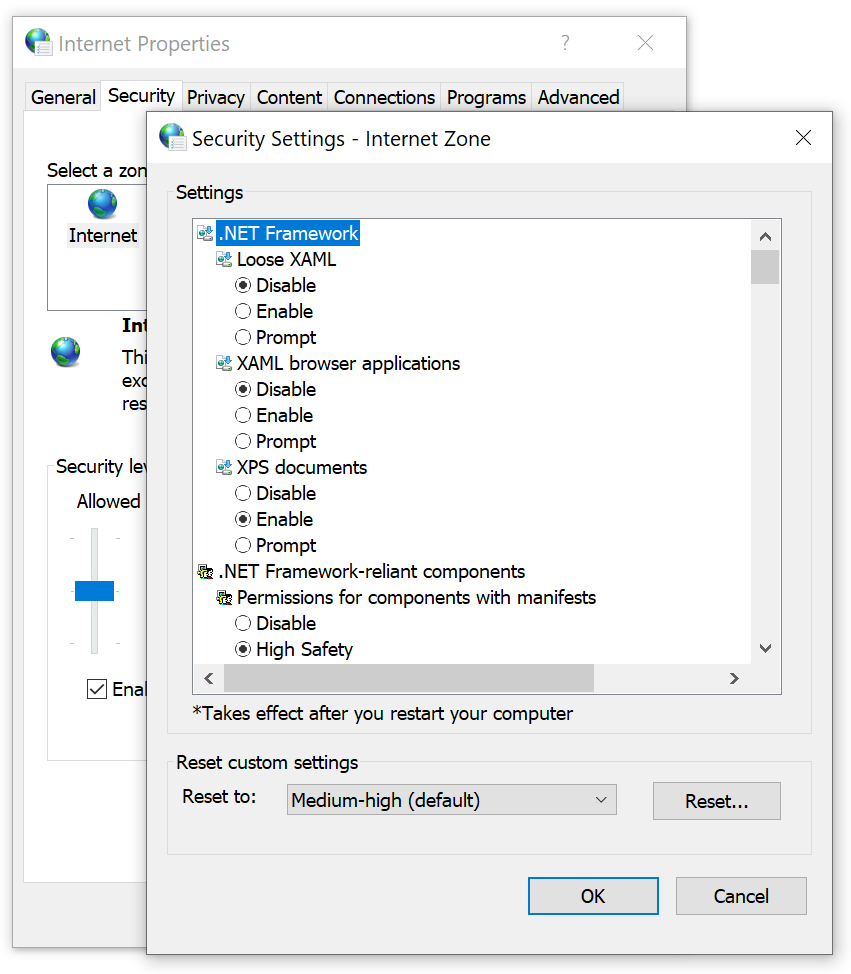
In corporate or other managed environments, administrators can use Group Policy to assign specific sites to Zones (via “Site to Zone Assignment List” policy) and specify the settings for URLActions on a per-zone basis. This allowed Microsoft IT, for instance, to configure the browser with rules like “ Treat https://mail.microsoft.com as a part of my Intranet and allow popups and file downloads without warning messages. “
Beyond manual administrative or user assignment of sites to Zones, the platform used additional heuristics that could assign sites to the Local Intranet Zone . In particular, the browser would assign dotless hostnames (e.g. https://payroll ) to the Intranet Zone, and if a Proxy Configuration script was used, any sites configured to bypass the proxy would be mapped to the Intranet Zone.
Applications hosting Web Browser Controls, by default, inherit the Windows Zone configuration settings, meaning that changes made for Internet Explorer are inherited by other applications. In relatively rare cases, the host application might supply its own Security Manager and override URL Policy decisions for embedded Web Browser Control instances.
The Trouble with Zones
While powerful and convenient, Zones are simultaneously problematic bug farms :
- Users might find that their mission critical corporate sites stopped working if their computer’s Group Policy configuration was outdated.
- Users might manually set configuration options to unsafe values without realizing it.
- Attempts to automatically provide isolation of cookies and other data by Zone led to unexpected behavior , especially for federated authentication scenarios .
Zone-mapping heuristics are extra problematic
- A Web Developer working on a site locally might find that it worked fine (Intranet Zone), but failed spectacularly for their users when deployed to production (Internet Zone).
- Users were often completely flummoxed to find that the same page on a single server behaved very differently depending on how they referred to it — e.g. http://localhost/ (Intranet Zone) vs. http://127.0.0.1/ (Internet Zone).
The fact that proxy configuration scripts can push sites into the Intranet zone proves especially challenging, because:
- A synchronous API call might need to know what Zone a caller is in, but determining that could, in the worst case, take tens of seconds — the time needed to discover the location of the proxy configuration script, download it, and run the FindProxyForUrl() function within it. This could lead to a hang and unresponsive UI.
- A site’s Zone can change at runtime without restarting the browser (say, when moving a laptop between home and work networks, or when connecting or disconnecting from a VPN).
- An IT Department might not realize the implications of returning DIRECT from a proxy configuration script and accidentally map the entire untrusted web into the highly-privileged Intranet Zone. (Microsoft IT accidentally did this circa 2011, and Google IT accidentally did it circa 2016).
- Some features like AppContainer Network Isolation are based on firewall configuration and have no inherent relationship to the browser’s Zone settings.
Legacy Edge
The legacy Edge browser (aka Spartan, Edge 18 and below) inherited the Zone architecture from its Internet Explorer predecessor with a few simplifying changes:
- Windows’ five built-in Zones were collapsed to three: Internet (Internet), the Trusted Zone (Intranet+Trusted), and the Local Computer Zone. The Restricted Zone was removed.
- Zone to URLAction mappings were hardcoded into the browser, ignoring group policies and settings in the Internet Control Panel.
Use of Zones in Chromium
Chromium goes further and favors making decisions based on explicitly-configured site lists and/or command-line arguments.
Nevertheless, in the interest of expediency, Chromium today uses Windows’ Security Zones by default in two places:
- When deciding how to handle File Downloads, and
- When deciding whether or not to release Windows Integrated Authentication (Kerberos/NTLM) credentials automatically.
For the first one, if you’ve configured the setting Launching applications and unsafe files to Disable in your Internet Control Panel’s Security tab, Chromium will block file downloads with a note: Couldn't download - Blocked .
Similarly, because Chrome uses the Windows Attachment Execute Services API to write a Mark-of-the-Web on downloaded files , the Launching applications and unsafe files setting (aka URLACTION_SHELL_EXECUTE_HIGHRISK ) for the download’s originating Zone controls whether the MoTW is written. If this setting is set to Enable (as it is for LMZ and Intranet), no MoTW is written to the file’s Zone.Identifier alternate data stream. If the Zone’s URLAction value is set to Prompt (as it is for Trusted Sites and Internet zones), the Security Zone identifier is written to the ZoneId property in the Zone.Identifier file.
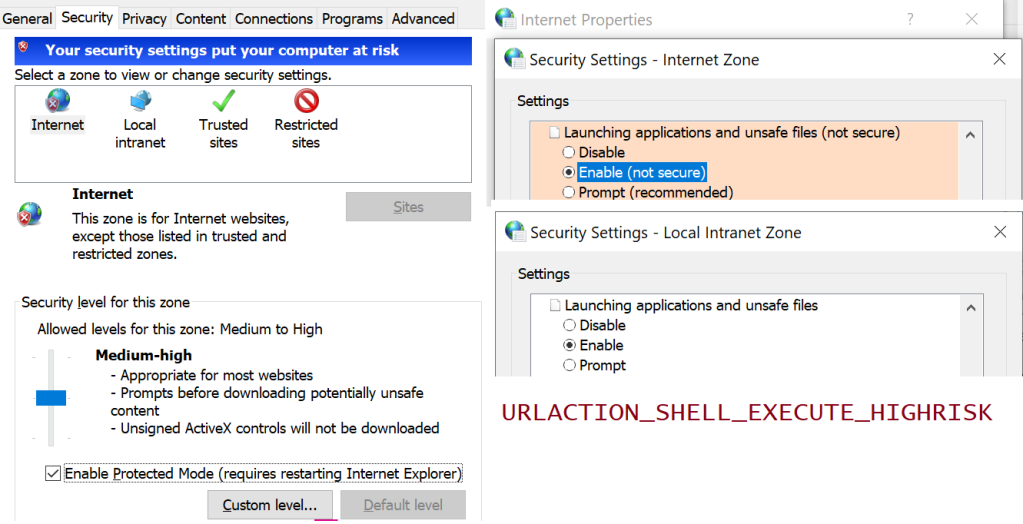
By setting a policy, Administrators can optionally configure Edge or configure Chrome to skip SmartScreen/SafeBrowsing reputation checks for File Downloads that original from the Intranet/Trusted Zone.
For the second use of Zones, Chromium will process URLACTION_CREDENTIALS_USE to decide whether Windows Integrated Authentication is used automatically, or the user should instead see a manual authentication prompt. By setting the AuthServerAllowList policy , an admin may prevent Zone Mapping from being used to decide whether credentials should be sent. Aside: the manual authentication prompt is really a bit of a mistake– the browser should instead just show a prompt: “Would you like to [Send Credentials] or [Stay Anonymous]” dialog box, rather than forcing the user to retype credentials that Windows already has.
Even Limited Use is Controversial
Any respect for Zones (or network addresses 2 ) in Chromium remains controversial— the Chrome team has launched and abandoned plans to remove all support a few times, but ultimately given up under the weight of enterprise compat concerns. The arguments for complete removal include:
- Zones are poorly documented, and Windows Zone behavior is poorly understood.
- The performance/deadlock risks mentioned earlier ( Intranet Zone mappings can come from a WPAD-discovered proxy script).
- Zones are Windows-only (meaning they prevent drop-in replacement of Windows by ChromeOS).
A sort of compromise was reached: By configuring an explicit site list policy for Windows Authentication, an administrator disables the browser’s URLACTION_CREDENTIALS_USE check, so Zones Policy is not consulted. A similar option is not presently available for Downloads.
Zones in the New Edge
Beyond the two usages of Zones inherited from upstream (Downloads and Auth), the new Chromium-based Edge browser adds three more:
- Administrators can configure Internet Explorer Mode to open all Intranet sites in IEMode . Those IEMode tabs are really running Internet Explorer, and they use Zones for everything that IE did.
- Administrators can configure Intranet Zone sites to navigate to file:// URIs which is otherwise forbidden .
- Administrators can configure Intranet Zone sites to not be put into Enhanced Security Mode .
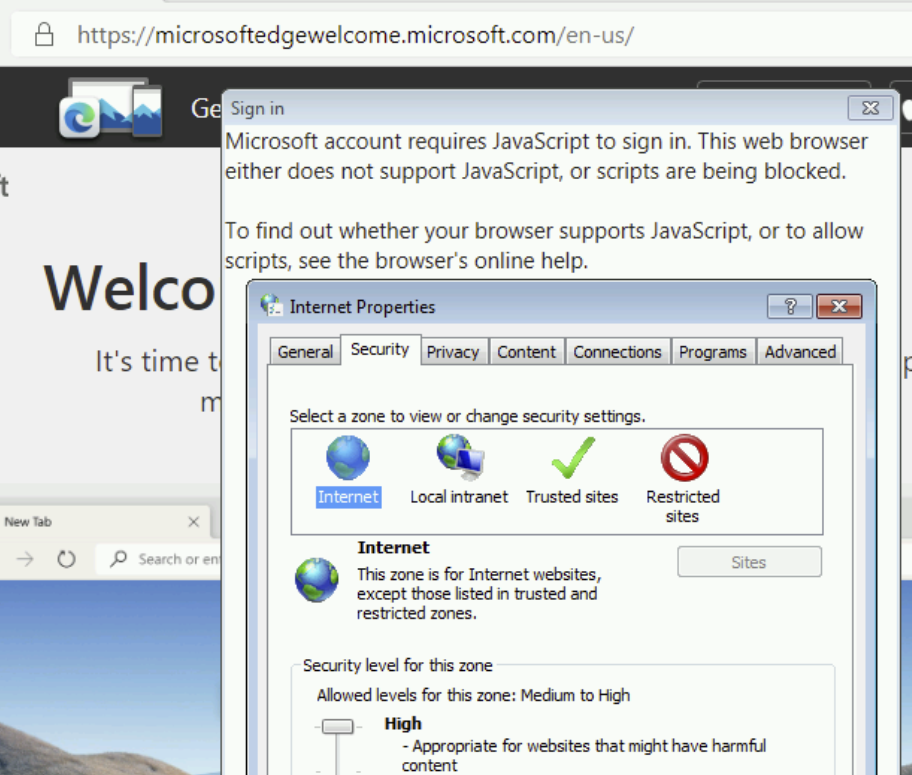
Update: This is very much a corner case, but I’ll mention it anyway. On downlevel operating systems (Windows 7/8/8.1), logging into the browser for sync makes use of a Windows dialog box that contains a Web Browser Control (based on MSHTML) that loads the login page. If you adjust your Windows Security Zones settings to block JavaScript from running in the Internet Zone, you will find that you’re unable to log into the new browser .
Downsides/Limitations
While it’s somewhat liberating that we’ve moved away from the bug farm of Security Zones, it also gives us one less tool to make things convenient or compatible for our users and IT admins.
We’ve already heard from some customers that they’d like to have a different security and privacy posture for sites on their “Intranet”, with behaviors like:
- Disable the Tracking Prevention , “Block 3rd party cookie”, and other privacy-related controls for the Intranet (like IE/Edge did).
- Allow navigation to file:// URIs from the Intranet like IE/Edge did (policy was added to Edge 95).
- Disable “ HTTP and mixed content are unsafe ” and “ TLS/1.0 and TLS/1.1 are deprecated ” nags. ( Update: Now pretty obsolete as these no longer exist )
- Skip SmartScreen website checks for the Trusted/Intranet zones ( available for Download checks only).
- Allow ClickOnce/DirectInvoke / Auto-opening Downloads from the Intranet without a prompt. Previously, Edge (Spartan)/IE respected the FTA_OpenIsSafe bit in the EditFlags for the application.manifest progid if-and-only-if the download source was in the Intranet/Trusted Sites Zone. As of Edge 94, other policies can be used.
- Allow launching application protocols from the Intranet without a prompt .
- Drop all Referrers when navigating from the Intranet to the Internet; leave Referrers alone when browsing the Intranet. (Update: less relevant now ).
- Internet Explorer and legacy Edge automatically send your client certificate to Intranet sites that ask for it. The AutoSelectCertificateForUrls policy permits Edge to send a client certificate to specified sites without a prompt, but this policy requires the administrator to manually specify the site list.
- Block all (or most) extensions from touching Intranet pages to reduce the threat of data leaks ( runtime_blocked_hosts policy).
- Guide all Intranet navigations into an appropriate profile or container (a la Detangle ).
- Upstream , there’s a longstanding desire to help protect intranets/local machine from cross-site-request-forgery attacks; blocking loads and navigations of private resources from the Internet Zone is somewhat simpler than blocking them from Intranet Sites. The current plan is to protect RFC1918-reserved address space .
At present, only AutoSelectCertificateForUrls , AutoOpenFileTypes, AutoLaunchProtocolsFromOrigins . manual cookie controls, and mixed content nags support policy-pushed site lists, but their list syntax doesn’t have any concept of “the entire Intranet” (all dotless hosts, hosts that bypass proxy).
You’ll notice that each of these has potential security impact (e.g. an XSS on a privileged “Intranet” page becomes more dangerous; unqualified hostnames can result in name collisions ), but having the ability to scope some powerful features to only “Intranet” sites might also improve security by reducing attack surface.
As browser designers, we must weigh the enterprise impact of every change we make, and being able to say “ This won’t apply to your intranet if you don’t want it to ” would be very liberating. Unfortunately, building such an escape hatch is also the recipe for accumulating technical debt and permitting the corporate intranets to “rust” to the point that they barely resemble the modern public web.
Best Practices
Throughout Chromium, many features are designed respect an individual policy-pushed list of sites to control their behavior. If you were forward-thinking enough to structure your intranet such that your hostnames are of the form:
- https://payroll. contoso-intranet.com
- https://timecard. contoso-intranet.com
- https://sharepoint. contoso-intranet.com
…Congratulations, you’ve lucked into a best practice. You can configure each desired policy with a *.contoso-intranet.com entry and your entire Intranet will be opted in.
Unfortunately, while wildcards are supported, there’s presently no way to express the concept of “any dotless hostname.”
Why is that unfortunate? For over twenty years, Internet Explorer and legacy Edge mapped domain names like https://payroll , https://timecard , and https://sharepoint/ to the Intranet Zone by default. As a result, many smaller companies have benefitted from this simple heuristic that requires no configuration changes by the user or the IT department.
Opportunity: Maybe such a DOTLESS_HOSTS token should exist in the Chromium policy syntax. This seems unlikely to happen. Edge has been on Chromium for over two years now, and there’s no active plan to introduce such a feature.
- Internet Explorer and Legacy Edge use a system of five Zones and 88+ URLActions to make security decisions for web content, based on the host of a target site.
- Chromium (New Edge, Chrome) uses a system of Site Lists and permission checks to make security decisions for web content, based on the hostname of a target site.
There does not exist an exact mapping between these two systems, which exist for similar reasons but implemented using very different mechanisms.
In general, users should expect to be able to use the new Edge without configuring anything; many of the URLActions that were exposed by IE/Spartan have no logical equivalent in modern browsers.
If the new Edge browser does not behave in the desired way for some customer scenario, then we must examine the details of what isn’t working as desired to determine whether there exists a setting (e.g. a Group Policy-pushed SiteList) that provides the desired experience.
1 Technically, it was possible for an administrator to create “Custom Security Zones” (with increasing ZoneIds starting at #5), but such a configuration has not been officially supported for at least fifteen years, and it’s been a periodic source of never-will-be-fixed bugs.
2 Beyond those explicit uses of Windows’ Zone Manager, various components in Chromium have special handling for localhost/loopback addresses, and some have special recognition of RFC1918 private IP Address ranges, e.g. SafeBrowsing handling, navigation restrictions, and Network Quality Estimation. As of 2022, Chrome did a big refactor to allow determination of whether or not the target site’s IP address is in the public IP Address space or the private IP address space (e.g. inherently Intranet) as a part of the Private Network Access spec . This check should now be basically free (it’s getting used on every resource load) and it may make sense to start using it in a lot of places to approximate the “ This target is not on the public Internet ” check. Within Edge, the EMIE List is another mechanism by which sites’ hostnames may result in different handling.
Ancient History
Security Zones were introduced with Internet Explorer 4, released back in 1997:
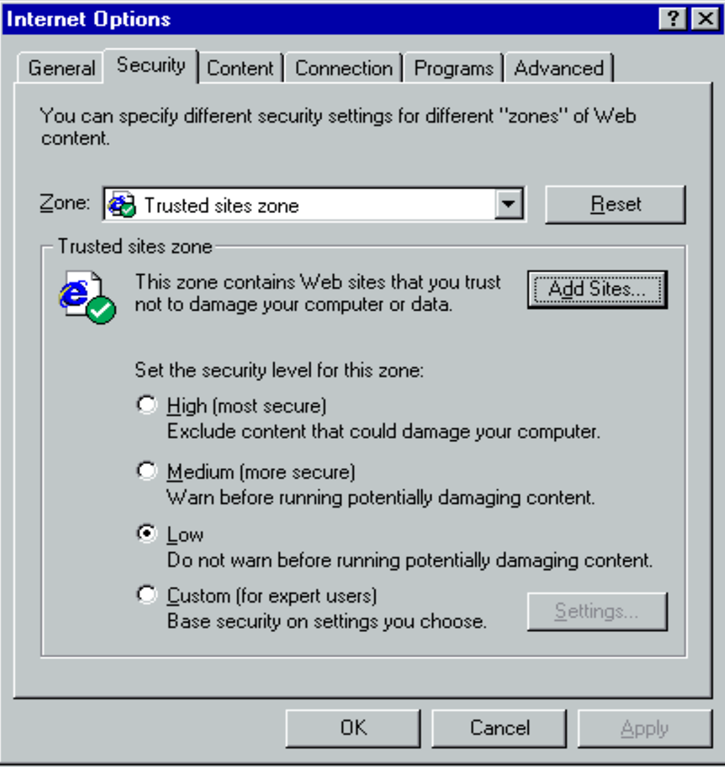
The UI has only changed a little bit since that time, with most of the changes happening in IE5. There were only tiny tweaks in IE6, 7, and 8.
Share this:
Published by ericlaw.
Impatient optimist. Dad. Author/speaker. Created Fiddler & SlickRun. PM @ Microsoft 2001-2012, and 2018-, working on Office, IE, and Edge. Now a GPM for Microsoft Defender. My words are my own, I do not speak for any other entity. View more posts
2 thoughts on “ Security Zones in Edge ”
In IE it is possible to see which zone is active on a page you’re currently viewing (alt to show menu bar, -> file -> properties).
Is it possible to see this in the new Edge?
No, although as noted, the Zone isn’t used for very much. To see the Zone, you’d have to reload the same page in IE (or use a command line utility or similar).
Leave a comment Cancel reply
- Already have a WordPress.com account? Log in now.
- Subscribe Subscribed
- Copy shortlink
- Report this content
- View post in Reader
- Manage subscriptions
- Collapse this bar
This browser is no longer supported.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support.
Internet Explorer security zones registry entries for advanced users
- 2 contributors
The retired, out-of-support Internet Explorer 11 desktop application has been permanently disabled through a Microsoft Edge update on certain versions of Windows 10. For more information, see Internet Explorer 11 desktop app retirement FAQ .
This article describes how and where Internet Explorer security zones and privacy settings are stored and managed in the registry. You can use Group Policy or the Microsoft Internet Explorer Administration Kit (IEAK) to set security zones and privacy settings.
Original product version: Internet Explorer 9, Internet Explorer 10 Original KB number: 182569
Privacy settings
Internet Explorer 6 and later versions added a Privacy tab to give users more control over cookies. This tab (select Tools , and then select Internet options ) provides flexibility for blocking or allowing cookies, based on the website that the cookie came from or the type of cookie. Types of cookies include first-party cookies, third-party cookies, and cookies that do not have a compact privacy policy. This tab also includes options to control website requests for physical location data, the ability to block pop-ups, and the ability to run toolbars and extensions when InPrivate browsing is enabled.
There are different levels of privacy on the Internet zone, and they are stored in the registry at the same location as the security zones.
You can also add a Web site to enable or to block cookies based on the Web site, regardless of the privacy policy on the Web site. Those registry keys are stored in the following registry subkey:
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Internet Settings\P3P\History
Domains that have been added as a managed site are listed under this subkey. These domains can carry either of the following DWORD values:
0x00000005 - Always Block 0x00000001 - Always Allow
Security Zone settings
For each zone, users can control how Internet Explorer handles higher-risk items such as ActiveX controls, downloads, and scripts. Internet Explorer security zones settings are stored under the following registry subkeys:
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings
- HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings
These registry keys contain the following keys:
TemplatePolicies
By default, security zones settings are stored in the HKEY_CURRENT_USER registry subtree. Because this subtree is dynamically loaded for each user, the settings for one user do not affect the settings for another.
If the Security Zones: Use only machine settings setting in Group Policy is enabled, or if the Security_HKLM_only DWORD value is present and has a value of 1 in the following registry subkey, only local computer settings are used and all users have the same security settings:
HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\CurrentVersion\Internet Settings
With the Security_HKLM_only policy enabled, HKLM values will be used by Internet Explorer. However, the HKCU values will still be displayed in the zone settings on the Security tab in Internet Explorer. In Internet Explorer 7, the Security tab of the Internet Options dialog box displays the following message to indicate that settings are managed by the system administrator:
Some settings are managed by your system administrator If the Security Zones: Use only machine settings setting is not enabled in Group Policy, or if the Security_HKLM_only DWORD value does not exist or is set to 0 , computer settings are used together with user settings. However, only user settings appear in the Internet Options . For example, when this DWORD value does not exist or is set to 0 , HKEY_LOCAL_MACHINE settings are read together with HKEY_CURRENT_USER settings, but only HKEY_CURRENT_USER settings appear in the Internet Options .
The TemplatePolicies key determines the settings of the default security zone levels. These levels are Low, Medium Low, Medium, and High. You can change the security level settings from the default settings. However, you cannot add more security levels. The keys contain values that determine the setting for the security zone. Each key contains a Description string value and a Display Name string value that determine the text that appears on the Security tab for each security level.
The ZoneMap key contains the following keys:
- ProtocolDefaults
The Domains key contains domains and protocols that have been added to change their behavior from the default behavior. When a domain is added, a key is added to the Domains key. Subdomains appear as keys under the domain where they belong. Each key that lists a domain contains a DWORD with a value name of the affected protocol. The value of the DWORD is the same as the numeric value of the security zone where the domain is added.
The EscDomains key resembles the Domains key except that the EscDomains key applies to those protocols that are affected by the Internet Explorer Enhanced Security Configuration (IE ESC). IE ESC is introduced in Microsoft Windows Server 2003 and applies to server operating systems only.
The ProtocolDefaults key specifies the default security zone that is used for a particular protocol (ftp, http, https). To change the default setting, you can either add a protocol to a security zone by selecting Add Sites on the Security tab, or you can add a DWORD value under the Domains key. The name of the DWORD value must match the protocol name, and it must not contain any colons (:) or slashes (/).
The ProtocolDefaults key also contains DWORD values that specify the default security zones where a protocol is used. You cannot use the controls on the Security tab to change these values. This setting is used when a particular Web site does not fall in a security zone.
The Ranges key contains ranges of TCP/IP addresses. Each TCP/IP range that you specify appears in an arbitrarily named key. This key contains a :Range string value that contains the specified TCP/IP range. For each protocol, a DWORD value is added that contains the numeric value of the security zone for the specified IP range.
When the Urlmon.dll file uses the MapUrlToZone public function to resolve a particular URL to a security zone, it uses one of the following methods:
If the URL contains a fully qualified domain name (FQDN), the Domains key is processed.
In this method, an exact site match overrides a random match.
If the URL contains an IP address, the Ranges key is processed. The IP address of the URL is compared to the :Range value that is contained in the arbitrarily named keys under the Ranges key.
Because arbitrarily named keys are processed in the order that they were added to the registry, this method may find a random match before it finds a match. If this method does find a random match first, the URL may be executed in a different security zone than the zone where it is typically assigned. This behavior is by design.
The Zones key contains keys that represent each security zone that is defined for the computer. By default, the following five zones are defined (numbered zero through four):
By default, My Computer does not appear in the Zone box on the Security tab as it is locked down to help improve security.
Each of these keys contains the following DWORD values that represent corresponding settings on the custom Security tab.
Unless stated otherwise, each DWORD value is equal to zero, one, or three. Typically, a setting of zero sets a specific action as permitted, a setting of one causes a prompt to appear, and a setting of three prohibits the specific action.
Notes about 1200, 1A00, 1A10, 1E05, 1C00, and 2000
The following two registry entries affect whether you can run ActiveX controls in a particular zone:
- 1200 This registry entry affects whether you can run ActiveX controls or plug-ins.
- 2000 This registry entry controls binary behavior and script behavior for ActiveX controls or plug-ins.
Notes about 1A02, 1A03, 1A05, and 1A06
The following four registry entries take only effect if the following keys are present:
- {AEBA21FA-782A-4A90-978D-B72164C80120} First Party Cookie *
- {A8A88C49-5EB2-4990-A1A2-0876022C854F} Third-Party Cookie *
Registry entries
- 1A02 Allow persistent cookies that are stored on your computer #
- 1A03 Allow per-session cookies (not stored) #
- 1A05 Allow third party persistent cookies *
- 1A06 Allow third party session cookies *
These registry entries are located in the following registry subkey:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\Zones\<ZoneNumber>
In this registry subkey, <ZoneNumber> is a zone such as 0 (zero). The 1200 registry entry and the 2000 registry entry each contain a setting that is named Administrator approved. When this setting is enabled, the value for the particular registry entry is set to 00010000 . When the Administrator approved setting is enabled, Windows examines the following registry subkey to locate a list of approved controls:
HKEY_CURRENT_USER\Software\Policies\Microsoft\Windows\CurrentVersion\Internet Settings\AllowedControls
Logon setting (1A00) may have any one of the following values (hexadecimal):
Privacy Settings (1A10) is used by the Privacy tab slider. The DWORD values are as follows:
Block All Cookies: 00000003 High: 00000001 Medium High: 00000001 Medium: 00000001 Low: 00000001 Accept all Cookies: 00000000
Based on the settings in the slider, it will also modify the values in {A8A88C49-5EB2-4990-A1A2-0876022C854F}, {AEBA21Fa-782A-4A90-978D-B72164C80120}, or both.
The Java Permissions setting (1C00) has the following five possible values (binary):
If Custom is selected, it uses {7839DA25-F5FE-11D0-883B-0080C726DCBB} (that is located in the same registry location) to store the custom information in a binary.
Each security zone contains the Description string value and the Display Name string value. The text of these values appears on the Security tab when you select a zone in the Zone box. There is also an Icon string value that sets the icon that appears for each zone. Except for the My Computer zone, each zone contains a CurrentLevel , MinLevel , and RecommendedLevel DWORD value. The MinLevel value sets the lowest setting that can be used before you receive a warning message, CurrentLevel is the current setting for the zone, and RecommendedLevel is the recommended level for the zone.
What values for Minlevel , RecommendedLevel , and CurrentLevel mean the following:
The Flags DWORD value determines the ability of the user to modify the security zone's properties. To determine the Flags value, add the numbers of the appropriate settings together. The following Flags values are available (decimal):
If you add settings to both the HKEY_LOCAL_MACHIN E and the HKEY_CURRENT_USER subtrees, the settings are additive. If you add Web sites to both subtrees, only those Web sites in the HKEY_CURRENT_USER are visible. The Web sites in the HKEY_LOCAL_MACHINE subtree are still enforced according to their settings. However, they are not available, and you cannot modify them. This situation can be confusing because a Web site may be listed in only one security zone for each protocol.
For more information about changes to functionality in Microsoft Windows XP Service Pack 2 (SP2), visit the following Microsoft Web site:
Part 5: Enhanced Browsing Security
For more information about URL security zones, visit the following Microsoft Web site:
About URL Security Zones
For more information about how to change Internet Explorer security settings, visit the following Microsoft Web site:
Change security and privacy settings for Internet Explorer 11
For more information about Internet Explorer Local Machine Zone Lockdown, visit the following Microsoft Web site:
Internet Explorer Local Machine Zone Lockdown
For more information about values associated with the actions that can be taken in a URL security zone, see URL Action Flags .
Additional resources

IMAGES
COMMENTS
This help content & information General Help Center experience. Search. Clear search
The setting (User Settings -> Administrative Templates -> Windows Components -> Internet Explorer -> Internet Control Panel -> Security Page -> Site to Zone Assignment List) still has good old IE in its name, but apparently should apply generally. At least this used to work across all browsers in the past. Accordingly, files that are downloaded ...
Chrome should really be grabbing the security settings from IE and work in the same way. If there is more than one hop for the auth, then you'll have to do this: [HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Google\Chrome] "AuthNegotiateDelegateWhitelist"="site.domain.com"
This blog article explains it clearly. In summary, Chromium uses Security Zones for File Downloads and automatic Windows Integrated Authentication. An explicit site list policy for Authentication will override using Zones for WIA. New Edge will also use Zones for tabs that are in IE Mode, as they are actually running in IE 11.
Hello All, I am coming to you because I am getting stumped with what I believe to be a Site to Zone Assignment List issue. Here is a rundown of what is happening: 1)We purchased a product from clickstudios called Passwordstate. It is a web based enterprise solution password manager. 2)installed the IE extension and the chrome extension on Windows 10 computers via GPO (small installs) 3)Works ...
In managed environments, administrators can use Group Policy to assign specific sites to Zones (via "Site to Zone Assignment List" policy) and specify the settings for URLActions on a per-zone basis. Beyond manual administrative or user assignment of sites to Zones, other heuristics could assign sites to the Local Intranet Zone .
The object being Site to Zone Assignment List. group-policy; windows-domain; Share. Improve this question. Follow asked Aug 20, 2019 at 5:24. Alexander Johansen Alexander Johansen. 177 1 1 silver badge 10 10 bronze badges. Add a comment | 1 Answer Sorted by: Reset to default ...
If you want to lock it down and add as needed, GPO will work just fine, just go to Win Components/Internet Explorer/Internet Control Panel/Security Page - Site to Zone Assignment - enable the policy, click List and add the sites as needed, a value of 1 is Intranet a value of 2 would be Trusted. Yes. I want to lock it down so I will do it in ...
4. Add one URL to Intranet Zone and Another Url To trusted Site Zone through GPO Requirement: Add one URL to Intranet Zone and Another Url To trusted Site Zone. The above requirement can be achieved in three ways. Option 1: Computer Configuration ""> Administrative Tools ""> Windows Components ""> Internet Explorer ""> Internet ...
In the right-hand pane, double-click "Site to Zone Assignment List". Enable the policy and click the "Show…" button next to "Enter the zone assignments here." This will pop up the "Show Contents" window. Click the "Add…" button. This will pop up the "Add Item" window.
When either deleting, or setting this to 0, the sites immediately appear in internet control panel, and works as expected. So while I know what is causing the problem, and have enough to fudge a workaround by deleting that key for each user on login, I still don't understand why that key is set to 1, or even exists in the first place (some ...
Manage Google Chrome using Group Policy, SCCM or your own management utility. On-Demand Demo. PolicyPak Least Privilege Manager v. Traditional Whitelisting (such as Applocker) ... Why doesn't Site to Zone list assignment work with the syntax I provided? Posted on December 18, 2020 by Ali Hassan.
3.Clearing ZoneMap Entries: Instead of relying solely on modifying the "site to zone assignment list" template, you can consider using a startup script in a GPO to delete the unwanted entries from the ZoneMap registry key. This script can run with elevated privileges and remove the obsolete entries. You can use PowerShell or batch scripting to ...
Let me know if you don't.) In the Group Policy Management Editor, go to User Configuration → Policies → Administrative Templates → Windows Components → Internet Explorer. Find the policy Disable changing home page settings. Set it to Enabled, and specify the URL for your home page (your Intranet). Once it applies, the option in IE ...
1. Create a new GPO, or use an existing GPO. 2. Edit the GPO for the following settings: a. Under User Configuration\Policies\Windows Components\Internet Explorer\Internet Control Panel\Security Page\Site to Zone Assignment List: Define this policy setting as Enabled, then click the Show ... button to define the URLs and zone assignment.
Deploy a set of trusted sites overriding users' ability to add trusted sites themselves. To acheive this, an Intune configuration profile Trusted site zone assignment can be deployed to devices/users group as required. Login to Intune Portal and navigate to: Devices > Windows > Configuration Profiles. Hit the Create button and Select New ...
In the right-pane, double-click Flags and click Decimal. Add 3 to the existing Value data. Example: If Flags value reads 0 (Decimal), set it to 3 (i.e., 0 + 1 + 2) Flags value listing (from MS-KB 182569) Flags value Setting. 1 Allow changes to custom settings. 2 Allow users to add Web sites to this zone.
IE trusted sites is one of Windows Security Zones. Chrome and Edge make very limited use of Windows Security Zones. There's a detailed blog about security zones in different browsers by EricLaw. You can check it. In paragraph Use of Zones in Chromium, it clarifies there's only two situations chromium uses Windows Security Zones: 1.When deciding ...
host.domain.fqdn. *.domain.fqdn. protocol://host.domain.fqdn. protocol://*.domain.fqdn. Essentially each entry is made of 2 mandatory choices: either "all protocols" or "this specific protocol", and "all hosts for this domain & subdomains" or "this specific host". Entries that are more restrictive take precedence (though I can never remember ...
Re: Site to Zone Assignment List - Powershell. # Step 2: Navigate to the Site to Zone Assignment List # This step is manual and requires navigating through the Group Policy Management Editor interface. # Step 3: Enable the Policy and Specify Zone Assignments # Define the list of URLs and their corresponding zone assignments.
Add your RapidIdentity URL to the Internet Sites list. User Configuration > Policies > Administrative Templates > Windows Components > Microsoft Edge > Internet Control Panel > Security Page > Site to Zone Assignments List. Set this policy to Enabled; Add an assignment for your RapidIdentity server to Intranet Sites, for example
Legacy Edge. The legacy Edge browser (aka Spartan, Edge 18 and below) inherited the Zone architecture from its Internet Explorer predecessor with a few simplifying changes: Windows' five built-in Zones were collapsed to three: Internet (Internet), the Trusted Zone (Intranet+Trusted), and the Local Computer Zone. The Restricted Zone was removed.
Value Setting ----- 0 My Computer 1 Local Intranet Zone 2 Trusted sites Zone 3 Internet Zone 4 Restricted Sites Zone Note. By default, My Computer does not appear in the Zone box on the Security tab as it is locked down to help improve security. Each of these keys contains the following DWORD values that represent corresponding settings on the ...